Access governance software provides you with a comprehensive solution to efficiently manage and control user access rights. Thus, in this article discover the top access governance software to choose the suitable one for your organization.
Access governance software offers a centralized platform that allows you to automate and streamline this entire access management lifecycle, from provisioning to deprovisioning. However, there are multiple access governance system available in the market and choosing the suitable one can be a daunting task.
Choosing a wrong access governance software could lead to unauthorized access, data breaches, and potential compliance violations. This might be due to lack of necessary features to effectively manage and monitor access rights.
Thus, choosing the right access governance system is not just about finding a solution that meets your current needs, but also one that can scale and adapt as your organization grows and evolves. Making an informed decision ensures that your organization remains secure, compliant, and efficient.
Now, let’s discuss the key features to look for in a suitable access governance software.
Key Features of Access Governance Software
Below mentioned are a few key features of access governance software:
- Centralized Access Control: The access governance software provides a centralized platform to manage and control user access rights across multiple systems and applications. With a unified view, you can efficiently grant, modify, or revoke access privileges, ensuring that employees have the right level of access to perform their roles effectively.
- Role-Based Access Control: Access governance tools simplify this process by implementing role-based access control (RBAC). With this, you can define user roles based on job functions or responsibilities and assign permissions accordingly.
- Automated User Provisioning and Deprovisioning: It automates the provisioning and deprovisioning processes, providing you with a seamless experience. With automated access provisioning, new employees receive the necessary access rights promptly, enabling them to start working without delays.
Similarly, when an employee leaves or changes roles, the software ensures timely deprovisioning of their access rights, mitigating the risk of lingering permissions and unauthorized access. - Access Certification and Compliance: Access governance tools simplify compliance management by offering access certification functionality. Through access certification campaigns, managers can periodically review and validate users' access rights, ensuring that access privileges align with business needs and compliance requirements.
- Audit Trail and Reporting: Access governance tools provide comprehensive audit trail capabilities, logging all access-related events and changes. This lets you track user access history, detect suspicious activities, and investigate potential security incidents.
Additionally, access governance systems offer customizable reports that provide insights into access patterns, compliance status, and user behavior, facilitating informed decision-making and enhancing overall security governance.
Let’s explore the top 11 access governance software along with its features:
Top 11 Access Governance Software
Let’s discuss the top access governance software.
1. Zluri
Zluri offers a powerful identity governance and administration (IGA) platform that allows you to ensure right and secure access to your entire SaaS landscape throughout the users’ lifecycle.
With Zluri's IGA platform, you can easily maintain control and enhance security through features, such as automated user provisioning, access reviews, and self-service access requests.
The platform empowers you to ensure that every user's access is adequately managed and aligned with your organization's policies. This strengthens security and helps you comply with the required regulations.
Let's explore how Zluri stands out from other data access governance software by offering unique capabilities.
- Powerful Discovery Engine
Zluri makes it easy for your IT team to analyze and uncover valuable data about your SaaS applications and users. We offer nine discovery methods to identify this information: MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
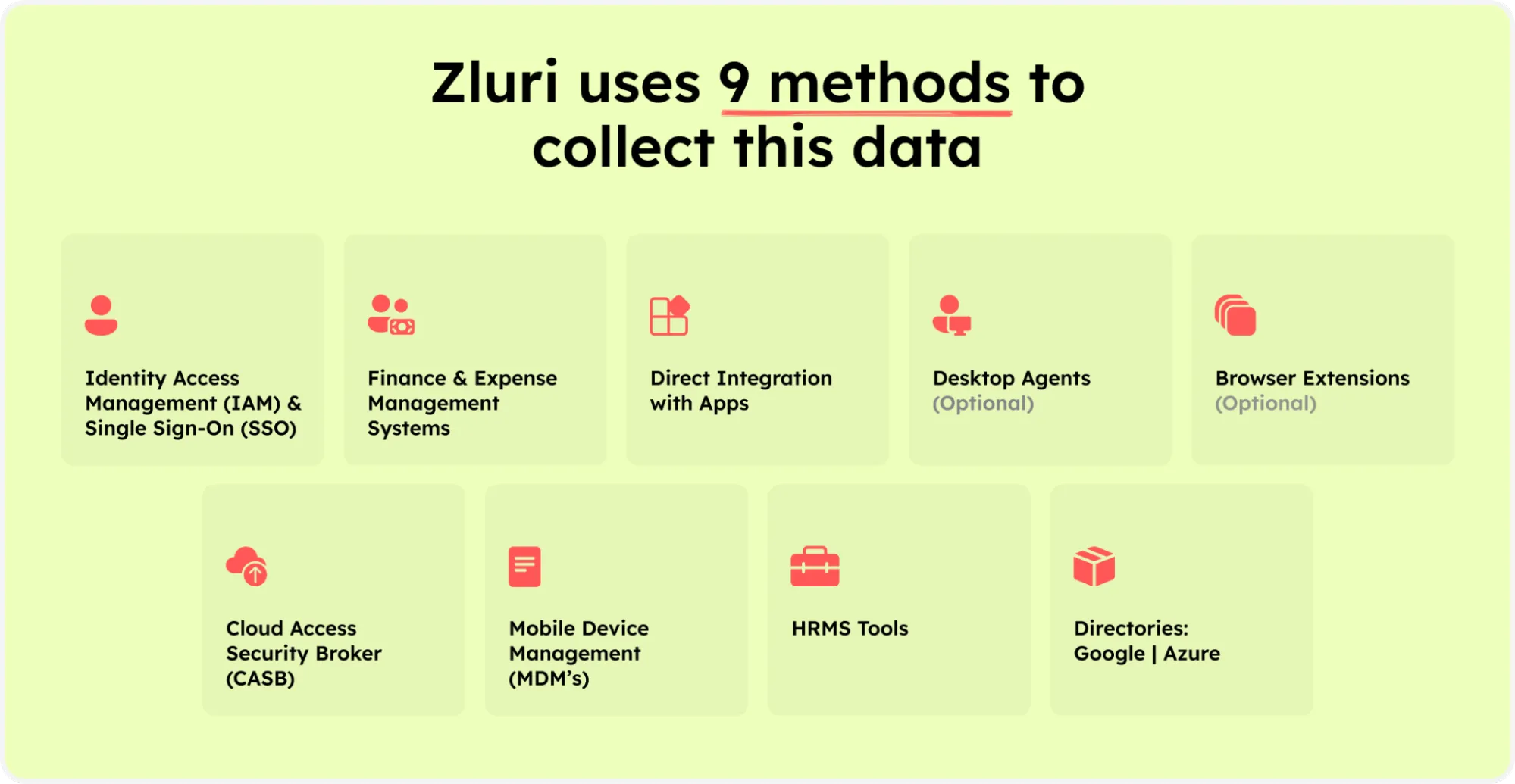
Zluri’s nine discovery methods
But Zluri doesn't stop at discovery. Zluri's commitment to real-time data integration sets it apart. By seamlessly integrating with over 300+ SaaS applications, Zluri offers a continuous flow of data, valuable insights, and AI-powered alerts. This ensures that you are always in the know about your organization's access landscape.
Zluri's API-based integrations facilitate in-depth exploration of data across all your SaaS applications. This meticulous approach guarantees 100% visibility into your SaaS environment, assuring you that no vital information remains concealed.
What's more, Zluri boasts the most extensive library, comprising over 240,000 apps. This vast repository enables Zluri to provide detailed access data, diving into the specifics of user permissions and access levels within your SaaS ecosystem. Zluri's granular insights empower you to understand and manage user access with unparalleled precision.
- Robust Automation Engine
Zluri's automation engine acts as the self-driving system for your organization. It effortlessly manages access workflows, ensuring seamless automation while adhering to a predefined set of rules and policies. By conducting thorough reviews, Zluri guarantees that your access governance procedures are not only efficient but also compliant with your organizational standards.
Now, let’s explore Zluri’s IGA capabilities
Lifecycle Management
Zluri's user lifecycle management solution streamlines user access management while maintaining strong security measures. Zluri's ULM platform makes it easy to bring new employees onboard by simplifying their access to necessary applications and resources.
By employing automated procedures and integrating seamlessly with HR systems, Zluri enables your IT teams to establish user accounts across multiple applications effortlessly, all from a centralized interface. This streamlined approach reduces errors, lightens the administrative burden, and guarantees that new employees enjoy the correct access privileges from their very first day.
Also, Zluri's ULM capabilities extend beyond onboarding to cover the departure of employees from your organization. Through automated deprovisioning workflows, Zluri assists your IT teams in promptly revoking user access across all applications. This proactive approach minimizes the risks associated with abandoned accounts, ensuring that your organization remains secure and compliant even as employees leave.
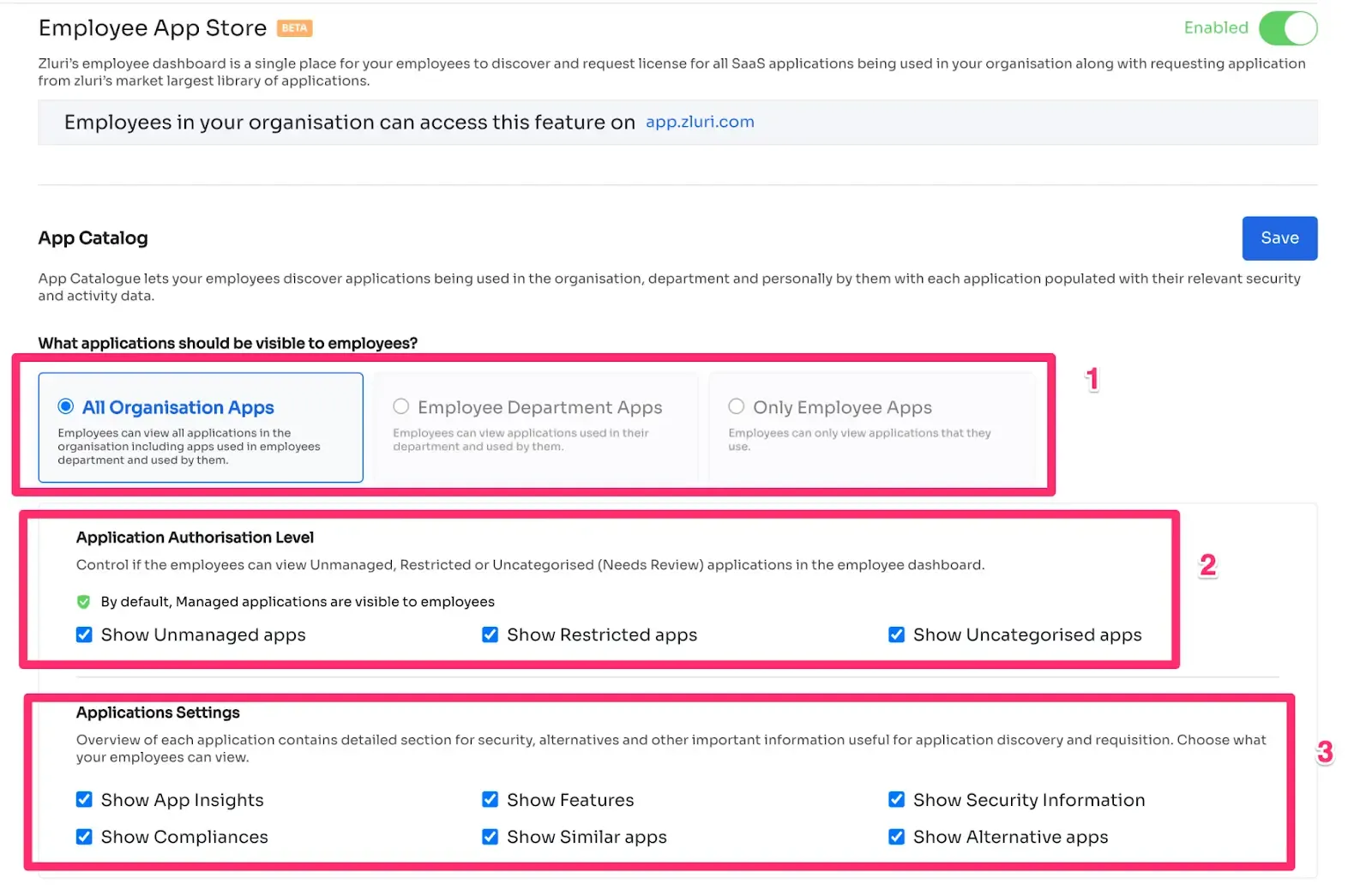
In addition, Zluri offers key unique features that differentiate it from others, ensuring effective access governance and access management:
Customizable Access Workflows: Zluri offers fully customizable access workflows designed specifically for your organization's needs. These predefined workflows eradicate the manual hassle of granting and revoking access permissions. The intuitive interface enables you to tailor workflows based on user roles, departments, and seniority levels, ensuring precise access governance.
- Seamless Onboarding and Offboarding
With Zluri's tailored workflows, onboarding and offboarding employees become seamless processes. The predefined "onboarding playbooks" and "offboarding playbooks" allow your team to efficiently provision access for new hires and deprovision access for departing employees.
Onboarding: With Zluri's tailored workflows, the onboarding process becomes a seamless journey. New employees are efficiently provisioned with the necessary access, aligning precisely with your security protocols and compliance standards. This streamlined approach ensures that each new member integrates swiftly and securely into your digital landscape.
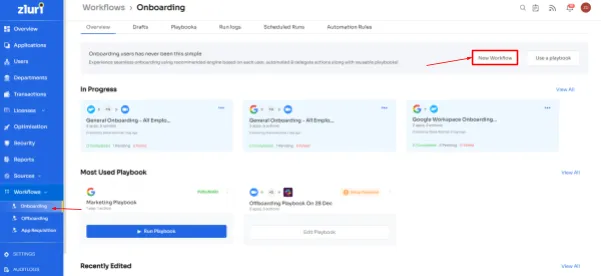
Onboarding
Offboarding: Access deprovisioning for departing employees is executed seamlessly, leaving no room for oversight or error. Zluri ensures that every user's access is meticulously managed even during transitions, upholding your security standards and compliance requirements. The result is an effortless offboarding process that safeguards your organization against potential risks associated with departing employees.
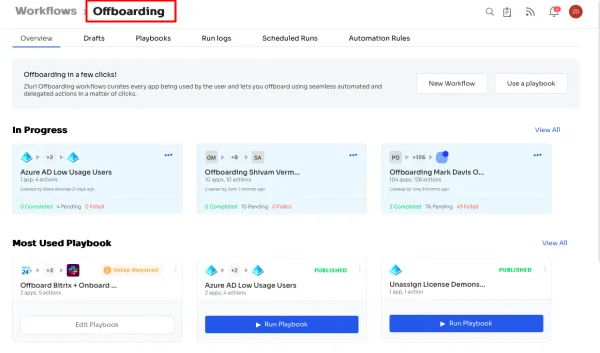
Offboarding
Powerful app recommendations & in-app suggestions: Zluri also provides contextual-based app recommendations based on user profiles, department, seniority level, etc., making it convenient for your team to choose the appropriate apps for provisioning.
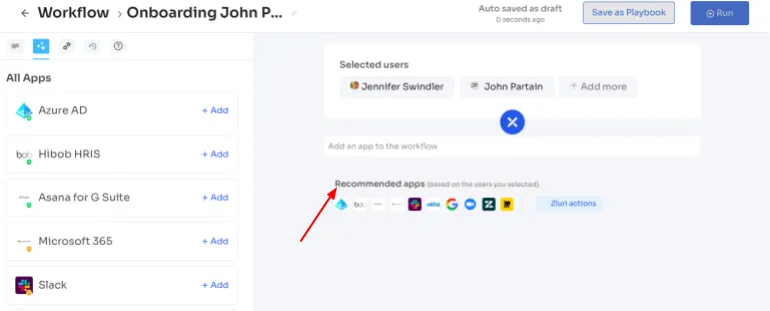

Moreover, it offers in-app suggestions to enhance user productivity by recommending required actions for efficient task performance.
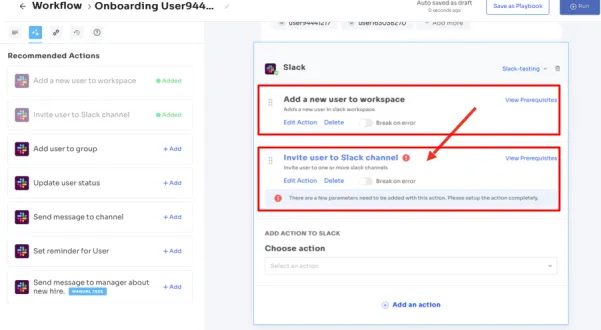
Automation Playbooks: By saving the workflows for both onboarding & offboarding as predefined “playbooks”, Zluri eliminates the need to recreate workflows for each user, further streamlining the process and increasing operational efficiency.
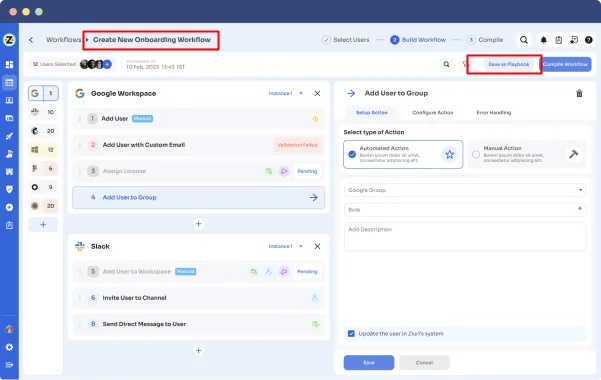
Onboarding playbooks helps to reuse it while onboarding an employee.
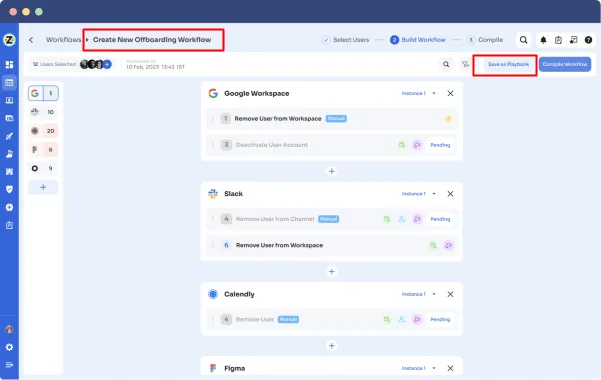
Use offboarding playbooks to revoke access for your former employees.
Note: These playbooks help your team to ensure security and compliance, while provisioning and deprovisioning users’ access even in the future.
But what happens when a user’s role changes during the mid-lifecycle transitions?
Ad-hoc access request management
Zluri simplifies the process of managing user access during role transitions with its self-serve model, the Employee App Store (EAS). This powerful feature empowers your IT team to maintain control over employees' access to essential tools and applications.

Zluri’s EAS DashboardUsing the EAS, your team or designated approver can review and approve access requests based on the employees' job roles and responsibilities. This ensures that permissions granted align with their specific needs, allowing you to govern access and protect sensitive information within your organization.
Zluri's transparent approval system consists of three levels: app owners, reporting managers, and IT admins. Higher-level authorities have the decision-making authority, enabling them to override decisions made by lower-level admins or managers.
In the event of an access request being rejected, decision-makers can provide comments explaining the reasons behind the rejection, ensuring transparency and clarity in the access request process. Approvers also have the ability to modify specific requests as needed.
To keep users well-informed, Zluri provides a "changelog" feature where users can track updates related to their access requests. This includes information such as the approval or rejection of requests, license duration or tier changes, and comments added by any admin. This helps users stay updated and aware of any changes or decisions made regarding their access to applications.
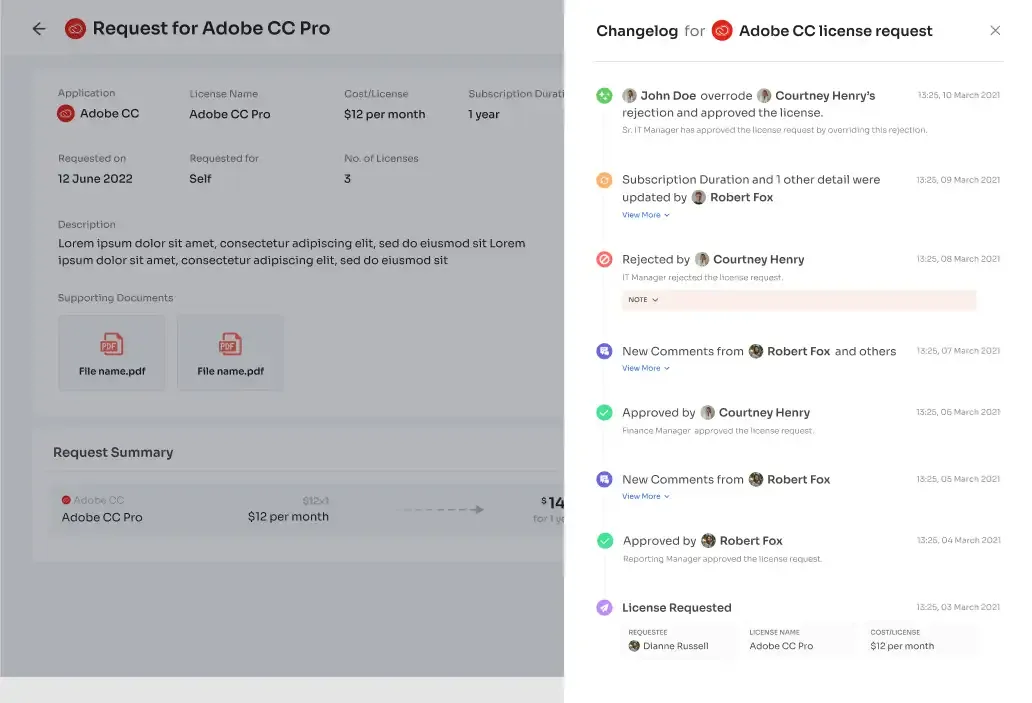
Changelog
Access certification :
Zluri's IGA solution simplifies user access review and permission management. It provides a centralized platform for security, GRC, and auditors to review and report on user access. With Zluri, you can easily set review parameters, choose reviewers, and schedule campaigns.
Zluri’s Access Review HomepageThrough intelligent automation, Zluri assesses user access rights based on predefined rules, saving time and reducing errors compared to manual spreadsheet reviews.
Zluri goes beyond reviews by offering auto-remediation capabilities. If access violations are detected, it takes immediate corrective actions, enhancing your organization's security and ensuring compliance. By revoking access for terminated employees or those with outdated privileges, Zluri helps mitigate the risk of unauthorized data breaches and keeps sensitive information secure.
Zluri generates comprehensive reports that provide valuable insights into access patterns, vulnerabilities, and compliance status. These reports make it easy to demonstrate compliance to auditors and make informed decisions about access management.
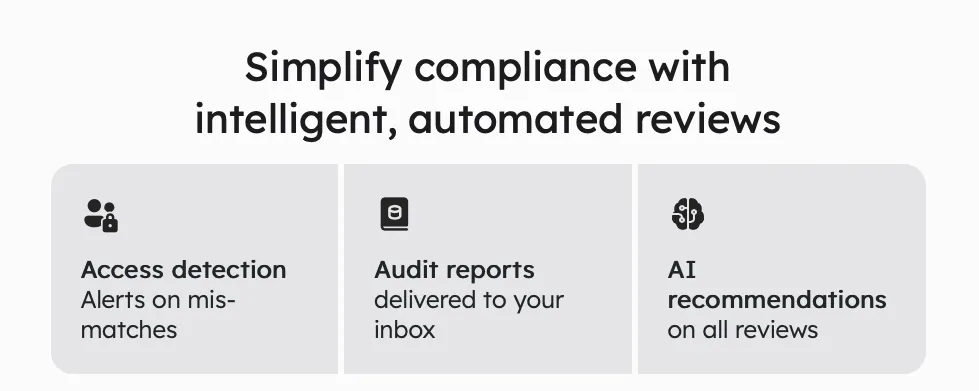
Zluri's unique approach to access reviews sets it apart from other IGA tools. Let’s see how.
Continuous Access Reviews: It enables you to maintain control over access privileges through recurring and scheduled certifications. Recurring certifications ensure consistent review and validation of access permissions, quickly identifying and addressing security weaknesses.
Moreover, scheduled certifications allow planned and timely evaluations, reducing the chances of missing critical access issues.
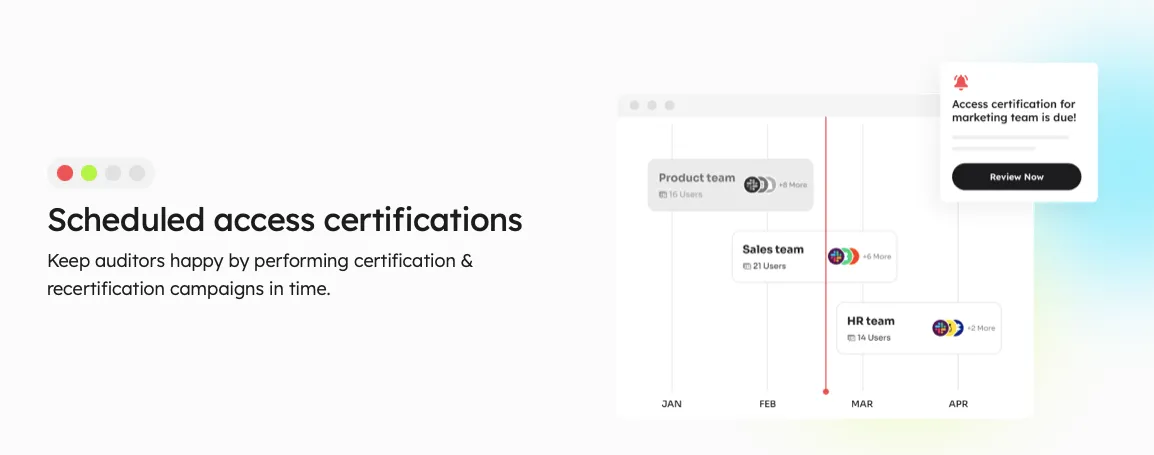
Scheduled Access CertificationZluri provides industry-standard certificate templates to simplify the certification process. These templates offer a standardized approach, making certifications efficient, comprehensive, accurate, and aligned with recognized guidelines.
Real-time Access Reviews: Zluri's IGA solution doesn't just offer data; it offers actionable intelligence. Detailed, comprehensive reports provide valuable insights into access patterns, vulnerabilities, and compliance status. These insights empower you to make informed decisions about access management and effortlessly demonstrate compliance to auditors.
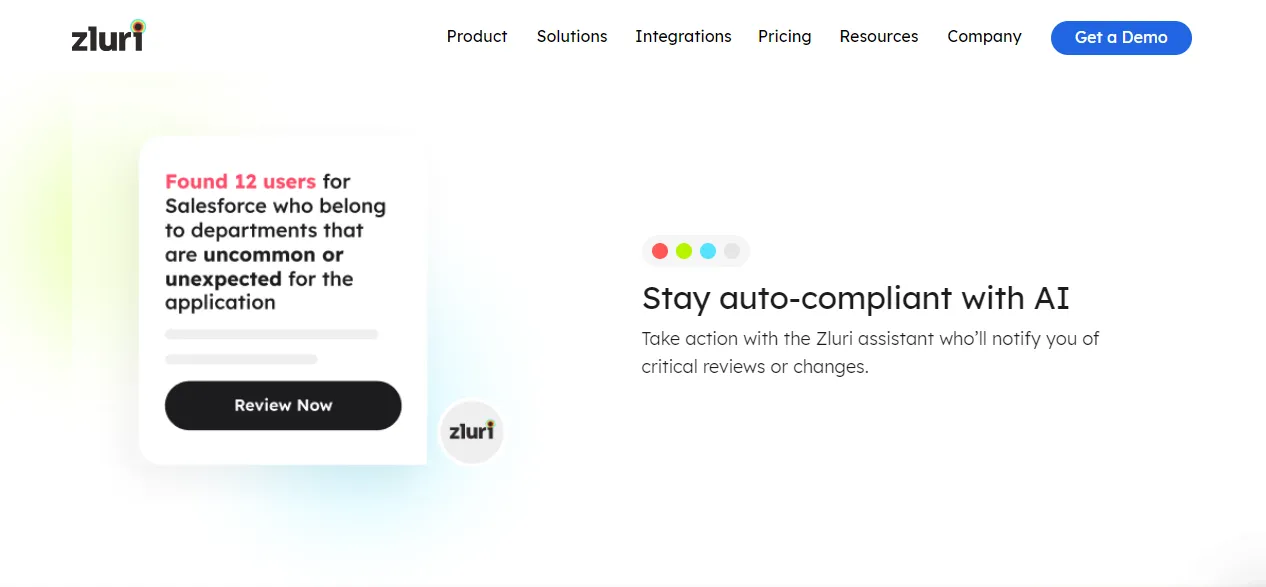
Auto CompliantZluri's AI compliance capabilities align access controls with industry regulations and standards, minimizing the risk of compliance violations and simplifying the entire compliance process.
Key Benefits
- Zluri leverages the five discovery methods to identify the complete SaaS landscape in your organization, making it convenient for your team to have complete visibility of your SaaS stack and manage users’ access to these apps efficiently.
- Zluri integrates with over 800 applications, empowering your team to get granular insights like users’ access and their details for each application.
- Zluri helps you stay audit-ready by providing your IT teams with compliance-related information, like identifying apps and their users that require special attention. This valuable information enables your team to take the necessary measures against unauthorized access, guaranteeing that only authorized personnel can access sensitive information and resources.
2. Okta Identity Governance
Okta Identity Governance provides a streamlined access request and approval process, enabling your organization to manage access requests and control user permissions efficiently.
The solution also facilitates automated approval workflows, ensuring access requests are routed to the appropriate stakeholders for review and authorization, saving valuable time and reducing administrative burden.
Key Features
- Access Certification and Review: The tool offers comprehensive access certification and review capabilities, allowing you to define certification campaigns and periodically assess user entitlements. Automated processes and customizable workflows enable you to streamline certification campaigns, identify and mitigate access risks, and ensure compliance with regulatory frameworks.
- Role-Based Access Control (RBAC): It provides a powerful RBAC framework that allows you to define roles, associate them with specific access privileges, and assign those roles to users or groups. With this feature, your team can easily manage access at scale, reducing the risk of unauthorized access and providing employees with appropriate levels of system and data permissions based on their job roles and responsibilities.
- Policy Enforcement and Violation Management: The tool also offers policy enforcement and violation management capabilities, enabling you to define access policies and automatically enforce them across your organization. The solution continuously monitors user access, detects policy violations, and triggers alerts or remediation actions as necessary.
- Audit and Reporting: It simplifies the audit process by providing extensive audit trails and reporting capabilities. With this feature, you can easily track user access changes, access request history, and approval workflows.
Moreover, the solution also offers customizable reports, allowing you to generate detailed insights into user access patterns, compliance status, and potential areas of improvement.
3. Avatier Identity Management
Avatier Identity Management offers a centralized platform for managing user identities and governing their access across your organization's systems and applications. It simplifies creating, modifying, and deleting user accounts, ensuring consistent access control throughout your IT ecosystem.
Key Features
- User Provisioning and Deprovisioning: The tool facilitates automated user provisioning and de-provisioning, ensuring that employees receive the appropriate access privileges based on their roles and responsibilities.
- Role-Based Access Control (RBAC): Its RBAC capabilities allow you to define user roles and associated permissions, aligning with your organization's hierarchy and business processes. With Avatier, you can easily assign roles to users, granting them the necessary access to perform their job functions effectively.
- Access Certification Capabilities: The tool offers access certification and attestation capabilities, enabling you to periodically review and validate user access rights across your systems. This feature allows you to identify and rectify any discrepancies or violations promptly.
- Segregation of Duties (SoD) Enforcement: The tool also provides SoD enforcement, which ensures that conflicting permissions cannot be assigned to a single user. This helps maintain a robust internal control environment, reducing the risk of fraudulent activities and data breaches.
4. StrongDM
StrongDM offers an access governance system that streamlines access governance processes and ensures secure and controlled access to your organization's critical resources.
It also offers a centralized access control system, enabling your team to establish consistent access policies across all resources. With this, you can define fine-grained access permissions and easily enforce them across databases, servers, and cloud infrastructure.
Key Features
- Comprehensive Visibility and Auditability: The tool provides comprehensive visibility into access activities by maintaining detailed logs and audit trails. These logs can also serve as valuable evidence during compliance audits, enhancing your organization's security posture.
- Two-Factor Authentication (2FA): By enforcing 2FA, you can add an extra layer of protection to user accounts and reduce the risk of unauthorized access. StrongDM integrates seamlessly with popular authentication providers, such as Google Authenticator and Duo, making it easy to implement and manage 2FA for your organization.
- Role-Based Access Control (RBAC): StrongDM offers robust RBAC capabilities that help you define and assign user roles based on their responsibilities and permissions. This feature minimizes the potential for human error and helps prevent over-privileged accounts.
- Real-Time Access Monitoring: With StrongDM, you can monitor access activities in real-time, providing an extra layer of security and oversight. Real-time access monitoring enables immediate identification and response to any suspicious activities, such as unusual logins or unauthorized data access attempts.
- Secure Remote Access: StrongDM also offers a secure remote access solution that allows you to grant access to resources without compromising security. StrongDM ensures secure connectivity to critical systems while maintaining granular control over user access, whether your employees work from the office or remotely.
5. JumpCloud Directory Platform
JumpCloud Directory empowers you and your IT team to enhance access governance, streamline IT security, and improve operational efficiency. It offers a robust single sign-on (SSO) capability, enabling users to access multiple applications with a single set of credentials.
Moreover, it integrates seamlessly with various multi-factor authentication (MFA) methods. Your team can significantly reduce the risk of unauthorized access by requiring users to provide additional authentication factors such as SMS codes, push notifications, or hardware tokens.
MFA also enhances access governance by adding an extra layer of security, ensuring that only authorized users can access critical systems and applications.
Key Features
- User Lifecycle Management: JumpCloud Directory offers a comprehensive set of features that enable effective user lifecycle management, a core component of access governance. The platform allows your team to automate user provisioning, deprovisioning, and modification processes across all systems, applications, and directories.
- Role-Based Access Control (RBAC): With JumpCloud Directory, your team can implement role-based access control (RBAC) policies effortlessly. This reduces the complexity of managing access rights, ensuring that employees have the appropriate level of access to perform their tasks and limiting exposure to sensitive information.
- Auditing and Compliance: With this tool, you can track and monitor user login attempts, changes to access permissions, and overall system usage. This comprehensive audit trail aids in identifying potential security breaches, ensuring regulatory compliance, and facilitating timely responses to security incidents.
6. Netwrix
Netwrix offers a access governance system that empowers your IT teams to streamline access control processes and strengthen data protection. It assists your team in managing user permissions, minimizing risks, and maintaining data integrity effectively.
Further, integration with identity and access management software enables your team to easily grant or revoke access permissions based on predefined rules and policies. This ensures employees have appropriate access to the needed data, reducing the risk of data breaches or unauthorized access.
Key Features
- Comprehensive User Activity Monitoring: It enables your team to track and analyze user behavior across various systems, applications, and data repositories. This comprehensive visibility allows for a proactive approach to security, identifying and mitigating potential risks in real-time.
- Role-Based Access Control (RBAC): The tool incorporates role-based access control (RBAC) functionality, allowing you to define access permissions based on job roles and responsibilities. This ensures that users are granted the right level of privileges required for their specific tasks.
- Data Classification and Risk Assessment: It offers data classification and risk assessment features, enabling your team to categorize data based on its level of sensitivity. By assigning appropriate labels or tags to data assets, you can implement granular access controls and prioritize security measures based on the risk level associated with each data type.
- Compliance and Audit Reporting: With this tool, you can generate detailed reports on user access activities, permissions, and changes, facilitating compliance with regulatory standards such as GDPR, HIPAA, or PCI DSS.
Further, these reports help demonstrate data governance efforts to auditors, ensuring transparency and accountability while providing valuable insights for ongoing security improvements.
7. One Identity Manager
One Identity Manager offers an advanced access governance system designed to simplify and streamline the management of user access rights and permissions. With its centralized dashboard, your team can easily manage the entire user lifecycle, ensuring employees have the right access privileges throughout their tenure.
Key Features
- Role-based Access Control (RBAC): The solution enables you to define roles and assign corresponding access rights to users based on their job responsibilities. With RBAC in place, you can ensure that users only have access to the resources necessary to perform their duties, reducing the potential for security breaches.
- Automated Access Certification: One Identity Manager automates the access certification process, enabling you to easily define access certification campaigns and generate reports for auditors. It streamlines the review process with a consolidated view of access rights, allowing your team to quickly identify and address any compliance issues.
- Segregation of Duties (SoD) Controls: It offers comprehensive SoD capabilities, allowing you to define and enforce logical access boundaries. By identifying and preventing potential conflicts, you can maintain a strong internal control environment and meet regulatory requirements efficiently.
- Audit and Compliance Reporting: The tool generates detailed reports that showcase user access activities, changes, and other relevant information. These reports are invaluable for internal audits, regulatory assessments, and demonstrating compliance with industry standards.
8. SecurEnds
SecurEnds provides your team with a centralized platform to discover and identify identities and manage and monitor access across the organization. With a unified view of user access rights, permissions, and entitlements, your team can efficiently handle user provisioning, access requests, and permissions modifications.
Key Features
- Access Certification and Reviews: SecurEnds offers a robust framework for conducting access reviews, ensuring that user entitlements align with your organizational requirements and policies. You can easily define access review campaigns, automate the process, and involve relevant stakeholders to validate and verify access rights.
- Segregation of Duties (SoD) Analysis: SecurEnds incorporates segregation of duties (SoD) analysis capabilities, allowing your team to identify and mitigate any potential conflicts within user access rights. It automatically analyzes access combinations and provides alerts and recommendations to address any conflicting access permissions, helping you maintain compliance and prevent fraud.
- Audit and Compliance Reporting: The tool generates comprehensive reports that capture user access information, access reviews, certifications, and any access-related policy violations. These reports facilitate evidence-based compliance assessments, simplifying auditing and ensuring adherence to industry regulations and best practices.
9. Solarwinds Access Rights Manager
SolarWinds Access Rights Manager (ARM) offers a comprehensive access governance system that empowers your team to efficiently manage user access, enforce security policies, and maintain compliance.
SolarWinds ARM provides robust user access management capabilities, allowing you to oversee and control user privileges across various systems and applications. With ARM, you can easily grant or revoke access rights, manage user roles, and streamline the onboarding and offboarding processes.
Key Features
- Role-Based Access Control (RBAC): SolarWinds ARM offers a centralized RBAC framework that enables your team to assign access permissions based on users' roles and responsibilities. By defining granular access levels, ARM helps minimize the risk of unauthorized access and prevents the potential misuse of sensitive data.
- Compliance and Audit: With ARM, your team can generate detailed access logs, track user activities, and conduct regular access reviews. These audit trails help identify security gaps and provide evidence of compliance during internal and external audits.
- Self-Service Access Requests: SolarWinds ARM offers a self-service portal that enables users to request access to applications, data, or resources as per their requirements. These requests go through an automated approval workflow, ensuring that access is granted or denied based on predefined policies.
- Access Recertification: The tool simplifies this process by automating access recertification campaigns. You can define recertification schedules, send notifications to appropriate stakeholders, and review and validate user access rights.
10. Evidian IGA
The Evidian IGA solution allows you to streamline and enhance your access governance processes. Evidian IGA offers comprehensive features designed to simplify access governance and bolster your organization's security framework.
With Evidian IGA, your team can automate the complete user lifecycle management from provisioning to deprovisioning of user accounts and access rights. This reduces the risk of unauthorized access and potential security breaches.
Key Features
- Efficient Access Request and Approval Workflows: The tool automates the access request process, eliminating manual and time-consuming tasks. Through predefined workflows and role-based access control, Evidian IGA enables you to define and enforce access policies based on job roles, ensuring that users have the appropriate level of access required to perform their tasks.
- Role-Based Access Control: Evidian IGA offers robust role-based access control capabilities, allowing you to define access rights based on job functions and responsibilities. You can establish a granular and scalable access governance framework by mapping job roles to specific permissions.
This approach simplifies access management and ensures that users are granted the appropriate access privileges based on their job requirements, reducing the risk of over- or under-provisioning. - Compliance and Audit Reporting: The tool also offers comprehensive compliance and audit reporting capabilities, providing you with the necessary insights to meet regulatory requirements and demonstrate adherence to industry standards. The tool generates detailed reports on user access, permissions, and changes made to access rights, allowing you to track and monitor access governance activities.
11. Zilla Security

Zilla Security's access governance solution provides a centralized platform for managing user access rights and permissions. By seamlessly integrating with your HR systems, the tool ensures accurate and timely updates to reflect employee details like role changes, ensuring access privileges align with organizational needs.
Further, the tool enables your team to efficiently grant or revoke access privileges across various systems, applications, and data repositories. It provides automated user provisioning, deprovisioning, and role-based access assignment, saving time and reducing your IT admin burdens.
Key Features
- Role-Based Access Control (RBAC): Zilla Security's access governance solution excels in RBAC implementation, allowing you to define roles, associate them with specific access rights, and assign users to these roles.
This granular approach facilitates the principle of least privilege, where users only have access to the resources necessary for their roles, thereby minimizing the risk of unauthorized access and potential security breaches. - Access Request and Approval Workflows: Zilla Security offers intuitive access request and approval workflows to streamline access management processes and maintain a secure environment. Moreover, you can define customizable workflows, enabling employees to request access to resources, applications, or data.
These requests are then routed to the appropriate approvers, ensuring proper authorization and accountability. The tool also allows for automated approvals for routine access requests, further increasing operational efficiency. - Compliance Monitoring and Reporting: Zilla Security's access governance software simplifies compliance monitoring by providing real-time visibility into access activities and generating comprehensive reports. Your team can track access events, identify potential anomalies or policy violations, and generate audit-ready reports.







.png)

.svg)














