When it comes to cybersecurity, managing privileged access is vital for securing your organization's digital assets. To establish robust protocols for controlling restricted access, you have a range of access management options to choose from.
Privileged access management (PAM), privileged identity management (PIM), and privileged user management (PUM) are 3 solutions that empower your team to develop a comprehensive account and user security strategy.
These solutions offer different approaches to managing privileged access, giving your IT teams flexibility in implementing effective access control measures.
The increased use of cloud technology has significantly changed how IT teams handle and secure user identities and accounts. With the growing popularity of distributed workplaces, the risk of data breaches and cyberattacks has also increased, particularly for privileged accounts with higher permissions.
To protect privileged identities and accounts from cybercriminals, it is important to have a strong privileged access management strategy in place. However, when it comes to privileged access and identity management within organizations, several terms are commonly used: PAM, PIM, and PUM. While they may seem similar, it is crucial to understand the differences between these terms and their significance in the world of cybersecurity.
This post will explore these 3 common security acronyms—PAM, PIM, and PUM—and clarify their differences. We will also discuss how these concepts fit into a comprehensive security strategy to provide a clear understanding of their roles and importance.
Privileged Access Management (PAM)
Privileged access management (PAM) refers to the practice of securing and managing privileged accounts and access within an organization. PAM solutions are designed to provide comprehensive tools and controls to safeguard privileged accounts and ensure that only authorized individuals can access them.
The primary goal of PAM is to protect privileged accounts from unauthorized access and misuse. This involves implementing robust security measures, such as strong authentication mechanisms, privileged session monitoring, and access control policies. PAM solutions also enforce the principle of least privilege, ensuring that privileged access is granted only when necessary and for a limited time.
By centralizing the management of privileged accounts, PAM helps organizations reduce the risk of privileged credential theft, insider threats, and unauthorized access to critical systems and data. PAM solutions typically offer features like privileged account discovery, password management, session recording, and privileged session analytics to enhance security and accountability.
Privileged Identity Management (PIM)
Privileged identity management (PIM) encompasses managing and securing privileged identities within an organization. PIM solutions focus on effectively managing the identities associated with privileged accounts and ensuring their secure usage.
In PIM, privileged identities refer to the credentials and attributes associated with privileged user accounts. These identities grant elevated access privileges and control over critical systems, sensitive data, and important resources. Managing these identities is crucial to maintain the security and integrity of an organization's infrastructure.
The primary goal of PIM is to establish strong controls and processes for managing the privileged identities. This includes activities such as privileged account provisioning, deprovisioning, password management, access request and approval workflows, session monitoring, and enforcing least privilege principles. By implementing robust PIM practices, organizations can mitigate the risks of unauthorized access, insider threats, and compromised privileged credentials.
Privileged User Management (PUM)
Privileged user management (PUM) specifically focuses on managing and overseeing privileged user accounts and their activities within an organization. PUM solutions concentrate on providing comprehensive control and monitoring capabilities for privileged users.
In PUM, privileged user accounts are those with elevated permissions and access privileges, granting them significant control over critical systems, sensitive data, and important resources. These accounts are often held by individuals who play crucial roles within an organization, such as system administrators, IT managers, or executives.
The primary objective of PUM is to ensure the secure and responsible usage of privileged accounts by implementing robust controls and monitoring mechanisms. This includes user lifecycle management, access request and approval workflows, session recording, auditing, and role-based access control (RBAC) for privileged users.
By centralizing the management of privileged accounts and closely monitoring user activities, your IT team can minimize the risk of unauthorized access, data breaches, and insider threats.
Now that you’ve explored each term in detail, you can understand that there is some overlap between these terms. Thus, understanding the distinctions can help you determine which approach or combination of approaches best fits your organization’s specific security needs and compliance requirements.
PAM Vs. PIM Vs. PUM: 5 Key Factors To Consider
While these terms seem similar, they refer to distinct approaches to address different aspects of privileged access and identity management. Let’s explore them!
1. Focus and Scope of Usage for PAM, PIM, & PUM
- PAM (Privileged Access Management): PAM primarily focuses on securing and managing privileged accounts and access, emphasizing control and monitoring of privileged credentials, authentication, and session management.
- PIM (Privileged Identity Management): PIM focuses on managing and securing privileged identities, emphasizing identity lifecycle management, role-based access control, and governance of privileged accounts.
- PUM (Privileged User Management): PUM is specifically concerned with managing and monitoring the activities of privileged users, focusing on user behavior, session monitoring, activity logging, and privilege elevation. It ensures compliance, detecting potential security breaches and mitigating insider threats.
2. Contextual Access Control
Contextual access control is an important aspect to consider when comparing privileged access management (PAM), privileged identity management (PIM), and privileged user management (PUM). Contextual access control refers to the ability to grant or deny access to resources based on contextual factors such as user attributes, environmental conditions, and situational context.
- PAM solutions typically provide robust contextual access control capabilities. They allow organizations to define access policies considering various contextual factors, such as user roles, access time, device type, location, etc. By incorporating these factors into access decisions, PAM solutions ensure that privileged accounts are granted access only when the specific conditions are met.
- PIM solutions, on the other hand, primarily focus on managing and securing privileged identities rather than providing extensive contextual access control. While PIM solutions may offer some basic contextual features, such as role-based access control (RBAC), they may not provide the same level of granular control as PAM solutions.
- Similarly, PUM solutions concentrate on managing privileged user accounts and their activities but may not offer advanced contextual access control capabilities. PUM emphasizes overseeing and controlling privileged user accounts rather than considering contextual factors in access decisions.Thus, PAM solutions generally provide the most comprehensive and granular contextual access control capabilities, while PIM and PUM solutions may have limited or more focused functionality in this area.It's important to note that each approach's level of contextual access control may vary, and you should evaluate your specific requirements and compliance needs when choosing between PAM, PIM, and PUM.
3. Risk Mitigation capability for PAM, PIM, & PUM
In terms of risk mitigation, PAM, PIM, and PUM play essential roles in securing privileged accounts and reducing potential risks within an organization.
- Privileged access management (PAM) focuses on securing privileged accounts and access. It provides robust controls, such as password management, session monitoring, and access request workflows, to ensure that only authorized individuals can access sensitive systems and data. PAM solutions aim to minimize the risk of unauthorized access, insider threats, and data breaches by implementing strict access controls and monitoring mechanisms.
- Privileged identity management (PIM) specifically addresses the management and security of privileged identities. It focuses on identity governance, including user lifecycle management, role-based access control (RBAC), and privileged user provisioning and deprovisioning. PIM solutions ensure that privileged identities are properly managed, audited, and monitored, reducing the risk of identity misuse and unauthorized access.
- Privileged user management (PUM) concentrates on managing privileged user accounts and their activities. PUM solutions provide privileged users with comprehensive control and monitoring capabilities, including user activity monitoring, session recording, and access review processes. By closely monitoring privileged user activities, organizations can detect and mitigate potential risks, ensuring compliance and reducing the risk of internal threats.While all three terms contribute to risk mitigation, their focus and approaches differ. PAM primarily emphasizes securing access to privileged accounts, PIM focuses on managing privileged identities, and PUM centers around managing privileged user accounts and activities. Understanding these distinctions is crucial in selecting the right approach or combination of approaches to mitigate organizational risks effectively.
4. User Productivity: PAM, PIM, & PUM
When considering user productivity, PAM, PIM, and PUM can significantly impact the efficiency and effectiveness of users within an organization. While they primarily focus on security and access management, they also play a role in streamlining user workflows and enhancing productivity.
- Privileged access management (PAM) solutions strive to balance security and user productivity. By implementing features such as single sign-on (SSO), session management, and password management, PAM aims to simplify the login and authentication processes for privileged users. This helps reduce the time and effort spent managing multiple credentials, enabling users to access the necessary systems and applications more efficiently.
- Privileged identity management (PIM) solutions contribute to user productivity by providing streamlined processes for privileged identity provisioning and deprovisioning. With features like automated user lifecycle management and role-based access control (RBAC), PIM solutions ensure that users have the appropriate access privileges based on their roles and responsibilities. This reduces the manual effort required to grant and revoke access, allowing users to access the necessary resources quickly.
- Privileged user management (PUM) solutions focus on managing privileged user accounts and activities to enhance both security and productivity. By implementing features like session recording and user activity monitoring, PUM solutions enable organizations to track user actions and detect suspicious activities. This ensures a balance between user productivity and security by allowing authorized activities while minimizing the risk of misuse or unauthorized access.While all three terms contribute to user productivity, their specific features and approaches differ. PAM emphasizes simplifying access for privileged users, PIM streamlines the provisioning and deprovisioning of privileged identities, and PUM focuses on monitoring and managing privileged user activities. Understanding these differences can help organizations choose the right approach or combination of approaches that align with their security requirements and user productivity goals.
5. Compliance and Auditing Support
In terms of compliance and auditing, PAM, PIM, and PUM play crucial roles in helping organizations meet regulatory requirements and maintain a secure environment. Each of these terms offers specific features to address compliance and auditing needs.
- Privileged access management (PAM) solutions provide robust compliance features to ensure privileged users follow regulatory guidelines and best practices. PAM tools often include session recording and auditing capabilities, allowing organizations to monitor privileged user activities comprehensively. These recorded sessions can be reviewed later for auditing purposes, providing visibility into user actions and identifying any potential security issues or policy violations.
- Privileged identity management (PIM) solutions also contribute to compliance by streamlining identity management processes. PIM tools typically include role-based access controls (RBAC), which enable organizations to enforce least privilege principles. PIM solutions reduce the risk of unauthorized access and help organizations adhere to compliance regulations by granting the minimum necessary access to privileged identities.
- Privileged user management (PUM) solutions focus on managing privileged user accounts, which is critical for compliance and auditing purposes. PUM solutions often include access request workflows and approval mechanisms, ensuring that users' access to sensitive resources is authorized and documented. Additionally, PUM solutions may have real-time monitoring capabilities to detect and respond to any suspicious activities involving privileged users.While all three terms contribute to compliance and auditing, they differ in their specific approaches. PAM emphasizes monitoring and auditing privileged user sessions, PIM emphasizes enforcing least privilege and access controls for privileged identities, and PUM emphasizes managing and documenting privileged user access through approval workflows. Understanding these differences can help you choose the right combination of solutions to meet your compliance requirements effectively. After thoroughly examining the factors, you can understand their differences and how their combined approach can create a strong privileged access management strategy. Now, let me introduce a comprehensive solution, "Zluri," that will effectively streamline access control management within your organization.
Zluri: A Robust IGA Platform To Streamline Access Management
In order to establish efficient access control and governance, it is essential to initially determine who possesses access to particular resources. Nevertheless, numerous current approaches lack the required level of detailed data to attain this degree of accuracy. Identifying this gap, Zluri takes a proactive stance with its inventive and pioneering Identity Governance and Administration (IGA) platform, reshaping how organizations oversee access privileges and permissions.
Zluri provides a centralized hub where you can effortlessly manage and monitor privileged access across your organization. From granting access to revoking it when necessary, Zluri has you covered. Unlike traditional solutions meant for on-premises setups, Zluri's platform is purpose-built to cater to the dynamic landscape of SaaS and AI technologies. It's a comprehensive solution encompassing vital access functions such as authentication, authorization, privacy, data protection, and regulatory compliance.
Essentially, Zluri begins by pinpointing and outlining the individuals in an organization who are authorized to use specific resources. This step is pivotal in creating a solid foundation for a thorough grasp of the access scenario, which then enables the implementation of efficient access control, governance, and security measures.
By providing a clear understanding of "who can access what," Zluri empowers organizations to make informed choices about user permissions, ensure regulatory compliance, and bolster overall data security.
But that's not all. Zluri's advanced features empower you with granular control over access rights. With its fine-grained permission management, you can ensure that users have exactly the privileges they need and not an inch more. No more sleepless nights worrying about unauthorized access or security breaches.
But, what distinguishes Zluri from other IGA tools?
Let's delve into this.
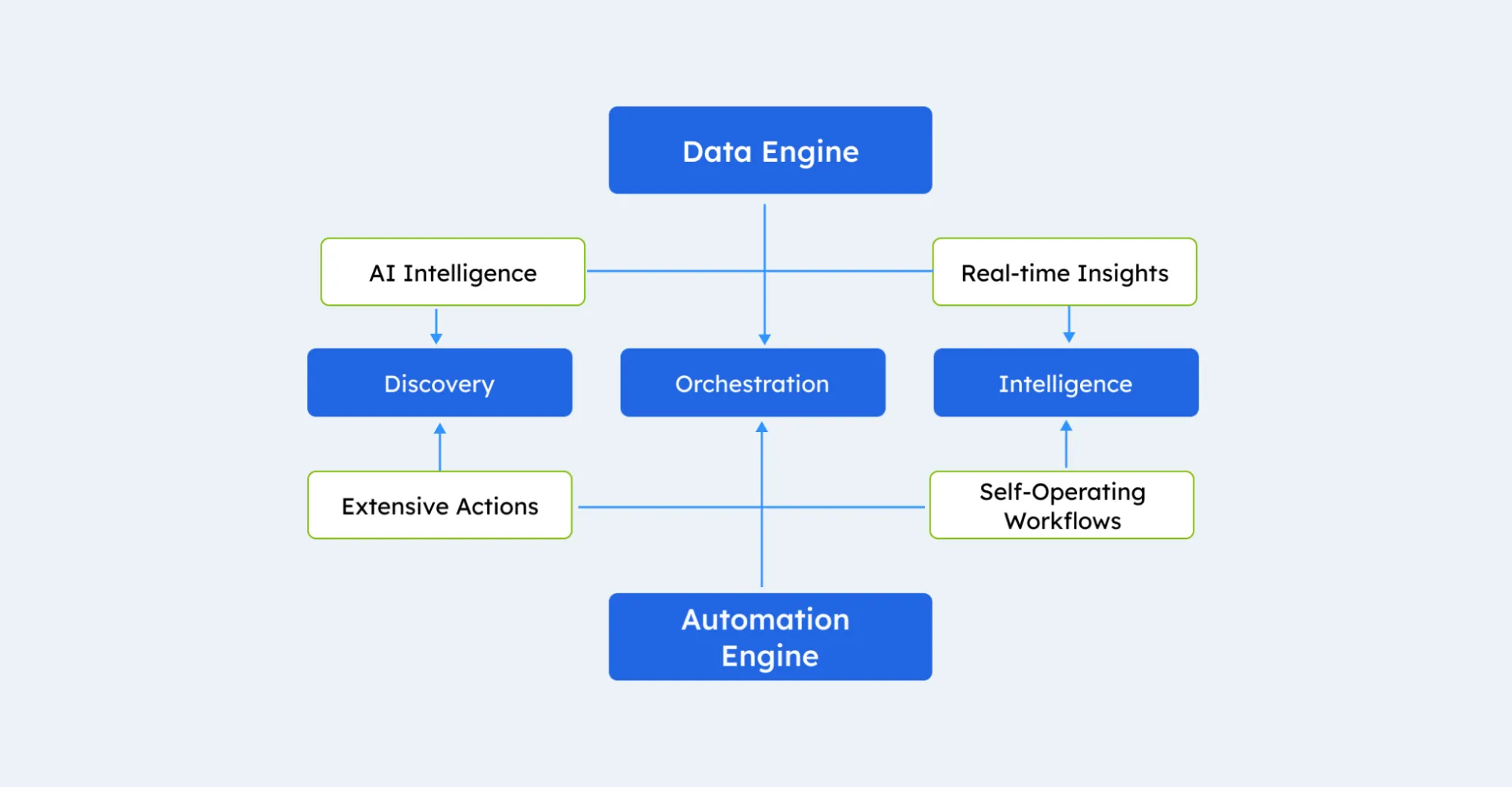
- Its Discovery Engine: Gain Immediate Insights into User Access Permissions
At the forefront, Zluri presents its impressive discovery engine—an adept powerhouse that uncovers the relationships between users and resources, essentially identifying who possesses access to what. Zluri equips your IT team with effortless analysis and revelation of all SaaS applications and user-associated data, facilitated by its nine distinct discovery methods.
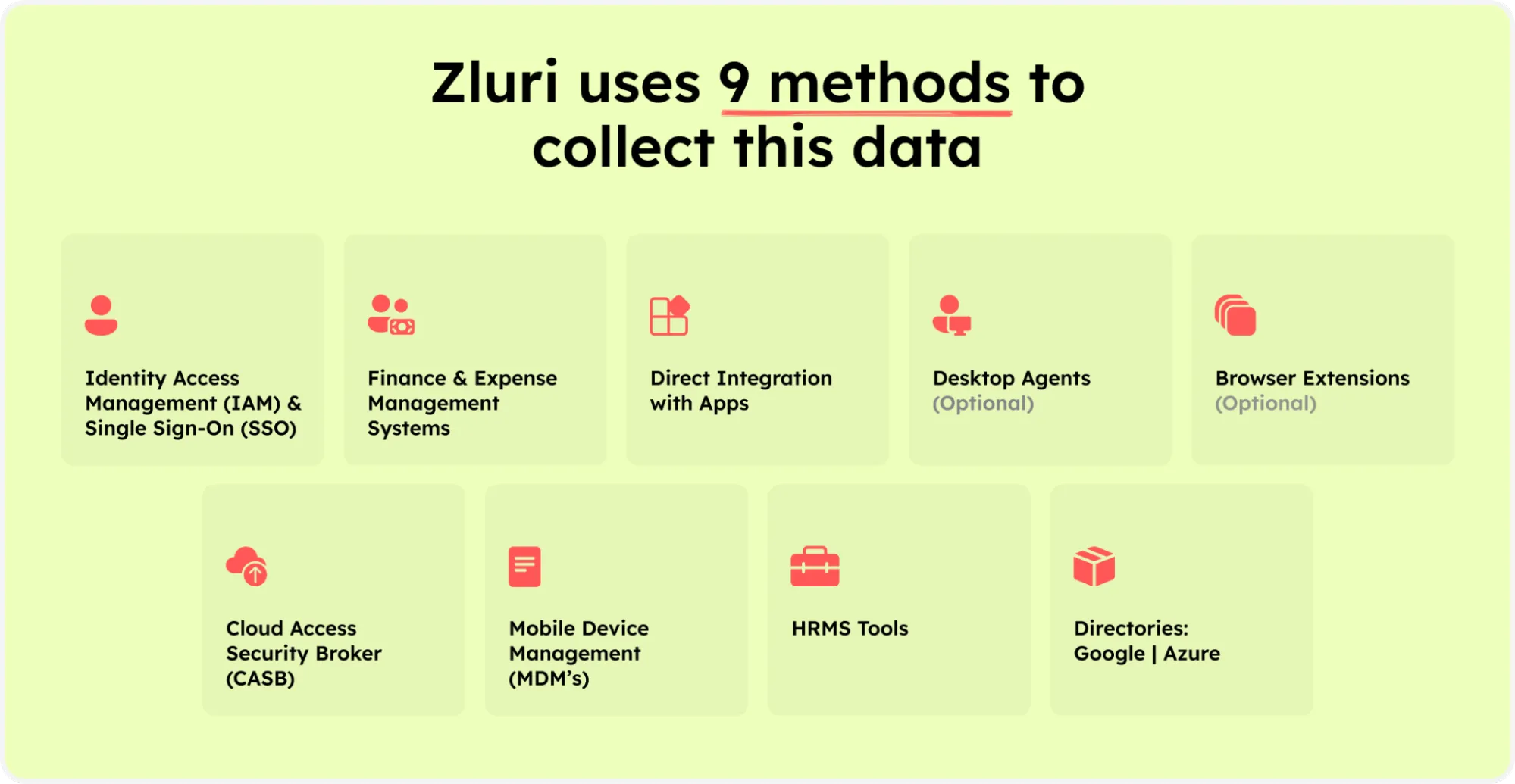
Zluri’s nine discovery methods
These approaches encompass sMDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional). By employing these methodologies, your team can effortlessly discern application access, active user presence, granted authorizations, pivotal user classification, and more. Consequently, once you unveil the access privileges for each user, overseeing and managing them becomes straightforward.
Seamlessly integrating with popular identity systems and core applications, Zluri attains a remarkable scope, streamlining authentication procedures to ensure a seamless user experience. Covering a spectrum of over 300 SaaS applications, Zluri delivers real-time data, informed observations, and AI-driven alerts, achieving comprehensive visibility through API-based integration. In doing so, it bolsters your security protocols, guaranteeing absolute control and transparency to fend off potential breaches and enhance overall security.
Moreover, Zluri provides intricate-level access data, offering exhaustive insights into user permissions within your SaaS ecosystem.
- Streamlined Access Governance via Zluri's Automation Engine
Zluri's automation engine adeptly oversees access workflows, guaranteeing accurate authorization assignments to appropriate users and unwavering compliance with policies. By instituting automation rules and triggers, it facilitates tailored and self-sufficient access and review workflows. This optimizes administrative procedures and maximizes the potential of IT management.
Delving into Zluri's IGA Core Capabilities: Autonomous & Automated
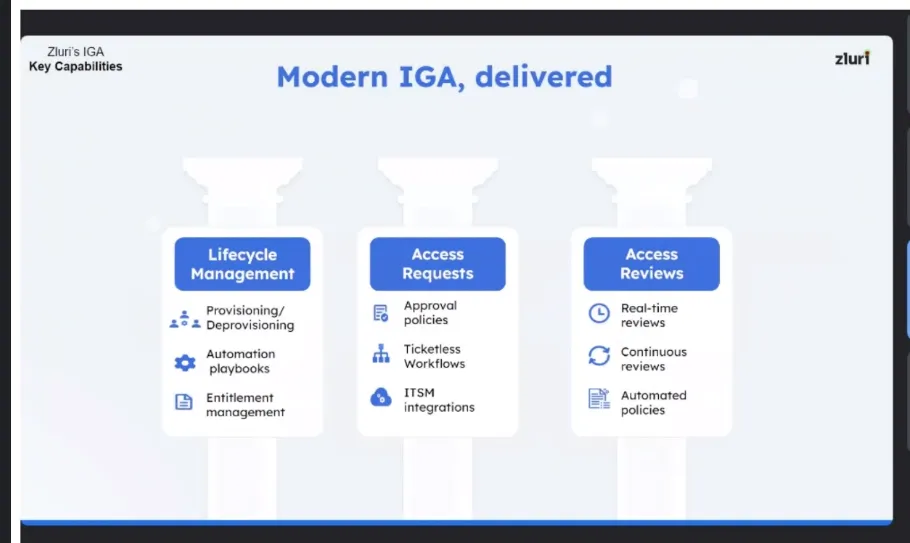
- Lifecycle management: Seamless User Provisioning & Deprovisioning
Zluri streamlines the entire user lifecycle journey, from onboarding to offboarding, with its unified provisioning and de-provisioning capabilities. This efficient process ensures that users have the right resources and privileges during their tenure while revoking access seamlessly when needed.
The platform enables your IT team to create and customize onboarding and offboarding workflows, streamlining the process of granting and revoking access to SaaS apps and data. With a few clicks, your team can securely provide access to multiple new joiners based on their job entitlements such as role, position, and department. This efficient workflow boosts your team's productivity, enhances employee efficiency, and ensures a secure environment for user identities and SaaS app data.

Three key unique features make Zluri's user lifecycle management platform stand out:
- Personalized workflows cater to specific roles and preferences, ensuring each user's smooth and personalized onboarding and offboarding experience. The user-friendly interface enables the creation of customized workflows tailored to user roles, departments, and seniority levels, ensuring efficient access management.
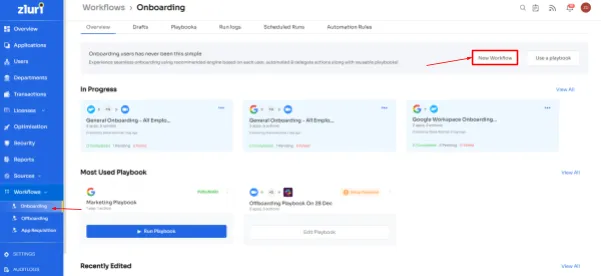
- Onboarding workflow

Offboarding workflow
- Reusable playbooks save time and effort by eliminating the need to recreate workflows for each user, ensuring consistency and accuracy during transitions. These reusable automation playbooks save onboarding and offboarding workflows as pre-defined templates, eradicating the necessity for redundant recreations.
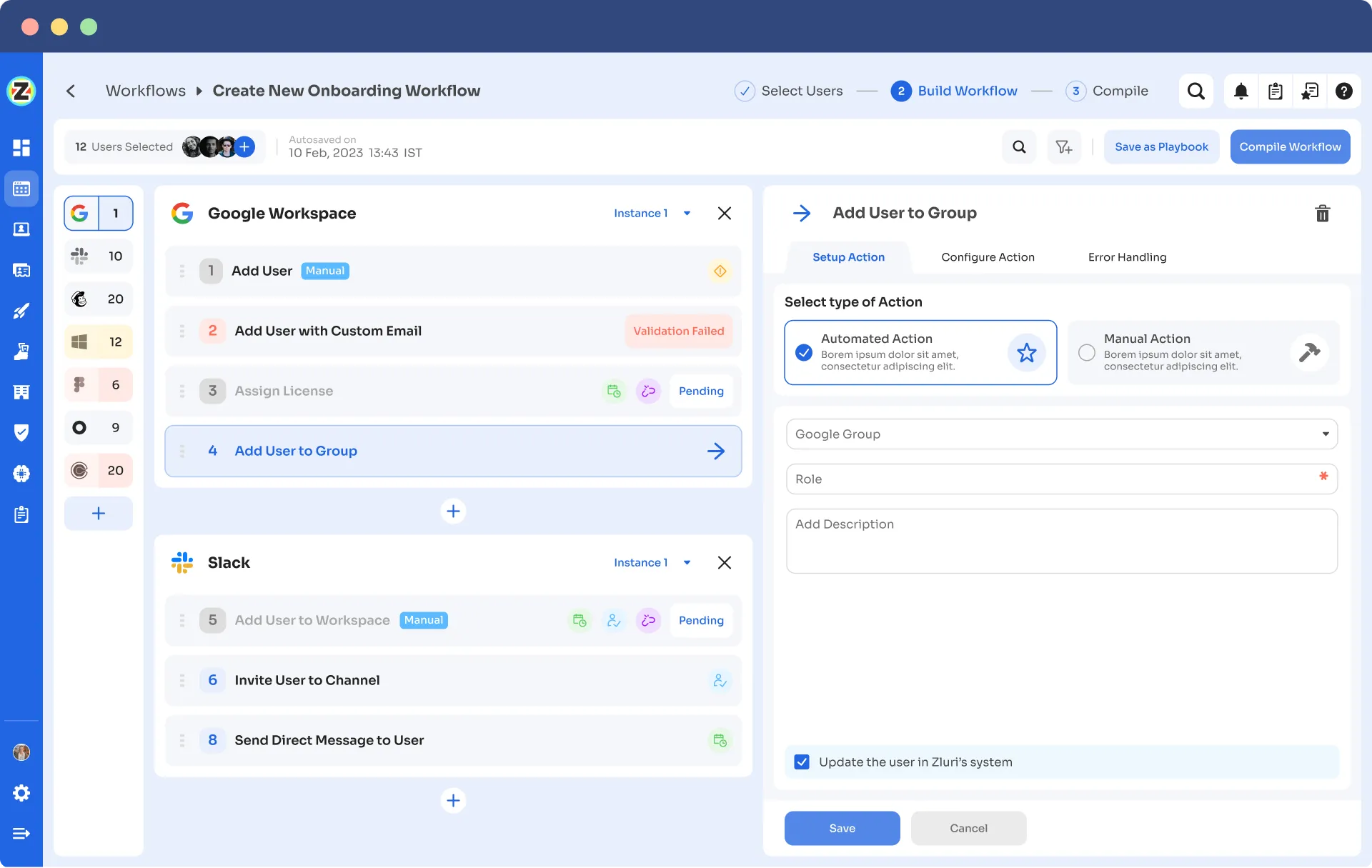
- Onboarding Playbooks
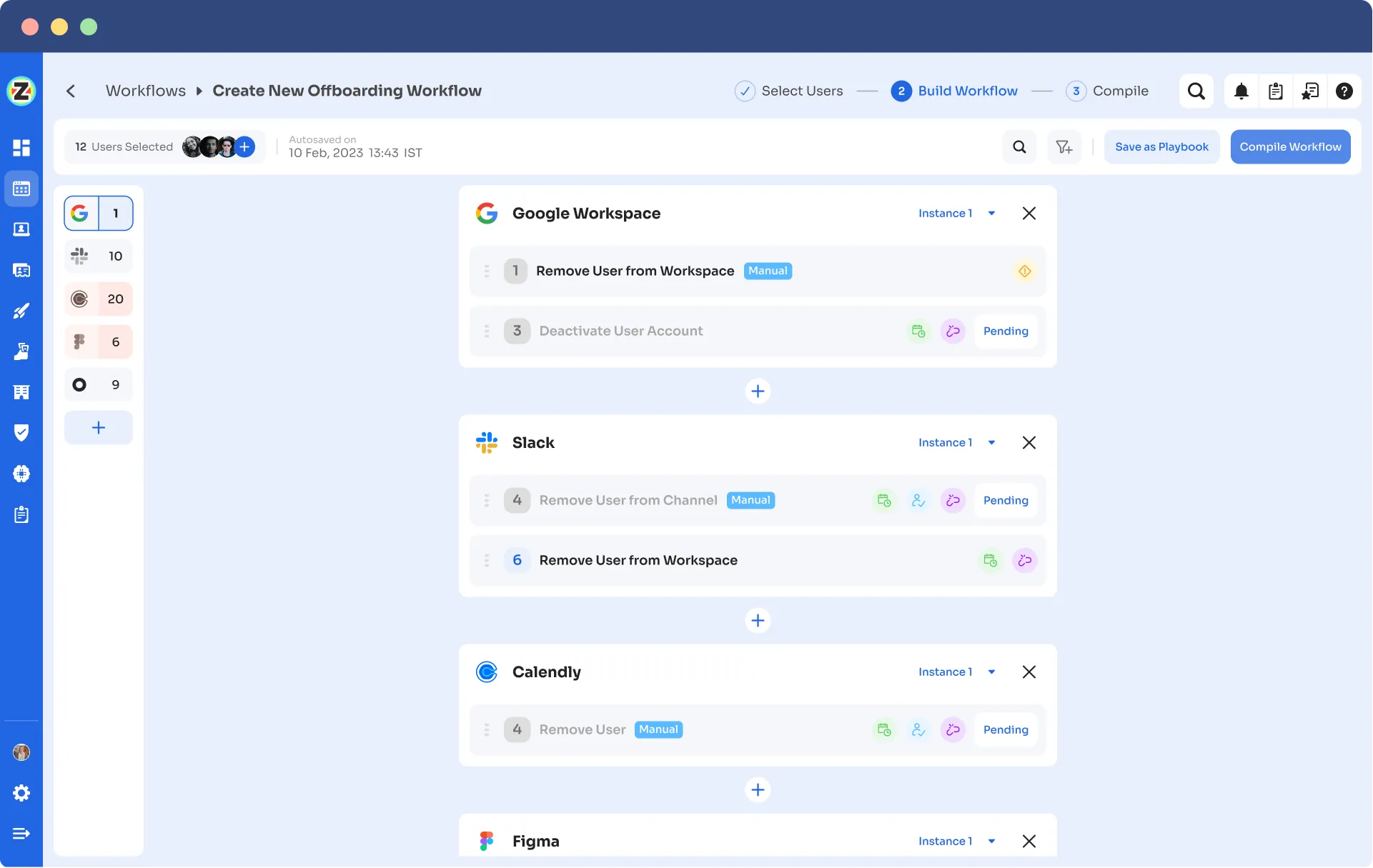
Offboarding Playbooks
- The system offers smart app suggestions and in-app recommendations derived from user profiles, departmental affiliations, seniority levels, and additional contextual considerations.

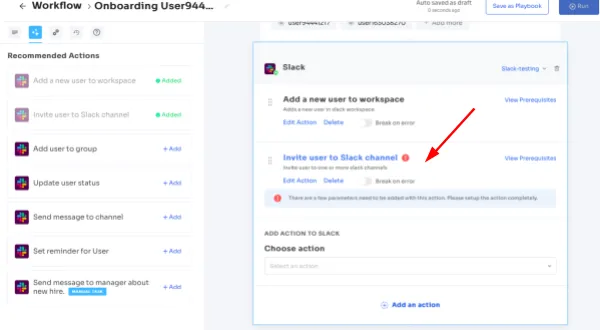
These app recommendations and in-app suggestions enhance user experiences, providing relevant tools and guidance to boost productivity and adhere to security protocols.
With Zluri, managing user access becomes efficient, secure, and user-centric, allowing your IT teams to optimize their access management processes and create a seamless experience for employees throughout their journey with the organization.
- Self-Serve Model: Helps Your IT Team Manage Ad-hoc Access Requests
Sometimes, users may require temporary access to specific resources beyond their assigned permissions. Zluri enables streamlined handling of these ad-hoc requests, allowing IT teams to evaluate and grant temporary access as needed, while still maintaining overall access control.
How does Zluri accomplish all of this? It offers a self-serve ad-hoc access request management model called the Employee App Store (EAS). EAS is a collection of SaaS apps approved and verified by IT teams. This innovative platform empowers your team to effortlessly grant access to essential tools based on employees' job roles and permissions.

With the Employee App Store, your IT team gains complete control over determining which apps are visible to each employee. This level of personalization ensures that employees have access to the specific tools relevant to their roles, enhancing their productivity and efficiency. All they need to do is submit an access request, and your IT admin will get notified immediately. Afterward, the IT admins or designated approvers can efficiently review and approve access requests.
To facilitate efficient decision-making and access control, higher-level authorities have the ability to override decisions made by lower-level administrators or managers. This flexibility enables swift and effective management of access requests while maintaining the necessary security controls.
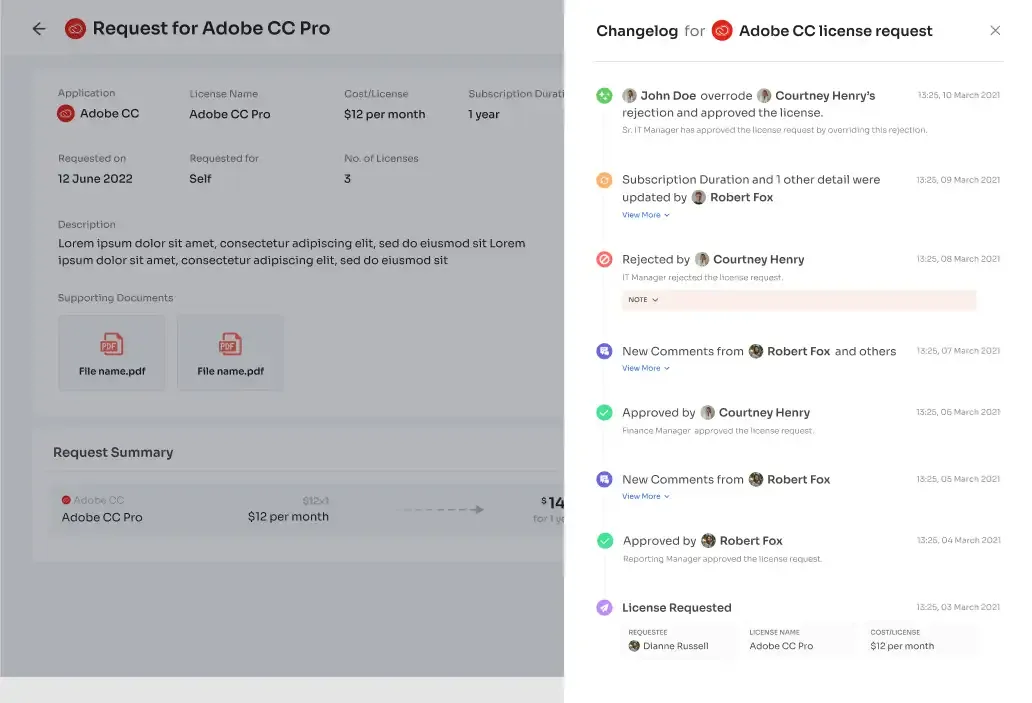
For employees, the Employee App Store provides a user-friendly interface where they can conveniently track the status and updates of their requests. The "changelog" feature offers comprehensive information on request approval or rejection, license duration or tier changes, and any comments administrators add. This transparency ensures visibility and accountability throughout the access management process, empowering employees with real-time updates on their requests.
- Maintaining security & compliance with regular Access certifications
In the era of decentralized SaaS, granting employee access is easier, but controlling privileges is more complex. Zluri simplifies this with centralized user access reviews and permissions management. Its access Certifications offer a comprehensive audit trail, ensuring clarity on who accesses critical resources. This proactive approach enhances data security and regulatory compliance management.
Zluri’s automated access certifications offer several key features:-
- Intelligent Automation for Access Rights: Zluri employs intelligent automation to evaluate user access rights based on predefined rules. This automation helps streamline the review process and reduce errors that might occur with manual methods.
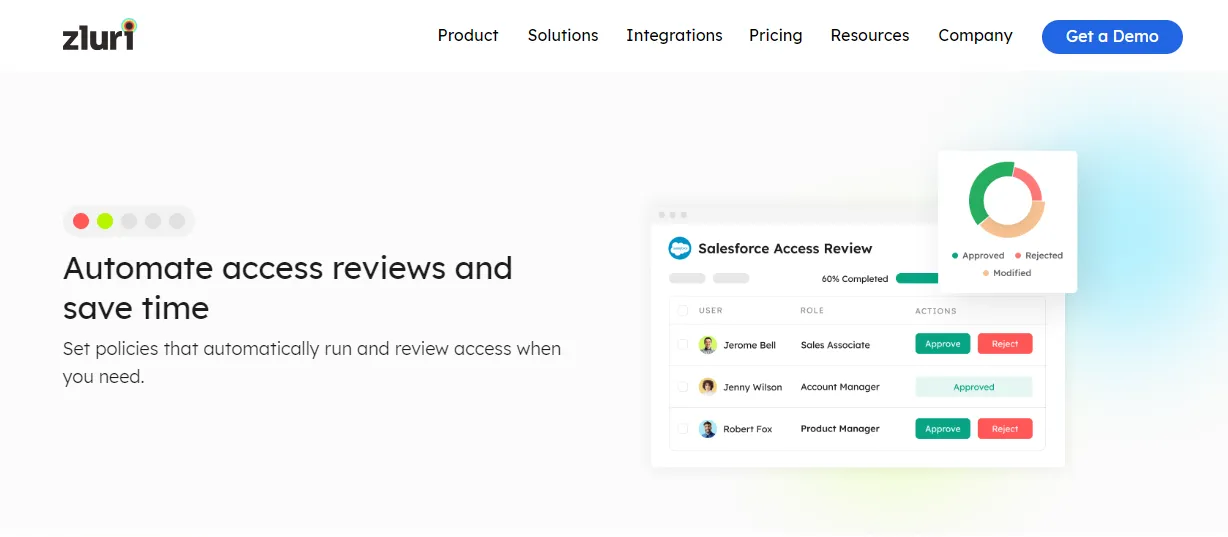
- Auto-Remediation Capabilities: Its auto-remediation capabilities promptly address access violations. This quick response enhances security by resolving access issues in a timely manner and contributes to maintaining compliance with access policies.
- Termination and Outdated Privileges Management: The platform enables IT teams to swiftly revoke access for terminated employees or outdated privileges. This feature helps mitigate the risk of unauthorized data breaches stemming from lingering access rights.
- Access Patterns and Vulnerability Insights: Zluri provides a variety of reports that offer insights into access patterns, vulnerabilities, and compliance status. This data aids in making informed decisions about access management and strengthens overall compliance efforts.
- Continuous Access Reviews and Certifications: The tool offers continuous access reviews that provide recurring certifications to validate permissions consistently. Scheduled certifications ensure that access reviews are conducted promptly, addressing critical access issues and enhancing security measures.
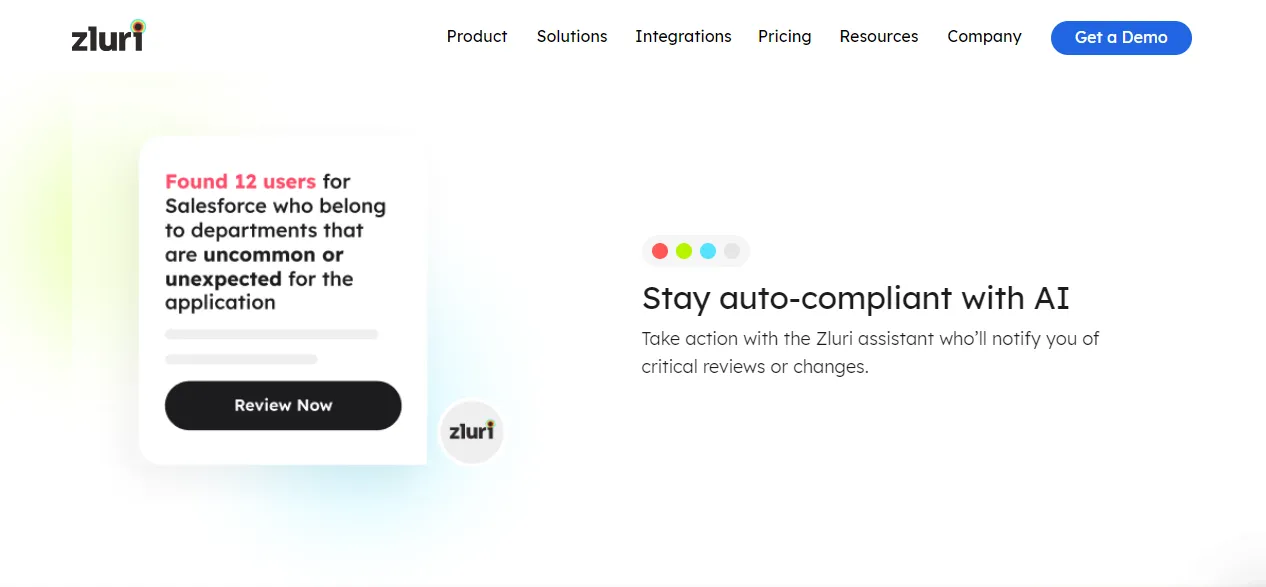
- Real-Time Access Reviews and Anomaly Detection: The platform's real-time access reviews utilize AI to scrutinize user behavior patterns and quickly detect anomalies. This proactive approach aids in identifying potential threats and taking timely actions to mitigate risks.
- AI-Powered Compliance Insights: Zluri's AI compliance capabilities provide intelligent insights into access controls. These insights align with industry regulations and standards, minimizing compliance risks and helping organizations adhere to relevant guidelines.
- Certificate Templates for Compliance: It offers industry-standard certificate templates that streamline the certification process. These templates help create comprehensive, accurate, and guideline-aligned documents, facilitating compliance efforts.
Still not convinced? Experience Zluri firsthand and gain efficient access management and enhanced security for your organization. Don't wait – book your demo now!
Also Read: If you want to choose a suitable IGA tool, you can go through How to choose an IGA tool






.png)


.svg)














