As an IT manager, you understand the criticality of maintaining effective identity management and access control. With multiple identity governance and administration (IGA) tools available in the market, choosing the right one for your IT team can be daunting.
SailPoint and ForgeRock offer powerful identity governance solutions that can make it tough for you to decide which one to choose. However, a thorough comparison of these IGA solutions can assist you in making a well-informed decision.
Imagine this scenario: Your organization recently experienced a security breach due to unauthorized access to sensitive data. The incident resulted in reputational damage, financial losses, and regulatory penalties.
As an IT manager, you were tasked with investigating the incident and finding ways to prevent similar breaches in the future. During your analysis, you realized the importance of implementing a robust IGA solution that can streamline access management, enforce security policies, and ensure compliance with regulatory requirements.
To make an informed decision, you need a thorough understanding of SailPoint and ForgeRock. By evaluating each solution's strengths, weaknesses, and unique features, you can determine which IGA tool aligns best with your organization's specific needs.
Let's delve into the key aspects of SailPoint and ForgeRock to compare their identity governance capabilities.
SailPoint vs ForgeRock: Comparison Based on 5 Parameters
Let’s explore the various parameters.
1. Unique category
- SailPoint is categorized as password management, identity and access management, access risk management, and identity security tool.
- ForgeRock is categorized as access management, identity management, identity governance tool, and directory services.
2. Integration capabilities
- With SailPoint, your team can integrate with (?) various systems, applications, directories, and databases within your organization. This integration ensures that critical data and identity information are synchronized across platforms, providing a holistic view of user access and reducing administrative burden.
With SailPoint, your team can integrate your IAM system with other business-critical applications, such as HR systems, IT service management platforms, and even cloud-based SaaS applications. This integration streamlines user provisioning, access request, and certification processes, enabling efficient management of user identities across your entire technology landscape.
SailPoint also integrates with popular cloud platforms such as Microsoft Azure, Amazon Web Services (AWS), and Salesforce. This integration ensures that access controls and user entitlements are effectively managed across cloud-based applications, enabling your IT team to enforce consistent security and compliance measures. - ForgeRock offers versatile integration capabilities that enable seamless connectivity with a wide range of systems, applications, and devices.
ForgeRock's integration capabilities are designed to seamlessly adapt to a wide range of technology landscapes, including on-premises systems, cloud platforms, and IoT devices. This empowers your IT team by providing them with the tools they need to manage user identities and access controls across multiple environments centrally.
One of ForgeRock's standout integration capabilities is its focus on identity relationship management (IRM). ForgeRock's IRM integration capabilities enable your team to establish and manage complex relationships between identities, enhancing risk mitigation and compliance enforcement across interconnected ecosystems.
ForgeRock also offers integration capabilities for emerging technologies such as artificial intelligence (AI), machine learning (ML), and blockchain. These integrations enable your IT team to leverage advanced analytics, adaptive authentication, and decentralized identity models, ensuring they are prepared to tackle evolving security and compliance challenges in the digital era.
3. Securing identities
- SailPoint’s identity governance platform enables your team to manage and govern identities throughout their lifecycle. They can use SailPoint to streamline access requests and approvals while ensuring that access is granted based on users' roles, responsibilities, etc.
One of SailPoint's standout features is its advanced identity analytics and risk intelligence capabilities. By leveraging machine learning and AI algorithms, SailPoint identifies access patterns, detects anomalies, and assesses risk levels associated with individual identities.
These insights equip your team with actionable intelligence to make informed decisions regarding access privileges, helping mitigate potential risks and strengthen overall security.
Moreover, SailPoint facilitates compliance management by automating access certifications and audits, ensuring that user access rights align with established policies and regulations. This streamlines the compliance process, saves time and effort, and helps your team demonstrate adherence to industry standards and regulations. - On the other hand, ForgeRock identity governance provides intelligent authentication and authorization mechanisms to strengthen identity security. Adaptive authentication allows your team to dynamically assess risk factors such as user behavior, location, and device characteristics.
By analyzing these contextual factors in real-time, ForgeRock ensures that the appropriate level of authentication is applied, minimizing the risk of unauthorized access. Moreover, granular authorization controls enable your IT team to enforce fine-grained access policies, granting users the precise privileges they need, enhancing security without hindering productivity.
In addition, the platform enables your IT team to implement privacy-centric controls that align with regulatory requirements such as GDPR and CCPA. Your team can define and manage user consent preferences, ensure transparent data handling practices, and empower identities to have control over their personal information.
4. Access management capabilities
- With SailPoint, your team can centralize access governance across your entire organization, allowing them to gain better visibility and control over user access rights. Your team can define and manage access policies, roles, and entitlements through a user-friendly interface, ensuring that access privileges align with your organization’s requirements and compliance regulations.
SailPoint enables your team to automate user provisioning and deprovisioning processes, making onboarding and offboarding employees, contractors, and partners effortless. This streamlined approach saves time and effort and minimizes the risk of unauthorized access.
SailPoint also incorporates robust authentication and single sign-on (SSO) capabilities. With SailPoint, users can enjoy a seamless and secure sign-on experience across multiple applications using a single set of credentials. Additionally, SailPoint supports multi-factor authentication (MFA), adding an extra layer of security by verifying user identities through additional factors like biometrics or SMS codes. - With ForgeRock, your team can establish a centralized access management system that enables them to define and enforce access policies across various applications and systems. By ensuring access privileges align with your organization's policies and compliance regulations, ForgeRock helps you mitigate security risks and maintain regulatory compliance.
The tool offers a highly customizable and user-friendly interface that enhances the access management experience for both admin and end-users. With ForgeRock's flexible identity and access management solutions, your team can create personalized access journeys tailored to specific user roles and needs.
Moreover, ForgeRock provides support for standards such as OAuth 2.0 and OpenID Connect, enabling secure and interoperable access to APIs and applications. Additionally, ForgeRock offers adaptive authentication, which intelligently evaluates risk factors and applies the appropriate authentication measures, such as multi-factor authentication (MFA), based on contextual information.
5. Pricing and rating
- SailPoint adopts a flexible and modular pricing structure designed to accommodate the diverse requirements of organizations. Its pricing model typically consists of a base license fee that covers the core functionality of the IAM platform. This includes features such as identity governance, user provisioning, and access certifications.
Additionally, SailPoint offers various add-on modules that allow you to customize the IAM solution based on specific needs. These modules could include advanced features like privileged access management, password management, or data access governance.
The pricing for the add-on modules is usually calculated based on factors such as the number of users, desired functionality, and the scale of deployment. - On the other hand, ForgeRock offers a pricing model that is often based on a per-user or per-identity basis. This means you pay for the number of users or identities managed within the ForgeRock platform.
The pricing structure considers the various components of IAM, such as authentication, authorization, and identity management. ForgeRock's pricing can be further influenced by factors such as the number of applications integrated, the level of customization needed, and the support and maintenance services required.
Additionally, ForgeRock offers different editions of its platform, ranging from standard to enterprise editions, each with its own set of features and pricing levels.
While both SailPoint and ForgeRock provide comprehensive IAM solutions, their pricing models differ primarily in determining costs.
SailPoint's approach emphasizes modularity and flexibility, allowing you to tailor their IAM solution to their specific needs by selecting and pricing individual modules. On the other hand, ForgeRock's pricing is more user-centric, charging based on the number of users or identities managed within their platform.
Ultimately, the choice between SailPoint and ForgeRock would depend on your team's unique requirements and their organization, as well as their preferences regarding pricing structures and scalability.
Customer rating of SailPoint:
- G2: 4.4/5
- Capterra: 4.2/5
Customer rating of ForgeRock:
- G2: 4.4/5
Once you've learned about the differences, you likely know which IGA tool would be perfect for what you need. But there are other tools, like Zluri, that also do a great job of making it easier for your IT team to manage and secure user access.
What exactly is Zluri, and how does it provide secure access? Let's give you a quick summary.
Zluri - An Autonomous and Automated Solution For Your IGA Needs
Embrace easy SaaS adoption while ensuring efficient identity governance and identity administration – that's crucial for your organization. Unfortunately, many solutions prioritize user data and overlook this essential aspect. But fear not because Zluri stands out with a unique approach.
Zluri offers the ultimate solution for your identity governance and administration needs. It empowers your IT team, giving them complete control and clear visibility over user access management. Monitoring and managing multiple SaaS applications becomes effortless with Zluri's convenient dashboard, ensuring authorized and secure access to critical tools.
But Zluri doesn't stop there! It goes above and beyond with a range of exceptional features that help your IT team efficiently manage the entire process. Let's explore its capabilities one by one, so you can fully grasp its power and benefits.
Now let’s see how Zluri helps you with identity governance and administration.
Gain visibility into users’ SaaS data with a powerful discovery engine
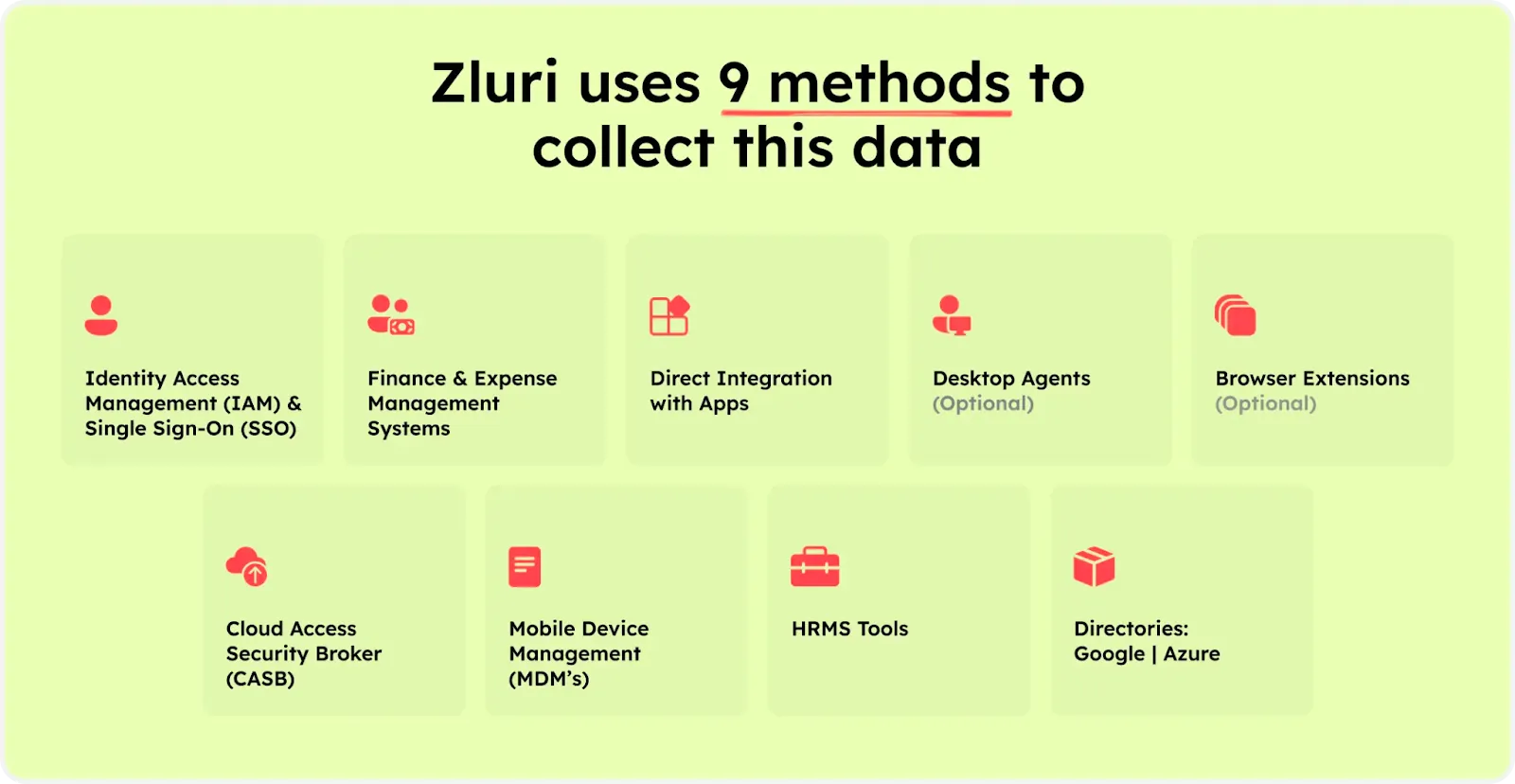
But Zluri doesn't stop there. It takes a step further by integrating with over 300+ SaaS applications. This means you get real-time data, valuable insights, and AI-powered alerts to keep you informed. This allows you to extract relevant information about user activities, permissions, and usage patterns. With this data, you can confidently perform access reviews and ensure the security and efficiency of your SaaS environment.
With API-based integrations, Zluri ensures thorough data discovery across all your SaaS applications, leaving no information hidden. You can trust us to provide 100% visibility into your SaaS environment.
Moreover, the platform boasts the largest library with over 240,000 apps, allowing us to provide detailed access data and dive into the specifics. This gives you a comprehensive understanding of user permissions and access levels within your SaaS ecosystem.
Simplify your access management with Zluri’s automation engine
Zluri's automation engine is like a self-driving system for your organization. It takes care of access workflows effortlessly, ensures smooth and efficient automation with thorough reviews, and follows a clear set of rules and policies.
Now, let’s explore Zluri’s IGA capabilities.
Lifecycle Management
With Zluri, your team can streamline user provisioning and deprovisioning, guaranteeing effective access management within your organization. By offering customizable permissions based on roles, departments, and seniority levels, Zluri ensures that every employee has appropriate access to the necessary tools with the right level of approval for their success.
When it's time for an employee to leave your organization, Zluri simplifies the process of revoking access to sensitive data and tools with just a few clicks. With Zluri, your team can confidently manage your organization's applications and secure valuable data, ensuring peace of mind and efficient control.
Let's see how Zluri does this.
- Making sure users have the right access to tools through a streamlined process for setting up their accounts
To give secure access to the new employees using Zluri's user-friendly interface, follow these simple steps:
Step 1: Go to the workflow module within Zluri's platform. From the drop-down menu, select the onboarding option. Click on "New Workflow" to proceed to the next step.
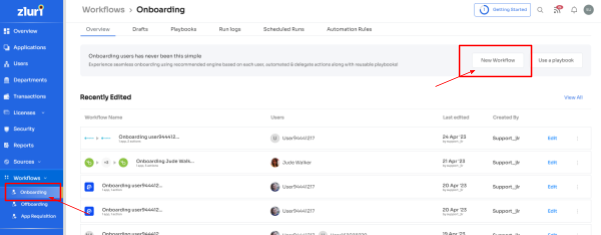
Step 2: Now, your team can choose the user(s) that need to give access to. Your team can use the search bar to locate a specific employee or browse through the list quickly. Once they select the employee(s), click "Continue" to move forward.

Step 3: Zluri provides contextual-based app recommendations based on factors such as the user's role, department, and even seniority level. This ensures that new employees have a smooth onboarding journey, increasing productivity and ensuring secure access.

Step 4: Zluri assists your IT teams by providing in-app suggestions. These suggestions help them automate additional tasks, such as adding users to relevant channels or sending them welcome messages in apps like Slack.

Step 5: Further, with Zluri, your team can save workflows as "playbooks'' for future use. This eliminates the security risks when onboarding employees with similar designations, user roles, permission levels, etc.
Note: These onboarding playbooks assist you in ensuring the right level of access to the right users at the right moment, safeguarding your sensitive data, and enhancing overall productivity.

- Effortless workflows to remove user access and ensure top-notch security
Zluri provides a convenient solution for automating user deprovisioning. This feature ensures that the user’s accesses are revoked, maintaining data security and compliance. Here's how you can use this feature:
Step 1: Access Zluri's main interface and navigate to the workflow module. Select " offboarding " from the drop-down and click "New Workflow."
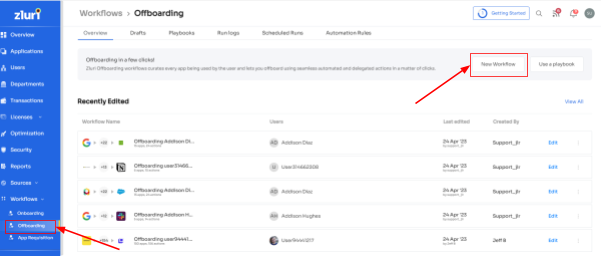
Step 2: Your team will find a dedicated offboarding user box within the platform. Here, your team can locate the employee(s) you want to offboard. They can either scroll through the list or use the search bar to find them. After selecting the users to offboard, click on "Continue" to proceed.

Step 3: Next, your team can review all the applications that the offboarded employee had access to. Also, they can click on each application to see the suggested actions under "recommended actions."
Choose and execute the necessary actions based on the recommendations for the applications.
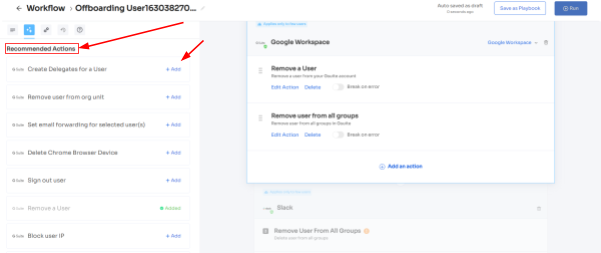
Step 4: Save the workflow as a "playbook" for future use. This allows your team to use the same playbook to deprovision users in the future.
Note: These offboarding playbooks help ensure that ex-employees cannot access your organization's data, leading to improved security and compliance with necessary regulations.

Further, with Zluri’s entitlement management capabilities, you can easily manage access to applications when you hire new employees. Instead of manually assigning access rights based on roles, Zluri automates the process for you.
With Zluri, your IT team gains full control over who can access each application. They can set up detailed access rules to make sure each user has the right level of access based on their role. This helps prevent unauthorized access and reduces the risk of data breaches. Zluri makes access management simple and efficient!
Access Request Management
When a user's role changes due to a mid-lifecycle transition, it's important for your team to ensure that unnecessary access is removed and the required permissions are granted based on their new job role or seniority. Zluri's Employee App Store (EAS) simplifies this process.
With the EAS, your IT team gains control over employees' access to necessary tools. For instance, access requests can only be approved if the requested permission level aligns with the employee's job role, ensuring access governance and preventing unauthorized access to sensitive information.

Zluri offers a transparent approval system with three levels: app owners, reporting managers, and IT admins. Higher authorities have the authority to override decisions made by lower-level admins or managers.
Additionally, decision-makers can include comments when rejecting an app request, providing an explanation for transparency in the access request process.
Approvers can also modify specific requests. For example, if an employee requests a "Asana Enterprise" license, approvers have the flexibility to change it to "Asana Premium" during the approval process if necessary.
Users can stay updated on their requests through the "changelog," which highlights approval or rejection status, changes in license duration or tier, and comments added by any admin.

Access Certifications
Zluri offers a powerful solution for simplified user access review and permission management! With Zluri, you gain a centralized platform that empowers security, GRC, and auditors to effortlessly review and report on user access.

Zluri streamlines the access review process by enabling you to set review parameters, choose reviewers, and schedule campaigns with ease. Through intelligent automation, it assesses user access rights based on predefined rules, saving time and minimizing errors compared to manual spreadsheet reviews.

But that's not all - Zluri goes the extra mile by offering auto-remediation capabilities. It takes immediate corrective actions if access violations are detected, enhancing your organization's security and ensuring compliance. By automatically revoking access for terminated employees or those with outdated privileges, Zluri helps safeguard against unauthorized data breaches, keeping sensitive information secure.
Rest assured, Zluri generates comprehensive reports that provide valuable insights into access patterns, vulnerabilities, and compliance status. These reports make it effortless to demonstrate compliance to auditors and make well-informed decisions about access management.
So, what makes Zluri truly stand out? Let's explore its unique features:
Continuous Access Reviews: Maintain control over access privileges with recurring and scheduled certifications. This ensures consistent review and validation of access permissions, quickly identifying and addressing security weaknesses. Scheduled certifications allow planned and timely evaluations, minimizing the chances of missing critical access issues.

Real-time Access Reviews: By harnessing AI's power, Zluri enhances data security and compliance processes. By conducting real-time access reviews and analyzing access patterns, user behavior, and system logs, Zluri identifies unusual or potentially risky activities. This allows proactive mitigation of security threats and the protection of sensitive data.

Industry-Standard Certificate Templates: Zluri provides easy-to-use certificate templates that simplify the certification process. These templates offer a standardized approach, making certifications efficient, comprehensive, accurate, and aligned with recognized guidelines.
AI Compliance Capabilities: Zluri's AI technology aligns access controls with industry regulations and standards, reducing the risk of compliance violations. By simplifying the compliance process, Zluri ensures your organization meets regulatory requirements effortlessly.

Here are the steps to automate the access review process.
- Step 1: Open Zluri's main interface, and go to the "Access Certification" module.
- Step 2: Now, to create an access certification, click on "Create a New Certification." Now, assign a suitable certification name and assign a responsive owner.
- Step 3: Under the setup certification, choose how you want to review users' access: either by Application, or Users.For example, if you select to review access by Application, add the application to audit users' access.

- Step 4: Choose a primary reviewer and a fallback reviewer from the drop-down menu. Once you are done selecting the reviewers, you can click on “Next.” Note: Generally, the primary reviewers are app owners. Also, choose the fallback reviewer carefully whom you think is responsible.

- Step 5: Choose the specific users to include in the certification process. You can also filter the data points such as user department, job title, usage, and more, as per your certification requirements. Then, click on "Next."Note: Select those relevant data points only that you wish your reviewers to see while reviewing the access. By filtering the criteria appropriately, you enable your reviewers to make swift and well-informed decisions, streamlining the review process and ensuring efficiency.
- Step 6: Configure actions based on your needs and choose from the drop-down options.

- For example, for rejection action, you can select the respective deprovisioning playbook to revoke the unnecessary access of the users. Once you set up the action, click “add applications”. Note: You can add multiple applications for the same certification.
- Step 7: Set the start and end dates for the certification process, depending on within what time span you want the review to be completed.Note: You can also click "Save Template" to save it for future use.
- Step 8: Lastly, you can keep track of the automated access review process by clicking on the ‘Review Status’ and view whether the review is still pending, modified, declined, or approved.Finally, you can easily track the entire review process on a chart. Once the review is complete and the assigned reviewer approves it, you can click 'conclude' to instantly send the reports to their email.To learn more about Zluri’s Identity Governance, Book a demo today!






.png)


.svg)














