
6 Ways To Implement Least Privilege with Identity Governance
Data breaches and cyber threats are on the rise, making IT managers need to adopt robust security measures to safeguard potential data. A critical aspect of strengthening security is adopting the principle of least privilege, which restricts user access rights to the minimum privileges necessary for their tasks.
However, managing and enforcing least privilege policies can be complex, especially in large and dynamic environments. To successfully implement least privilege, you can leverage the power of modern identity governance solutions.
Implementing least privilege with modern identity governance is vital for bolstering your data security and maintaining a robust security posture throughout your organization.
By granting users only the minimum access privileges necessary for their roles, you can limit the exposure of sensitive data and critical systems. This approach enhances security by minimizing attack surfaces and improves operational efficiency by defining precise access rights.
The principle of least privilege (PoLP) is a fundamental concept in cybersecurity that grants users the minimum access privileges necessary to perform their specific tasks or responsibilities. By adhering to this principle, your IT teams can effectively reduce the attack surface and limit the potential damage caused by unauthorized access or malicious activities.
Implementing PoLP involves carefully analyzing user roles, defining granular access controls, and regularly reviewing and adjusting permissions to ensure alignment with job responsibilities.
This proactive approach to security helps you mitigate the risks associated with insider threats, external attacks, and accidental data breaches. By providing users with only the essential access privileges they need, your IT teams can enhance the overall security posture and protect sensitive information from unauthorized access or misuse.
Furthermore, least privilege with modern identity governance enhances compliance with industry regulations and data protection standards like GDPR and HIPAA, by implementing granular access controls and limiting privileges to safeguard sensitive data.
It also enables effective auditing and monitoring through centralized identity management, providing better visibility into user activities. This allows you to promptly track and respond to suspicious behavior, ensuring accountability and supporting incident response efforts.
This blog post will discuss a few effective ways to implement least privilege with the help of modern identity governance, empowering your IT teams to protect critical assets.
6 Effective Ways To Implementing Least Privilege With IGA
Implementing these ways helps you establish a least privilege model that limits access to what is required for specific roles and tasks. This reduces the risk of unauthorized access, minimizes the potential impact of security breaches, and helps you maintain a strong security posture.
Let's explore key ways to implement Least Privilege with modern identity governance:
1. Implement & Embrace Role Based Access Control
An essential factor in attaining the principle of least privilege is role-based access control (RBAC). RBAC assigns users to predefined roles based on their job functions and responsibilities. Each role is associated with a set of access privileges required for that role. By granting access based on roles rather than individual users, RBAC simplifies access management and ensures that users only have the necessary permissions for their roles.
For example, let’s say you are using RBAC to manage access for an HR application. In this case, HR managers can be assigned a role that allows them to update employee details, while other employees are restricted to viewing only their own information.
When formulating your access control strategy, it is considered a best practice to assign users the minimum necessary permissions required to perform their tasks effectively.
Role-based access control (RBAC) serves as a valuable mechanism to maintain alignment between individuals' job functions and their access levels, while also simplifying the process of assigning access. Within a modern identity governance solution, roles can be created and defined, ensuring that users with similar job roles are granted consistent access rights to specific systems.
These roles can be tailored based on responsibilities, departments, projects, and more, providing administrators with an efficient means to allocate appropriate access privileges. By implementing RBAC, your organization establishes a structured approach to achieve the principle of least privilege, enabling the establishment of standardized and repeatable processes for assigning access to resources.
This templated method ensures proper access and promotes simplicity and consistency in managing access rights.
2. Leverage Identity Lifecycle Management
Managing least privilege becomes even more challenging due to the dynamic nature of employment within your organization. New hires, third-party vendors, promotions, department changes, and departures all contribute to the complexity of maintaining proper access privileges. It requires a careful balance of least privilege and instant access to ensure employees have the appropriate access for their roles and only for the necessary duration.
Modern identity governance and administration (IGA) solutions are crucial in enabling IT teams to effectively manage each identity's entire lifecycle. This ensures that identities are not burdened with excessive or unnecessary permissions as employment or contractual status changes, promoting a secure and streamlined access control environment.
Thus, implementing identity lifecycle management (ILM) within an identity governance and administration (IGA) framework is a powerful way to enforce the principle of least privilege. ILM streamlines user access management, automates provisioning and deprovisioning, ensures segregation of duties, and supports compliance requirements. It starts from user onboarding and encompasses provisioning, access management, role-based assignments, and ultimately, user offboarding.
Moreover, by integrating ILM into the IGA solution, you can establish a streamlined and automated process for managing user access throughout their lifecycle. This includes defining user roles, assigning appropriate access privileges based on those roles, and ensuring timely updates or revocations as users change roles or leave the organization.
3. Grant Just-in-Time (JIT) Privileged Access
Maintaining a balance between least-privilege access and employee workflow is crucial for your organization. This can be achieved by leveraging a combination of role-based access control and time-limited privileges. In traditional role-based access control, users are assigned access rights based on their defined roles.
However, there may be situations where users need temporary or elevated access permissions to perform specific tasks or projects. That’s where just-in-time privileges can be helpful. To achieve this, your IT team can replace hardcoded credentials with dynamic secrets or implement one-time-use credentials. Dynamic secrets ensure access credentials are generated on demand and have a limited lifespan.
One-time-use or disposable credentials are unique and valid for a single session or a specific purpose. These mechanisms allow for the temporary elevation of access privileges when necessary without the risk of granting permanent or excessive permissions.
Employing time-limited privileges can prevent privilege creep, which refers to accumulating unnecessary access rights over time. Users are granted increased authority only for the duration required to complete a specific task or short-term project. Once the task is completed or the timeframe expires, the temporary privileges are revoked, ensuring that access permissions align with the principle of least privilege.
Further, this approach balances security and productivity, enabling users to perform their duties effectively without compromising the overall access control framework. It prevents the unnecessary accumulation of privileges, reduces the risk of unauthorized access, and maintains a secure environment that adheres to the principle of least privilege.
4. Continuous Monitoring & Auditing Of All Privileged Access
Implementing continuous monitoring and auditing of privileged access is considered one of the best ways to maintain a strong security posture. By continuously monitoring privileged access, your IT teams can proactively detect any suspicious or unauthorized activities, allowing for timely response and mitigation. Further, regular auditing of privileged access ensures that access rights are aligned with least privilege principles and compliance requirements.
Continuous monitoring involves real-time tracking and analysis of privileged user activities, such as monitoring system logs, analyzing user behavior, and flagging any anomalies or deviations from normal patterns. It also involves tracing individual actions, capturing keystrokes, RDP and SSH sessions, and utilizing automation tools to identify any abnormal activity and promptly alert you of potential issues. This approach helps you identify potential security breaches, insider threats, or unauthorized access attempts promptly.
Simultaneously, regular auditing of privileged access involves conducting comprehensive reviews of access rights, permissions, and entitlements assigned to privileged accounts. This process ensures that privileges are assigned based on job roles, responsibilities, and the principle of least privilege. It also helps identify any excessive or outdated privileges that need to be revoked, minimizing the risk of privilege misuse or abuse. Additionally, ensure that all inactive accounts are closed or deprovisioned to minimize security risks.
By following a continuous monitoring and auditing approach, your IT team can effectively manage and protect privileged access. It provides enhanced visibility into user activities, strengthens overall security, and enables organizations to maintain compliance with regulatory standards. Ultimately, this proactive approach helps you stay one step ahead of potential security threats and ensures a robust privileged access management framework.
5. Maintain Segregation Of Duties
Once access has been granted, it is crucial to establish and maintain order by ensuring that the assigned access rights are appropriate and aligned with the user's role and responsibilities.
To mitigate risks and maintain effective oversight, you need checks and balances in place. Segregation of duties (SoD) is a principle in organizational governance that ensures checks and balances, reducing the potential for unauthorized activities, and enhancing transparency and accountability. But how does it do so?
SoD involves separating critical functions across different individuals, departments, or job functions to prevent one person from gaining excessive autonomy and power.
For instance, a software developer should not have unrestricted access to move code across different environments, nor should someone in the finance department have access to both accounts payable and accounts receivable. By separating duties, organizations reduce the risk of unauthorized activities, conflicts of interest, and the potential for both intentional and unintentional errors.
The purpose of SoD is to establish checks and balances within an organization's operations, ensuring that no single person has the ability to perform incompatible actions that could lead to breaches, errors, or misuse of resources.
By separating duties, you can reduce the risk of unauthorized activities, conflicts of interest, and the potential for both intentional and unintentional errors. SoD is a fundamental control mechanism that promotes transparency, accountability, and the overall integrity of business processes.
If not already in place, modern identity governance solutions offer the capability to enforce Segregation of Duty (SoD) constraints. By implementing SoD, organizations can ensure that identities do not possess conflicting access rights, thereby reducing the risk of unauthorized actions. Additionally, you can evaluate situations in real-time, enabling timely intervention when necessary.
By adopting effective identity governance practices and leveraging the power of SoD, you can maintain control, mitigate risks, and prevent unauthorized activities that could potentially disrupt operations or compromise security.
6. Unlock User Behavior Analytics (UBA)
Unlocking user behavior analytics (UBA) is considered a best practice in modern cybersecurity and it offers several benefits to organizations. By harnessing UBA, your IT teams can gain valuable insights into user activities, detect anomalies, and proactively identify potential security risks.
UBA analyzes patterns, deviations, and contextual information from user actions, allowing for the detection of suspicious behaviors, insider threats, and compromised accounts that traditional security measures may miss. You can even gain real-time insights into potential risks and track critical areas such as application usage, failed login attempts, unused accounts, and external threat data.
This proactive approach helps your IT team stay one step ahead of cyber threats and enables faster incident response. This enhanced threat detection capability empowers organizations to take timely action, preventing security incidents and minimizing the impact of potential breaches.
Additionally, UBA provides you with a scalable and automated form of visibility and control, facilitating the prevention of risky user actions and breach attempts. By adopting UBA as a best practice, you can strengthen your security posture, protect sensitive data and resources, and effectively mitigate risks in today's dynamic threat landscape.
Achieving least privilege is an ongoing endeavor that necessitates the adoption of modern identity governance practices. These practices encompass several essential elements, such as streamlined workflows for users and administrators, role-based access control, identity lifecycle management, and segregation of duties.
To support and enable these practices, you need a reliable and comprehensive platform that ensures compliance, mitigates risks and enhances operational efficiency in your organization. Let me introduce Zluri, an exceptional platform that guarantees your organization's security, compliance, and efficiency.
Implementing Least Privilege Made Easy with Zluri's IGA Platform
In today's interconnected world, managing user access rights and ensuring robust identity governance is a critical challenge for your organization. Introducing Zluri: your advanced solution for modern identity governance and administration (IGA).
Implementing least privilege has never been easier with the advanced capabilities of Zluri's IGA platform. This comprehensive solution empowers your IT teams to efficiently manage user access rights, strengthen security, and ensure compliance with ease.

The platform provides a user-friendly interface and robust features that simplify the process of implementing least privilege. With Zluri, your IT team can define and enforce granular access controls based on roles and responsibilities, ensuring that users have the precise level of access they need to perform their tasks without unnecessary privileges. Further, it helps your IT teams to optimize user access management, and navigate the complex landscape of permissions, roles, and entitlements.
By leveraging Zluri's platform, you can seamlessly manage access permissions, track user activities, and detect potential security risks. The platform enables your IT teams to have a centralized view of user access across the organization, making it easier to identify and remediate any access-related issues promptly.
Wondering how Zluri accomplishes all this & what sets it apart?
The platform boasts exclusive capabilities, including a data engine, automation engine, access certifications, and more, making it stand out from its competitors.
Let's explore its key capabilities, enabling your IT team to effectively manage access privileges, governance, and beyond.

- Robust Discovery Engine Delivers Real-time Insights into User Access Data
Zluri stands out from its competitors when it comes to data discovery, mainly because it operates as a top-notch SaaS management platform. This fundamental aspect grants Zluri a remarkable edge in efficiently pinpointing SaaS application and user access data, presenting your IT team with unparalleled visibility into the access patterns of users.

Zluri uses 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.
Zluri offers powerful methods for your team to effortlessly manage user access to applications, identify active users, assess permissions, and gain valuable app-related insights. To address the vulnerability of identity systems to breaches, Zluri ensures seamless integration and complete control, bolstering your security measures.
With robust integration capabilities covering 50% of popular identity systems and core apps, Zluri streamlines authentication, providing a smooth user experience. Access to over 300+ SaaS apps, real-time data, AI-powered alerts, and API-based integration ensures 100% visibility. Zluri delivers granular-level access data for comprehensive insights into your SaaS ecosystem.
- Powerful Automation Engine Boosts Security & Productivity with Tight Access Control
Zluri's automation engine functions as an effortless autonomous system, revolutionizing your organization's access management workflows. By easily handling access control processes with meticulous reviews and strict adherence to established rules and policies, it elevates your security and productivity to new heights.
This powerful engine operates in two key ways. Firstly, you have the flexibility to define automation rules and triggers that perfectly align with your identity governance policies, ensuring consistent compliance with your predefined guidelines.
Secondly, Zluri empowers you to create personalized access and review workflows that operate autonomously, triggered by specific events. This self-operating governance and orchestration loop not only enhances control over access privileges but also streamlines administrative tasks, unleashing the full potential of your IT management capabilities. With Zluri's automation engine, you can optimize efficiency while maintaining robust security and governance throughout your organization.
Key capabilities of Zluri’s Modern IGA Solution: Autonomous & Automated
- Its ULM Solution ensures Right Access To Right Individuals
In the world of identity administration, access provisioning marks the initial stage, while access revocation serves as the final step. Between these crucial endpoints lies the intricate security and compliance structure that demands vigilant oversight from IT teams. Zluri’s user lifecycle management (ULM) feature solves and simplifies it. It offers a smooth and efficient access provisioning and deprovisioning process, enabling IT teams to effectively manage user access privileges throughout their tenure in the organization.

With Zluri, access provisioning becomes a seamless operation. IT teams can easily onboard new users by automating the process of granting appropriate access rights based on predefined roles and responsibilities. This eliminates manual errors and ensures users have the necessary access to perform their job functions from day one. By automating access provisioning, IT teams can save time, reduce administrative overhead, and enhance overall operational efficiency.
Similarly, Zluri simplifies the deprovisioning process when users leave or change roles within the organization. With just a few clicks, administrators can revoke access rights, ensuring that departing or transitioning users can no longer access sensitive systems or data. This helps prevent unauthorized access and reduces the risk of data breaches that can occur when access rights are not promptly revoked.
By providing a smooth access provisioning and deprovisioning experience, Zluri helps your organization maintain a strong security posture and minimize the risk of access-related vulnerabilities. With efficient access management, your IT team can ensure that users have the right level of access at the right time, while also mitigating the potential risks associated with unused or outdated access privileges.
Zluri's focus on smooth access provisioning and deprovisioning align with best practices in identity governance and administration, enabling you to enhance your security, streamline access management, and improve overall operational effectiveness.
You can find additional information and details here to delve deeper into Zluri's Lifecycle Management.
- Manages Access & Deep Entitlements for 143+ apps
Effectively managing access and entitlements across a diverse range of applications can be a complex undertaking for IT teams. However, Zluri rises to the challenge by offering a robust solution that streamlines access management and deep entitlements for over 150 applications. Seamlessly integrating with popular identity providers and application ecosystems, Zluri enables IT teams to efficiently manage user access and entitlements from a unified interface.

With Zluri, IT admins gain granular control over access rights and entitlements for each application. The platform empowers them to define and enforce fine-grained access policies, ensuring that users have the precise level of access aligned with their roles and responsibilities. This level of control helps mitigate the risk of unauthorized access and strengthens the organization's overall security posture.
Zluri's deep entitlement management capabilities go beyond basic access controls. It enables organizations to manage and monitor entitlements within applications, ensuring that users only have access to the specific features, functions, and data they truly need. This level of granularity allows organizations to enforce the principle of least privilege, reducing the attack surface and maintaining a highly secure environment.
With Zluri, your IT team gains the tools they need to simplify access management, strengthen security, and ensure compliance across your application landscape.
- Ticketless Ad-hoc Access Requests Management
As organizations face the challenge of managing access effectively, the risk of mismanagement becomes evident. Employee transitions to new roles or departments and specific app access needs for particular tasks constantly change access requirements. Unfortunately, the traditional manual method involves multiple steps, leading to days of waiting for app access approvals. Zluri eliminates the time-consuming manual access request process through automation.

To make the access request process ticketless, Zluri offers a self-serve model - The Employee App Store (EAS). EAS is a curated collection of pre-approved applications meticulously selected by your IT team. Embracing a self-serve model, this innovative platform empowers employees with unparalleled flexibility. They can effortlessly choose any application from the app store and gain rapid access without any delays.

Zluri doesn’t stop here! By integrating with HRMS, it stays up-to-date with changes and automatically fetches and presents updated employee data on a centralized dashboard. This integration empowers your IT team to effortlessly access and verify employee details, removing the need for manual efforts. With this streamlined process, access permissions seamlessly align with each employee's current role and responsibilities.
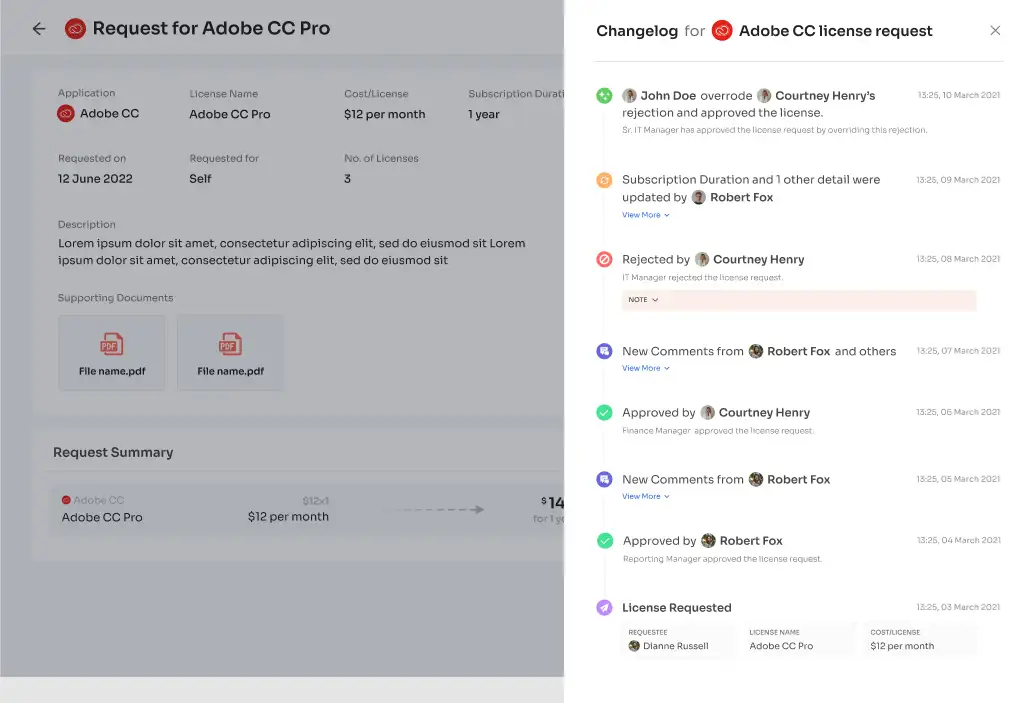
Further, EAS enables your IT admins to review and approve access requests, ensuring alignment with employees' responsibilities and safeguarding against unauthorized access. Higher-level authorities can override lower-level decisions for effective access control.
The process remains transparent with comments for rejection explanations or modifications during approval. Users can track request status and updates through the \"changelog\" feature, enhancing visibility and accountability in access management.
- Enhances security & compliance with regular access reviews\certifications
Zluri's powerful access certification feature empowers your team with comprehensive control over reviewing user access rights, ensuring compliance with industry regulations and internal security policies. By conducting regular access certifications, you can effortlessly validate and evaluate user access privileges, simplifying the certification process. This allows you to seamlessly approve or revoke access as needed.

Consider an e-commerce company that heavily relies on the cloud-based customer support platform called \"SupportConnect\" to efficiently manage and address customer inquiries. The IT team grants access to a group of support agents to assist with a peak sales season expected to last 3 months. However, due to the team's exceptional performance, they efficiently handle the surge in just 1 month.
In this scenario, the team lead or designated approvers can turn to Zluri's IGA Solution for seamless access management. They can review the access permissions granted to the support agents and decide whether to revoke access immediately, given the early completion of the peak season.

On the other hand, if no action is taken, Zluri's system will automatically revoke the access after the initial 3-month period, ensuring compliance and bolstering security without the need for additional intervention. This intelligent approach from Zluri ensures the company maintains strict access control and adheres to compliance regulations effortlessly.

Zluri's automated reviews delivers a remarkable 70% reduction in your manual efforts and expedite the entire review process by up to 10 times. Through intelligent automation, the platform efficiently collects and organizes access data, while analyzing access patterns to deliver a seamless and efficient review experience.
But Zluri doesn't stop there; it offers a host of exclusive features that set it apart from its competitors, going beyond the mentioned access review functionalities.
- Strong Access Control with Continuous Certifications:
Zluri stands out among other IGA tools with its innovative approach to access reviews. When you implement Zluri's IGA solution, you gain the advantage of continuous certifications, enabling precise control over access privileges.
With this proactive practice of regularly auditing and validating access permissions effectively mitigates the risks of unauthorized entries and potential data breaches. Through recurring certifications, access permissions undergo consistent scrutiny, swiftly identifying and resolving any potential security vulnerabilities.
This ongoing process ensures robust access controls, providing unwavering vigilance in safeguarding your organization's sensitive information.
- Streamlined Access Reviews with Scheduled Certifications:
With Zluri's scheduled certifications, you can strategically plan and execute access reviews at specific intervals, ensuring that access permissions receive regular and timely evaluations, eliminating the risk of overlooking critical access issues.

To further streamline the certification process, Zluri offers industry-standard certificate templates. Following recognized guidelines, these templates provide a standardized approach that simplifies certifications for you and your team. By leveraging these templates, you guarantee a comprehensive, precise, and compliant certification process that aligns with established standards.
- Next-Generation Data Security with Real-Time Access Reviews:
Empowering your organization's protection measures, Zluri's IGA solution introduces cutting-edge AI capabilities and real-time access reviews, transforming data security and compliance procedures.

With the prowess of AI, Zluri conducts continuous access reviews, analyzing access patterns, user behavior, and system logs in real-time. This intelligent approach rapidly identifies any abnormal or potentially risky activities, proactively alerting you to security threats and fortifying the safeguarding of sensitive data.
Stay constantly informed about any access rights changes or potential issues, enabling swift responses to access-related concerns and reducing the risk of unauthorized access or misuse. Zluri's real-time access reviews revolutionize data security, providing enhanced protection for your organization's valuable assets.
- Harnessing Intelligent AI for Seamless Compliance:
With Zluri's cutting-edge AI compliance capabilities, your organization gains invaluable insights and expert recommendations, ensuring smooth alignment with industry regulations and standards. By leveraging Zluri's advanced AI technology, the compliance process becomes streamlined, making it easier to meet regulatory requirements and significantly reducing the risk of compliance violations.

Integration of AI-driven intelligence empowers your organization with proactive tools to maintain a secure and compliant environment effortlessly. Thus, you can rely on Zluri's intelligent AI to navigate the complexities of compliance and safeguard your organization's reputation and data integrity.
- Elevating Security and Compliance with Auto-Remediation:
Zluri goes above and beyond access reviews, taking its capabilities to new heights with auto-remediation features. When access violations are detected, Zluri automatically initiates corrective actions without delay, fortifying your organization's security and ensuring compliance.

Through swift measures like revoking access for terminated employees or those with outdated privileges, Zluri effectively mitigates the risk of unauthorized data breaches, enhancing the protection of sensitive information.
This proactive approach strengthens your organization's security posture and guarantees adherence to compliance standards, providing peace of mind in the face of potential threats. With Zluri's auto-remediation, you can confidently take security and compliance to the next level.
Experience the ease and effectiveness of implementing least privilege with Zluri's IGA Platform and take control of your organization's security and compliance efforts.
Book a demo now & experience the power of simplified access governance firsthand!



Go from SaaS chaos to SaaS governance with Zluri
Tackle all the problems caused by decentralized, ad hoc SaaS adoption and usage on just one platform.
.webp)
















.webp)
.webp)





.webp)