SaaS technology offers businesses broader access to IT resources than ever before. On average, large enterprises utilize more than 1000 SaaS tools, constantly increasing as new applications are introduced. However, using numerous tools leads to high SaaS security risks as managing and monitoring many apps gets intricate.
The Zero Trust model is one of the most effective authentication systems used for taming SaaS challenges as it trusts no connection and access requests without accurate information required for verification.
Businesses rely excessively on SaaS tools these days, thus, requiring an effective SaaS management and security tool. In addition, as the number of remote and geographically distributed work environments has increased, there is a significant chance that employee connections originate from networks outside the organization's control.
Shadow IT is another recurring issue as it has become effortless for the employees to purchase or subscribe to SaaS applications as per their needs, hence, making the IT environment beyond the corporate's control. Furthermore, the IT department does not review these applications; therefore, they pose a threat and increase the risk of data breaches.
The SaaS applications are generally managed by a third party and are out of the organization's control. Therefore, it is difficult for companies to ensure that their SaaS apps are secure and data is maintained.
Zero trust, an innovative stringent security model, takes care of these challenges, denies access by default, and examines each device and network in the context of the security situation at that time. Furthermore, this system enforces these policies regardless of the user, location, and software you access.
Let's understand Zero trust in brief–
What is the Zero Trust model?
Zero Trust is a security system that requests user identity for decision-making and uses it to determine if the user can be trusted to access the resources. This security model requests user identity and has the qualities of trusting nothing, validating everything, and giving companies the highest amount of security. It is considered the ultra-safe model, a shielding pattern for the upcoming, unrecognized, common threats. Contrasting to perimeter security, it does not assure trust and allows users inside the organization's resources to presume they can be trusted. It demands that every user and device be identified to grant any level of access. These users and devices must also continue to re-verify themselves in cases of re-entering these zones.
This model authenticates every user with the help of a combination of authentication categories, including MFA. This way, through secure, layered authentication techniques, it limits and monitors security credentials and network traffic.
The applications and devices remain locked unless and until the appropriate user verifies themselves, fulfilling Zero Trust's demands. In addition, identity Protocols(IP) enable geofencing and listing by location, which narrows network access. Zero trust protects enterprises by securing third-party access, multi-cloud remote access, IoT visibility and security, and data centre micro-segmentation.
How Does Zero Trust Model Help In Improving SaaS security?
The Zero Trust model helps overcome the SaaS challenges of modern digital transformation. It mitigates the severity and the impacts of cyberattacks, including the time and cost efficiency for the period required for cleaning up these breaches.
Here are some important ways it helps eliminate SaaS security challenges:
1. Mitigates potential dangers of your company
Zero-trust solutions prevent all applications and services from interacting with each other until their identity attributes have been checked. These attributes are fixed properties that adhere to trust principles like authentication and authorization requirements.
Therefore, reducing risk as it makes the network contents and the relationships among its components transparent. As baselines are set, a zero-trust strategy further reduces risk by eliminating software and services that are overprovisioned and by constantly verifying the "credentials" of every communicating asset.
The IT and security team can gain business insight and manage and protect organizational and business risk with zero trust. When the security teams have complete business awareness, they achieve an all-around visibility of the SaaS applications and organizational operations, which helps them understand the context required for Zero Trust.
2. Reduces the data breach incidents
Using the principle of least privilege, all entities are considered hostile. Before providing "access," every request is checked, users and devices are verified, and permissions are monitored. This "access" is reevaluated every time something changes, like the user's location or accessed data.
In case breaches occur, zero trust reduces the accessibility of the stolen credentials or blocks the hacker's path by buying time for the users and systems to respond and minimize the possibility of attack. This is done with Zero Trust's limiting the radius capability.
The Zero Trust's limiting radius means that the companies utilizing traditional network-based segmentation are risk-prone, while identity-based segmentation allows the least privilege principles. With this type of segmentation, the credentials used by service accounts must have limited access to the resource level.
Many breaches happen when these accounts are overly privileged due to not being monitored carefully; thus, Zero Trust ensures that the security is layered and identity-based.
3. Assists with compliance management
Zero trust disconnects all users and workload connections from the internet to avoid exposure or exploitation. Due to this isolation, audits reveal fewer problems, making it easier to demonstrate compliance with privacy laws and regulations (such as PCI DSS and NIST 800-207).
Using fine-grained restrictions, zero trust micro-segmentation can partition regulated and non-regulated data, allowing you to set boundaries around sensitive data (such as credit card information or backups). This results in greater visibility and control during audits and data breaches.
The Zero Trust's compliance support benefits auditors and organizations going through audits. It simplifies the process as auditing is critical for companies and individuals dealing with compliance, and Zero Trust allows fulfilling it.
The policies usually ask the organizations to prove their usage, storage, and data collection for compliance. Zero trust gives auditors the necessary guarantee about the data in the organization's systems. In addition, it provides information about the apps and devices that have access to it and the storage location.
4. Zero Trust Authentication with Single Sign-On (SSO)
Currently, most SaaS providers support SSO integration. This means enterprises can centralize identity management instead of building a separate store for identity data. Make sure that when you choose a SaaS solution, it supports SSO in a way that works with your identity management system.
For an identity management system to work, it must consider how dynamic the business is. As jobs change and people come and go, so make the access rules for employees. One way to solve this problem is to connect your identity management system to an HR system that is a reliable source of employee roles and responsibilities. Once the HR system and SSO provider are both live, changes to employees are automatically sent to the SSO provider, and permission decisions are automatically made in the integrated SaaS application.
Using SSO Zero trust authenticates to provide access to all applications and assets. A token or indication validates their transparently visible identity whenever the user wants to enter an application. Applying SSO, the passwords are never asked for a login, while with the Zero Trust model, the users can access it based on their identity as it is the safest way to verify an individual.
5. It promotes SSPM (SaaS Security Posture Management)
SSPM (SaaS Security Posture Management) is a new security category that can automatically evaluate the security posture of a SaaS application, find security flaws, and help administrators set up secure environments. The main goal of SSPM is to keep data safe and prevent unrecognized logins into SaaS services without permission.
The ability of SSPM systems to enforce the principle of least privilege is one of the reasons why they are vital for zero trust. It is highly typical for apps to issue excessive rights, which gives users access to data or actions they do not require for their day-to-day role.
After a user has been authorized, determining the breadth of the application and the data they should be permitted to view at any time is essential to access control. This level of granularity is required for zero trust access to work effectively.
SSPM technologies allow a to keep an eye on all of its SaaS applications and see where they might be vulnerable. They can also suggest ways to improve security and, in some cases, automatically fix weak configurations.
In the zero-trust security model, every user is checked and proven to be who they say they are using a combination of authentication methods (multi-factor authentication). Using layered and secure authentication, limiting and watching network traffic, and keeping credentials safe becomes easier. Devices are still password-protected, so only authorized users can access them.
How Zluri Helps Improve SaaS Security?
Zluri’s SaaS management platform provides enterprises with comprehensive management of their SaaS apps. It helps you improve your SaaS security by discovering the SaaS apps used in your organization. It enables businesses to automate repeated tasks, such as employee onboarding and offboarding, as well as compliance monitoring.
Here are a few features of Zluri that help you improve your SaaS security:
1. Centralized SaaS Inventory
One of the most underrated parts of access control is the idea of centralization. IT teams can monitor users, programs, databases, data flows, and other system parts when access control is centralized.
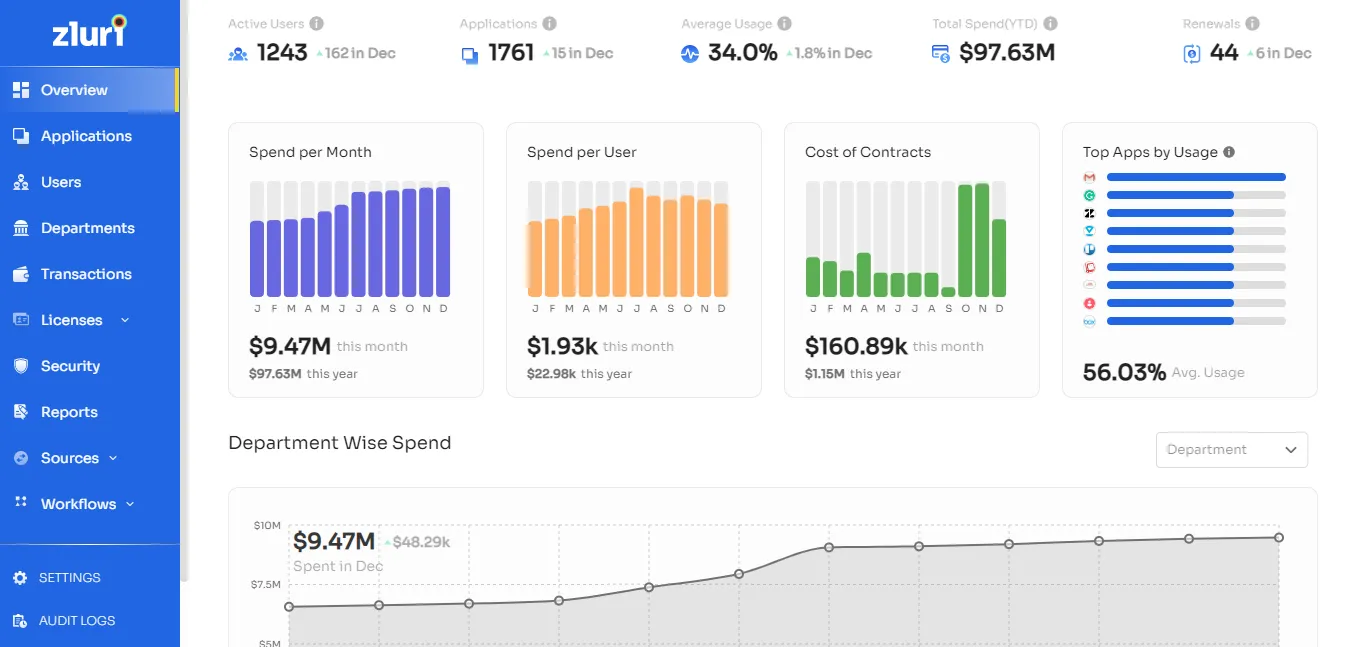
It is hard for previous identity management solutions to give the unified view needed to handle all the information simultaneously. Because of this, businesses need a way to keep track of user identities, get all the information, and manage everything from one place.
IT teams should find a way to keep track of user identities in one place. To do this, they should establish an identity security system. For example, Zluri is a cloud-based SaaS management platform that helps keep an accurate inventory of SaaS services. It uses nine different discovery methods.
It gives a complete picture of all SaaS apps and insights in real-time. Through Zluri's centralized model, access to resources and applications, user behaviour, and tracking unusual events can all be kept an eye on.
2. Role-Based Access Control
"Role-based access control" means limiting the employee's access based on their role in the business infrastructure. Implementing RBAC (Role-Based Access Control) does not provide sole individual control over a certain activity. However, businesses are safer when roles are split up because attacks on a single account are less likely to affect the whole system.
For example, a regular worker in an accounting office does not need to be able to access digital financial accounts. So, that person can be stopped from getting into those accounts. Role-based access control not only helps with identity security and cybersecurity but also helps with business processes.
Zluri makes it easy to control, monitor, and manage programs by giving users and devices granular control over the access they are given. As part of the best practices for access management, businesses should give their employees different jobs. This will help figure out who can do what within the organization.
3. Gives Least Privilege Access
Zluri's least privilege principle says that employees should only be able to see and use the information and resources they need to do their jobs. The role-based access model puts more emphasis on identity governance, while the principle of least privilege emphasizes the initial permissions that are given.
One of the best things about the principle of least privilege is that if something terrible gets into an organization, it will cause less damage.
For example, if a system is infected with malware and is part of an organization that follows the principle of least privilege, it won't be able to spread to other devices. This means that viruses, worms, and rootkits are less likely to be run because most other employees need admin rights to install them.
4. One-click De-provisioning
Zluri keeps the company's data safe by removing former employees from all the apps they use. Instead of just taking away access to their SSO or Google workspace, you can take away access to all the apps the employee had access to. This keeps the organization's data safe from any potential danger.
Zluri takes the data back up for those apps while cancelling the user's licenses so that the admin can give it to the new owner.
For example, it keeps track of users' sign-in logs, audit logs, and access logs, as well as the apps to which they have access, the level of permissions they have for using those apps, and the level of access logs they have. If the user still has access to any apps or has yet to be deleted, Zluri will let you know that they can still use the app.






.png)


.svg)














