Office 365 Security Checklist
Here's a checklist to help you enhance the security of your Office 365 deployment:
1. Enhance password security by enforcing unique passwords
Strong and unique passwords are the first defense against unauthorized access to your organization's systems and data. Consider the following key points to reinforce this aspect:
- Mitigating Password Reuse: Over 70% of individuals reuse passwords, risking your data. Encourage unique passwords for all accounts, especially Microsoft 365, to avoid vulnerabilities.
- Password Complexity: Passwords should be at least eight characters long and include a mix of uppercase, lowercase, digits, and avoid common and easily guessable phrases.
- Regular Password Changes: Enforce password changes at least once a year to minimize long-term exposure.
- Data Backup: Ensure robust data backup strategies to safeguard your organization's data, even if passwords are compromised.
Further, to promote strong password creation, consider adopting the following strategies: - Educate Users: Conduct regular cybersecurity awareness training sessions to educate employees about the importance of strong, unique passwords and the risks associated with weak ones. Encourage them to use password managers to generate and store complex passwords securely.
- Enforce Password Complexity: Configure systems to enforce password complexity requirements automatically. This ensures that users cannot select weak passwords that are easily guessable.
- Password Management Tools: Invest in password management tools that facilitate secure password creation and storage. These tools can help employees generate and manage complex passwords without the burden of memorization.
Additionally, embracing multi-factor authentication (MFA) and role-based access control (RBAC) adds additional layers of protection, making it even more challenging for malicious actors to compromise accounts. Following these recommendations can enhance your organization's overall security posture and safeguard your valuable data.
2. Ensure timely updates to avoid using outdated software versions
Regular software updates are essential for mitigating vulnerabilities within your IT infrastructure. Outdated software, like older Microsoft Office versions, becomes a prime target for cyberattacks as security updates cease with time.
Once a software version reaches its \"expiry date,\" the absence of security updates exposes your organization to emerging threats. Without these updates, your software becomes defenseless against sophisticated malware that can propagate across your network, including ransomware.
Automating software updates is a pivotal step in ensuring security and operational efficiency:
- Centralized Management: Leverage tools like Microsoft Endpoint Configuration Manager for streamlined scheduling and deployment of updates across your entire IT infrastructure.
- Patch Testing: Prior to deployment, rigorously test updates in a controlled environment to swiftly identify and resolve potential conflicts, ensuring a smooth update process.
- Scheduled Maintenance: Collaborate with your IT team to establish designated maintenance windows during non-business hours, minimizing disruptions to your organization's daily operations.
- User Communication: Maintain open lines of communication with your team, providing regular updates about the schedule. Emphasize the significance of these updates for bolstering security measures.
- Monitoring and Reporting: Implement robust monitoring and reporting systems to track the status of updates in real-time. This empowers you to swiftly identify and address any issues, ensuring a secure and stable IT environment.
3. Safeguard information sharing to prevent unauthorized access
Creating clear and comprehensive data-sharing policies is the cornerstone of information security. Collaborate with legal and compliance teams to develop policies that define data classification, user access control, encryption standards, and data retention/deletion rules. This step sets the foundation for secure data-sharing practices, reducing the risk of data breaches.
Office 365 is your ally in securing data sharing. Use DLP features like sensitivity labels to classify documents based on their content automatically. Set up strict enforcement and incident monitoring policies to address security breaches swiftly.
Furthermore, understand the risks of unauthorized access, from ransomware threats to data profiteering, and take proactive steps like restricting external linking and conducting employee training to bolster your organization's defense against data breaches.
By implementing these strategies, you and your teams can safeguard your organization's most valuable asset - internal company information - and ensure it stays secure and confidential.
4. Configure Microsoft 365 settings to block sensitive data sharing
Sensitive data, such as credit card numbers and personally identifiable information (PII), must be protected rigorously. Leaked sensitive information can result in severe legal implications and hefty fines for your organization. Thus, it is imperative to have a system in place that prevents sensitive data from being shared through various communication and collaboration channels.
To address this challenge, Microsoft 365 offers a range of security settings and features that can help you prevent sensitive data from being shared inappropriately.
- Define Sensitive Information Parameters: Establish recognition criteria for sensitive data. Create rules and policies specifying what qualifies as sensitive information, like credit card numbers, PII, or medical records.
- Implement Data Classification and Labeling: Utilize data classification and labeling tools in Microsoft 365. Tag documents and emails with appropriate labels to identify and protect critical data. This ensures consistent protection policies.
- Leverage Microsoft 365 Security Settings: Employ Microsoft 365's security settings to trace and block sensitive data sharing. Configure policies to prevent specific data types from being sent via email or stored on SharePoint and OneDrive, enforcing data protection policies.
- Monitor and Report: Regularly analyze the effectiveness of your data protection measures. Microsoft 365 offers reporting tools to track data-sharing activities and identify potential security breaches. Stay proactive in addressing anomalies or violations.
- User Training and Awareness: Educate employees on data security best practices. Conduct training sessions to raise awareness about the consequences of sharing sensitive information and how to use Microsoft 365 securely
By effectively implementing and configuring Microsoft 365 settings, you can prevent sensitive information from being shared, ensuring legal compliance, data protection, and peace of mind for your organization.
5. Prioritize in-house and external training resources
As an IT manager, it's imperative to recognize the pivotal role of cybersecurity awareness training in fortifying the human element of security. While technical defenses are essential, human error remains one of the leading Microsoft 365 security concerns, often providing cybercriminals with an entry point into your systems.
One of the key challenges faced is the tendency to downplay the importance of security education until potential risks escalate into urgent, high-stakes problems. Security training is often deferred as a secondary concern, despite human error's clear and present danger.
Some of the most common human mistakes that can significantly harm your organization include sharing sensitive and confidential company information with third parties, inadvertently clicking on infected links and email attachments, accidental data deletion, and vulnerability to social engineering tactics employed by cybercriminals.
To address these vulnerabilities effectively, you must invest in comprehensive security education for your employees. You have two primary options for implementing such training.
Firstly, you can ask your in-house security department to create customized training modules tailored to your organization's needs. Alternatively, you can purchase pre-built training resources designed by cybersecurity experts.
Collaboration with external cybersecurity experts is also highly beneficial. These experts can provide assessments and strategic improvements based on their extensive industry knowledge. Their external perspective can offer fresh insights and best practices, ensuring a comprehensive approach to cybersecurity training.
Microsoft Office 365 is a critical component of most organizations, making it a prime target for cyber threats. You need a robust identity governance and administration (IGA) solution to address these challenges effectively.
Strengthen Microsoft Office 365 Security with Zluri’s IGA Solution
Zluri's IGA Solution is tailor-made to enhance Office 365 security while streamlining user management processes. Incorporating Zluri's IGA solution into your Microsoft Office 365 security strategy empowers you and your teams to strengthen security protocols, efficiently manage user access, and navigate the complexities of regulatory frameworks.
With a centralized dashboard, proactive security measures, and adaptability to modern work environments, Zluri's IGA solution offers a holistic approach to enhancing security and compliance in the digital age. Let’s explore how Zluri's IGA solution can empower you and your teams to fortify your Office 365 security infrastructure.
1. Zluri's innovative discovery methods for unparalleled insights
Zluri's IGA solution boasts an advanced data engine that redefines identity governance and security practices for modern organizations. This data engine utilizes state-of-the-art discovery methods to provide unparalleled insights into your SaaS applications and user-related data. Here's how it works:

Zluri’s nine discovery methods
Comprehensive Discovery Methods:
- Zluri offers seamless integration with single sign-on (SSO) systems, providing a unified view of user access for enhanced security and simplified access management. Integration with identity providers strengthens identity management and governance.
- Finance system analysis delivers a comprehensive view of your app ecosystem for informed decisions, while direct app integration simplifies monitoring and security. Desktop agents enable real-time monitoring at an individual level, aiding in identifying security risks and resource optimization.
- Browser extensions gather non-intrusive data on web-based applications and user activities, ensuring complete and accurate insights for IT teams.
Efficiency through Automation:
Zluri's data engine eliminates all the tedious manual tasks and user access tracking. This automation sets new standards by intelligently distinguishing between managed, unmanaged, and shadow IT applications. The benefits are substantial:
- Resource Utilization: Efficiently allocate resources by identifying and managing active applications.
- Time Savings: IT teams save valuable time that can be redirected towards critical tasks.
- Granular Perspective: Get a detailed view of active users and critical users, enhancing security measures.
2. Elevate your Office 365 Security with Zluri’s streamlined provisioning & deprovisioning processes
Zluri's IGA solution streamlines access governance, providing your IT team with an intuitive interface to automate lifecycle management for users. With precision and simplicity, you can ensure that authorized employees receive tailored access to Office 365 resources. No more manual provisioning and deprovisioning, no more risks of over-provisioning – just robust, error-free security.
Customized Onboarding Workflows:
Experience a revolution in onboarding. Zluri empowers your IT team to create and customize onboarding workflows effortlessly, accommodating specific job roles, positions, and departments.
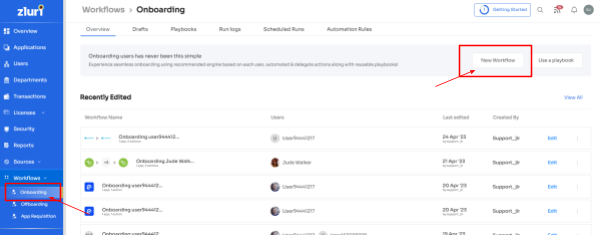
Configure access privileges based on job responsibilities with just a few clicks, leaving no room for errors. Boost efficiency, enhance productivity, and fortify Office 365 security with Zluri's cutting-edge workflow capabilities.
Seamless Offboarding Workflows:
Zluri's IGA solution doesn't stop at onboarding; it transforms offboarding too. Automatic access revocation for all devices, apps, and systems ensures that former employees cannot breach your Office 365 data.
With data backup and secure transfer to new owners, sensitive information remains safeguarded even after employee departures. It simplifies license revocation and eliminates SSO access, providing a proactive defense against data misuse.
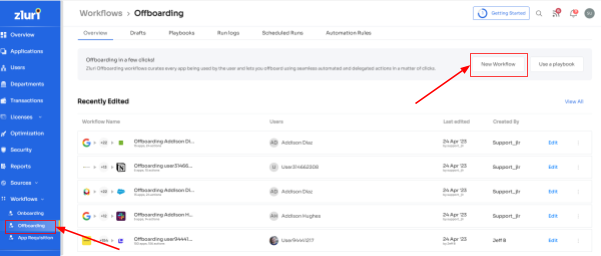
Zluri's user-friendly approach to offboarding guarantees consistent, secure deprovisioning, making transitions a breeze. Reduce the administrative burden and gain confidence in managing departures, no matter how sensitive. With Zluri, effortless user access deprovisioning becomes your reality, boosting productivity and fortifying your digital assets.
Adapt and Optimize with Ease:
Zluri's IGA solution offers outstanding reusability and flexibility for playbooks. Effortlessly update them as needed, ensuring continuous efficiency in your Office 365 security strategy. Manage and adapt your playbooks with ease, streamlining and optimizing your procedures over time with Zluri's user-friendly approach.

Elevate your IT strategy with Zluri's IGA solution. Strengthen Microsoft Office 365 security, streamline your workflows, and embrace a future where security is not a concern but a certainty.
3. Access request management with Zluri's employee app store (EAS)
Managing access permissions during employee transitions can be a complex and time-consuming task. Balancing the need to provide employees with the right access for their roles while safeguarding sensitive data is crucial. That's where Zluri's Employee App Store (EAS) comes in—a game-changing solution designed for you.

How Zluri’s EAS helps with efficient access request management:
Efficient Access Request Management: Zluri's EAS streamlines the process of managing access requests, ensuring that employees receive precisely the right level of access needed for their roles. This efficiency reduces the risk of over-provisioning or granting unnecessary access, which can be a security vulnerability.
Unprecedented Control: Zluri's solution empowers IT managers with greater control over access privileges, helping them enforce security policies more effectively. This control is essential in preventing unauthorized access to sensitive data within Microsoft Office 365.
Multi-Layered Approval System: The multi-layered approval system in EAS ensures that access requests are thoroughly reviewed and authorized by the appropriate personnel. This approach minimizes the chances of unauthorized access and strengthens security by preventing improper access.

Transparent Access Management: The transparency in access management, including detailed explanations and comments for approvals and rejections, enhances security by ensuring that access decisions are well-documented and understood. This transparency is crucial for audit purposes and maintaining a secure environment.
Fine-Tuning Access Requests: Zluri's solution allows for fine-tuning access requests, ensuring that permissions are aligned with the organization's security requirements. This fine-tuning capability helps IT managers implement the principle of least privilege, which is a fundamental security best practice.
Comprehensive Changelog Functionality: The changelog functionality keeps a detailed record of all access-related changes, including approvals, rejections, and alterations in permissions. This comprehensive logging is essential for security auditing and monitoring, ensuring that any suspicious activity can be promptly detected and investigated.
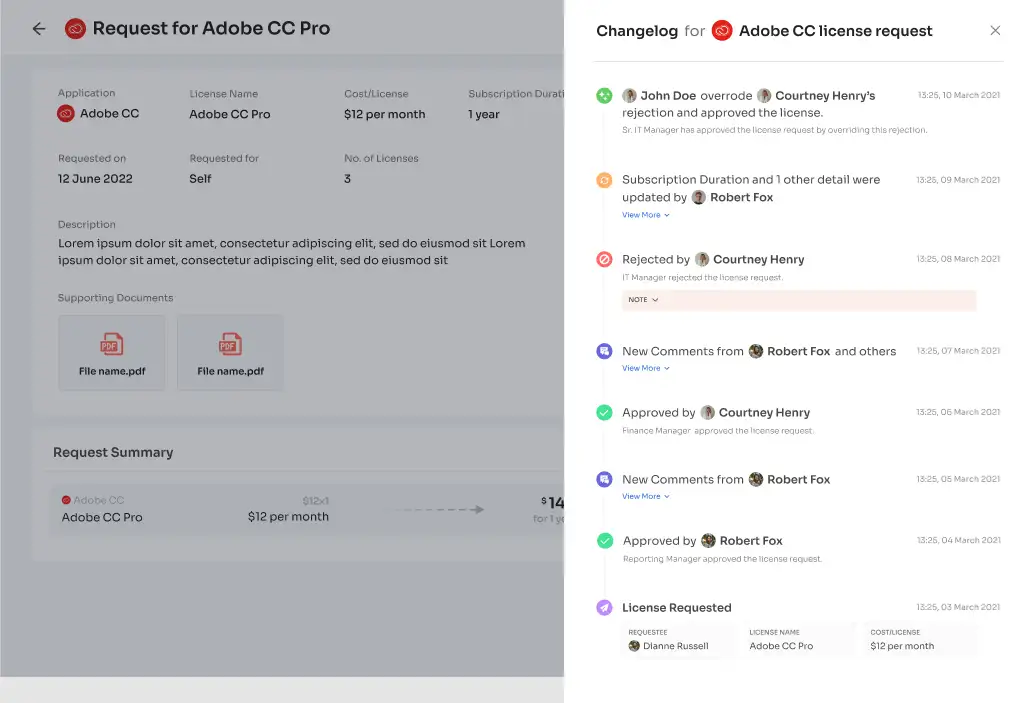
Promoting Collaboration and Transparency: By encouraging collaboration and providing a clear audit trail of access-related actions, Zluri's solution fosters a security-conscious culture within the organization. This culture of transparency and collaboration is vital for maintaining a strong security posture.
4. User access reviews to enhance security
Zluri's IGA solution simplifies and supercharges the access review process within your Office 365 environment. The platform provides a comprehensive view of user activities and access levels, empowering you to promptly detect and mitigate risks associated with excessive or inappropriate access.

Let's explore how Zluri's IGA solution transforms user access reviews by providing a unified access platform and automated review mechanisms tailored to strengthen Microsoft Office 365 security.
Unified Access: A Comprehensive View of Digital Identities
With Zluri's IGA solution, you gain unprecedented visibility into your organization's access landscape. Imagine a unified approach consolidating user access-related information from various sources into one intuitive platform.
No more juggling multiple directories or identity repositories; all the data you need to comprehend access privileges and user activity is now at your fingertips.
- Access Directory: Zluri's IGA solution captures and organizes user information from various sources, including active directory and other identity repositories, ensuring complete and accurate records. This means user identities and their access privileges are easily accessible for review, especially within your Microsoft Office 365 environment.
- Access Privileges: Zluri's unified access empowers administrators like you to oversee and manage user access privileges across the organization. This enhanced visibility enables swift identification of access discrepancies or suspicious permissions, fortifying your defense against cyber threats within your Microsoft Office 365 applications.
- Activity & Alerts: Stay ahead of potential security breaches with Zluri's proactive approach. The IGA solution tracks user activity in real-time and triggers instant alerts for anomalous behavior or unauthorized access attempts, ensuring the utmost security for your Microsoft Office 365 environment.
Transform Your Access Review Process with Zluri's Automation
Zluri offers a suite of powerful automated review capabilities that streamline your access control system within Microsoft Office 365, ensuring top-notch security and compliance with regulatory standards.
- Access Rules: Define access rules and policies specific to Microsoft Office 365 based on roles, responsibilities, and business requirements. Through automation, the platform conducts instant reviews and validations of user access against established criteria, ensuring that your Office 365 environment remains secure and compliant.
- Scheduled Certification: Proactively schedule certifications within Microsoft Office 365 to verify if employees' access aligns with your organization's policies and regulatory requirements. This ensures that access permissions within Office 365 are always up-to-date and compliant, contributing to a strengthened security posture.
- Auto-Remediation: Zluri's auto-remediation capabilities go beyond reviews, actively responding to access violations within your Microsoft Office 365 environment. When the system detects unauthorized access or potential security breaches, it triggers corrective actions for immediate resolution, safeguarding your Office 365 data effectively.Manual access reviews often demand significant time and human effort, involving coordination with various departments, data gathering, and cross-referencing access permissions. These tasks are prone to human errors and can lead to compliance issues or security gaps.
Unlock the Power of Zluri's IGA Solution for Office 365 Security
- 10X Faster Reviews: Zluri's automated access reviews revolutionize the process. You can achieve reviews that are not just faster but up to 10 times quicker. This rapid turnaround ensures that your Office 365 environment is constantly monitored and secured without burdening your IT team.
- 70% Reduction in Effort: Our solution streamlines access management, resulting in a staggering 70% reduction in effort. By automating time-consuming tasks, your team can focus on higher-value activities, such as addressing emerging threats and optimizing security strategies.
- Enhanced Security and Compliance: Zluri's IGA Solution ensures that your Office 365 environment remains secure and compliant. By automating access reviews and enforcing security policies, we minimize the risk of security gaps and compliance issues, offering you peace of mind.So why wait? Book a demo now!







.png)

.svg)














