Automation empowers IT managers with an efficient and resourceful approach to access management. By prioritizing security, compliance, and operational efficiency, IT managers can harness the full potential of automated least-privileged access to safeguard their valuable data, systems, and intellectual property from ever-evolving security threats in the cloud era.
Imagine your IT team receiving an urgent access request from a developer who needs access to a specific cloud service to troubleshoot a critical issue. Without automation, your team would have to review the request manually, verify the developer's need, and initiate the access provisioning process. This could take hours or even days, leaving the developer frustrated and hampering the organization's ability to respond swiftly to the issue.
Enter the game-changer: automating least privilege access, the revolutionary approach transforming how you can protect your organization’s assets and elevate efficiency. Why is it important? Let’s explore:
The Importance of Least Privilege Access Management
Let's delve into the importance of automating least privilege access management:
- Enhanced Security: In today's digital landscape, data breaches, malware attacks, and cyberattacks have become the norm. Automating least-privilege access is a potent shield against these threats. Companies can significantly reduce the attack surface by granting employees access only to the resources they genuinely need, thwarting potential intruders and unauthorized insiders.
- Increased Operational Efficiency: Manual processes can drag a company's productivity and overall operational performance. Imagine a scenario where employees no longer need to invest their valuable time completing access request forms and anticipating approval. You streamline this entire process by automating the provisioning and revocation of access. Access requests can be handled swiftly, empowering your team to focus on their core tasks without unnecessary delays.
- Improved Compliance: Non-compliance can result in hefty fines and reputational damage. Fortunately, automating least-privilege access simplifies compliance efforts. With proper automation in place, you can ensure that permissions are granted according to predefined rules and regulations, reducing the risk of compliance breaches.
- Mitigated Security Incidents: The repercussions of a security breach can be devastating for any organization. But with automated least privilege access, you have a robust defense against potential damage. Minimizing the number of privileged users and resources limits the potential impact of a security incident, keeping your operations running smoothly even during challenging times.
- Seamless Employee Experience: It can frustrate employees to navigate complex access request processes. Automation brings a sense of renewal, empowering your team to quickly obtain the access they need with minimal hassle. This improved user experience boosts overall satisfaction and enhances employee productivity.
- Empowering IT and Security Teams: Your IT and security teams play a critical role in keeping your organization’s data safe. Automating least privilege access lightens their workload by reducing the need for manual access management. As a result, they can focus on strategic initiatives and proactively address emerging security threats.
Automation empowers you and your IT team with an efficient and resourceful approach to access management. By prioritizing security, compliance, and operational efficiency, you can harness the full potential of automated least-privileged access to safeguard valuable data, systems, and intellectual property from ever-evolving security threats and suspicious activities in the cloud era.
Identity governance and administration (IGA) is the comprehensive answer to the rising need for LPA. By integrating RBAC, identity lifecycle management, access certifications, access analytics, and compliance functionalities, IGA empowers you to build a robust security foundation.
One such solution is Zluri. Zluri empowers you to embrace a proactive approach to security, safeguarding your organization’s valuable assets from potential breaches. As a comprehensive IGA solution, Zluri is a testament to how advanced technology can provide a secure, efficient, and future-ready access management strategy for organizations in the SaaS landscape.
Streamlining Least Privilege Access with Zluri's Powerful Automation Capabilities
Zluri's cutting-edge IGA platform revolutionizes access management by streamlining the implementation of the least privilege access policy. With Zluri's powerful automation capabilities, your IT teams can effortlessly manage user access, granting appropriate permissions and thwarting unauthorized access attempts.
The platform's intuitive interface ensures a seamless experience, reducing the burden on your team and freeing them up to focus on strategic initiatives. Moreover, Zluri ensures data security by enabling secure access management from any location. The platform adheres to the demands of the modern workforce, offering flexible and remote access options without compromising the confidentiality and integrity of sensitive data.
Discover & catalog your SaaS apps efficiently
With Zluri's powerful automation capabilities and innovative discovery methods, you can efficiently streamline least-privilege access and gain comprehensive insights into your organization's SaaS apps. By embracing Zluri's data engine, you can bolster your security, enhance compliance efforts, and unlock the true potential of intelligent discovery methods, paving the way for a secure and future-ready IT ecosystem.

Zluri's data engine plays a crucial role in streamlining least privilege access in the following ways:
- Comprehensive App Discovery: Zluri's data engine uses advanced discovery methods to identify all the SaaS applications being used within your organization. By having a clear and up-to-date inventory of apps, your IT team can assess the access rights of each application and its users, ensuring that privileges are granted appropriately.
- Detailed User Access Insights: The data engine provides a granular view of user access to various applications. Your team can quickly identify which users can access specific applications and scrutinize the permissions granted. This insight allows them to enforce least privilege access more effectively by revoking unnecessary permissions.
- Automation for Efficiency: Zluri's powerful automation capabilities remove the need for manual app categorization and user access recording. This automation accelerates productivity, freeing up time and resources for your IT team to focus on enforcing least privilege access policies.
- Strengthening Security Posture: By accurately identifying users with specific application access and granting permissions appropriately, Zluri's data engine strengthens your organization's security posture. It helps prevent potential security vulnerabilities that may arise from overprivileged users.
- Compliance and Risk Mitigation: Least privilege access is critical to compliance with various data protection regulations. Zluri's data engine assists you in ensuring that user access aligns with compliance requirements, mitigating the risk of unauthorized access and data breaches.By providing in-depth insights, automation, and strengthening security and compliance regulations, Zluri empowers you and your teams to efficiently manage user access to SaaS applications and minimize the risks associated with overprivileged users.
Effortless management of employee access with Zluri’s automation engine
Managing user access is not just about granting or revoking permissions; it's about maintaining a dynamic and efficient user lifecycle. Zluri's automation engine optimizes this lifecycle, from instant onboarding to offboarding and everything in between.
As users' roles evolve within the organization, Zluri dynamically adapts their permissions to match their current responsibilities, ensuring they always have the right level of access and reducing the risk of overprivileged accounts.
Revolutionizing User Access Provisioning: Streamlining Least Privilege with Zluri's Cutting-Edge Automation
Efficient user access provisioning is vital to any organization's security and productivity strategy. Ensuring employees have the appropriate level or minimum level of access to the resources they need without compromising sensitive information is crucial for maintaining a secure work environment. Here, we introduce Zluri, a game-changing platform that revolutionizes the onboarding process, making it seamless and efficient while relieving your IT team of repetitive and time-consuming tasks.

At the core of Zluri's capabilities is its ability to grant access only to authorized employees and provide them with the right access level to essential SaaS applications and data. By doing so, the platform effectively mitigates the risks associated with human errors and over-provisioning, which can lead to security blind spots and can be a threat actor.
Zluri's mission is to empower your IT team and put them in control of the onboarding process. The platform's intuitive interface enables your IT team to create and customize onboarding workflows tailored to each new employee's specific job entitlements, roles, positions, and departments. This high level of customization ensures that new hires get access to the tools and data necessary for their roles, enhancing security by preventing unnecessary access.
The efficiency of Zluri becomes evident as it enables your IT team to grant secure access to multiple new hires simultaneously. With streamlined workflows and automated processes, the onboarding experience becomes efficient and secure, saving time and effort for both the IT team and the new employees.

Zluri further simplifies the access provisioning process with its user-friendly interface, allowing IT teams to configure access privileges based on job roles and responsibilities with just a few clicks. Put simply, Zluri utilizes role-based access controls and least privileged access control, eliminating the necessity for intricate workflow designs and significantly decreasing the likelihood of errors during onboarding.
Zluri takes workflow efficiency to the next level by enabling you to save these processes as pre-defined \"playbooks.\" This innovative feature eliminates the repetitive task of recreating workflows for individual users, resulting in a streamlined process and a substantial boost in operational performance.

Revolutionizing User Access Deprovisioning: Streamlining Least Privilege with Zluri's Cutting-Edge Automation
Zluri allows you to implement the principle of least privilege, where users are granted only the minimal access required to perform their specific tasks. This approach significantly reduces the potential for damage and the risk of unauthorized access by limiting the exposure of sensitive resources to only those who need it.
Zluri automates the process of revoking user access when an employee leaves the organization, ensuring access rights are promptly removed across all devices, applications, and critical systems, leaving no room for oversight or human error. By eliminating manual intervention, Zluri reduces the chances of access privileges lingering after an employee's departure, bolstering data security.

Traditional offboarding processes can be time-consuming, requiring coordination between HR and IT teams to disable access across various platforms. Zluri's automation capabilities significantly speed up this process, enabling HR and IT teams to focus on more strategic tasks rather than tedious manual procedures. This streamlined approach increases efficiency and saves valuable time, making it easier to manage personnel changes.
By promptly deprovisioning user access, Zluri strengthens your organization's security posture. Access to critical resources is revoked immediately, reducing the risk of unauthorized data access or exfiltration by departing employees. Moreover, Zluri's automation ensures access management policies remain consistent and compliant with industry regulations, safeguarding your organization from potential compliance issues.
Empowering your organization with Zluri's EAS: Streamlining LPA for enhanced security & efficiency
Managing access permissions and ensuring the least privileged access for employees can be challenging. Zluri offers a game-changing solution called the Employee App Store (EAS), an intelligent self-service model that streamlines access request management, making the process efficient and secure.
By leveraging Zluri's EAS, you can empower your teams to request and approve access tailored to each employee's job role while maintaining complete control over access privileges and safeguarding sensitive data.

Intelligent Self-Service Model:
Zluri's EAS eliminates the need for manual permission management by offering an intelligent self-service model. Employees can request access to the applications and resources they need through the Employee App Store.
This granular approach ensures that employees have the necessary access level to perform their duties effectively while minimizing exposure to sensitive information, thus promoting the principle of least privilege access.

Multi-Tiered Approval System:
The EAS operates on a robust multi-tiered approval system, involving app owners, reporting managers, and IT admins. This hierarchy ensures that higher authorities can make decisive decisions, overriding choices made by lower-level admins or managers when necessary. This multi-tiered approach enhances security by adding an extra layer of scrutiny and prevents unauthorized access to critical resources.
Comprehensive Explanations and Comments:
Comprehensive explanations and comments accompany every approval or rejection of an access request. This fosters transparency and collaboration within your organization's access management process. Employees gain insight into why their requests were approved or rejected, helping them better understand your organization's access policies.
Tailored Access Permissions:
Zluri's intelligent solutions enable approvers to modify specific access requests, tailoring permissions precisely to the organization's unique requirements. This flexibility ensures that employees have the necessary access without unnecessary restrictions while maintaining security and adhering to the principle of least privilege.
Changelog for Transparency:
Zluri's EAS offers a comprehensive \"changelog\" feature, allowing users to track updates related to access requests. This feature captures valuable insights, from approvals and rejections to license duration or tier changes. Any comments or changes made by administrative accounts are recorded, fostering a collaborative and well-informed approach to access management.
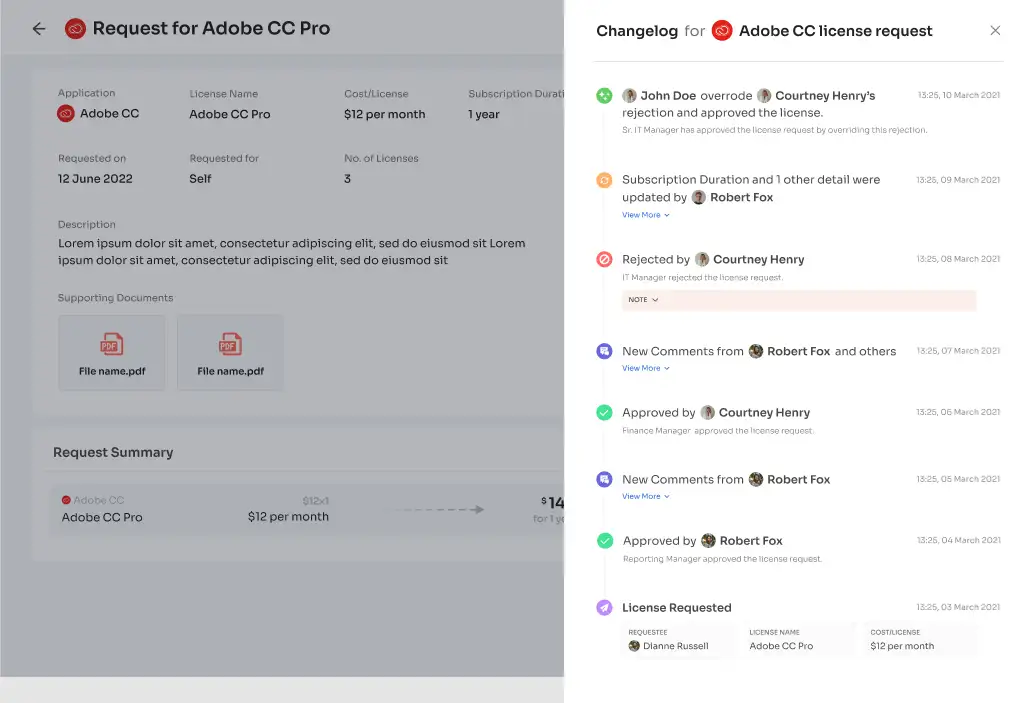
Revolutionizing access certifications & strengthening security with Zluri
Zluri's IGA solution makes the access review process highly precise and thorough. The automation algorithms intelligently analyze user access rights, roles, and entitlements, cross-referencing them with predefined access policies. This ensures that employees have precisely the level of access they need and nothing more.
Unnecessary excessive privileges are promptly identified and remediated, reducing the likelihood of potential security loopholes. Furthermore, Zluri's IGA solution allows for ongoing access monitoring and dynamic adjustments. As business requirements evolve and personnel change, access privileges can be automatically updated or revoked, ensuring access rights remain current and aligned with the principle of least privilege.

This proactive approach bolsters security and simplifies compliance efforts by providing a transparent and auditable access control process.
Achieving Efficiency and Security through Unified Access
Zluri's IGA provides a comprehensive and efficient approach to access management, streamlining least privilege access in organizations. By offering a unified view of digital identities, consolidating user access-related information, and maintaining a proactive alert system, Zluri's IGA strengthens security measures and ensures that users have the appropriate access privileges for their roles.
Embracing this innovative platform can help organizations optimize their access management processes and fortify their cybersecurity posture in today's ever-evolving digital landscape.
- Access directory: At the core of Zluri's IGA lies its access directory, a powerful feature that captures and organizes user information from various sources. This data consolidation ensures that every user's identity and associated access privileges are meticulously recorded and readily accessible for review.
By eliminating incomplete or inaccurate records, your admins can confidently make informed decisions about access rights within the organization. - Access privileges: With Zluri's unified access approach, admins gain unparalleled visibility and control over user access privileges across the entire organization. This comprehensive oversight enables quick identification of potential access discrepancies or suspicious permissions.
By maintaining a clear view of access rights, Zluri's IGA strengthens the organization's defense against cyber threats and insider threats, reducing the risk of unauthorized access and data breaches. Moreover, this constant alignment of access rights ensures that users have the appropriate access levels needed for their roles, promoting efficient and secure operations. - Access and Alerts: Zluri's IGA solution takes security a step further by continuously tracking user activity in real-time. A robust alert system instantly flags any unusual or potentially malicious behavior. This proactive stance empowers administrative accounts to respond promptly to potential security risks and take necessary action, preventing security incidents before they escalate.
By staying ahead of potential threats, you can maintain the integrity of their digital identities and safeguard sensitive information effectively.
Embracing Automation for Enhanced Security and Productivity
Zluri's IGA solution offers a game-changing approach to streamline least privilege access, enhancing efficiency and strengthening security through automation. By empowering organizations with precise access controls, proactive reviews, and automated remediation, Zluri helps companies maintain a compliant and secure access environment, ultimately safeguarding sensitive data and ensuring smooth operations.
- Access Rules and Policies: Zluri's IGA allows you to control access rules and policies precisely. By aligning access privileges with roles, responsibilities, and business requirements, organizations can ensure that users have the appropriate level of access without unnecessary privileges.
Automation takes center stage in this process, enabling the platform to conduct instant reviews of access requests against pre-defined criteria. This automated validation ensures access is granted only to authorized personnel, reducing the risk of unauthorized access and potential security breaches. - Scheduled Certification: To maintain a robust access control environment, Zluri's IGA introduces a proactive scheduling feature for automated access reviews at regular intervals. These scheduled certifications ensure access rights remain up-to-date and aligned with evolving security policies and best practices.
By conducting periodic reviews, you can reduce security gaps and minimize the likelihood of lingering access privileges that should have been revoked due to changes in user roles or responsibilities. - Auto Remediation: Zluri's IGA solution excels with its efficient automated remediation actions. The platform takes remediation actions without manual intervention when faced with security vulnerabilities or non-compliant access situations. These actions include revoking access, notifying users and their managers about access changes, or initiating access request workflows for necessary approvals.
Automating responses to security threats mitigates potential risks promptly, and security incidents are addressed in real-time.
The power of automation revolutionizes the access review process, leading to a substantial reduction in administrative burdens. Zluri's IGA solution simplifies and automates key tasks, such as generating access review reports, sending notifications to stakeholders, and tracking review progress. As a result, your teams experience up to a remarkable 70% decrease in manual efforts required for access reviews.
Maintaining regulatory compliance with industry regulations and internal policies is critical for organizations. Zluri's automated access reviews help demonstrate compliance with least privilege principles, making audits smoother and more efficient.
The platform generates comprehensive reports and audit trails, showcasing how access permissions have been reviewed and approved, bolstering the organization's ability to comply with regulatory requirements
Further, Zluri's 'access certification' module simplifies the process of conducting user access reviews. The intuitive interface enables stakeholders to easily understand their assigned tasks, review access permissions, and provide approvals or revocations with just a few clicks. This user-friendly approach promotes seamless collaboration between different teams, fostering a culture of security awareness and accountability.
Here’s how to automate user access reviews? Zluri’s ‘Access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the \"Access certification\" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.
- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the \"Application\" review method if desired and add the relevant application(s) to be audited for users' access.

- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.

- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.
Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.

- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the "Save Template" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the "Review Stage" section.
To boil it down, Zluri's IGA solution offers a game-changing approach to streamline least privilege access, empowering you and your teams to optimize their access management processes and fortify their cybersecurity posture in today's complex and dynamic cloud environment.
With Zluri's cutting-edge automation capabilities, your IT teams can efficiently manage access permissions, grant appropriate privileges, and safeguard sensitive data, all while enabling seamless productivity and user satisfaction. Book a demo now!







.png)

.svg)














