In the realm of organizational identity and access management, two pivotal concepts emerge as crucial components: Identity and Access Management (IAM) and Identity Governance and Administration (IGA). These concepts play integral roles in effectively managing user identities and access privileges.
By understanding the key differences between these two concepts, IT managers can make informed decisions about implementing the most suitable approach to safeguarding their digital assets and ensuring efficient access controls.
In the complex landscape of user identity and access rights management, IT managers require effective solutions to navigate the digital maze successfully. IAM and IGA emerge as the compass and guiding light, respectively, offering streamlined workflows, enhanced security measures, and simplified compliance efforts.
Wistia_ID: xdyx0ms4d9
By harnessing the power of IAM and IGA, IT managers can overcome pain points, empower productivity, strengthen security, and achieve regulatory compliance.
What is IAM?
In a world where efficiency and agility are paramount, the concept of identity and access management (IAM) emerges as a crucial framework. IAM encompasses a set of policies, technologies, and processes that are specifically designed to manage and control access to systems, networks, and data resources.
IAM ensures that each individual or entity is granted the precise access they need, preventing unauthorized access and potential security breaches. By implementing IAM, organizations can safeguard their resources and ensure that only authorized individuals or entities have appropriate access privileges.
Authentication is a crucial component of IAM, as it involves verifying the identity of individuals or entities seeking access to a system or resource. This process plays a critical role in ensuring that only authorized users gain access to the appropriate resources within an organization.
Moreover, IAM aids in enforcing security policies, streamlining access management procedures, and ensuring compliance with regulatory requirements. By centralizing and automating access control, IAM enhances efficiency, reduces administrative burdens, and promotes a secure environment for organizations and their sensitive data.
What is IGA?
Identity governance and administration (IGA) is a robust framework that extends beyond traditional identity and access management (IAM). It integrates a combination of policies, procedures, and cutting-edge technologies to empower you in effectively managing digital identities and access rights across diverse systems and applications.
IGA revolves around the central goal of safeguarding an organization's digital identities, guaranteeing their integrity, precision, and effective administration from beginning to end throughout the entire lifecycle. This encompasses various aspects, including the creation, modification, and termination of user identities and associated access privileges and entitlements.
By implementing IGA, you can establish a comprehensive and centralized approach to govern the entire identity lifecycle of your organization. This includes activities such as user provisioning, role management, access certifications, and policy enforcement.
IGA enables maintaining control and visibility over their digital identities, ensuring that the right individuals have the appropriate access rights based on their roles and responsibilities.
It is important to understand the distinctions between IAM and IGA. IAM focuses on providing secure access to resources, while IGA goes a step further by emphasizing identity governance, compliance, and risk management.
Let’s take a look at the key differentiating factors of IAM and IGA, highlighting their unique features.
Differences Between IAM & IGA
Following are some key differences between the two concepts:
1. Scope
IAM, with its granular attention to detail, primarily concentrates on efficiently managing user access to specific applications, systems, and data within an organization's ecosystem. It aims to ensure that users have the appropriate levels of access necessary for their roles, minimizing the risk of unauthorized entry or data breaches.
By implementing IAM solutions, you can establish secure user authentication, robust authorization protocols, and streamlined access controls tailored to your organization’s unique requirements.
On the other hand, IGA adopts a broader approach to digital identity management, encompassing a comprehensive range of practices and processes. IGA handles user access to applications and systems and extends its purview to include various vital aspects of identity governance. Along with provisioning, access certification, and policy enforcement, it also includes compliance management and overall governance strategies.
IGA is a comprehensive framework that harmonizes and orchestrates diverse identity management functions, ensuring adherence to regulatory requirements, internal policies, and industry best practices.
2. Governance & compliance
By implementing IAM solutions, you can effectively manage user identities, their access privileges, and the overall lifecycle of user accounts. The focus lies on efficient administration and optimization of access, bolstering productivity while reducing security risks.
On the other hand, IGA goes beyond the realm of user access management and delves into the intricate world of governance and compliance.
While IAM lays the foundation for user access, IGA is specially designed to ensure that an organization's identity management practices align with internal policies, industry regulations, and government mandates. It functions as a comprehensive framework encompassing tools and processes that enable access certification, risk assessment, and policy enforcement.
Within the governance domain, IGA serves as a powerful mechanism for establishing robust controls and maintaining a well-defined hierarchy of responsibilities. It enables you to enforce segregation of duties, preventing unauthorized access and potential fraud. By implementing IGA solutions, you can define and enforce policies governing the entire identity lifecycle, from user provisioning to access revocation. This not only fortifies security but also ensures adherence to compliance standards.
3. Integration
While IAM primarily focuses on managing user access within a single system or application, IGA extends its reach to encompass a broader scope.
IAM solutions provide functionalities such as user provisioning, authentication, and authorization, ensuring that individuals have the appropriate level of access to perform their duties effectively within a specific context. This approach is suitable for scenarios where user access management remains confined to a single system or a limited number of applications.
On the other hand, IGA solutions encompass a more comprehensive approach to managing identities and access across an organization's entire digital landscape. By integrating with multiple systems, applications, and even business processes, IGA enables you to establish a unified view of identity data and access rights. This centralized perspective allows you to gain better visibility and control over user access throughout the enterprise ecosystem.
4. Identity lifecycle management
IAM primarily centers around streamlining the provisioning and authentication processes, granting appropriate access levels, and ensuring secure user authentication. By implementing IAM solutions, you can bolster their security posture, mitigate data breaches, and enforce compliance with industry regulations. This allows you to manage user access privileges efficiently, improving operational efficiency while minimizing security risks.
On the other hand, IGA incorporates additional functionalities related to the entire lifecycle of digital identities, from their inception to eventual retirement. While IAM primarily focuses on granting access rights, IGA expands the purview by encompassing crucial identity governance aspects such as role-based access control, segregation of duties, and policy enforcement.
With IGA, you can establish and enforce comprehensive governance policies, ensuring user access rights align with business policies and regulations. It enables you to implement access request management, ensuring that the requested access aligns with established governance policies and regulations. It enables you to maintain appropriate access controls based on users' roles and responsibilities, reducing the risk of unauthorized access or potential data breaches.
5. Functions & capabilities
The core function of IAM is to ensure that only authorized individuals or entities can gain access to specific resources within an organization's infrastructure. IAM solutions typically offer robust authentication mechanisms such as multi-factor authentication (MFA), single sign-on (SSO), and password management to enhance security and streamline access for employees, partners, and customers.
Additionally, IAM systems provide authorization controls to manage permissions and entitlements, ensuring that users have the appropriate level of access based on their roles and responsibilities.
On the other hand, IGA focuses on audit, certification, and access discrepancy resolution. IGA solutions enable you to establish comprehensive identity lifecycle processes, encompassing user provisioning, deprovisioning, access requests and access review workflows. These processes facilitate regular audits and certifications to ensure compliance with regulatory requirements and internal policies.
Moreover, IGA systems help identify and resolve access discrepancies by comparing user entitlements against defined access policies, reducing the risk of unauthorized access or excessive privileges
The complexity and scale of modern technology environments demand a comprehensive solution that ensures seamless control and visibility over user access across the organization. Enter Zluri—a cutting-edge platform revolutionizing identity governance and administration, empowering you to maintain unparalleled control and visibility over user access.
Zluri's Intelligent Solution for IGA: Streamlining Access & Enhancing Security
Zluri understands the intricate nature of user access management in the modern business world. With various SaaS applications being used by different teams within an organization, tracking who has access to what becomes increasingly difficult. Mismanaged access can lead to security risks, compliance issues, and operational inefficiencies, making it crucial to have a robust identity governance and administration solution in place.
Zluri offers intelligent solutions to address your IGA requirements, focusing on streamlining access management and enhancing security. Through features such as data discovery, user lifecycle management, access requests, and access certifications, Zluri protects your organization's applications and sensitive information.
Data Engine: Unveiling Insights with Discovery Methods
Zluri's data engine, fueled by cutting-edge discovery methods, is your IT team's ultimate ally in effortlessly analyzing and uncovering SaaS app and user-related data. With nine robust discovery methods, including MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional), you gain a comprehensive view of your organization's application landscape.

Zluri’s nine discovery methods
Through these discovery methods, your team can quickly identify who has access to specific applications, pinpoint active users, scrutinize permissions granted, and even identify critical users accessing the apps. This level of granularity provides invaluable insights that strengthen your organization's security posture and compliance efforts.
Manually categorizing SaaS apps and recording user access data can be a time-consuming and resource-intensive task. That's why Zluri's data engine takes automation to the next level. It automatically identifies managed, unmanaged, and shadow IT apps, allowing your IT team to reclaim valuable time and resources. Say goodbye to tedious manual tasks and hello to a more efficient way of managing your app ecosystem.
Maintaining a secure access environment is paramount, and Zluri makes it a breeze for your IT team. With Zluri's intelligent IGA solution, you can ensure that the right employees have appropriate permissions for service accounts, eliminating the risk of unauthorized access. Take charge of access permissions, tighten security, and stay ahead of potential threats.
Automation Engine: Efficient access & user lifecycle management
With Zluri's advanced automation engine, your teams can say goodbye to manual access management hassles and welcome streamlined processes that enhance efficiency and bolster security. Streamlining the user lifecycle is a multifaceted task that extends beyond merely managing user access. It encompasses the delicate process of granting appropriate access, adapting permissions to match evolving roles, and securely revoking access when needed.
This crucial aspect enables your IT team to maintain seamless operations without compromising the safety and security of your organization's valuable SaaS app data.
1. Streamlining provisioning by creating an onboarding playbook
Zluri takes the hassle out of user access provisioning by streamlining the entire process and liberating your IT team from repetitive tasks. Manual provisioning has become a thing of the past, as Zluri's platform seamlessly automates these operations. Rest assured that authorized employees receive the right level of access to essential SaaS apps and data when needed, reducing the risk of human errors and over-provisioning.
Empower your IT team with Zluri's intuitive interface, allowing them to effortlessly create and customize onboarding workflows. With these workflows in place, your team can efficiently grant secure access to multiple new employees simultaneously, tailored to their specific job entitlements, roles, positions, and departments.
Designing these workflows is a breeze with Zluri's user-friendly interface, enabling your IT team to configure access privileges based on job roles and responsibilities with just a few clicks. Embrace Zluri's workflow capabilities to witness increased efficiency, enhanced employee productivity, and heightened security for your users and SaaS app data. Say goodbye to the complexities of access provisioning and embrace a seamless and efficient solution with Zluri.
To streamline the Onboarding process using Zluri, follow these straightforward steps:
Step 1: Access Zluri's workflow module and select "Onboarding" from the dropdown menu. Begin creating your onboarding workflow by clicking on "New Workflow."

Step 2: Select a user for onboarding; easily choose the user(s) you wish to onboard. You can manually select them or utilize the search bar to find specific employees. Simply click "Continue" to proceed.

Step 3: On the left side, explore the recommended apps and select the necessary ones for the user. Define the desired actions for each application to tailor the onboarding process.

Step 4: Customize actions further by selecting "Edit Action" and providing the required details. If needed, schedule these actions to execute on the day of onboarding. Once finalized, save the actions by clicking on "Save Task."

Step 5: To preserve the workflow for future use, select "Save as Playbook." Name your playbook in the prompted dialogue box and click "Save Playbook." Your onboarding workflow is now ready to be utilized.

Note: Zluri's solution stands out with its playbooks' exceptional reusability and flexibility. Update them effortlessly whenever necessary, ensuring ongoing efficiency within your onboarding process.
2. Streamlining deprovisioning by creating an offboarding playbook
When an employee leaves your organization, whether due to resignation, retirement, or termination, managing their access can be a time-consuming and complex task. However, with Zluri's intelligent lifecycle management platform, the entire deprovisioning process becomes effortless and highly efficient. Not only does this save you valuable time and effort, but it also ensures the security of your data.
Zluri's platform automatically revokes the departing employee's access to all devices, apps, and systems, preventing any unauthorized access to sensitive information. Additionally, it takes care of data backup and transfer to a new owner, safeguarding essential data from being lost.
Furthermore, Zluri handles the revocation of the employee's licenses and eliminates their single sign-on (SSO) access, effectively blocking their usage of any organization applications. By following this straightforward process, you can consistently and securely offboard employees with ease and confidence.
Now, to streamline the Offboarding process using Zluri, follow these straightforward steps:
Step 1: Access Zluri's main interface and navigate to the workflow module. From the drop-down list, select the offboarding option and click on "New Workflow."

Step 2: Choose the user(s) you wish to offboard by selecting "Select the user for offboarding." Once you've made your selection, click "Continue."

Step 3: Zluri provides recommended actions tailored to specific apps. Effortlessly choose from a range of suggested actions and execute them across the selected applications.

Step 4: To include additional actions, click "Add an Action." Fill in the necessary details and save the task by clicking "Save Task.".

Step 5: Finalize the workflow by saving it as a playbook. Provide a name, and click "Save Playbook," your offboarding workflow is now set and ready to go.
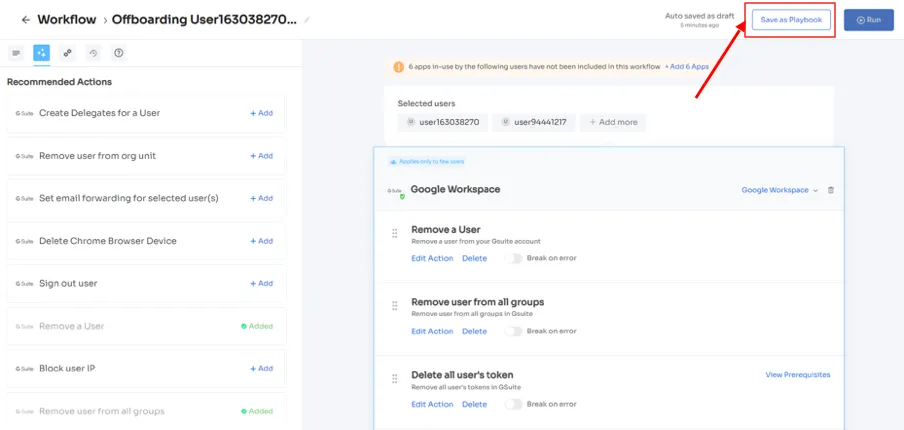
Note: With these playbooks, you have the power to design workflows and define actions based on specific triggers and conditions, tailoring the automation precisely to your organization's unique requirements and processes. The possibilities are limitless; through this automation, deprovisioning processes are supercharged, guaranteeing swift and accurate access revoking.
3. Access Request Management
Managing access privileges during role or department changes can be a complex task for your team. It is crucial to ensure that employees have the necessary permissions to perform their new job responsibilities while eliminating any unnecessary access rights. Enter Zluri's groundbreaking self-serve model, the Employee App Store (EAS), designed to revolutionize this process and simplify your access management.

No longer will you rely on manual processes to manage employee permissions. Instead, the EAS enables your team or approver to review and approve access requests based on the suitability of the requested permission levels for each employee's specific job role.
By implementing Zluri's IGA solutions, you gain unparalleled governance over access privileges, ensuring that sensitive information remains protected within your organization's confines. With this cutting-edge technology at your disposal, you can effortlessly prevent unauthorized access to critical data and maintain full control over what tools and resources your employees can access.

The robust approval system sets the stage for seamless decision-making, featuring three distinct levels: app owners, reporting managers, and IT admins. This multi-tiered approach ensures that higher authorities have the ultimate power to override decisions made by admins or managers at lower levels, enabling swift and decisive action when needed.
Transparency lies at the core of Zluri's IGA solutions. The innovative platform allows decision-makers to include comments when rejecting an app request, providing comprehensive explanations for their decisions. This fosters transparency throughout the access request process, ensuring that employees understand the rationale behind each determination.
But it doesn't stop there. Zluri's intelligent solutions empower approvers with the ability to modify specific requests, tailoring access to align precisely with your organization's requirements. Keeping stakeholders informed is key, which is why Zluri's IGA solutions offer a comprehensive "changelog" feature. Users can easily track updates, ranging from approvals or rejections of requests to changes in license duration or tier.

Additionally, the changelog captures valuable insights, including comments added by any admin, facilitating a collaborative and informed approach to access management.
Access certifications
In the dynamic landscape of cybersecurity, user access reviews have emerged as a critical pillar for safeguarding organizations' digital assets. Maintaining the right balance between granting appropriate access privileges and mitigating potential security risks is paramount to prevent data breaches and unauthorized activities.
Time is of the essence in the corporate world, and Zluri's IGA solution recognizes this. Access reviews are now completed at a breathtaking pace by harnessing the power of automation. What used to be a time-consuming and cumbersome process is now streamlined, allowing admins to focus on mission-critical tasks. With Zluri's IGA solution seamlessly handling the bulk of the review process, you'll experience a staggering tenfold increase in review efficiency. Say goodbye to tedious manual reviews and hello to lightning-fast access assessments.
Let’s see how Zluri's IGA solution revolutionizes user access reviewing by providing a unified access platform and implementing automated review mechanisms.
Unified Access: A 360-Degree View of Digital Identities
Imagine a unified access management approach that empowers you and your teams with an all-encompassing view of your organization’s access landscape. Zluri's IGA solution makes this vision a reality, seamlessly consolidating user access-related information from diverse sources within a singular, intuitive platform. No more juggling multiple directories or disparate identity repositories—everything you need to understand access privileges and user activity is now at your fingertips.
- Access Directory: At the core of Zluri's IGA lies its robust capability to capture and organize user information from various sources, including active directory and other identity repositories. No more worrying about incomplete or inaccurate records; Zluri ensures that every user identity and their associated access privileges are meticulously recorded and easily accessible for review.
- Access Privileges: With Zluri's unified access, admins gain an unprecedented vantage point to oversee and manage user access privileges across the entire organization. This enhanced visibility allows for swift identification of any potential access discrepancies or suspicious permissions, creating a formidable defense against cyber threats. Ensuring the right users have the right access at all times has never been more efficient.
- Activity & Alerts: Stay ahead of potential security breaches with Zluri's proactive approach. Our IGA solution tracks user activity in real-time, triggering instant alerts for anomalous behavior or unauthorized access attempts. This vigilant alert system acts as your early warning mechanism, enabling you to take immediate action against any security risks.
Automated Reviews: Unleashing the Power of Automation
Manual access review processes can be a significant hindrance to productivity and security. Zluri's IGA solution introduces a game-changing approach with its cutting-edge automated review capabilities. By seamlessly integrating automation into access management, Zluri's IGA ensures that your organization operates more efficiently, reduce human errors, and enhance security.
- Access Rules: Zluri's IGA solution puts you in control of defining access rules and policies based on roles, responsibilities, and business requirements. Through automation, the platform conducts instant reviews and validations of user access against pre-established criteria, eliminating any potential ambiguities in the process. This ensures that only authorized personnel can access critical resources, minimizing security risks and compliance issues.
- Scheduled Certification: Bid farewell to irregular access reviews that can lead to lapses in security. Zluri's IGA brings a forward-thinking scheduling feature that automates system-generated reviews at regular intervals. This proactive approach ensures that access rights remain up-to-date with the organization's ever-evolving security policies, maintaining a consistent and compliant environment.
- Auto Remediation: Rest easy knowing that Zluri's IGA solution has your back regarding security vulnerabilities. The platform flexes its muscles with automated remediation actions, efficiently addressing potential risks. Whether it's promptly revoking access, notifying users and managers, or initiating access request workflows for approvals, Zluri's IGA ensures that you take control of access management like never before. By automating these processes, your team can swiftly respond to security threats and maintain a robust security posture.Take, for instance, a multinational corporation managing a vast network of employees, each with varying access needs. Zluri's IGA simplifies granting and validating access, significantly reducing administrative overhead. Furthermore, if an employee's role changes or when they depart from the organization. With Zluri's automated reviews and scheduled certifications, access rights are updated promptly, ensuring data remains protected and compliance is upheld.
Wondering how to automate user access reviews? Zluri’s comprehensive ‘Access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the "Access certification" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.
- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the "Application" review method if desired and add the relevant application(s) to be audited for users' access.

- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.

- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.
Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.

- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the "Save Template" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the "Review Stage" section.It’s no secret that administrative overhead can be a drag on any organization's productivity. However, with Zluri's IGA solution ensuring the automation of access reviews, the burden on your team is drastically reduced. Experience a remarkable 70% reduction in manual efforts, allowing your team to reallocate their time and talents to more strategic initiatives. Unleash the full potential of your workforce as they focus on high-impact projects and drive your organization forward.Experience the power of Zluri's intelligent solutions for IGA and optimize your access management today. Stay ahead of the curve, enhance efficiency, and fortify your security framework like never before. Book a demo today!







.png)

.svg)














