Your compliance team wants quarterly reviews. Your security team wants it monthly. You can barely handle the annual. Everyone's right—and everyone's wrong.
- The compliance team is looking at SOX requirements that mandate quarterly reviews for financial systems.
- The security team is looking at privileged accounts that drift fast and create breach risk.
- You're looking at 149 person-days of effort per review cycle and thinking "we can't do this every month."
Here's the problem: Organizations try to apply one review frequency across all access. That's like using the same maintenance schedule for your car's oil (every 3,000 miles) and your tires (every 50,000 miles). Different components wear at different rates and need different service intervals.
The answer isn't picking a frequency and applying it everywhere. It's building a risk-based framework where review frequency matches the actual risk and compliance requirements for different types of access.
Why One Review Frequency Doesn't Work
Most organizations fall into the compliance calendar trap. A compliance framework requires quarterly reviews, so they schedule quarterly reviews for everything—all 50 applications, all 1,000 users, all access types from read-only viewer to super admin.
This creates massive inefficiency. They're reviewing low-risk, read-only access to a project management tool with the same frequency as admin access to production databases.
The first barely needs annual review while the second probably needs monthly.
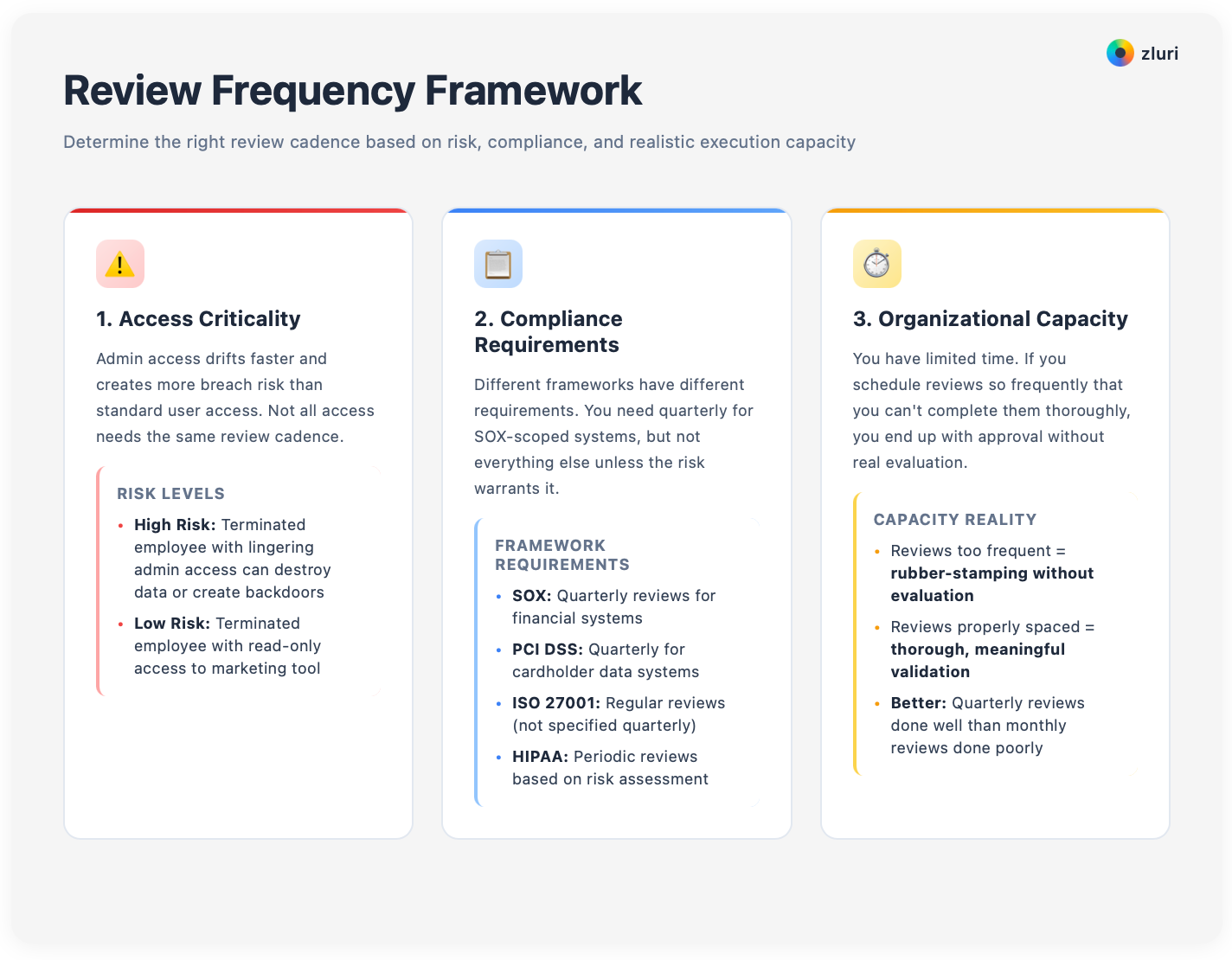
Three factors should determine your review frequency: Access criticality, compliance requirements, and organizational capacity.
Access criticality matters because admin access drifts faster and creates more breach risk than standard user access. A terminated employee with lingering admin access can destroy data or create backdoors. A terminated employee with lingering read-only access to a marketing tool is low risk. These don't need the same review cadence.
Compliance requirements vary by framework. SOX requires quarterly reviews for financial systems. ISO 27001 requires regular reviews without specifying quarterly. PCI DSS requires quarterly for systems handling cardholder data. HIPAA requires periodic reviews based on risk assessment. You need quarterly for SOX-scoped systems, but you don't need quarterly for everything else unless the risk needs it.
Organizational capacity is finite. You have limited time. If you schedule reviews so frequently that you can't complete them thoroughly, you end up with approval without real evaluation. Better to do quarterly reviews well than monthly reviews poorly.
The cost of wrong frequency cuts both ways.
Too frequent and you spend 149 person-days every month instead of every quarter. Reviewers get review fatigue and start clicking "approve all" without actually evaluating. Real violations get missed because the process is so frequent it becomes routine.
Too infrequent and you create compliance gaps when auditors expect quarterly but you're doing annual. Security drift piles up—that terminated employee's admin access stays active for 9 months instead of 3. Breach risk grows as violations stack up between reviews. When violations finally get discovered, there are hundreds instead of dozens.

The solution is matching frequency to risk.
The Risk-Tiered Review Framework
Here's a four-tier framework that balances security, compliance, and operational capacity. We've seen this structure work across organizations from 200 to 5,000 employees.
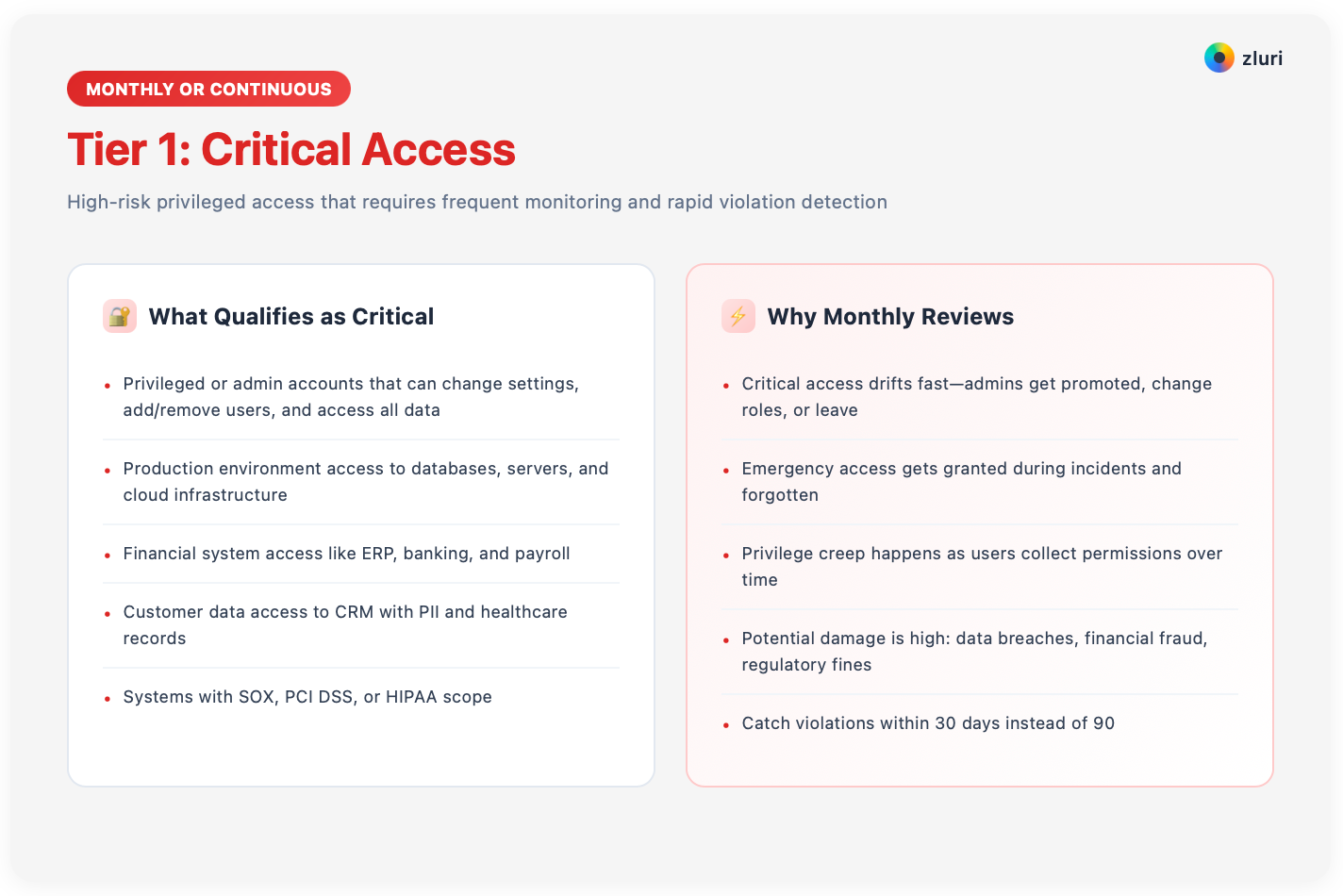
Tier 1: Critical Access (Monthly or Continuous)
Critical access includes privileged or admin accounts that can change settings, add or remove users, and access all data.
Production environment access to databases, servers, and cloud infrastructure.
Financial system access like ERP, banking, and payroll.
Customer data access to CRM with PII and healthcare records. Systems with SOX, PCI DSS, or HIPAA scope.
Monthly reviews make sense because critical access drifts fast. Admins get promoted, change roles, or leave the company. Emergency access gets granted during incidents and forgotten. Privilege creep happens as users collect permissions over time.
The potential damage from misused critical access is high—data breaches, financial fraud, regulatory fines, reputation damage.
Monthly reviews catch violations within 30 days instead of 90.
For organizations with continuous monitoring capabilities, these reviews can be even more frequent—flagging suspicious changes in real-time rather than waiting for scheduled reviews.
What a monthly review actually looks like: You're not re-reviewing all 1,000 employees monthly—you're reviewing the 50-80 people with privileged access to critical systems.
That's manageable.
Focus on changes since last review—new admin grants, inactive admin accounts with no login in 30+ days, admins who changed roles, admins whose manager left, and any policy violations flagged by monitoring.
Tier 2: Standard Business Access (Quarterly)
Standard business access includes standard application access to SaaS tools like Slack, Asana, and HubSpot. Department-level permissions where the Marketing team has access to marketing tools. Most collaboration and productivity tools.
It mainly includes systems with sensitive data or compliance scope.
Quarterly strikes the right balance for this tier. It's where most of your access lives—the bulk of your 100 applications and 1,000 users.
It's frequent enough to meet most compliance frameworks and catch violations before they pile up excessively. It's infrequent enough that you and reviewers can complete thorough reviews without fatigue.
Quarterly reviews also align with business cycles.
Q1 often follows year-end employee turnover.
Q2 catches spring hiring and role changes.
Q3 captures summer interns and contractors.
Q4 prepares for audit season and year-end cleanup.

What quarterly review looks like: Full review of all standard business access. All users, all applications in Tier 2. Managers review their team's access. Application owners review privileged access to their apps.
You run the process, make the changes, and save evidence for auditors.
Tier 3: Low-Risk Access (Semi-Annual or Annual)
Low-risk access includes read-only or viewer access where users can see content but not modify it. Limited-scope applications like single-department tools with fewer than 20 users. Internal documentation systems. Tools without sensitive data, financial access, or compliance requirements.
Semi-annual or annual reviews work because low-risk access doesn't change much and creates minimal security impact if misused. A former employee with read-only access to an internal knowledge base isn't a breach risk.
Reviewing this access quarterly is inefficient—it checks a box without reducing actual risk.
Semi-annual or annual reviews free up your time to focus on high-risk access. You're still reviewing these systems, just less frequently. If risk goes up—say the tool starts storing customer data—you move it to Tier 2.
Low-risk reviews are often combined with another review cycle for efficiency. During Q2 and Q4 standard reviews, add a section for Tier 3 access. Since low-risk access is typically concentrated in a few applications, it adds minimal reviewer workload.

Tier 4: Compliance-Driven (Framework-Specific)
Some systems are explicitly scoped by compliance frameworks. These may overlap with other tiers but compliance dictates minimum frequency.
SOX (Sarbanes-Oxley) requires a quarterly minimum for access to financial systems. This includes ERP systems, general ledger, accounts payable/receivable, banking platforms, and payroll systems. Can't negotiate on frequency—quarterly is the standard.
PCI DSS (Payment Card Industry) requires quarterly minimum for systems that store, process, or transmit cardholder data. This includes payment gateways, e-commerce platforms, POS systems, and any database with credit card information.
ISO 27001 requires "regular review of user access rights" without specifying quarterly. Annually is generally acceptable, but higher-risk systems should be quarterly. Your external auditor will guide interpretation.
SOC 2 typically requires quarterly for critical systems, but varies by Trust Service Category and your control design. Work with your auditor to define expectations.
HIPAA requires "periodic review" based on risk assessment. High-risk systems like EMR and patient databases typically get quarterly reviews. Lower-risk systems annually.

How to handle overlap: If a system is both Tier 1 (critical access) and Tier 4 (SOX-scoped), review it at the highest frequency requirement—monthly for critical access meets the quarterly SOX requirement. Document that your risk-based approach exceeds compliance minimums.
Four User Access Review Frequency Models
Different organizations need different approaches. Here are four models with guidance on when to use each.
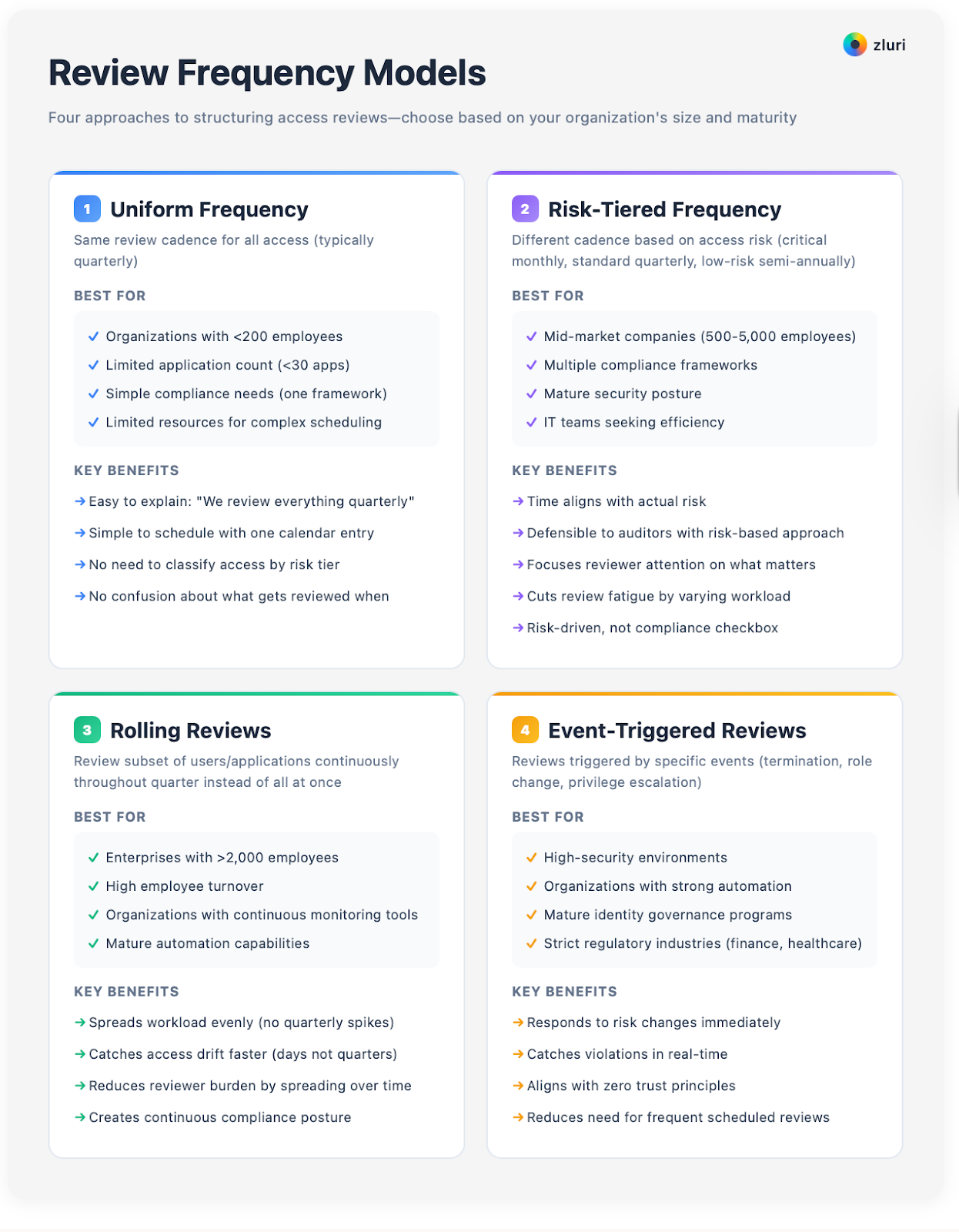
Model 1: Uniform Frequency
This model uses the same review cadence for all access. Most commonly quarterly for everything.
Best for small organizations with fewer than 200 employees, limited application count under 30 apps, simple compliance needs like one framework, and limited resources for complex scheduling.
The main advantage is simplicity.
Easy to explain to reviewers—"we review everything quarterly."
Simple to schedule with one calendar entry that repeats every quarter.
No need to classify access by risk tier. No confusion about what gets reviewed when.
The downside is massive inefficiency at scale. Organizations review low-risk access as often as critical access. You spend time on low-value reviews instead of focusing on high-risk areas. Reviewer fatigue leads to approvals without thorough evaluation.
Once you exceed 50 applications or 200 employees, uniform frequency becomes unsustainable. The effort required for quarterly reviews of everything exceeds what you can deliver without automation.
Model 2: Risk-Tiered Frequency
This model uses different review cadence based on access risk classification. Critical access monthly, standard quarterly, low-risk semi-annually.
Best for mid-market companies with 500-5,000 employees, multiple compliance frameworks, mature security posture, and IT teams seeking efficiency.
The benefits are clear. Your time aligns with actual risk. Defensible to auditors—"we review high-risk access more frequently than frameworks require." Focuses reviewer attention on what matters. Cuts review fatigue by varying workload. Shows leadership that the process is risk-driven, not a compliance checkbox.
The tradeoffs:
Requires upfront work to classify access by risk tier.
More complex scheduling—you need calendars for Tier 1 monthly, Tier 2 quarterly, Tier 3 semi-annually.
Reviewers need training on why different systems have different frequencies.
Some auditors may question non-uniform approaches, though this is rare if risk rationale is documented.
Start by classifying your top 20 most critical applications as Tier 1. Everything else defaults to Tier 2 initially. After your first two review cycles, identify true low-risk access and move to Tier 3. Gradually refine tiers based on actual risk patterns you observe.
Model 3: Rolling Reviews
This model reviews a subset of users or applications continuously throughout the quarter instead of reviewing everything at once.
Best for enterprises with over 2,000 employees, high employee turnover, organizations with continuous monitoring tools, and mature automation capabilities.
Rolling reviews spread your workload evenly instead of creating quarterly spikes. They catch access drift faster—violations discovered within days, not quarters. They reduce reviewer workload by spreading reviews across time. They create continuous compliance posture instead of point-in-time snapshots.
The challenges:
Complex to track and need strong tooling to manage rolling schedules.
Harder to align with quarterly audit requirements, though you can map rolling reviews to quarterly periods.
Requires mature processes—don't try this until you've mastered standard quarterly reviews.
Can create confusion about "when is my review due?"
For example, instead of reviewing all 4,000 employees in Q1, review 1000 employees in January, 1000 in February, 1000 in March, 1000 in April. By the time you finish the 4,000th employee, it's time to start the 1st employee again—creating continuous coverage.
Model 4: Event-Triggered Reviews
This model starts reviews based on specific events rather than calendar schedule. Termination triggers immediate access review. Role change triggers access review within 5 days. Privilege escalation triggers review before it's granted.
Best for high-security environments, organizations with strong automation, mature identity governance programs, and industries with strict regulatory requirements like financial services and healthcare.
Event-triggered reviews respond to risk changes faster than any scheduled review model. They catch violations immediately rather than waiting for scheduled review. They align with zero trust principles. They cut the need for frequent scheduled reviews if events are comprehensive.
The downsides:
Unpredictable workload means you can't plan "we'll spend 40 hours in Q1."
Requires robust automation to detect events and trigger workflows.
Complex to set up event rules properly.
You still need baseline scheduled reviews for full coverage.
Common triggers include employee termination requiring review of all access within 1 hour. Contractor end date triggering review 7 days before contract expires. Role change requiring review within 5 business days.
Privilege escalation request needing review before granting. Extended leave over 60 days requiring review and access suspension. Return from leave needing review before restoring access. Manager change requiring review of inherited team access. Security incident triggering review of all access for affected users.
The Hybrid Approach (Recommended)
Most mature organizations combine models. They use risk-tiered frequency for scheduled reviews—monthly for critical, quarterly for standard. They add event-triggered reviews for specific scenarios like terminations and privilege escalations. They use rolling reviews for their largest applications like Salesforce with 500+ users reviewed continuously.
The key is matching the model to your organization's size, complexity, risk profile, and operational capacity.
Start simple with Model 1 (uniform quarterly) if you're doing reviews for the first time. Move to Model 2 (risk-tiered) once you've completed 2-3 cycles and understand which systems are truly high-risk.
Consider Model 3 (rolling) or Model 4 (event-triggered) only after you've mastered risk-tiered reviews and have strong automation in place. Partner with Security to define risk tiers and with Compliance to make sure your frequency approach meets audit requirements.
Building Your Review Calendar
Once you've chosen your frequency model, you need an operational calendar. Here's a sample annual calendar for the risk-tiered model:
January brings Tier 1 (Critical) monthly review, Tier 2 (Standard) Q1 quarterly review, and Tier 4 (Compliance) Q1 quarterly review. Priority: Post-holiday cleanup and terminated employees.
February focuses on Tier 1 monthly review only. Use freed capacity for remediation backlog or discovery improvements.
March handles Tier 1 monthly review only. Prepare for Q2 review by updating reviewer lists and refining discovery.
April includes Tier 1 monthly review, Tier 2 Q2 quarterly review, and Tier 4 Q2 quarterly review. Priority: Role changes and spring hiring additions.
May covers Tier 1 monthly review only.
June tackles Tier 1 monthly review only. Mid-year audit prep includes evidence compilation and process documentation.
July brings Tier 1 monthly review, Tier 2 Q3 quarterly review, Tier 3 (Low-risk) semi-annual review, and Tier 4 Q3 quarterly review. Priority: Summer contractors and interns.
August handles Tier 1 monthly review only.
September covers Tier 1 monthly review only. Prep for Q4 by validating compliance scope and confirming reviewer availability.
October includes Tier 1 monthly review, Tier 2 Q4 quarterly review, and Tier 4 Q4 quarterly review. Priority: Year-end audit prep and contractor expirations.
November focuses on Tier 1 monthly review only. Audit evidence preparation.
December tackles Tier 1 monthly review only. Year-end compliance reporting.

The workload distribution shows 4 high-workload months when quarterly reviews coincide with monthly critical reviews, and 8 low-workload months with only monthly critical reviews. This creates a manageable rhythm where you're not drowning every month, but you're maintaining continuous oversight.
Making Periodic Reviews Sustainable
Frequency is only sustainable if the process is efficient. We've learned from hundreds of IT teams that trying frequent reviews without automation leads to exactly the problems described earlier—review fatigue, incomplete evaluations, and eventual abandonment of the process.
Complete visibility using 9 discovery methods is the foundation. You can't review what you don't know exists. Traditional IGA platforms only discover apps with IDP/SSO integrations.
Comprehensive platforms use 9 discovery methods that ensure your periodic reviews cover 95%+ of actual access, not just 40% visible through SSO. Those nine methods include SSO integration, finance system data, browser extensions, desktop agents, MDM, CASB, HRMS integration, network monitoring, and employee self-reporting.
Group-based reviews multiply efficiency. Reviewing individual users doesn't scale. Group-based access reviews let you validate group membership once, then automatically validate all group members—this approach delivers 10-15x efficiency for monthly critical access reviews.
Closed-loop remediation prevents bottlenecks. Decisions are useless if changes take weeks to happen. Platforms with closed-loop remediation make revocations via API immediately after approval—minutes instead of weeks. This is critical for monthly reviews where you can't afford 18-day remediation cycles.
Contextual AI risk scoring focuses attention. Monthly reviews of critical access might involve 500 access items. AI pre-flags the 50 high-risk items like inactive accounts and excessive permissions so reviewers focus on what matters instead of approving everything without detailed evaluation.
Continuous monitoring catches violations in real-time. For truly critical access, consider continuous monitoring that flags violations immediately instead of waiting 30 days for monthly review. If a terminated employee still has production access, you need Security alerted immediately—not discovering it at next month's review.
Don't increase review frequency without improving review efficiency. If your quarterly reviews take 149 person-days manually, monthly reviews aren't sustainable.
Add automation first—get your quarterly reviews down to 55 person-days—then consider monthly reviews for critical access. Partner with Security and Compliance to justify the investment in platforms that enable efficient frequent reviews.
Proving the Value of Risk-Based Frequency
Leadership and auditors may question why you're not reviewing everything with the same frequency. Here's how you defend the approach.
The risk-based rationale is straightforward: "We review critical access monthly because it creates the highest breach risk. This exceeds compliance requirements, which only mandate quarterly. We review standard access quarterly to meet compliance frameworks and catch violations before they pile up. We review low-risk access semi-annually because the security impact of these violations is minimal and our resources are better spent on high-risk areas."
The efficiency gains tell a compelling story: By tiering reviews, organizations cut person-days from 149 per cycle to 55—a 63% improvement.
We're now reviewing critical access 4x more frequently than we did under uniform quarterly reviews, while reducing overall time investment.
This is more security for less cost.
The audit defense is clear: "Our risk-tiered approach meets or exceeds all compliance requirements. SOX systems get quarterly reviews as required. Critical access gets monthly reviews, which exceeds the quarterly minimum. Low-risk access gets semi-annual reviews, which still meets ISO 27001's 'regular review' requirement. We've documented our risk classification criteria and can show that review frequency aligns with actual risk."
Research shows that 68% of organizations with mature access governance programs use risk-tiered review frequencies rather than uniform quarterly. The approach aligns with industry best practices.
Getting Started with Periodic Access Reviews
If you're currently doing annual reviews or nothing at all, here's your path forward.
Phase 1 (Months 1-3) establishes the quarterly baseline. Start uniform quarterly reviews for everything. This creates your compliance baseline and gives you data on effort required, violations discovered, and process gaps. Don't try to be sophisticated yet—just complete a review cycle successfully.
Phase 2 (Month 4) identifies critical access. After your first quarterly review, classify your access into tiers. Which 15-20 applications are truly critical? Which users have privileged access? This becomes your Tier 1 for monthly reviews.
Phase 3 (Months 5-7) starts monthly critical reviews. Begin reviewing Tier 1 critical access monthly while keeping quarterly for everything else. This shows that more frequent reviews are manageable for high-risk areas.
Phase 4 (Months 8-12) optimizes and expands. Move low-risk access to semi-annual cadence. Add automation to cut effort. Consider event-triggered reviews for terminations and privilege changes. Measure efficiency gains and show ROI to leadership.
By month 12, you'll have a mature, risk-based review program that's efficient, effective, and defensible to auditors.
The Right Frequency Reduces Risk Without Overwhelming IT
One size doesn't fit all. Critical access needs frequent review while low-risk access doesn't. Organizations doing periodic reviews well are the ones who've matched frequency to actual risk.
The framework breaks down to four tiers:
Tier 1 (Critical) gets monthly or continuous review.
Tier 2 (Standard) gets quarterly review.
Tier 3 (Low-risk) gets semi-annual or annual review.
Tier 4 (Compliance) follows framework-specific minimums.
The result is more security with less effort. You catch critical violations within 30 days instead of 90. You review low-risk access appropriately, not excessively. Your time focuses on what matters.
Leadership can see that the process is risk-driven, not a compliance checkbox. Auditors see that your frequency exceeds minimum requirements.
The question isn't "how often should we review?" but rather "how often should we review this specific type of access?" Match the cadence to the risk, and periodic reviews become sustainable.
Get Started
Book a Demo to see how automation enables efficient periodic reviews






.png)


.svg)














