As an IT manager, ensuring the security of your organization's systems and data is paramount. One essential solution in achieving this goal is the effective user access review template. This template serves as a structured approach to regularly evaluate and manage user access rights within your organization's IT infrastructure.
Managing user access effectively is paramount for any organization striving to maintain robust cybersecurity practices and regulatory compliance. However, ensuring that access privileges align with job roles and responsibilities can become increasingly challenging as companies grow and evolve.
In this article, we introduce a comprehensive user access review template designed to streamline the process of evaluating and managing user permissions. By implementing regular access reviews using this template, organizations can proactively identify and mitigate security risks, enforce the least privilege principle, and optimize access control mechanisms.
Let's explore how this user access review template can help organizations enhance security, minimize risk, and ensure compliance.
Why Is There a Need for a User Access Review Template?
The need for a user access review template arises from several critical factors in modern organizational management and cybersecurity practices.
Firstly, as businesses grow and evolve, the complexity of user access permissions increases exponentially. With various departments, roles, and levels of access, maintaining a clear overview of who has access to what becomes challenging.
Secondly, regulatory compliance requirements, such as GDPR, HIPAA, or PCI DSS, mandate regular reviews of user access to ensure data privacy and security. Failing to comply with these regulations can result in hefty fines and reputational damage.
Thirdly, the ever-present threat of insider threats, data breaches, and cyber attacks necessitates proactive measures to mitigate risks. A user access review template provides a structured framework for systematically assessing and validating user access rights, identifying any discrepancies or anomalies, and taking prompt corrective actions.
Ultimately, implementing a user access review template helps organizations enforce the principle of least privilege, enhance cybersecurity posture, maintain regulatory compliance, and safeguard sensitive data effectively.
Benefits of User Access Review Template
The various benefits of user access review templates are mentioned below.
- It ensures data security by identifying and addressing potential vulnerabilities. Outdated or unnecessary access rights can pose serious risks, making the system susceptible to breaches or unauthorized data exposure. Utilizing a template can swiftly pinpoint and rectify such discrepancies, fortifying the digital infrastructure against potential insider threats.
- A UAR template enhances regulatory compliance. Stringent data protection regulations like GDPR or HIPAA bind many industries. Failing to manage user access appropriately can result in non-compliance and severe penalties. The template is tangible documentation of compliance efforts, aiding your team in audits and reporting.
- The template simplifies the user access review process, saving valuable time and resources. This efficiency translates into enhanced productivity, allowing you and your team to focus on strategic initiatives rather than being bogged down by administrative tasks.Now, we will explore the essential components that must be included in a user access review template.
7 Key Components To Include In A User Access Review Template
Let’s discuss the components of a user access review template in detail.
1. User information
User information serves as the foundation upon which your user access review template stands. You create a holistic view of users' access needs and responsibilities by gathering and maintaining essential user details, such as full names, roles, departments, and contact information.
This user information acts as a compass, guiding you through the process of evaluating user privileges and rights. It ensures that access permissions align with job roles and responsibilities, mitigating the risks associated with unauthorized access and potential data breaches.
Further, with user-specific data, you can swiftly identify redundant or unnecessary access privileges. This streamlines the review process, freeing up valuable time for your IT team to focus on strategic initiatives rather than manual access management.
2. Access permissions information
Access permission information in a user access review template is the pillar that fortifies your organization against unauthorized access and data breaches. By comprehensively documenting who has access to what, you create a clear audit trail that can be reviewed regularly.
This enables you to proactively identify and rectify discrepancies or unauthorized access attempts, minimizing security risks and potential compliance issues.
The access permission simplifies the user access review process by providing a consolidated view of user privileges across various applications. This streamlines the identification of redundant access, ensuring that only authorized personnel can access critical resources.
Moreover, you can confidently make informed decisions about user access requests/ modifications, minimizing the potential for errors and unauthorized data leaks.
Key Elements of Access Permission Information:
- App Role: Clearly defining each user's role within an application ensures that their access privileges align with their job responsibilities. This element helps you understand the scope of each user's access.
- App Status: Knowing whether an application is active, inactive, or deprecated is vital. You can promptly revoke access for employees who no longer require a specific application, reducing security vulnerabilities.
- Type of App License: Understanding the type of license associated with each user helps optimize cost efficiency. You can ensure that users are allocated licenses that align with their usage patterns, preventing unnecessary expenses.
3. Reviewer information
Reviewer information serves as a vital element in the UAR process. Regular access reviews ensure a clear accountability structure when designated reviewers are identified by their names and emails.
It establishes a chain of responsibility, allowing you to trace back and verify who has reviewed specific access permissions. This strengthens internal control and provides a transparent audit trail that can be crucial for compliance purposes.
Moreover, knowing who is responsible for reviewing access permissions streamlines the workflow. You can facilitate communication between reviewers and access owners, swiftly addressing any questions or concerns. This prevents delays and ensures that access reviews are conducted promptly.
Further, by maintaining a well-documented record of reviewer information, you can easily demonstrate to auditors that access reviews are conducted rigorously and in line with industry standards.
Key Elements of Reviewer Information:
When crafting a UAR template, ensure that the following key elements are included for each designated reviewer:
- Name: Clearly state the full name of the reviewer. This helps in easy identification and ensures that the right individuals are assigned the responsibility.
- Email: Provide the email address of the reviewer. Email is a primary mode of communication, enabling you to send notifications, updates, and reminders related to access reviews.
- Role or Department: Indicate the reviewer's role or department within the organization. This context aids you in understanding the reviewer's relationship with the access permissions being reviewed.
4. Review frequency and timeline
The review frequency and timeline in a UAR template are the cornerstones of your organization's cybersecurity strategy. By clearly outlining how often access permissions are evaluated and setting a schedule for these evaluations, you establish a proactive approach to security.
With technology evolving rapidly, users changing roles, and potential security threats emerging, regular reviews ensure that access privileges remain aligned with employees' responsibilities and any organizational changes.
In addition, it fosters a heightened sense of accountability within your team and among users. Clear guidelines regarding when and how reviews will occur ensure everyone is on the same page, reducing the risk of oversights or delays.
Key Elements of Review Frequency and Timeline:
- Defined Review Intervals: Clearly stipulate how often user access reviews will take place – quarterly, semi-annually, or annually. These intervals provide a consistent framework for your team, making planning and executing the reviews easier.
- Timely Notifications: Include provisions for automated notifications to remind responsible stakeholders about upcoming reviews. This ensures everyone is prepared, reducing the chances of last-minute rushes or missed deadlines.
- Documentation: Documentation adds transparency and accountability to the process. Specify the documentation process for each review. This might involve maintaining records of access changes, reasons for adjustments, and the individuals responsible for authorizing them.
- Review Scope: Clearly outline the scope of the review, detailing which systems, applications, and data repositories will be assessed. This prevents overlooking critical access points and ensures a comprehensive evaluation.
5. Review details
The inclusion of comprehensive review details in a user access review template is an essential part of efficient access management. It provides a clear snapshot of the current state of user permissions, highlighting any deviations from the intended access levels.
Having necessary review details simplifies the task of tracking access permissions, reducing manual effort and enhancing accuracy. The clarity provided by the template streamlines communication across departments and ensures a cohesive understanding of access privileges.
Moreover, the review details allow you to proactively address potential security vulnerabilities, safeguarding the organization's data and systems. By maintaining a thorough record of approved, rejected, modified, and pending access requests, you can efficiently respond to audits and compliance checks.
Key Elements of the UAR Template:
- Number of Users Records Approved: This section quantifies the users whose access permissions have been reviewed and approved, ensuring that all individuals with the right access can seamlessly continue their work without disruptions. This information helps you track progress and maintain a controlled environment.
- Number of Users Records Rejected: Highlighting rejected records is equally important. This section identifies users whose access requests were deemed inappropriate, ensuring that only authorized personnel have entry to critical systems. This step reinforces security measures and prevents potential breaches.
- Number of User Records Modified: Access requirements evolve, and the ability to modify user records is integral to meeting changing organizational needs. This section shows how many user permissions were adjusted, guaranteeing that access remains relevant and aligned with roles and responsibilities.
- Number of Users Records Pending: Access reviews often require additional attention or approval. This category highlights the number of access requests still awaiting a decision, enabling you to identify bottlenecks in the review process and maintain a streamlined workflow.
6. Access change details
Access change details in a user access review template provide a comprehensive view of all changes in user permissions during the review period. By incorporating this granularity level, you can track and validate every access change, minimizing the risk of unauthorized access and potential security breaches.
Further, the clear visibility into access changes empowers you to identify anomalies swiftly, remediate issues promptly, and maintain airtight security and compliance.
Key Elements of Access Change Details:
- Access Revoked: This section highlights users whose access has been revoked during the review period. With this insight, you can confirm that former employees or those who no longer require access are promptly removed, reducing the risk of unauthorized entry.
- Access Modified: Here, you'll find users whose access privileges have been altered in any way. This could include changes in roles, departments, or data permissions. Tracking these changes enables you to ensure that modifications are legitimate and aligned with business requirements.
- No Change: This element showcases users whose access remains unchanged. While seemingly straightforward, this section is crucial for verification purposes. It confirms that no unauthorized adjustments have taken place without your knowledge.
7. Review workflow
User access to resources like SaaS apps can become complex as organizations grow, leading to potential security vulnerabilities and compliance risks. A review workflow acts as a safety net, helping you maintain control and transparency in granting, modifying, or revoking user privileges.
Review workflow ensures access rights are consistently evaluated, aligned with job roles, and up-to-date, minimizing the possibility of unauthorized access or data breaches. Further, it helps you ensure access rights align with industry regulations, avoiding penalties and legal complications.
Steps Involved in a Review Workflow
- Identification of Review Frequency: Determine how often the user access review needs to take place – quarterly, semi-annually, or annually. This frequency should align with your organization's security policies and compliance requirements.
- Access Inventory: Compile a comprehensive inventory of all systems, applications, and data that require user access. Categorize these resources based on their criticality to prioritize the review process.
- User Access Assessment: Collaborate with department heads or managers to identify the appropriate access levels for each user role. Ensure that access rights are aligned with job responsibilities.
- Automate Review Workflow: Utilize a reliable user access review tool that offers automation capabilities. Set up notifications and reminders for reviewers and approvers to initiate the review process.
- Reviewer Assignments: Assign designated reviewers for each resource category. These reviewers should assess and approve access changes based on their understanding of resource requirements.
- Access Review Execution: Reviewers evaluate user access against predefined criteria, considering factors like role changes, job responsibilities, and project involvement. They either approve access, recommend modifications, or reject the access.
Note: Any excessive or inappropriate access should be promptly addressed.
- Documentation and Audit Trail: Maintain a detailed record of each review cycle, including reviewer comments, approver decisions, and any access changes made. This audit trail ensures transparency and assists in future user access review audits.
- Access Reconciliation: Periodically reconcile the approved access rights with the actual access granted in systems. Address any inconsistencies to maintain accuracy.
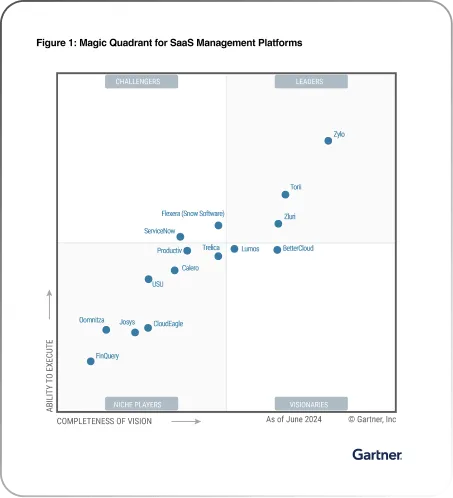
- Continuous Improvement: After each review cycle, analyze the review process's effectiveness. Identify bottlenecks, challenges, or potential improvements to refine the workflow further.Once you have learned about the key components, you'll be in search of a suitable user access review tool that will meet your requirements. One such UAR tool is Zluri. It simplifies the complex task of monitoring user access across your IT ecosystem, giving you the solution to proactively identify and rectify unauthorized access or potential breaches.
How Does Zluri Help You Implement a User Access Review Template?
Ensuring secure user access is paramount for businesses of all sizes. With Zluri's cutting-edge user access review solution, you and your team can streamline the implementation of user access review templates and ensure efficient user permissions management. Let's see how
- Streamlined Review Process: Zluri's user access review solution empowers you to conduct thorough and efficient reviews of user access permissions. By centralizing access data and providing intuitive dashboards, Zluri enables your IT team to quickly identify and address any discrepancies or potential security risks.
- Auto-remediation: Zluri revolutionizes user access management with its cutting-edge auto-remediation functionality. As per Kuppingercole's research and analysis report, unlike conventional reviews, Zluri's dynamic feature takes proactive measures to address access violations swiftly.
In the event of unauthorized access or suspected breaches, it autonomously initiates corrective actions for rapid resolution. Moreover, Zluri's auto-remediation promptly identifies and removes unnecessary access, effectively mitigating security risks in real-time.
- Automated Notifications and Reminders: Zluri simplifies the user access review process by automating notifications and reminders. IT managers can set up automated alerts to notify relevant stakeholders when access reviews are due or when anomalies are detected, ensuring timely action and compliance with security protocols.
- Comprehensive Reporting: Zluri provides comprehensive user access review reporting capabilities that offer insights into user access patterns, compliance status, and potential security threats. IT managers can generate customizable reports to track access review progress, identify trends, and demonstrate compliance to stakeholders and auditors.
- Streamlined Collaboration: Collaborating with stakeholders during the access review process is essential. Zluri facilitates seamless collaboration by providing a centralized platform where all stakeholders can easily access and review relevant information.
- Enhanced Compliance: Maintaining compliance with regulatory requirements is a top priority for IT managers. With Zluri's user access review solution, you can ensure compliance by implementing standardized review processes and documenting audit trails.
Further, to know more about Zluri, Book a Demo Now.
FAQs
What is a periodic user access review?
Periodic user access review involves systematically verifying that a designated group of employees possesses the correct permissions for accessing relevant resources at a given moment. This process ensures optimal security and efficiency within your organization's digital infrastructure.
What is a periodic review of user identities and access rights?
The periodic review of user access encompasses a series of pivotal stages. Initially, we initiate data collection to compile comprehensive insights into user access privileges, roles, and associated duties. Subsequently, our focus shifts to meticulous data analysis, aiming to pinpoint any irregularities, such as instances of over-privileged users or dormant accounts.
What is access certification?
Access certification streamlines the evaluation of user access rights, necessitating validation from a third party to affirm the ongoing necessity of access within a predefined timeframe. Typically orchestrated within identity security platforms or identity governance and administration (IGA) tools, this process ensures meticulous oversight and management of access privileges.
What does access recertification mean?
At the core of access, recertification lies the paramount goal of mitigating unauthorized access risks while curbing the likelihood of data breaches or compliance breaches. Through consistent access reviews, businesses can swiftly pinpoint and rectify any deficiencies or susceptibilities within their access control frameworks, fortifying their security posture.
What is an access management tool?
Identity and access management (IAM) software equips organizations with robust tools designed to authenticate both individuals and devices seeking access, ensuring that authenticated users gain appropriate resource permissions. Serving as a centralized solution, IAM software streamlines identity verification, access management, and detection of security breaches, bolstering overall security measures.









.svg)



























.webp)







.webp)
.webp)





.webp)