Identity and access management (IAM) is a set of business processes, policies, and technologies that makes managing digital identities easier. With an IAM framework in place, IT teams can control who can access important information in the organization.
It uses various authentication systems like single sign-on, two-factor & multifactor authentication, and privileged access management.
However, setting up and running an IAM solution comes with challenges, especially in a complex cloud environment. In this article, we talk about the top IAM challenges and how you can overcome them.
New cloud-based IAM solutions are rising favorably as they standardize and streamline identity management. However, when businesses adopt cloud computing, managing administrator access is challenging.
Access management involves managing user identities, controlling access to those identities and the resources that go with them, and monitoring the entire process to ensure your organization is safe.
Wistia_ID: xdyx0ms4d9
Additionally, it's about enhancing user experience and ensuring that your digital transformation strategy works. Even though the number of data breaches is increasing, and stolen credentials cause most of them, it's crucial to view access management from a broader perspective than merely IT security.
Identity and access management are crucial for every organization. First, it helps your employees to stay compliant with your organization's rules and regulations. Second, it guarantees that employees can use the right tools and resources when they need to keep working. Third, you can regulate the flow of information among your employees. Lastly, access management enables you to monitor and regulate the behavior of your employees.
It's important to understand that access management can improve the overall user experience of your organization. You can achieve this by making information easier to find, enabling employees to access it, and facilitating team collaboration within your organization.
Identifying the users, resources, and services to which each user needs access is crucial for cloud-native security. It lays the groundwork for enforcing the principle of least privilege, which aims to reduce risk by granting users the least amount of access they need to do their job well and maintain high productivity.
IT infrastructures in modern businesses are more decentralized than ever, and end users require on-demand access to an ever-expanding catalog of cloud services. This article provides an overview of the most pressing issues in identity and access management, as well as suggestions for how to deal with them.
Top Challenges of IAM & How You Can Overcome Them
Managing user identities and permissions is a complex task. However, it must be accomplished correctly to ensure that the procedure is smooth for the company.
Using a practical approach, you can execute a seamless procedure that will benefit your organization and help you overcome identity and access management difficulties.
The following are the major challenges of using IAM for cloud and SaaS applications while keeping on-premises systems safe and the right solution to deal with each.
1. Lack of centralized view
As companies switch from storing their data on-site to storing it in the cloud, centralized on-site data has become decentralized. This gives different departments more freedom but makes IAM more dangerous.
In a centralized system, all organization's users share the same username. This gives the admin control over who can access company data, but it also means that they are in charge of managing user identities, user credentials, user profiles, and user identification (ID) attributes.
As you move data away from a central location, you may need to employ decentralized identity management. In decentralized identity management, each department has its user identification system.
Each department is in charge of a user's identity and access rights, which are not shared with other departments. This means that each department takes on some duties of centralized administration.
The advancement of technology has made it far simpler than ever before for employees to perform their jobs in the comfort of their homes. Because of this, managers must have the ability to keep track of who may access particular systems. This can be challenging, particularly when the organization needs a centralized system for managing access privileges across the board. In addition, if IT and finance managers lack a centralized perspective of applications, they'll have little to no understanding of the resource waste costs.
Keeping this in mind, Zluri’s SaaS management platform empowers you to get a centralized view of all the SaaS apps in your organization. It keeps track of app users and gives real-time insights into app usage.
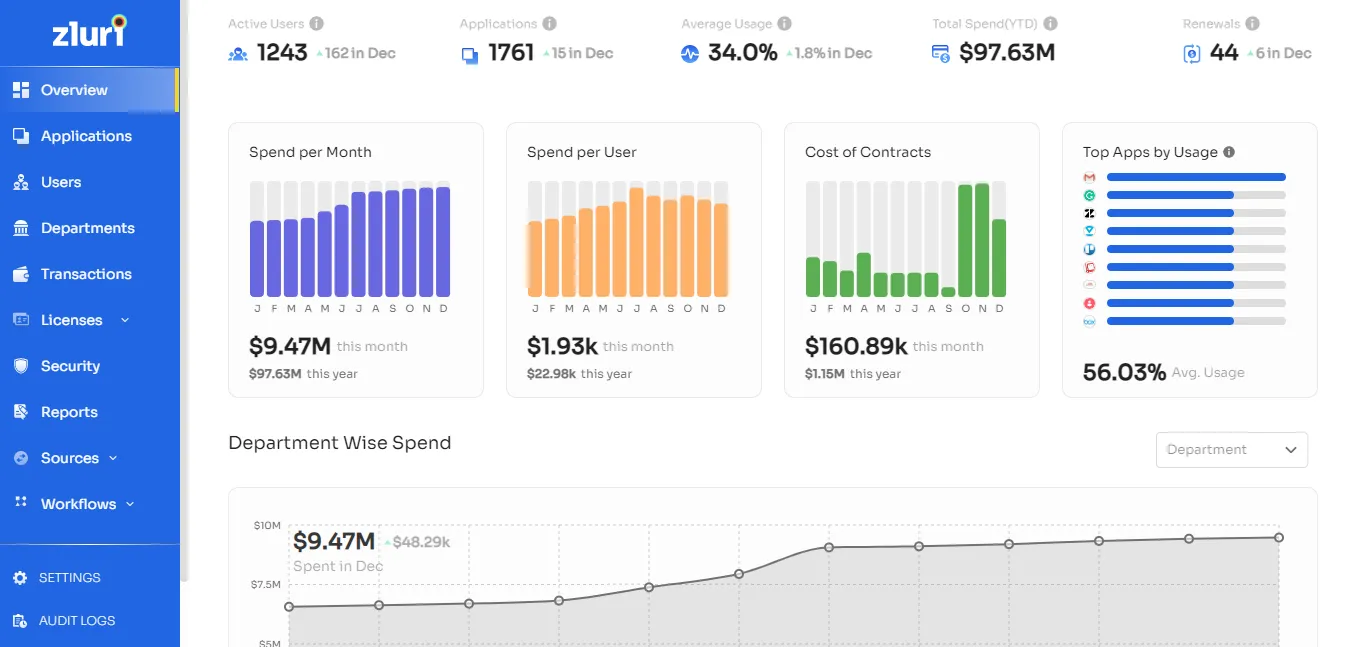
Zluri integrates with several single sign-on and identity providers and collects directory information. In addition, it gathers a list of authorized apps and login events from the SSO. These include sign-in attempts, the number of times a user has tried to access an app, and whether or not the attempt was successful.
Moreover, it keeps the IT admin informed about the apps being used actively and unused so that they can take appropriate actions at the time of renewal.
2. Difficulties in User Lifecycle Management
User lifecycle management is a strategic and tactical plan for onboarding new users, setting up a procedure that enables each user to work smoothly across multiple devices and services on the network and remove the access promptly during offboarding.
When a user successfully logs in to the cloud, the system gives them a certain amount of its resources, such as processing time, memory, storage space, and bandwidth. Depending on the system's space, these resources could be available even when logged out.
Manual Provisioning and Deprovisioning Process
IT usually gives new employee access to the company's network, file servers, email accounts, and printers when they start working there. However, since many SaaS applications, like Salesforce, are managed at the department level, access to these apps is often given by the application's admin instead of a single IT person.
Since SaaS apps are built to work on demand, it should be easy to provision them centrally. As a natural part of the onboarding process, a modern IAM solution should be able to automate the provisioning of new SaaS apps.
When a user is added to a core directory service (like Active Directory), their membership in certain security groups should ensure they are automatically given the right applications and access permissions for their role.
Similarly, offboarding an employee is a greater concern for IT teams. IT can revoke access to email and corporate networks from a central location. Still, they rely on external application administrators to revoke access to each SaaS application for a former employee. This puts the company at risk as important business apps and data are now in the hands of former employees.
Mid-Lifecycle Management (Change of role due to promotion, etc.)
Managing the mid-lifecycle of employees is critical for any organization since this model is used to identify and explain the crucial stages an employee goes through during his employment period in the organization. In addition, it gives staff members a standardized set of procedures to adhere to during their employment with the company and aids management in evaluating data.
For example, a user has been promoted to the marketing manager position. As a result of this new role assignment, the user will now have access to the specific collection of associated resources.
Roles are digital entities linked to specific applications through permissions called 'entitlements.' These define what a user of a role can and can't do with their access. For example, as users' jobs change within an organization, they may need access to different resources and no longer need access to others. Using Roles makes it easy to switch departments and give or take away access.
Zluri automates repetitive IT operations like employee onboarding and off-boarding, making them faster and safer. IT/HR teams no longer have to manually onboard new SaaS users, which is time-consuming and exhausting. It can provide work tools on or before the first day of onboarding. Access can be provided to users for new apps or tools for a new role assigned. Thus, it helps manage the employee mid-lifecycle management.
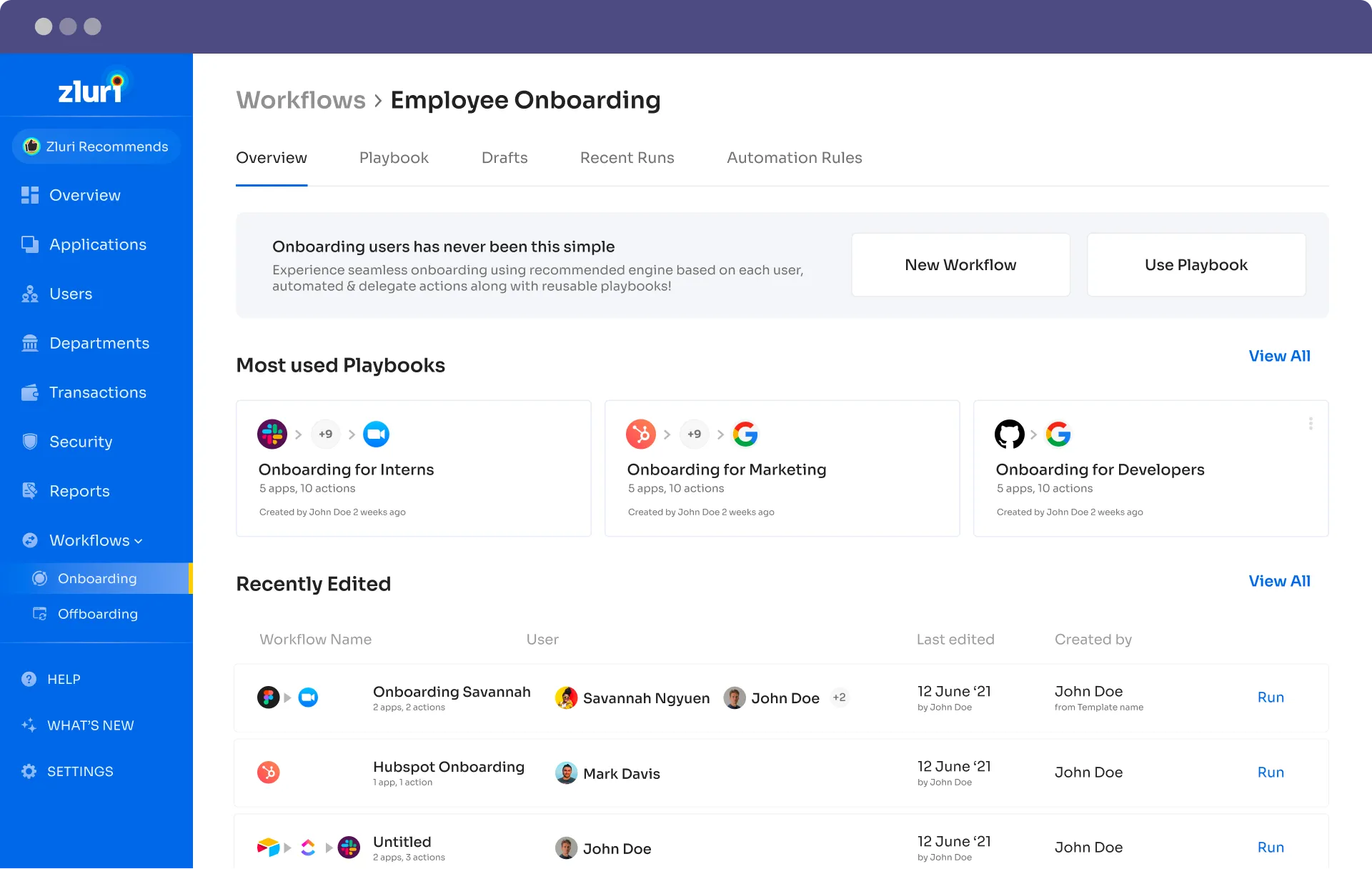
Zluri's use of case-driven process automation is unique. The system contains a lot of data to assist users in developing workflows. Zluri uses customized workflows that examine the new hire's job profile, seniority, and department to offer them access to applications instead of utilizing cumbersome templates.
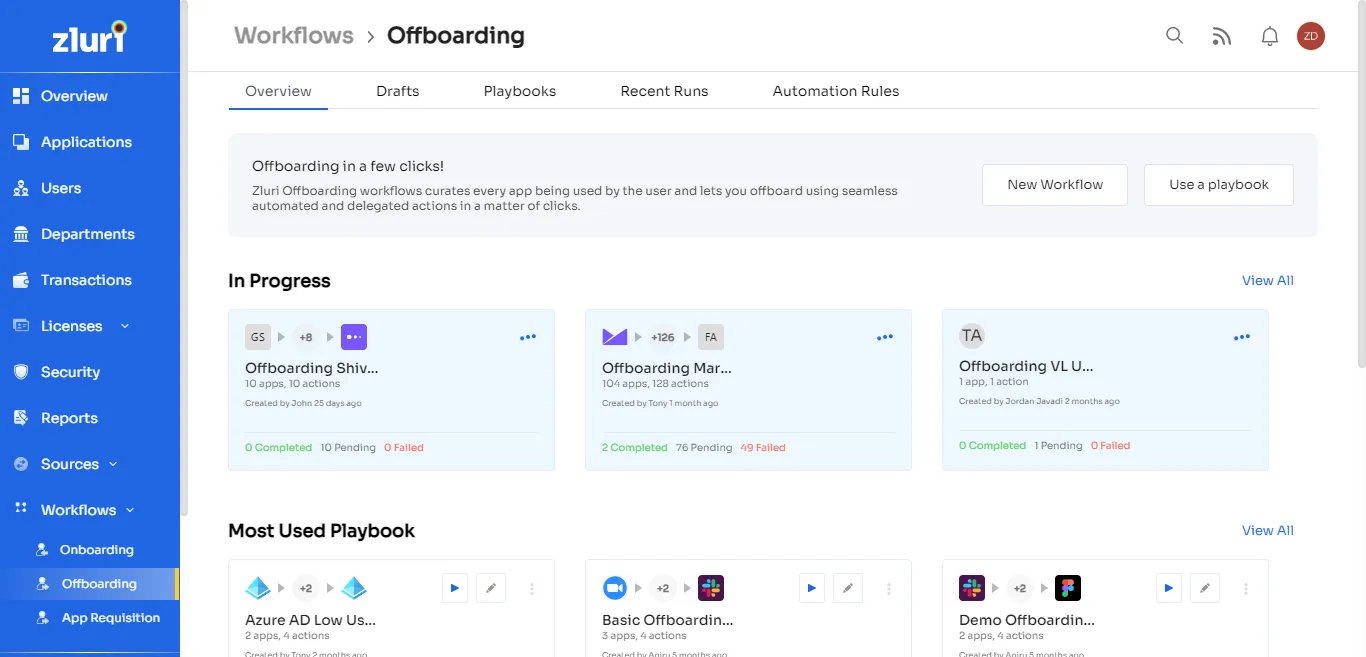
At the time of offboarding, Zluri removes access to all applications used by departing employees, not simply the SSO or Google workplace account. Zluri backs up application data before ending licensing, which you can transfer to a new owner.
Access Request Management
Organizations need to give employees access to the systems and data they need to do their jobs, but they also need to ensure that this access is safe. This can be hard to do, especially if there are many users in the organization.
Wistia_ID: svw7jw37f1
Access request management involves the process of receiving, evaluating, and approving or denying user requests to access various organizational data and resources. This process involves more than just figuring out who makes the request and what kind of access they want. It's a balancing act to ensure the organization runs safely and securely.
After the IT team has reviewed a request, the requestor will need to manually assign a role, provide an account in the requested app, be added to a group, etc. The common problem is that descriptions of access are written in business terms that are difficult to translate into precise technical terms.
Due to this lack of clarity, organizations likely fail to meet the principle of least privilege, put sensitive information and mission-critical resources at risk, and even violate compliance rules.
When IT takes longer to grant access to SaaS apps, it makes employees less productive and could lead them to buy without IT's permission. These shadow apps can cause SaaS sprawl problems like duplicate apps, apps that aren't used or used too little, and security and compliance problems.
One way to manage users is to divide them into groups and provide access to the systems and data it needs. This method can help lower the chance of data breaches and other security problems. But with user access management tools, each user can be given their own permissions and roles, making it easier to give and take away access as needed. With these tools, tracking and checking what users are doing is easier.
You can use Zluri's Employee App store as a quick and easy way to solve this problem. The employee app store lets employees request a license and check on the status of the request.
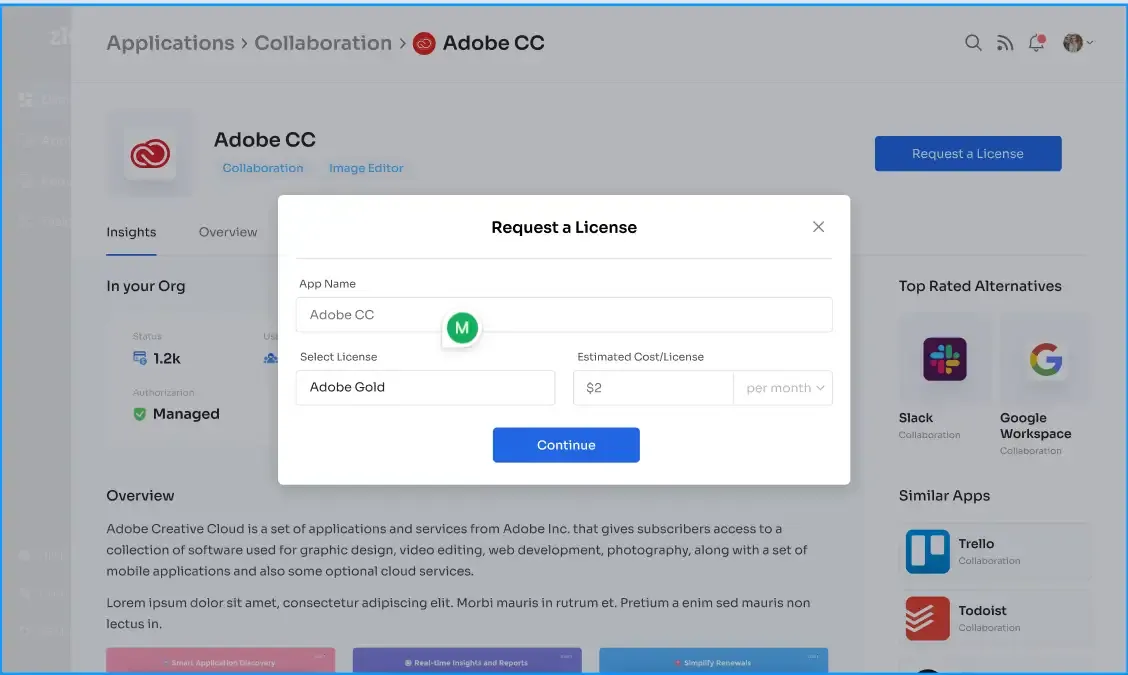
Employees can also ask for new apps if the ones they want aren't already in the SaaS stack. Also, this procurement request can be sent to Zluri's SaaS buying service to get a better deal. The employee app store dashboard has all your company's SaaS apps. Employees can view their applications and department apps. This aids them in selecting suitable apps.
The IT staff can now automate the SaaS approval process, define the number of approvers, and choose which apps and data departments/employees can see. IT staff saves time, and transparent SaaS purchases prevent shadow apps.
3. Keeping Application Integrations Updated
To centralize Single-sign-on and user management, you need to build integrations with different applications and keep track of the maintenance needs for each application's new versions. Most businesses cannot afford to have their IT departments handle their own set of 'connectors' across that ever-evolving ecosystem.
A solid cloud-based IAM solution keeps up with these changes to keep application integration and access updated and functional. The IAM service should mediate all integration technologies and methods, making IT difficulties transparent.
As APIs change and expand, the cloud IAM provider should handle these programmatic interfaces, relieving IT staff from the burden of tracking connector and application version requirements.
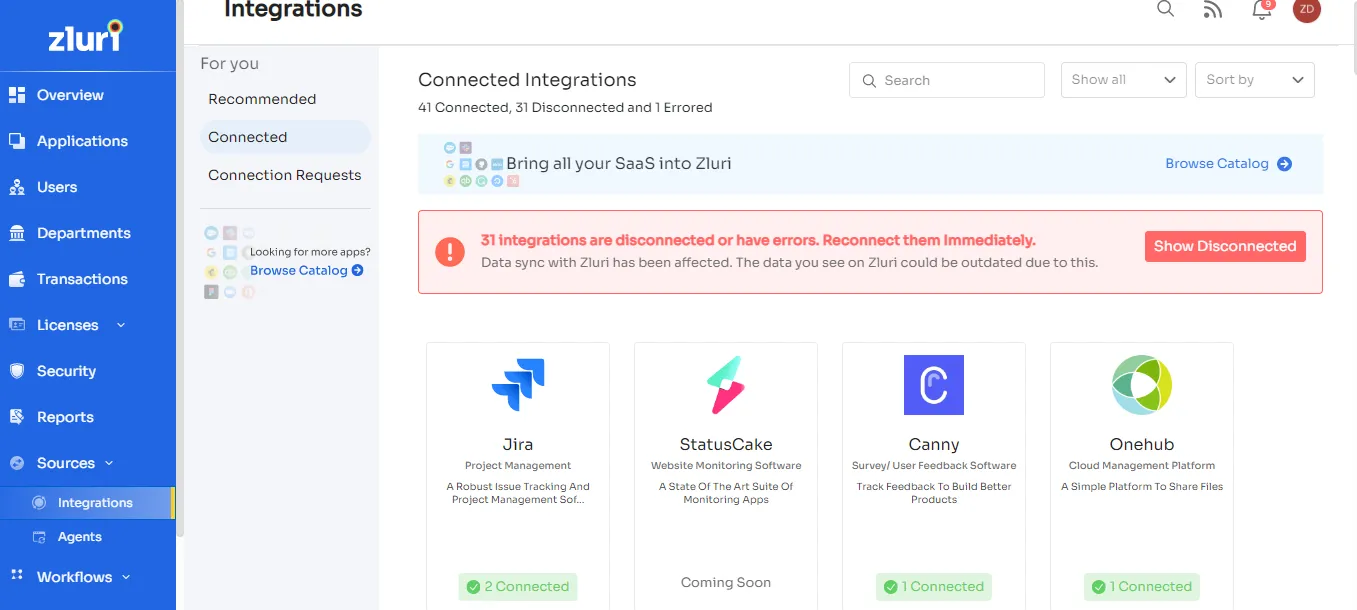
Zluri supports 750 integrations with the most popular SaaS applications in its integration library. Through direct integration, Zluri knows which users can access a SaaS app and what permissions they have. It also gathers user activity data that helps measure each user's overall SaaS usage.
4. Compliance Visibility into Third Party SaaS Tools
When it comes to cloud services, it's important to know who has access to applications and data, where they access it, and what they do with it. For auditing, there should be a central place where you can see and control all of your systems.
When it comes to cloud services, this is especially true. But only the most advanced services, like Salesforce, offer to report for compliance, and even then, it's only for one application.
If auditors question which employees have access to your applications and data, you need to be able to see and control all of your systems from one place. Your IAM service should let you set access rights across services and give you centralized compliance reports on access rights, provisioning and deprovisioning, and user and administrator activity.
Being in line with different security standards gives potential customers confidence and helps organizations protect their sensitive data from threats from inside and outside the company. Compliance prevents data breaches, makes audits easier, and takes less time.
Zluri has the ability to ensure that the organization's apps meet regulatory requirements. It automatically manages all SaaS applications' compliance and ensures that they align with associated compliance requirements. This results in applications always being ready for audits.






.png)


.svg)














