Saviynt and CyberArk are well-known IGA platforms that offer a wide range of capabilities. However, they have certain differences too. In this article we’ll compare the similarities and differences between both IGA tools. With the help of these insights you as an IT manager can decide which tool is the perfect fit for your organization.
The increased number of IT assets and resources in organizations and the changing regulatory requirements highlight the importance of using a robust identity governance and administration platform. Additionally, you have different types of users (employees, contractors, vendors, etc.) who will have access to your organization’s critical data and are in a position to compromise its security, either accidentally or intentionally.
That’s why choosing the right IGA tool matters when it comes to managing these users’ identity and data governance to save your organization from data security issues and compliance non-observance. But, it’s equally challenging to select the perfect fit to manage your cloud assets centrally as too many IGA applications are in the market.
Hence, as an IT manager, you need to be aware of the different features of this platform, feature comparison, pricing, and how customers rate them. This article helps you understand the detailed comparison between the two leading identity governance and administration platforms, Saviynt and CyberArk. This can be very helpful for you to base your decision on your requirements and develop an informed decision that protects your precious data, enforces the right policies, and keeps damage-causing IT risks away.
By comparing two different applications and breaking their features down, you can clearly understand their strengths, weaknesses, and unique features, which will tell what aligns better with your requirements.
Detailed Comparison - Saviynt vs. CyberArk - Based On IGA Features & Functionalities
Following are the different features that both Saviynt and CyberArk have to suit your identity governance and administration needs. By the end of this section, you will have a clear idea about the common functionalities of an IGA platform and how they can help you protect your identities, organize and automate access management functions, and manage industrial and regional compliances.
1. Solution categories
- Saviynt: This tool is specialized in identity management and is mainly used for privilege access management, workforce, third-party, and machine identity management, and continuous compliance management. A fair share of its customers has 10k+ employees or more, making it ideal for large organizations with complex identity management needs.
- CyberArk: Similar to Saviynt, CyberArk is also used more by companies with employees higher than 10k. Yet, its custom features are also suitable for entry-level and mid-range organizations. Its primary focus is on privileged access management, identity lifecycle management, secrets management, and cloud security.
2. Identity lifecycle management
Both Saviynt and CyberArk have lifecycle management as part of their IGA tool, allowing you to automate identity and access distribution so that only the right users access your company’s resources at the right time. However, each application functions slightly differently from the others.
- Saviynt: This tool comes with workforce identity management using which you can build your zero-trust foundation and ensure that the cloud entities are accessed only by the authorized and right users. It’s not only suitable for your employees working from the office but the remote workers and their devices are also governed to mitigate risks and breaches.
It does end-to-end identity management where you can smoothly onboard users, provide them with the required level of access to IT resources, manage their identities centrally, as well as access requests and entitlements, and revoke it instantly when users leave. This ensures promptness in user lifecycle management and prevents the inefficiencies, delays, and errors that happen when you manually onboard user identities.
Further, you can create automated workflows to grant access to users and enforce relevant policies. With this, you can easily grant lowest-level access and set up approvals to increase the access levels. When you have to onboard a new user or a device, you can do it within minutes and enable relevant permissions and entitlements, the least level of access required.
You can customize the rules and policies for different types of users; for example, employees and third-party users simultaneously allow convenient access for users.
Also, Saviynt has an RPA-powered bot solution called iBot to discover and onboard applications without any integrations or heavy deployment steps. Thus, you can centrally manage the identities of users, applications, and devices and mitigate every possible insider threat and risk. - CyberArk: CyberArk provides a detailed and step-by-step mechanism to automate the different stages of lifecycle management so that every user can access the right assets at the right time with the right permissions. Like Saviynt, CyberArk identity also works based on the joiner, mover, and leaver processes, based on which the identity is managed across the different phases of the lifecycle.
You can create their identities, add them to directories, and provide access in the joiner phase. In the mover phase, you will update their role in directories. This is when they pick up a new role within the organization, get promoted, or switch to a new department. The leaver phase is when the user leaves the organization; hence their access will be removed, and the user identity is terminated, which again is updated in the directory.
You can use automated workflows to streamline this process which doesn’t require any coding but does every task discussed above seamlessly and on time as scheduled. No matter how complex your identity workflow is, you can automate and orchestrate it with the help of CyberArk. This also means setting triggers and alerts to notify you where any user performs an unusual activity.
CyberArk’s identity management focuses on providing a user-friendly interface for IT teams to create and customize workflows and manage increased workloads if the organization scales. These workflows work based on if or but logic, and with drag-and-drop features, the IT administrator can orchestrate the whole workflow. Here is an example. A new user is onboarded (HRMS, workday, etc.) -> Which group do they belong to - dev -> Give access to developer suites and channels -> Provide required permissions -> Send notifications to the user once access is given.
With the identity directory services of CyberArk, you can manage different types of users centrally, which you can sync from the HRMS platforms and protect their identities. It also allows integrating on-premise and cloud directories (AD, LDAP, or Azure).
Both Saviynt and CyberArk allow IT managers and administrators full visibility and control over the identities in a unified directory without much complication, provide the least privileges, spot and respond to unusual activities, and carry out flexible role-based access management, no matter the number of users.
3. Access management
Both Saviynt and CyberArk allow your IT team to manage access to different levels of users across the organization with the help of the following unique features.
- Saviynt: Saviynt allows you to manage regular and privileged users together with a cloud PAM. It has specific tools like vaulting, secrets management, and just enough access to protect your privileged access resources and not allow users to access or misuse the privileged and highly confidential organization’s data.
The features of Saviynt’s PAM are diverse and cover everything from entitlement management to dashboard access to intuitive reporting. Other options are available to efficiently manage privileged access, including providing time-bound privileged sessions. Basically, Saviynt’s Privileged access management solutions work on the principle of zero-trust, zero-standing privileges.
So, when any user has to use elevated permissions, they can use Just-In-Time access (JIT) to carry out their tasks, which can be done across any platform, application, or device.
Saviynt also has third-party access governance, using which you control and mitigate risks due to outsiders like vendors or non-employees. Hence, you still have their identities and can track what they have access to and maintain time-bound access without onboarding them. - CyberArk: One of the prominent features of CyberArk is Privileged Access Management (PAM) so that you can securely allow access to the privileged entities of your organization. PAM is crucial for IT teams as it involves protecting the organization's most important and confidential data. Hence, not everyone can be left to access it, and even authorized users must be monitored to prevent the mishandling of data.
CyberArk lets you prevent unauthorized users from having privileged access and keep looking for unusual activities by privileged users so that you can prevent risk before it happens. Your team can create a threat detection response to automatically notify IT managers or admins, isolate the identity, or perform any other risk mitigation task. You can further strengthen the authentication of privileged users with Single Sign-Ons and Multi-factor authentication (MFAs).
CyberArk also has Just-In-Time access through which you can grant users elevated privileges only when they need it and not all the time. By adopting this granular approach for privileged assets, applications, and accounts, your team can have full control over these privileged resources, track privileged users and their sessions with higher privileges, and reduce the chances of a cyber-attack by reserving the highly sensitive data for occasions only when it's needed.
4. Access request management
Users must be allowed to request access to applications they need to carry out their tasks efficiently. But this often creates too many complications as users don’t know how to place their access request, delays in approval workflows, or not knowing what applications or what access levels they need. Both Saviynt and CyberArk have access request management and self-servicing platforms. Here is how this feature works.
- Saviynt: This tool has an intelligent access request platform for users where users are recommended tools based on what their coworkers, departments, and peers are using. They can also search and find the application and send it across for approval. Saviynt also has a mobile app from where users can place requests too. It can also integrate with other ticketing systems like ServiceNow to place request any way they want.
Based on the Segregation of Duty policies you have enabled, Saviynt can automatically detect and trigger a warning if a user is requesting access more than what’s required for their role. The best part of Saviynt’s access management is that it uses intelligence to detect dangerous access combinations or privileges and shows the user why they cannot place their request due to the estimated risk. The user can proceed further with a valid justification if they still need access. Thus, your team doesn’t receive requests that, if processed, can lead to unauthorized usage of applications, which further leads to a breach or vulnerability.
To further mitigate the risk, you can set up custom approver workflows that will be responsible for approving or denying access to a user. Saviynt shows the risk possibility to the approver before they make their decision. This is very much needed to strengthen your perimeter against security breaches that happen due to wrong provisioning and strictly enforce zero-trust policy and segregation of duties.
As Saviynt filters access requests before it reaches the IT team’s queues, they can process and provide access quickly and let users work without friction. It’s also easier for the IT teams to create workflows with available templates and place your security checks in the right spots of the access request process. - CyberArk: CyberArk Identity has ways to manage the access requests of your employees, like Saviynt. It allows you to set up approvers, create approval workflows, and allow users to request access through their CyberArk identity user accounts. Users will be able to see the applications the IT admin has published in the CyberArk cloud directory and request access.
IT administrators must also establish roles under which users can be granted access. They should also give approvers rights to make decisions so that they can verify the request, validate it, and approve or reject the request. They can view the incoming requests from their CyberArk identity accounts. Users can be granted two types of access, permanent and windowed. Permanent - when the access will be revoked only when the user leaves the organization, or moves to a different role. Windowed - In this case, access will be granted only for a short duration.
CyberArk has made it easy for both users and IT teams to process access requests seamlessly. It allows users to request application access and gain visibility over the available applications, whereas the IT teams find it easy to create custom approval workflows for each application, set up approvers, and oversee the operations, all in a single place.
5. Security and compliance
Security and compliance management will be your utmost priority when choosing an IGA solution. Here is how both CyberArk and Saviynt ensure data security and maintain industrial standards.
- Saviynt: Saviynt acts as an intelligent IGA platform with better controls for IT teams to allow and manage users accessing the company’s IT infrastructure. With in-depth visibility and segregation of duties across users, you can easily prevent risks and security breaches while strictly maintaining data compliance.
Saviynt doesn’t stop with segregating roles; it also creates a zero-trust environment by allowing no standing privileges for users. Hence, no user can put the company's critical information at risk, and even careless mistakes are prevented. Another feature of Saviynt that enhances your IT security is that it has access certification through which you can review and allow privileged access when the user requests it for a task. Thus, no standing privileges are allowed to any user at any time, further reducing the opportunities for any breach activity.
Let’s see how Saviynt allows you to maintain compliance. It allows you to comply with standards like SOX, HIPAA, PCI DSS, FISMA, and more. You can achieve this by setting up fine-grained access control mechanisms, allowing the least privileges by default, and segregating duties (no two privileges are offered at the same time to any user, which can potentially lead to an access or data violation).
You can prepare documentation for audits easily with the help of Saviynt’s reporting capabilities and dashboards. Hence, you can always stay prepared for internal and external audits.
With Saviynt, you can ensure end-to-end governance as you control both workforce, third-party, and machine identities too from the moment they are onboarded to discarded from the network. - CyberArk: CyberArk ensures that your data remains safe and allows your workforce and third parties to safely access your organization's data while your team controls their privileges at a fine and granular level. It provides a higher level of visibility to the identities of your devices, users, and other third parties and allows you to manage all from a single interface by creating a zero-trust environment for them.
It also prevents insider threats through principles of least privilege, session monitoring and isolation, privileged user monitoring and threat response, and allowing just-in-time access, especially for remote users. Saviynt also has powerful analytics capabilities that instantly generate insights and instantly highlight anomalies in your network. All these ensure that your users have access only to the required entities and not higher than that.
With all the above data controls for privileged and regular access management, CyberArk lets you achieve continuous compliance management and adhere to IT regulations and audit standards.
6. Integrations
App integrations are crucial to save time for your IT team and relieve their manual workload. This means the IGA application can connect with other platforms, applications, directories, and infrastructure, which is to connect with multiple applications and work together. Here is how Saviynt and CyberArk facilitate integrations.
- Saviynt: This tool has many native integrations with which you can connect and extend the identity functionalities. You can connect it with platforms like Salesforce, ServiceNow, Slack, Microsoft Teams, Azure AD, etc, to automate your identity and lifecycle management.
- CyberArk: Similar to Saviynt, CyberArk offers many native integrations to simplify and simplify your identity management. It connects with platforms like Google Cloud, Workday, Microsoft 365, AWS, and more. With these integrations, you can extend the capabilities of your IGA application, protect a wider range of assets, devices, and applications, and enforce custom policies to prevent security issues.
After thoroughly comparing Saviynt and CyberArk, you might have understood which tool best aligns with your IT team's specific needs. However, it's crucial to note that other platforms are also available and worth considering. One such exceptional platform is Zluri, which offers remarkable features that help your IT team simplify the identity governance process.
So, let's have a quick look at how Zluri is a better alternative to Saviynt and CyberArk.
Zluri: A Reliable, Automated & Autonomous Identity Governance & Administration Platform
With a hike in SaaS adoption and work decentralization, managing and reviewing user access has become more difficult for IT teams. As they fail to gain complete visibility into user access which further poses a security threat to the SaaS app data. Fortunately, a modern solution can help your IT team mitigate these issues, i.e., Zluri. Why Zluri? What makes it different from the rest?
Zluri is a modern identity governance and administration (IGA) platform focusing on data security and compliance, which is a concern for most organizations. So to meet these needs and govern your organization's entire user access environment, Zluri offers features like a data discovery engine, automated access reviews, auto-remediation, and more.
That further helps your IT team to gain complete visibility into user access, assisting them to define policies for reviews, remediating access post-review, and more, ensuring effective access governance.
Moreover, it takes a step further by introducing additional benefits, i.e., automating user lifecycle management, allowing your IT team to streamline provisioning, access request management, and deprovisioning processes through automation. By leveraging these features, both your IT team and employees can improve their productivity and efficiency, eliminating the need for manual work.
This is just a glimpse of what Zluri is capable of. The bigger picture is yet to be explored. So, let’s learn about its remarkable capability one by one to understand how Zluri sets itself apart from its competitors and provides an unparalleled solution for effective access governance.
1. Enables Your IT Team To Discover SaaS Stack With Zluri’s Data Discovery Engine
Zluri is better at discovering SaaS apps and user access data than other competitors, as it is primarily a SaaS management platform. This background has provided Zluri with a clear-cut advantage, making it highly effective in discovering accurate SaaS apps and user access data.
How does it identify these data? Well, it uses nine discovery methods, i.e., MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional). As per Kuppingercole's report, by implementing these Zluri’s methods, your IT team gains the ability to explore and identify essential user access details.
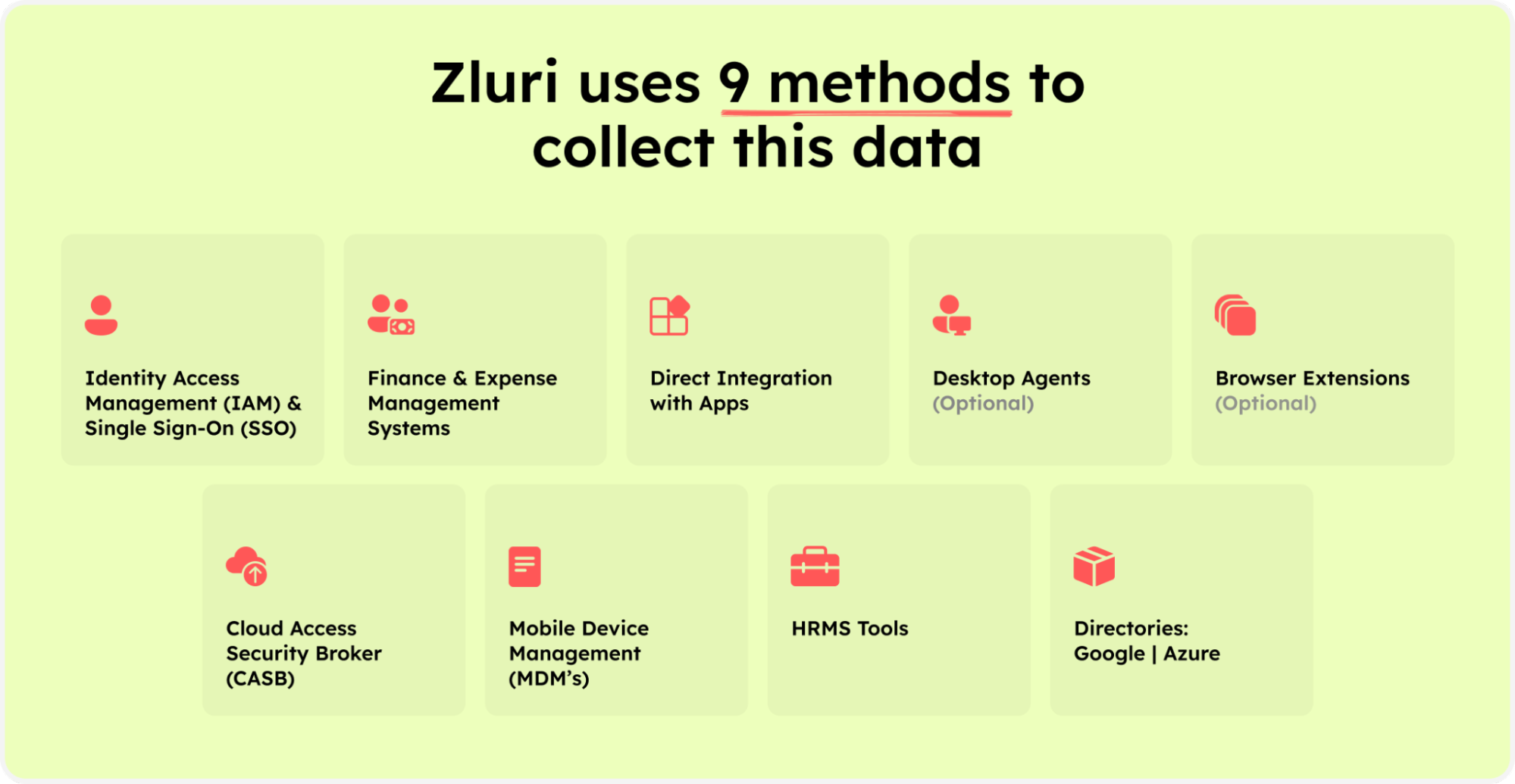
Zluri’s nine discovery methods
They can seamlessly find out which users have access to particular SaaS apps, what all access rights are granted to them, identify the user status (active or inactive), and more.
These curated insights are a game-changer for user access management and SaaS app data security. Armed with such granular knowledge, your IT team finds it easier to conduct access reviews. Additionally, this streamlines the reviewing process, enhancing its efficiency and reducing the likelihood of overlooking critical details, ultimately ensuring that access permissions align precisely with user roles and compliance mandates.
2. Automate The Entire Access Management Process With Zluri’s Automation Engine: Ensuring User Access Aligns With Their Role & Responsibilities
Efficient access management starts the moment an employee joins a company. And the IT team is responsible for ensuring that, starting from day one, the right access to the necessary applications is provided to the new hires. However, when IT teams manage this provisioning process manually, it becomes susceptible to errors, severely impacting productivity and operational efficiency.
- Ensuring Right Access Is Granted To Right Employees On Day 1
So what Zluri does is it links user profiles to their digital identity right at the onboarding stage. So further, when your IT team authenticates a user's identity to provide access during the provisioning process, they can simply cross-verify the information through its centralized dashboard. Thus, this integration enables your IT teams to precisely assign user access in accordance with their specific job roles.
But it doesn't stop there; Zluri automates the entire provisioning process, granting new employees access with just a few clicks. By automating the process, your team can ensure the right access is granted to the right employees with the right level of permissions to necessary apps. That further enhances your employees' productivity by allowing them to start working from day one.
Here’s how your IT team can automate the provisioning process. Well, firstly, your IT team needs to create onboarding workflows. All they have to do is select users they want to grant access to or onboard and apps (you can even choose from recommended apps option), which all apps they want the users to access.
Then, your team can take necessary actions easily by clicking "add an action." Here, they can schedule the workflow and more.
Zluri even provides in-app suggestions, allowing your team to add employees to different channels, groups, or projects or send automated welcome messages.
The actions can vary for different applications and are mentioned under recommended actions. Once all the actions are set, you can directly run the workflow or save it as a playbook for future use.
For added efficiency, Zluri offers automated playbooks (i.e., collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.

Note- Apart from that, your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the finance department employees.
- Manage Your Employee’s Access Request Seamlessly With Zluri’s EAS
Now, we enter a crucial phase where the risk of access mismanagement becomes a concern. As employees shift to new positions, departments, or require access to particular applications for specific tasks, their access needs keep on changing.
Generally, they need to wait for days for approval of their app access requests due to the multistep nature of the manual process. So, this is where Zluri steps in to eliminate the time-consuming manual access request process through automation. Let’s see what it does.
So, to stay updated with the changes, Zluri integrates with HRMS. With the help of this integration, Zluri automatically retrieves and displays updated employee data on a centralized dashboard. By leveraging this integration, your IT team can easily access and verify employee details without manual effort.
This further helps ensure that access permissions align with current employee roles and responsibilities. Whether granting or revoking access, your team can efficiently manage user privileges based on the most up-to-date information available.

It doesn't stop there; Zluri simplifies the access request process by making it ticketless. It offers an Employee App Store (EAS), a self-serve model, a collection of applications pre-approved by your IT team. With this self-serve model, employees enjoy the flexibility of choosing any application from the app store and gaining quick access in no time.

All they need to do is raise a request, and the IT team will verify and review their identity before providing access to the requested application. If approved, employees gain access right away. If access is declined, they receive prompt notifications along with reasons for the decision, any modifications made, or suggested alternatives for the application, all viewable in the "Changelogs."

- Revoke Access When Not Required By The employees
Revoking access from departing employees or those who no longer require certain application access is a critical task for IT teams. Even a single oversight in this process can potentially lead to security breaches, jeopardizing data security.
Zluri recognizes this concern and provides a solution by automating the deprovisioning process. With just a few clicks, your IT team can effortlessly revoke the required or all access from employees without missing any crucial steps. This automation ensures timely and thorough revocation, safeguarding SaaS app data from potential security breaches such as unauthorized attempts.
Furthermore, your team can simply create an offboarding workflow to automate the process. All they need to do is select the users from whom they want to revoke app access, and then they will come across a list of recommended actions (such as signing out users, removing them from org units, and more).
Your team can choose one or multiple actions at once from the list; a point to note is that these actions will be executed post the deprovisioning process. Once all desired actions are added, your team can run the workflow instantly or save it as a playbook for future use.
3. Enables Your IT Team To Automate Access Certification Seamlessly
Now comes the most critical aspect of access management: access reviewing. Ensuring that each user has the appropriate access permissions to apps and data is crucial to maintaining data integrity. So what Zluri does to simplify the reviewing process is it offers exquisite access review capabilities that help your reviewers to review who has access to what. Let’s explore its access review capabilities one by one.
- Unified Access Review
Zluri's unified access review feature enables your IT team to determine which users have access to particular SaaS apps and data. To gain this insight, Zluri utilizes an access directory that centralizes all user access-related data in one centralized place.
With the valuable data points provided by the access directory, such as what access permissions the user has (admins, users, or others), which department or position they are from, and more, your IT team can thoroughly examine users' access privileges and ensure they align with their designated roles.
Furthermore, to keep the operation running smoothly, Zluri's activity & alerts capabilities come as a great help. This feature provides real-time data on users' recent activities and notifies IT teams about new logins or any suspicious actions attempted by unauthorized users.
Armed with all these data points, reviewers can quickly make decisions during access reviews, ensuring that the right users continue to have the right access privileges until the end of their tenure.
- Automated Access Review
With Zluri, your IT team can automate the entire access review process; they create a certification, select the apps and users you want to review, and the rest of the reviewers will review and update you about the compilation via email.
So, by automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%. Now let's move ahead and see how it works.
- Once you gain access to contextual data through Zluri's unified access feature, you can create access rules around these insights. For example, if someone is an admin on Salesforce, you can easily set up a review policy specifically tailored to that scenario.
- Next comes the schedule certification feature, where you can create certifications based on the gathered information. This allows you to take action based on the insights you've gained. For instance, you can use data like last login, departments, user status (active or inactive), and more to make informed decisions during the review process, such as whether the user can carry on with the existing access or need any modification.With Zluri's context-rich insights, your team can proactively take actions that align with the organization's set access management policies. It's a more efficient approach to ensure the right user has the right access, all while keeping your data secure.
So let's see how you can create an access certification in Zluri:
Your IT/GRC team needs to follow the steps below to automate the access certification process:
Step 1: From Zluri’s main interface, click on the ‘Access Certification’ module.
Step 2: Now select the option ‘create new certification.’ You have to assign a certification name and designate a responsive owner to oversee the review.
Step 3: Under Set Up Certification, choose the ‘Application’ option. Proceed further by selecting the desired application for which you want to conduct the review and choose a reviewer (generally, the primary reviewers are the app owners) accountable for reviewing access to that particular application.
After that, you need to select the fallback owner/reviewer; if the primary reviewer is unavailable, the fallback owner can review the user access (you can select anyone for the fallback reviewer whom you think is responsible enough). Also, the reviewers will get notified through the mail that they will conduct a review.
Once you are done selecting the reviewers, you can click on Next.

Step 4: Select Users for Review, choose the users whom you want to review for the selected application. Once you are done selecting the users click on next. You will be able to view all the information related to the users. Then you need to specify the criteria or parameters such as user department, job title, usage, and more. Now click on update and then click on next.
Note: Select those relevant data points only that you wish your reviewers to see while reviewing the access. By filtering the criteria appropriately, you enable your reviewers to make swift and well-informed decisions, streamlining the review process and ensuring efficiency.


Step 5: Now the Configure Action page will appear, basically, here you have to choose actions. These actions will run post the review.
There are three actions:
Approved- once reviewers approve the user access, Zluri won't run any action, and the users can continue with their same access without any interruption.
Rejected- when the reviewer declines or doesn’t approve the user access, you have to run a deprovisioning playbook to revoke that application's access from the user. If the user has access to critical apps, then you can request the assigned reviewer to manually deprovision the user access, or else Zluri will auto-remediate if it’s not critical access.
Modify- In this last case, you again need to create a playbook to modify the user access. However, you need to state whether the access permission needs to be upgraded or degraded.
Step 6: Additionally, you can even schedule the actions by setting up the start date and within what time span you want the review to be completed.

Step 7: Lastly, you can keep track of the automated access review process by clicking on the ‘Review Status’ and viewing whether the review is still pending, modified, declined, or approved.
Also, you can add multiple applications and follow the same process for each selected application.
Zluri also provides the owner access to a snapshot view of the entire certification process status. Also, they can get an overview of the pending reviews and monitor the status of each app’s review status, including their assigned reviewers and completion status.
You can even send reviewers reminders who are yet to complete their reviews.
Further, to streamline the reviewer process, Zluri provides reviewers with all the user access data in a single screen, i.e., the reviewer screen. For the same screen, reviewers can approve, modify, and decline access by verifying the data, and also they have to add relevant comments on the same.
Now, you can view the entire status of the review process on the chart, and once the process is completed and the owner (assigned reviewer of the certification process) is fine with the review. You can click conclude, and it will send the reports to the reviewers' email.
So Book a free demo with us to know more about the features and use cases of Zluri.






.png)


.svg)














