Creating a user provisioning policy is crucial for maintaining security and operational efficiency in organizations. This article explores the key components needed to develop an effective user provisioning policy.
IT teams might face the challenge of efficiently managing user access and permissions across various systems and applications. As organizations grow and evolve, the task of user provisioning becomes increasingly complex. You might often come across issues such as security vulnerabilities, compliance risks, and operational inefficiencies.
Implementing a robust user provisioning policy is paramount for addressing these challenges head-on. A well-defined user provisioning policy serves as a blueprint for the systematic creation, modification, and removal of user accounts throughout their lifecycle.
To create an efficient user provisioning policy, you need to understand the key components involved in a user provisioning policy. But before exploring the key components, let’s know the benefits first.
Benefits of User Provisioning Policy
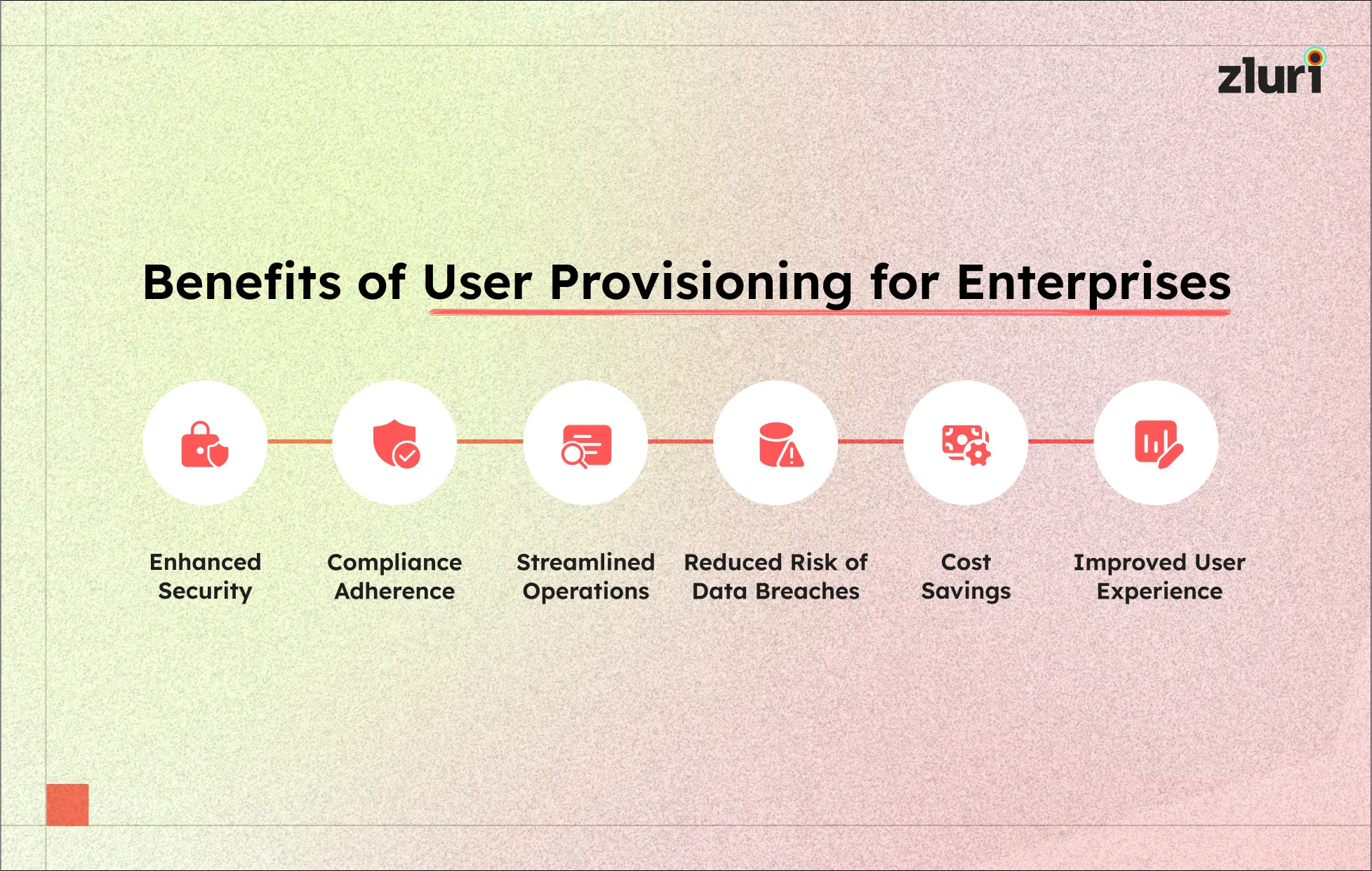
User provisioning policies offer numerous benefits, ranging from strengthened security to operational efficiency and regulatory compliance, making them essential components of any robust cybersecurity framework.
- Enhanced Security: By strictly controlling access rights, user provisioning policies significantly reduce the risk of unauthorized access to sensitive data and resources, thus bolstering overall security measures.
- Compliance Adherence: Implementing robust user provisioning policies helps organizations meet regulatory requirements and industry standards by ensuring that access to sensitive information is properly managed and audited.
- Streamlined Operations: Automating user provisioning processes eliminates manual tasks, reduces errors, and enhances operational efficiency by swiftly granting or revoking access based on predefined rules and roles.
- Reduced Risk of Data Breaches: Promptly removing access for departing employees and adjusting permissions as per changing roles minimizes the likelihood of insider threats and potential data breaches.
- Cost Savings: By automating access management and minimizing the risk of security incidents, organizations can avoid costly repercussions associated with data breaches and regulatory fines, leading to substantial cost savings in the long run.
- Improved User Experience: User provisioning policies ensure that employees have timely access to the resources they need to perform their duties, enhancing productivity and satisfaction among users.
In this post, we will discuss the components required to create a strong user provisioning policy.
Key Components Involved in a User Provisioning Policy
Now, let’s explore the essential components of an effective user provisioning policy.
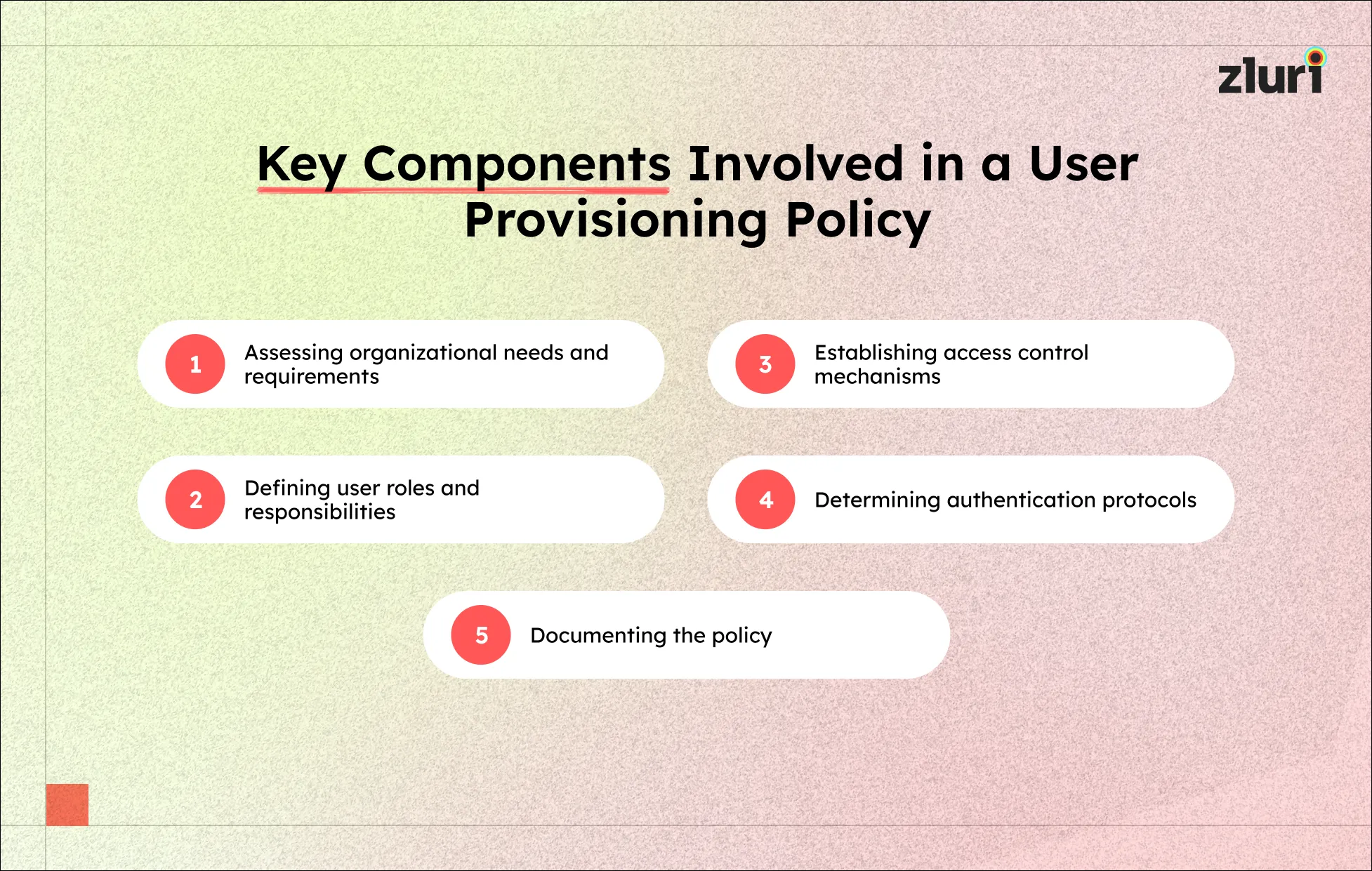
1. Assessing organizational needs and requirements
Assessing organizational needs and requirements is crucial when crafting a user provisioning policy. This step involves understanding what your organization does, how it operates, and what tools and systems are essential for its smooth functioning. By doing so, you can tailor the user provisioning policy to align perfectly with your company's goals and objectives.
For instance, let's consider a mid-sized company expanding its operations globally. In such a scenario, the user provisioning policy must account for factors like varying regulatory requirements across regions, diverse employee roles and permissions, and the need for seamless access to resources regardless of geographical location.
Without assessing the above mentioned specific needs, the provisioning policy may fall short, leading to compliance issues, security vulnerabilities, and operational inefficiencies.
Further, incorporating an assessment of organizational needs into the user provisioning policy brings several benefits.
- It ensures that the policy aligns closely with the company's objectives and operational workflows, enhancing overall productivity and employee satisfaction.
- It helps mitigate security risks by tailoring access controls based on job roles, departments, and compliance requirements, thus reducing the likelihood of unauthorized access or data breaches.
- It facilitates scalability and adaptability, allowing the policy to evolve alongside the organization's growth and changes in technology landscape.
2. Defining user roles and responsibilities
Defining user roles and responsibilities is essential in creating a robust user provisioning policy within any organization. By clearly outlining who has access to what systems, applications, and data, you establish a framework for efficient and secure user management. Each user role should align with specific job functions and responsibilities within the organization. This ensures that access privileges are granted based on the principle of least privilege.
Incorporating user roles and responsibilities into the user provisioning policy, you can streamline the onboarding and offboarding process. When a new employee joins the company, you can quickly assign them the appropriate roles and permissions based on their job requirements. This targeted approach minimizes the risk of granting excessive access, reducing the potential for security breaches or data misuse.
Furthermore, clearly defined user roles and responsibilities enhance accountability across the organization. Users understand their access rights and are accountable for adhering to security protocols and data handling procedures relevant to their role. This clarity fosters a culture of responsibility and helps mitigate insider threats by ensuring that access privileges are granted and revoked promptly as job roles change.
Moreover, incorporating user roles and responsibilities into the user provisioning policy simplifies audits and compliance efforts. By maintaining a documented record of who has access to sensitive information and systems, you can easily demonstrate compliance with regulatory requirements and industry standards. This enhances your organization's overall security posture and reduces the administrative burden on your team.
3. Establishing access control mechanisms
Access control mechanisms are vital components of a robust user provisioning policy within any organization. By establishing access control mechanisms, you're essentially setting up rules and regulations that determine who can access what within your company's systems and resources. This helps ensure that only authorized individuals can access sensitive information or perform certain actions, thereby reducing the risk of unauthorized access or data breaches.
Moreover, by clearly defining access levels and permissions for different users or user groups, you can streamline the onboarding process for new employees. Instead of manually granting access to each individual system or resource, you can simply assign them to the appropriate user group with predefined access rights. This saves time and minimizes the chances of human error in granting or revoking access.
Furthermore, access control mechanisms allow you to easily manage user privileges throughout their employment lifecycle. You can quickly adjust access levels as employees change roles within the organization or when they leave the company. This helps ensure that former employees no longer have access to sensitive information, reducing the risk of insider threats.
Additionally, access control mechanisms enable you to enforce security policies more effectively by restricting access to certain resources based on factors such as user location or device type.
4. Determining authentication protocols
In crafting an effective user provisioning policy for your organization, determining authentication protocols stands as a pivotal component. These protocols ensure only authorized users gain access to critical systems and data. By defining clear authentication standards, you establish a solid foundation for safeguarding your organization's assets and upholding data integrity.
Incorporating robust authentication protocols into your user provisioning policy empowers you to streamline access control processes. By implementing multi-factor authentication, for instance, you add an extra layer of security, mitigating the risk of unauthorized access due to compromised passwords. Moreover, by selecting authentication methods tailored to your organization's needs, such as biometric verification or smart card authentication, you enhance both security and user experience.
Furthermore, aligning authentication protocols with your organization's compliance requirements ensures adherence to industry standards and regulations. Whether it's HIPAA, GDPR, or PCI DSS, integrating compliant authentication measures bolsters your organization's data protection efforts and minimizes the risk of regulatory fines or penalties.
Additionally, regularly auditing and updating authentication protocols enables you to stay ahead of emerging threats and evolving compliance mandates. This maintains a proactive stance in safeguarding sensitive information.
5. Documenting the policy
Documenting the policy is crucial as you create a clear and comprehensive guide that outlines the steps, rules, and responsibilities involved in the user provisioning process. For instance, imagine your organiztion implementing a new user provisioning policy. By documenting each step, from requesting access to granting permissions, to revoking access when needed, everyone involved understands their role and what's expected of them.
Having a documented user provisioning policy ensures consistency and accuracy in the provisioning process. With clear guidelines in place, there's less room for error or ambiguity. Further, documentation provides a reference point for troubleshooting and auditing. If issues arise or audits are conducted, having a documented policy streamlines the resolution process and demonstrates compliance with regulatory requirements.
Moreover, documenting the policy enhances transparency and accountability. When all stakeholders can access and understand the policy, it fosters trust and confidence in the provisioning process.
Additionally, it facilitates communication and collaboration among IT teams, HR departments, and other relevant stakeholders. For example, if an employee changes roles or leaves the company, documented procedures ensure a smooth transition of access rights, minimizing disruptions to business operations.
Furthermore, documentation allows for continual improvement of the user provisioning process. By regularly reviewing and updating the policy based on feedback and changes in technology or organizational requirements, you can adapt and optimize the provisioning workflow to meet evolving needs efficiently.
Implement a User Provisioning Policy Efficiently with Zluri
Implementing a user provisioning policy is crucial for any organization. This can enhance security, streamline operations, and ensure compliance with regulatory requirements.
To achieve this efficiency, automation is key. Automating the user provisioning process helps minimize manual errors, reduces administrative overhead, and accelerates onboarding and offboarding of employees. Further, you can enforce consistent access controls across all applications and systems, ensuring that users have the appropriate level of access based on their roles and responsibilities.
One such solution that simplifies user provisioning and helps you implement its policy is Zluri. Zluri offers a comprehensive access management solution designed to streamline the user provisioning process. Let’s see how.
Zero-touch Onboarding: Zluri provides zero-touch onboarding that streamlines your user provisioning by automating tedious tasks with precision. With Zluri, effortlessly configure predefined workflows that orchestrate user account creation and access rights assignment based on roles and permissions.
Access Beyond SCIM Apps: Escape the limitations of traditional access management systems that struggle with non-SCIM applications. Zluri overcomes these challenges by integrating with a vast array of applications, even those not supporting SCIM protocols. This centralized user provisioning management across diverse platforms ensures seamless access control throughout your software ecosystem.
Secure User Deprovisioning: Zluri's robust user deprovisioning features helps to revoke access privileges when needed. Also, as per, Kuppingercole's research and analysis report, it automatically disables accounts, revokes permissions, and removes user credentials across all connected applications. This strengthens your defenses against unauthorized access and potential data breaches.
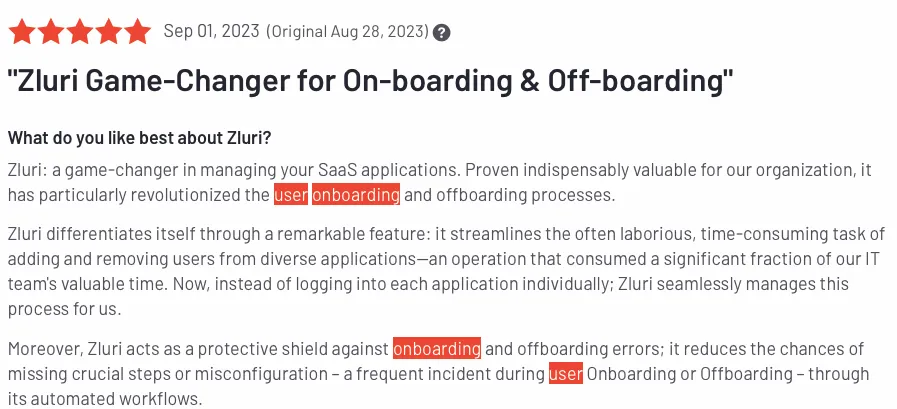
Further, with detailed audit trails and compliance reports, Zluri empowers you to showcase regulatory compliance and uphold accountability effortlessly.
By implementing an efficient user provisioning policy and leveraging automation tools like Zluri, you can improve security, enhance operational efficiency, and ensure compliance with regulatory standards.
FAQs
What is access provisioning?
Access provisioning is the process of setting up a computer system. It involves making user accounts, giving passwords, allowing email addresses, and giving permission to see different kinds of data.
What are dormant accounts?
A dormant account is one that hasn't been used for a while, except for earning interest. When an account stays dormant for a certain time (the duration differs by state), it becomes the state's unclaimed property.
What is identity and access management principle?
Identity and access management (IAM) helps companies give specific permissions to different users instead of giving everyone the same access. Nowadays, many IAM systems use RBAC, where each user's access depends on their role and responsibilities at work.
What is the role of IAM in user provisioning?
User provisioning, also known as user account provisioning, is an IAM process that provides necessary information about users/employees, like their name, job title, and department, to give them the right access and permissions they need.









.svg)














