The importance of privileged accounts has been apparent for a very long time. The major concern is they are riskier; hence implementing tools and practices such as PIM helps in reducing the risks that are associated with privileged accounts.
A privileged account is commonly used by IT administrators, security teams, helpdesk, application owners, database administrators, etc. And are usually secured by passwords, multi-factor authentications, keys, session recordings, and behavior analytics, to name a few.
A privileged account is any user account with more privileges than ordinary users. For example, privileged accounts might be able to install or remove any application or upgrade the operating system.
There are many privileged accounts in every organization. Local administrative accounts, domain administrative accounts, emergency accounts, service accounts, and active directory accounts are some of the privileged accounts across organizations.
IT admin and other privileged users in the organization have access to critical information in your network.
Privileged identity management (PIM) allows users to manage, restrict, and monitor users access privileges to critical resources within an organization. Privileged accounts have the power to view or take action on the IT assets of the organization, and hence, it's important to manage the privileged accounts.
Managing privileged accounts can help you to prevent cyber-attacks, data breaches, non-compliant and more. It also reduces malware attacks and helps in monitoring unusual activities to send alerts for deviations.
A lot of care is required to ensure that Privileged accounts are not abused or misused. This is where Privileged identity management has a role to play.
Privileged identity management (PIM) helps to discover and document the presence of privileged accounts in web applications, packaged software programs, custom programs, and other applications.
Privileged identity management helps track the interdependencies of the applications to ensure that each password change is synchronized to avoid service disruptions. It can centralize your views, control, and authority over privileged accounts. PIM makes it possible to keep an eye at a time on all the accounts.
Every company has a group of users/accounts, each with its own set of rights and privileges. A few privileged accounts have special rights like installing or deleting an application, updating software, changing configuration settings, etc.
Risks Associated with Unmanaged Privileged Accounts
Privileged accounts are riskier than standard as they have access to the organization's critical information. Internal and external exploiters like hackers can use unmanaged privileged accounts to misuse the highly confidential data and compromise the entire network.
Below mentioned are a few risks that might be a matter of concern:
- The different privileged accounts that exist on a network at a given time are unknown.
- Not having complete details of the privileged accounts
- No strong password for privileged accounts can potentially become a threat as any external source may access and exploit it.
- Not monitoring privileged accounts will lead to no log of who used accounts to access any critical information.
Managing privileged accounts is essential. If attackers get access to the accounts and misuse the information, it will cause tremendous damage to the organization. This may cause losing reputation, paying hefty fines or going through legal battles, and more.
PIM vs. PAM vs. IAM

Privileged Identity Management (PIM): It is a practice of managing, controlling, monitoring, and securing privileged accounts and reporting if any unusual activity happens.
Privileged Access Management (PAM): It involves IT security systems, policies, tools, and techniques to safeguard identities with special access or capabilities not available to regular users and to prevent the abuse of privileged access by those users too. People, processes, and technology combine to make what constitutes PAM.
Identity Access Management (IAM): It involves each individual in the network who has a unique identity that can be tracked and managed.
In short, IAM covers all access for all users and systems, and PAM & PIM cover privileged access patterns. Privileged identity management helps in monitoring the unregulated areas of IAM and confirms those with administrative rights to prevent the misuse of the information.
Privileged Identity Management Best Practices

When you are in the process of implementing Privileged Identity Management, there are a few best practices that are better to follow to reduce the complexities of the organization and prevent any data breaches.
1. Discover privileged accounts automatically: most organizations cannot find all the privileged accounts in their IT environment. These unmanaged privileged accounts create a security vulnerability that can be exploited to access critical data. Leveraging an automated discovery solution to continuously find privileged accounts on your cross-platform network and bring them under management.
2. Change privileged accounts passwords regularly: attackers or hackers need credentials like passwords to succeed and access privileged accounts. So, frequently change the credentials for each account to protect sensitive information.
3. Go beyond passwords: passwords are only part of your PIM risk exposure. It is essential to block every way to log in or use privilege as it creates a security risk of accessing privileged accounts. There are other ways like multi-factor authentication, SSH keys, AD group memberships, etc., that are required to be found, brought under management, and updated.
4. Alerts and lockout account/session on violations: if any violations occur, alerts should be sent to the authorized user, and accounts or sessions should be locked to prevent access to the privileged account.
5. Include session monitoring, analysis, and recording: users often need privileged access to get their work done. These users can expose you to risk either intentionally or accidentally.
Control the access for authorized users by launching them into an audited and recorded session. Additionally, make sure that users never get to see the credentials and reduce the risk.
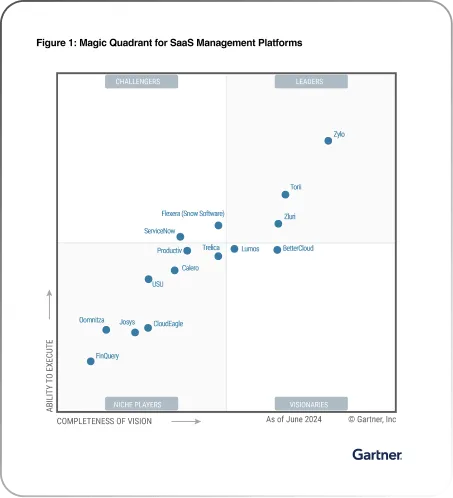
Use Zluri as a Privileged Identity Manager for SaaS Applications
Zluri is an SMP that helps with the effective management of your company-wide SaaS applications. Zluri automates SaaS discovery, management, and spending in just a few clicks. The good part is that it allows you to manage, monitor, and track privileged identities associated with each SaaS tool.

You can see the Admin and Superadmins directly from Zluri for all the apps at once. Furthermore, you can filter the users by their app role.
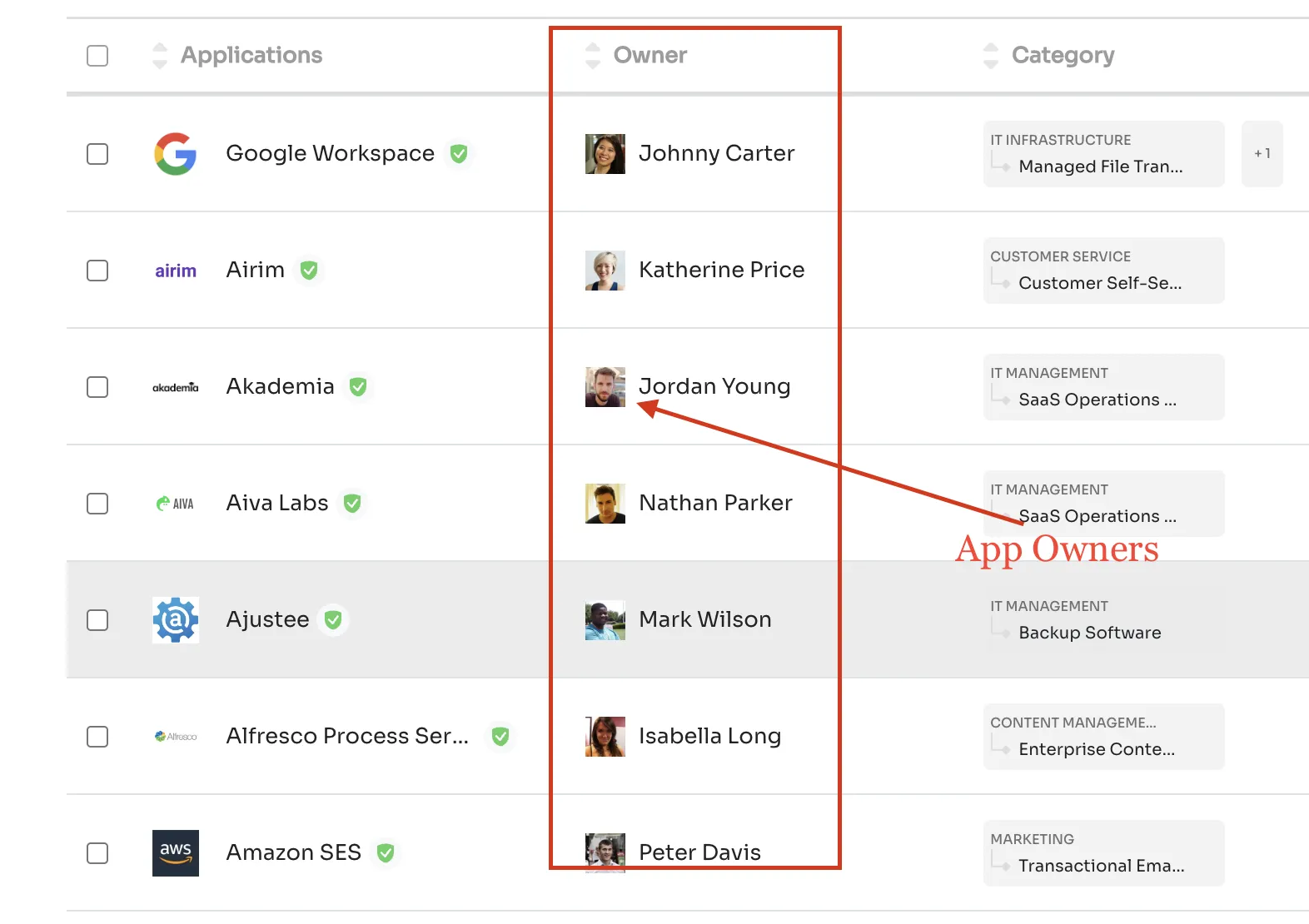
Zluri provides a single dashboard for you to assign and revoke privileges for the multitude of SaaS apps without much hassle. It also shows you the risk and threats associated with these apps and the security and compliance they lack, helping you comply with different regulations.









.svg)



























.webp)







.webp)
.webp)





.webp)