As an IT manager, keeping up with finance compliance certifications is essential. These certifications help you handle all the complicated rules and regulations smoothly. Also, it prevents your organization from getting into trouble with the law and keeps your reputation intact.
Handling extensive financial data—such as client payment details and transaction records—demands robust compliance with stringent standards. These standards, mandated by regulatory bodies, encompass encryption, secure storage, and stringent access controls to mitigate the risks of data breaches and unauthorized access.
Financial compliance standards are pivotal guidelines that govern financial operations, ensuring transparency, integrity, and accountability. Adherence fosters trust and credibility among clients and partners, promotes fair competition, and upholds market integrity by preventing unfair practices. Non-compliance can result in severe penalties, reputational damage, and legal consequences.
Navigating these compliance challenges is essential. This article will explore the critical financial regulatory standards required for ongoing compliance.
Simplified regulatory checklist for financial institutions:
- Implement robust data protection measures, such as encryption protocols and secure access controls, to safeguard sensitive customer information.
- Regularly assess and address vulnerabilities through comprehensive cybersecurity measures.
- Train and educate employees on data privacy best practices to ensure consistent adherence to security protocols.
- Maintain accurate and up-to-date records of financial statements, transactions, and regulatory filings.
- Develop documentation retention policies to ensure compliance with reporting requirements.
- Conduct regular internal audits to verify the accuracy and completeness of records.
- Implement measures to protect against cyber threats and ensure quick recovery in case of a breach or disaster.
- Ensure you have qualified individuals serving as compliance officers.
This article will explore the various financial regulatory standards required to remain compliant.
Top 6 Financial Compliance Regulations
Now, let’s discuss the regulatory standards for financial institutions.
1. Payment Services Directive (PSD2)
PSD2 is a regulatory framework implemented by the European Banking Authority (EBA) to enhance the security and openness of payment services within the EU. It sets out guidelines for organizations that provide or facilitate payment services, including banks, fintech companies, and other financial institutions.
As an IT manager, you ensure your organization's adherence to PSD2. Compliance with this regulation brings several benefits to your company.
Firstly, it enhances security by introducing strong customer authentication (SCA) measures. SCA requires customers to provide at least two forms of identification when making electronic transactions, reducing the risk of fraud and unauthorized access to sensitive data.
Moreover, PSD2 compliance encourages innovation by promoting open banking. Open banking allows customers to share their financial data securely with authorized third-party providers (TPPs) through application programming interfaces (APIs). This enables you to ensure that your organization's systems and APIs comply with PSD2's technical standards to facilitate secure data sharing.
Adhering to PSD2 also ensures your organization's competitiveness in the market. It enables your organization to participate in the growing ecosystem of payment service providers, opening doors to new revenue streams and strategic collaborations.
In addition, to achieve PSD2 compliance, you should collaborate closely with various stakeholders, including legal and compliance teams, developers, and third-party service providers. This collaboration involves reviewing and updating security protocols, implementing secure APIs, and regularly monitoring and testing the systems to ensure compliance with PSD2 requirements.
2. Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is a set of security requirements established by major card brands to protect cardholder data and prevent fraud. It focuses on securing payment card transactions and the data associated with them.
PCI DSS outlines a comprehensive set of controls and best practices to be implemented that process, store, or transmit payment card data. Adhering to PCI DSS is essential for maintaining your clients and vendors' trust, reducing the risk of data breaches, and upholding your organization's reputation.
Adhering to PCI DSS can also lead to operational efficiency and improved security practices. The standard provides a framework for implementing robust security controls, including network segmentation, access controls, encryption, vulnerability management, and regular security testing.
To ensure PCI DSS compliance, conduct regular assessments, implement appropriate security measures, and provide employee training and awareness programs. Additionally, maintaining documentation and evidence of compliance is vital to demonstrate adherence to the standard's requirements.
3. Gramm-Leach-Bliley Act (GLBA)
Enacted in 1999, the GLBA aims to safeguard the privacy and security of customers' non-public personal information (NPI) held by financial institutions. While the GLBA primarily targets financial organizations, it indirectly impacts the IT infrastructure and practices within these institutions, making adherence to the regulation essential.
The GLBA requires financial institutions to implement measures that protect customer information's confidentiality, integrity, and availability. This includes adopting comprehensive information security programs that identify and assess potential risks, implement safeguards to mitigate those risks, and regularly monitor and update these safeguards.
Adhering to the GLBA has several benefits for financial institutions. Let’s discuss the benefits.
- Compliance with the GLBA helps establish trust and confidence among clients. When clients know their personal and financial information is being protected, they are more likely to engage with the institution and maintain long-term relationships.
- GLBA compliance promotes good data governance practices. The regulation requires financial institutions to document their information security policies and procedures, conduct regular risk assessments, and develop incident response plans. Following these guidelines can enhance your organization's data governance framework, ensuring the appropriate handling, storage, and disposal of customer information. Such practices also help identify vulnerabilities and weaknesses in the IT infrastructure, allowing for prompt remediation and reducing the risk of data breaches.
- Adherence to the GLBA helps you align your security practices with the required industry standards. The regulation sets a baseline for information security requirements, which includes implementing access controls, encryption, network monitoring, and regular employee training.
By incorporating these measures, you can strengthen your institution's security posture, reduce the likelihood of data breaches, and demonstrate due diligence in protecting customer information.
4. The Sarbanes Oxley Act (SOX)
SOX was enacted in the early 2000s. It establishes a set of rules and standards to promote transparency, accountability, and accuracy in financial reporting, directly impacting your IT operations.
The primary objective of SOX is to protect shareholders and the general public from accounting errors and fraudulent activities within organizations. It imposes strict requirements on recording, storing, and auditing financial data.
Your team plays a vital role in complying with these requirements by ensuring the proper functioning of your IT systems, data security measures, and internal controls. By adhering to SOX, you help safeguard your organization's financial information and uphold its reputation.
One key aspect of SOX is the establishment of internal controls over financial reporting (ICFR). These controls ensure that financial information is accurate and reliable, reducing the risk of errors or misstatements.
As an IT manager, you must implement and maintain effective internal controls within your IT infrastructure. This involves establishing access controls, segregation of duties, data backup and recovery procedures, and monitoring mechanisms.
Another important provision of SOX is the requirement for data retention and accessibility. The act mandates that you retain financial records and audit trails for a specific period, typically up to seven years. You are responsible for implementing appropriate data retention policies, ensuring secure storage, and enabling efficient retrieval of financial data when needed.
5. Anti-Money Laundering (AML) Directives
AML directives serve as guidelines provided by regulatory authorities to combat money laundering activities. In the IT industry, adhering to these directives requires implementing sophisticated tools, protocols, and procedures.
By doing so, you can detect and prevent suspicious financial transactions, identify potential risks, and establish a secure framework to ensure the integrity of their operations. This helps mitigate legal and reputational risks and fosters trust among clients, partners, and stakeholders.
The implications of non-compliance with AML directives can be severe, leading to hefty fines, legal consequences, and irreparable damage to a company's reputation.
Therefore, investing in advanced technologies such as machine learning algorithms, artificial intelligence, and big data analytics can streamline AML processes, enhance transaction monitoring capabilities, and identify suspicious patterns that might indicate money laundering activities.
Additionally, adhering to AML directives helps protect your organization from being inadvertently involved in facilitating illegal activities. Complying with AML regulations ensures that your company is not being exploited as a conduit for illicit funds, safeguarding your operations from potential legal liabilities.
Moreover, a robust AML program protects your company's interests and contributes to the larger goal of combating financial crime. It promotes employee awareness, ensuring proper training and fostering a culture of compliance. By doing so, you help build a safer, more secure financial environment for your organization and the industry as a whole.
6. BASEL III
BASEL III is a set of international banking standards developed by the Basel Committee on banking supervision. While its primary aim is to strengthen the global banking system, BASEL III also has significant implications for IT managers within financial institutions.
Understanding and adhering to BASEL III can contribute to your organization's financial stability, risk management, and regulatory compliance.
BASEL III also emphasizes the importance of risk management within banks. It emphasizes identifying, measuring, and monitoring various types of risks, such as credit, market, and operational risks.
As an IT manager, you are responsible for implementing and maintaining the technological infrastructure that supports risk management activities. This includes ensuring the availability and integrity of data used for risk calculations, implementing robust security measures to protect sensitive information, and establishing efficient risk reporting mechanisms.
Furthermore, BASEL III promotes greater transparency and disclosure. Banks are required to provide more comprehensive and timely information to regulators, investors, and the public. You need to ensure that your organization's data management systems can capture and store relevant data, generate accurate reports, and disseminate information securely.
Finally, compliance with BASEL III allows your organization to improve its operational efficiency and resilience. By implementing the necessary systems and processes to adhere to BASEL III requirements, you can leverage technology and automation to optimize compliance efforts, reduce manual errors, and create a more agile and adaptable environment.
7. Payment Services Directive (PSD2)
PSD2 is a regulatory framework implemented by the European Banking Authority (EBA) to enhance the security and openness of payment services within the EU. It sets out guidelines for organizations that provide or facilitate payment services, including banks, fintech companies, and other financial institutions.
As an IT manager, you ensure your organization's adherence to PSD2. Compliance with this regulation brings several benefits to your company.
Firstly, it enhances security by introducing strong customer authentication (SCA) measures. SCA requires customers to provide at least two forms of identification when making electronic transactions, reducing the risk of fraud and unauthorized access to sensitive data.
Moreover, PSD2 compliance encourages innovation by promoting open banking. Open banking allows customers to share their financial data securely with authorized third-party providers (TPPs) through application programming interfaces (APIs). This enables you to ensure that your organization's systems and APIs comply with PSD2's technical standards to facilitate secure data sharing.
Adhering to PSD2 also ensures your organization's competitiveness in the market. It enables your organization to participate in the growing ecosystem of payment service providers, opening doors to new revenue streams and strategic collaborations.
In addition, to achieve PSD2 compliance, you should collaborate closely with various stakeholders, including legal and compliance teams, developers, and third-party service providers. This collaboration involves reviewing and updating security protocols, implementing secure APIs, and regularly monitoring and testing the systems to ensure compliance with PSD2 requirements.
How An IGA Solution Helps You Stay Compliant With The Required Financial Standards?
With SaaS's rapid growth, granting your employees special access privileges has become easier. However, managing and controlling these privileges has also become more complex, posing security risks and compliance challenges.
To maintain a secure and compliant environment, ensuring that the right individuals have the proper permissions is crucial. This is where an identity governance and administration (IGA) solution like Zluri comes in.
Zluri’s IGA platform revolutionizes how you manage access, helping you streamline IT audits, ensure compliance, and effectively control user access.
Zluri's IGA solution provides a powerful feature for reviewing user access, making managing and evaluating permissions simple. At first, Zluri leverages Nine discovery methods and integrates with over 300+ applications that help you gain 100% visibility into your SaaS landscape.
By identifying all the SaaS apps through a centralized platform, your IT teams gain complete visibility into your organization's SaaS ecosystem.
With this visibility, you can efficiently manage user access across the SaaS stack, handle access requests, and ensure compliance with required financial standards, maintaining appropriate access rights throughout your organization.
Let's take a closer look at how it works
Empower your user’s data with Zluri’s unified access
Zluri offers a unified access solution that simplifies the complex task of monitoring user access across different systems and applications. This unified access enhances your organization's security, boosts operational efficiency, and ensures compliance with financial regulations.
The unified access includes the following:
- Access Directory: It gives you centralized control over your organization's access permissions. You'll have a clear and comprehensive view of who has access to which resources and applications. This visibility is crucial for maintaining a secure environment and preventing unauthorized access, helping you comply with financial standards.For instance, let's consider a financial company with multiple branches and numerous employees. Keeping track of access rights becomes challenging. Managing various access lists, permissions, and user roles across different financial applications can be overwhelming. However, with Zluri's unified access, you can simplify this complexity, gain a clear overview of access rights, and ensure a secure environment for your organization's sensitive financial data. This enables you to stay compliant with the required financial standards and regulations.
- Access Privileges: Understanding and managing access privileges for your users is crucial in effective access management. Zluri makes it easy to define and monitor user roles, departments, and other relevant information determining their access privileges. This context may include factors like job roles, involvement in specific projects, or other pertinent data.Having this level of control allows you to ensure that each user has access only to the resources they need for their specific tasks. This reduces the risk of data breaches and enhances overall security, which is essential for maintaining compliance with financial standards.
Let's take an example from the financial sector.
Consider an accountant in your organization who handles sensitive financial data. With Zluri's assistance, you can precisely assign the necessary access to the accountant. They would have access to financial tools required for their role while being restricted from accessing other unrelated areas of your IT infrastructure. This way, you maintain compliance with the necessary financial regulations and protect sensitive financial information from unauthorized access.
- Activity & Alerts: With Zluri, you can get real-time insights into user activity, like login/logout times for various applications, to monitor user behavior and spot potential security threats. Zluri's proactive alerting system sends instant email alerts for any unusual activities or security breaches, enabling you to act swiftly and safeguard your IT environment. For instance, your company needs to adhere to strict data access controls. Zluri allows you to monitor user activities across all financial applications in real-time. If an employee attempts unauthorized access to sensitive financial data, Zluri's proactive alerting system immediately notifies you via email. This prompt alert empowers you to address the issue promptly and avoid potential compliance breaches, safeguarding your organization's financial data and reputation.
Streamline your access review process with automation
Enhance your access control system effortlessly with Zluri's automated reviews. Safeguarding your sensitive data and ensuring compliance with regulatory requirements is now easier than ever. Zluri's automated reviews capabilities offer valuable features, and it involves:
- Access Rules: With Zluri's access insights, you clearly understand your organization's access landscape. This valuable information forms the basis for creating precise access rules. For instance, if you discover certain employees have unnecessary access to financial data, you can quickly set up rules to limit their permissions and bolster data security.For instance, your organization needs to follow strict financial rules that say only a few people can have a view of money records. With Zluri's access insights, you can see that some of your employees can see crucial money data that they don't need.Using Zluri's access rules, you promptly establish strict access controls for sensitive financial information. This ensures that only authorized personnel can access such data, reducing the risk of data breaches and maintaining compliance with financial standards. Further, with Zluri's automated reviews, you can confidently safeguard your financial data and maintain a secure environment.
- Scheduled Certification: Zluri streamlines the certification process, making it easy to schedule certifications in advance. By setting up certification tasks based on valuable insights, you can ensure that employees' access aligns with the organization's policies and regulatory requirements. This proactive approach keeps access permissions up-to-date and compliant at all times.For instance, let’s consider a finance company that needs its employees to stay updated on financial regulations. With Zluri, the IT teams can schedule certifications to meet the finance compliance standards. This ensures that each employee has the necessary permissions to handle financial data correctly, avoiding any compliance issues.
- Auto-remediation: Taking access management to the next level, Zluri introduces auto-remediation capabilities. Beyond regular reviews, this powerful feature actively responds to access violations. If any unauthorized access or security breaches are detected, Zluri automatically triggers corrective actions for immediate resolution. This proactive approach enhances your organization's security and effortlessly maintains compliance with industry standards.For instance, if a team member in your finance department gets a promotion, adjusting their access privileges becomes effortless with Zluri. You can seamlessly modify their access to match their new responsibilities. Similarly, if a user has unnecessary access to sensitive financial data, Zluri's auto-remediation swiftly revokes their access, minimizing potential security issues.In short, traditional manual access reviews can be quite time-consuming and require significant human involvement. It involves coordinating with different departments, gathering data, and cross-referencing access permissions. Unfortunately, this manual approach can be monotonous and prone to human errors, which might result in compliance issues or security vulnerabilities.However, with Zluri's automated reviews, the burden of manual efforts is significantly reduced by up to 70%, and the review process becomes 10 times faster. Intelligent automation handles the heavy lifting, including collecting and organizing access data and analyzing access patterns. This ensures compliance with financial standards and allows your IT team to focus more on strategic initiatives, utilizing their time and skills more efficiently.
Now, let’s discuss the steps to automate the access review process.
- Step 1: Open Zluri's main interface and go to the \"Access Certification\" module.
- Step 2: To create an access certification, click \"Create a New Certification.\" Now, assign a suitable certification name and assign a responsive owner.
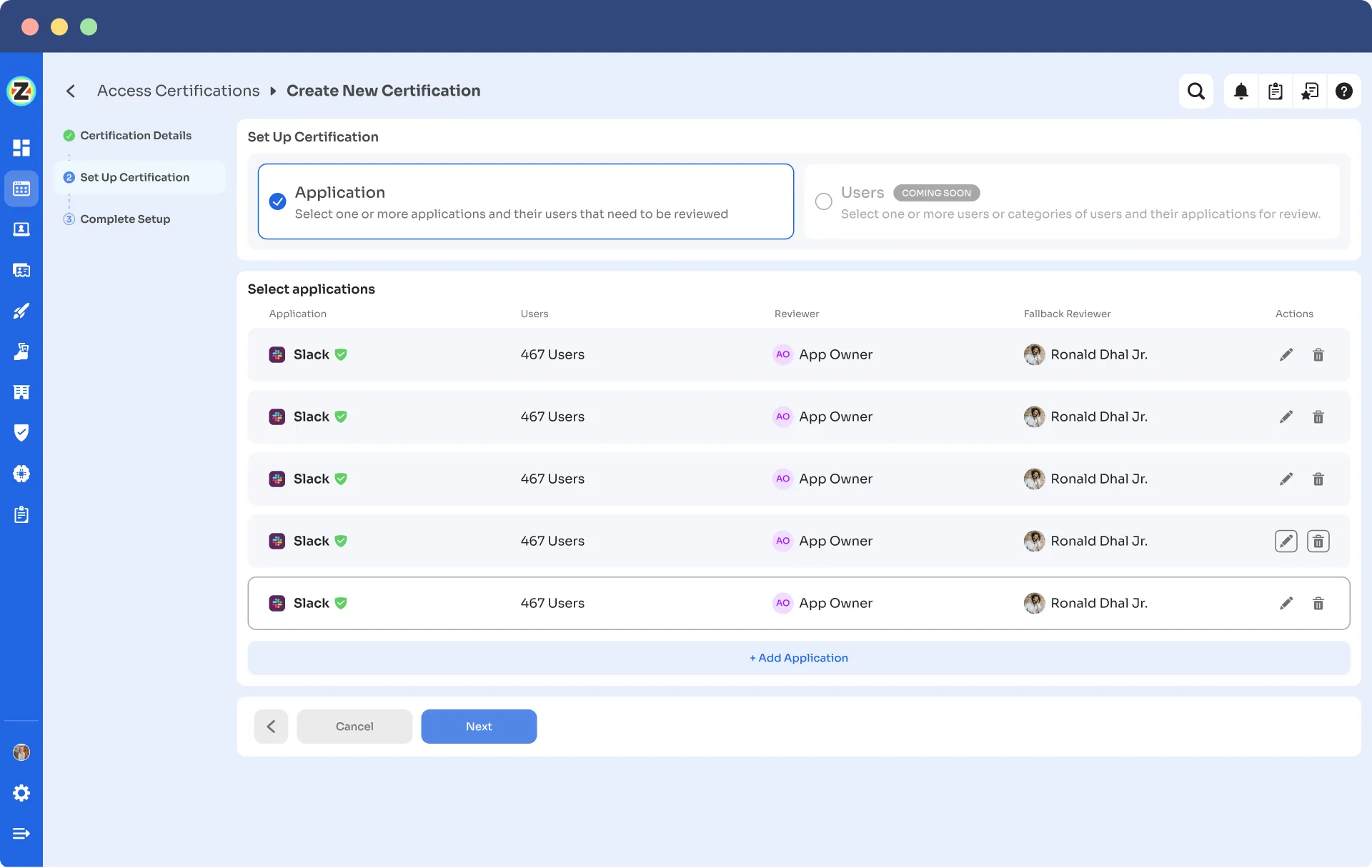
- Step 3: Under the setup certification, choose how you want to review users' access: either by Application or Users.
For example, if you select to review access by Application, add the application to audit users' access.
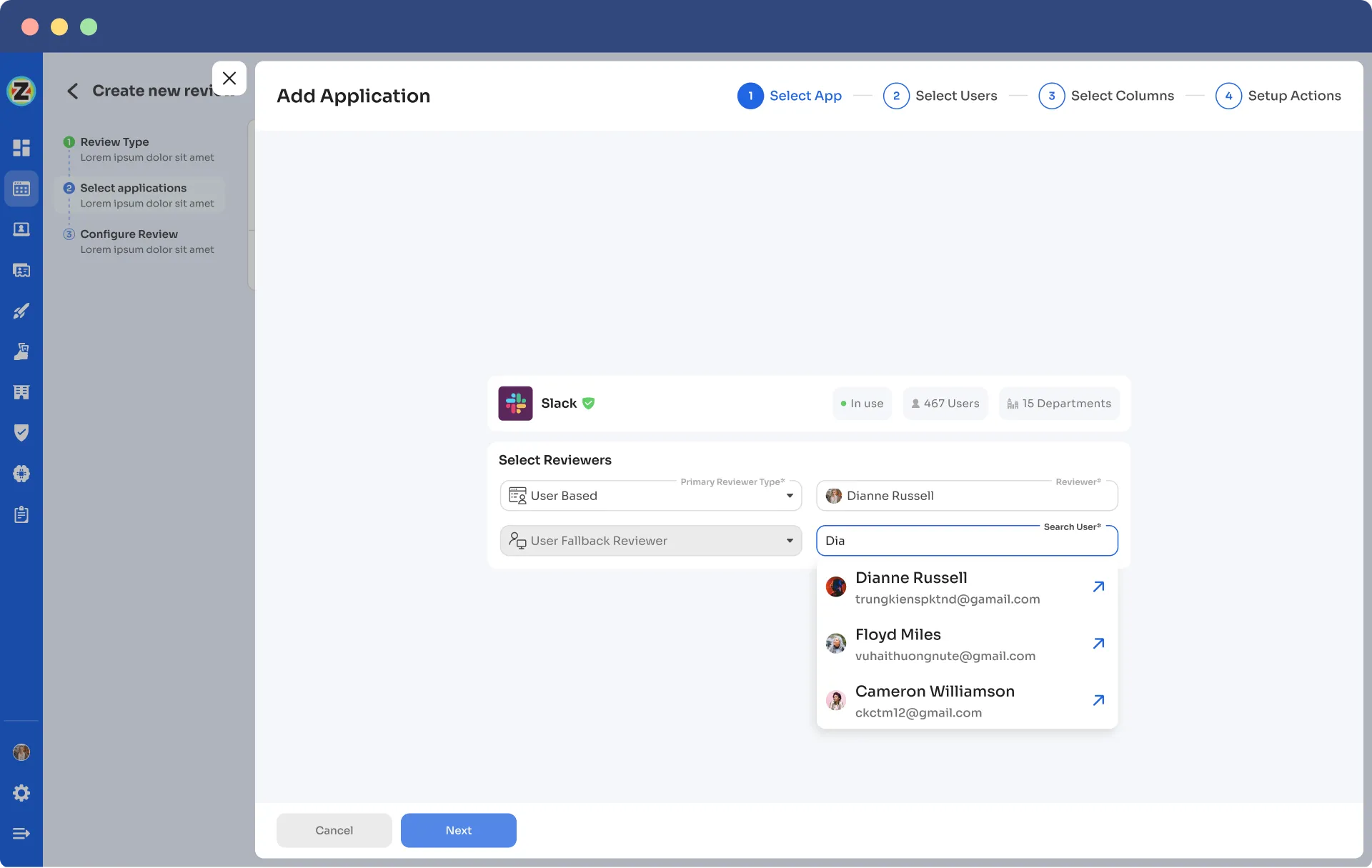
- Step 4: Then, choose a primary reviewer and a fallback reviewer from the drop-down menu. Once you are done selecting the reviewers, you can click on Next.
Note: Generally, the primary reviewers are app owners. Also, choose the fallback reviewer carefully whom you think is responsible.
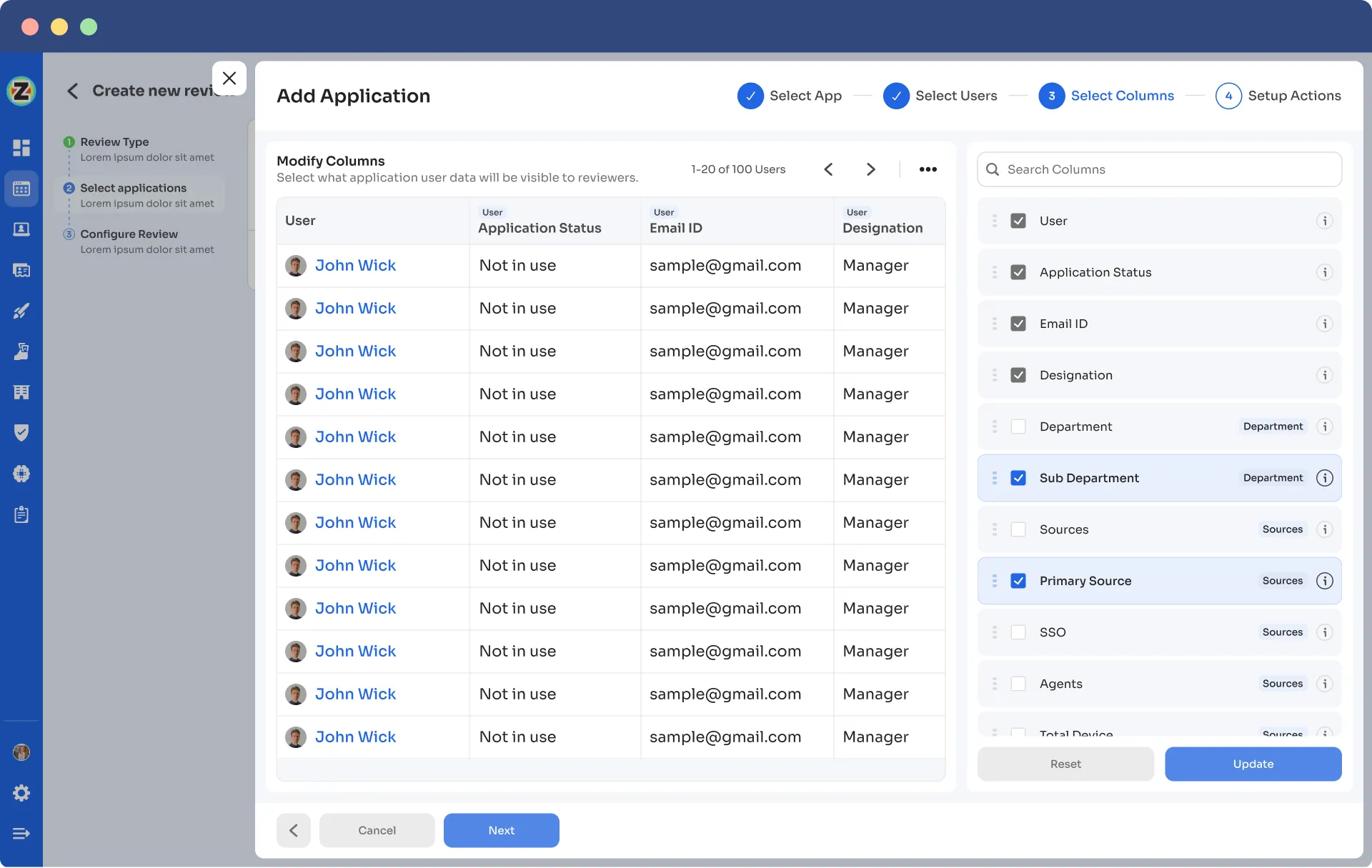
- Step 5: Choose the specific users to include in the certification process. You can also filter the data points, such as the user department, job title, usage, and more, as per your certification requirements. Then, click on \"Next.\"
Note: Choose only the important data points you want your reviewers to see during the access review. Using the right filters, you help them make quick and well-informed decisions, making the review process smoother and more efficient.
- Step 6: Now, configure actions based on your needs and choose from the drop-down options.
For example, for rejection action, you can select the respective deprovisioning playbook to revoke the unnecessary access of the users.
Once you set up the action, click “add applications”.
Note: You can add multiple applications for the same certification.
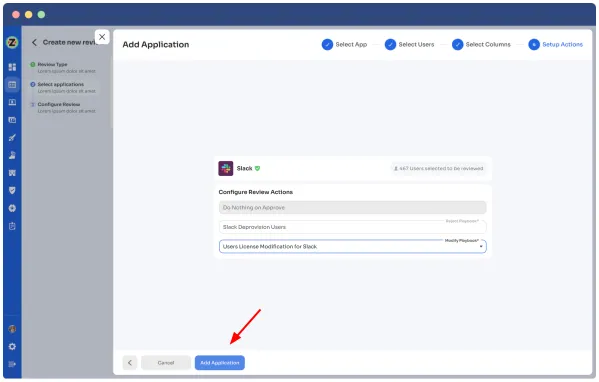
- Step 7: Set the start and end dates for the certification process, depending on the time span you want the review completed.
Note: You can also click \"Save Template\" to save it for future use.
- Step 8: Lastly, you can keep track of the automated access review process by clicking on the ‘Review Status’ and viewing whether the review is still pending, modified, declined, or approved.
Finally, you can easily track the entire review process on a chart. Once the review is complete and the assigned reviewer approves it, click 'conclude' to instantly send the reports to their email.
Want to know more about Zluri’s IGA capabilities, Book a Demo Now.






.png)


.svg)














