
Saviynt Vs. Okta: Which IGA Tool To Choose?
Saviynt enables your IT team to merge various identity, role, and group definitions across on-premise, hybrid, and cloud infrastructure. This helps to create a single, authoritative identity source. Meanwhile, Okta links all your SaaS apps, logins, and devices into a unified digital ecosystem. With Okta, your IT team gains seamless access to all the required resources, enabling efficient connectivity across the board.
However, both tools offer other distinct functionalities. So, you, as an IT Manager, can carefully evaluate each capability before deciding which IGA platform to choose.
To find the best among Saviynt and Okta, you must thoroughly examine each tool's capabilities and how well it aligns with your GRC team's requirements.
Let's take an example. To help you understand better, an organization requires a tool that puts more emphasis on compliance policies. So which IGA tool will be more apt for this situation, Saviynt or Okta?
In this scenario, Saviynt can be a better platform to choose as it emphasizes merging identity, role, and group definitions across various infrastructure types. It provides a comprehensive solution for managing and governing user identities, access rights, and compliance policies.
Okta is more suitable for organizations that require a centralized platform for ensuring that authorized people have access to the right SaaS apps and data with the least friction when needed.
This brief overview highlights how the features of these tools can greatly impact your decision-making process. However, it's important to recognize that relying solely on one specific capability is not enough while determining the ideal solution. Instead, it is essential to conduct a thorough evaluation and carefully consider the unique features offered by each tool.
So, let's move on and differentiate both tools based on different parameters to help you decide which IGA platform will best cater to your GRC team's needs.
Saviynt Vs. Okta: Detailed Comparison To Choose The Best
To assist you in determining which tool's functionalities are more effective in streamlining the identity governance and administration management process, we have thoroughly compared each parameter. This analysis will support your decision-making process in selecting the most suitable tool for your GRC team's requirements.
1. Identity Governance & Administration
- Saviynt Enables Zero Trust With Risk-Based Governance
Saviynt ensures your employees have seamless access to SaaS apps and data while maintaining compliance. It achieves this by streamlining Identity Governance and Administration processes and enhancing organizational agility through intuitive workflows and automation.
Furthermore, its powerful identity warehouse enables frictionless access, and by enabling Zero Trust in hybrid and multi-cloud environments, Saviynt establishes a robust security framework.
Moreover, Saviynt's advanced governance capabilities and its versatile cloud identity warehouse help your GRC team mitigate security risks, such as unauthorized access attempts.
It provides your team with 360-degree visibility across identity and access, enabling better decision-making with AI/ML-driven recommendations, remediation, and automated provisioning. Also, Saviynt can ingest any identity and analyze complex access and usage data, providing your team with valuable insights.
Additionally, Saviynt facilitates streamlined access request management through its browser plugin and integrations with Slack and Microsoft Teams. It also simplifies access management through the use of roles, rules, and policies.
By empowering employees with self-service features, Saviynt reduces the dependency on IT teams. It ensures visibility, control, and compliance through its control center, reducing review fatigue through intelligent certification campaigns identifying high-risk access.
Besides that, Saviynt also offers the flexibility to tailor IGA processes with bring-your-own connectors, widgets, and more.
- Better Security And Better Productivity With Okta Identity Governance
On the other hand, Okta's unified governance solution enables your GRC team to enhance security posture, mitigate modern security risks, and improve operational efficiency. By ensuring the right individuals have appropriate access to resources with minimal friction, Okta enables seamless and secure access management.
Furthermore, with Okta's Workflows platform, your GRC team can customize complex identity governance requirements, with or without not code. This flexibility allows for tailored governance processes that align with your unique needs. Additionally, Okta facilitates seamless collaboration between HR and IT teams, automating employee onboarding and offboarding processes for streamlined operations.
In terms of compliance, Okta automatically generates reports and provides a comprehensive view of each employee's access patterns. This visibility allows your GRC team to identify any potential red flags before they escalate into major issues.
Also, by leveraging Okta's self-service access request capabilities, frustration is minimized, and productivity is enhanced. Your IT admins can automate access configurations, reducing the time and effort required for manual access provisioning.
Apart from that, Okta's cloud-native solution and extensive library of over 7,000 pre-built integrations allow your IT team to automate complex identity processes at scale. This ensures efficient identity management across your organization's ecosystem.
2. Securing Every Identity
- Saviynt provides your GRC team complete visibility into all identities, reducing access sprawl and enhancing compliance with the help of its robust monitoring capabilities. Further, allowing them to assign access based on the principle of least privilege and also uniformly grant access controls to your employees.
The platform offers a built-in control repository that maps security controls across various regulations, industry standards, and compliance frameworks.
Your GRC team can effectively manage identity processes, including provisioning, through easily configurable policies and controls. Moreover, low-risk access can be automatically granted to your employees while high-risk requests are escalated for review.
Furthermore, it enables simple administration of resource access policies, secure management of privileged credentials, threat detection through user activity monitoring, and enriching risk profiles with identity analytics.
Apart from that, with Saviynt's platform, you can seamlessly integrate with hybrid ecosystems, extending governance to all identity types. Also, Saviynt's continuous monitoring of multi-cloud ecosystems identifies new identities, data, attributes, and information, triggering security alerts or automatically terminating risky processes. Its centralized identity hub scales alongside your cloud usage, enabling policy enforcement, activity documentation, and compliance maintenance. - Meanwhile, with Okta, your IT team can easily assign the right SaaS applications to the right employees and revoke access when needed. This process is automated and integrated with various systems such as HR systems, IT resources like Active Directory (AD) LDAP, and more.
One of the key benefits of Okta's IGA is its centralized view of employees' access and their accounts. This centralized view provides your GRC team with a complete understanding of which employee has access to which SaaS apps.
It further becomes easier to conduct audits and generate reports on which applications employees have access to, which employees were recently deprovisioned, the level of access permission granted, and other relevant access-related information. This visibility helps in maintaining compliance and identifying any access-related issues.
Moreover, Okta's IGA solution offers APIs that allow your team to programmatically extract data from your auditing tools. This eliminates the hassle of manual data extraction and enables seamless integration with your existing auditing processes. Your team can easily extract the necessary data for reporting or analysis purposes, further enhancing the efficiency of your GRC activities.
3. Seamless Authentication Procedure
- Saviynt provides your IT team with a centralized control panel for privileged access management across clouds, applications, and infrastructure. This unified view allows your team to monitor risks in real-time and respond promptly to any potential threats or vulnerabilities.
One of the key capabilities of Saviynt is its role-appropriate access feature. With this capability, your GRC team can enforce access roles, reducing the need for standing privileges. By assigning access based on specific roles and responsibilities, they can minimize the risk associated with excessive access permissions. This approach enhances security and helps maintain a least privilege model within your organization.
It also offers converged Privileged Access Management (PAM) and Identity Governance and Administration (IGA) capabilities. This integration enables smarter decision-making by providing comprehensive privileged access data alongside governance-driven risk mitigation. With converged PAM+IGA, your GRC team can have a holistic view of access privileges and better align them with your governance policies.
In addition to its advanced features, Saviynt ensures compliance with evolving regulations. The platform is authorized and certified by ISO, SOC, and FedRAMP, meeting stringent security standards and regulatory requirements. This compliance readiness helps organizations demonstrate their adherence to industry best practices and regulatory frameworks. - Okta provides a multi-factor authentication solution designed to secure your employees' accounts and prevent credential theft and fraud. Implementing multi-factor authentication ensures that only authorized users have access to sensitive data stored in both customer-facing and enterprise applications. This added layer of security helps protect against unauthorized access and data breaches.
With Okta's ThreatInsight feature, your IT team can automatically block suspicious IP addresses, further enhancing the security of your employees' identities and SaaS application data. By leveraging ThreatInsight, your team can proactively identify and mitigate potential threats by analyzing various risk factors, including network, IP, device, and location, throughout the authentication process.
This contextual approach allows your GRC team to create access policies that dynamically adapt to the level of risk associated with each authentication attempt.
Furthermore, it includes single sign-on capabilities, enabling your employees to authenticate themselves once and access multiple SaaS applications using a single set of credentials. This streamlined access process improves employee experience and simplifies the management and administration of user access for your IT and GRC teams.
Additionally, it offers a centralized platform for your IT teams to view, manage, and secure all employee access.
It seamlessly integrates with various identity stores, such as Active Directory (AD), LDAP, HR systems, and other third-party identity providers. This integration simplifies the onboarding and offboarding processes, ensuring access is efficiently granted or revoked across all applications and systems.
After thoroughly comparing Saviyant and Okta, you may have understood which IGA tool aligns better with your GRC team's requirements. However, it's important not to limit your options to just these two tools. The market offers a range of efficient platforms, and one such alternative worth considering is Zluri. This platform provides exceptional functionalities to streamline the identity governance and administration process and presents itself as a viable alternative to Saviynt and Okta.
So, what exactly is Zluri, and what unique features does it bring to the table? Let's have a quick look.
Zluri: Your Modern Identity Governance & Administration Solution
In today's fast-paced world, with the increasing adoption of SaaS and decentralized work, managing and reviewing user access has become more complex for IT teams. They struggle with visibility into user access, posing security risks to data stored in SaaS applications. Thankfully, there's a solution that tackles these challenges head-on: Zluri.
Zluri is a modern identity governance and administration (IGA) platform that prioritizes identity governance, focusing on data security and compliance. It offers powerful features like a data discovery engine, automated access reviews, and auto-remediation, giving IT teams full visibility into access. This helps them define access policies for reviews and efficiently remediate access issues post-review, ensuring effective access governance.
But that's not all–Zluri goes the extra mile by providing identity administration features. This empowers IT teams to manage access requests and streamline provisioning and deprovisioning processes through automation. As per Kuppingercole's report, by leveraging these capabilities, both IT teams and employees can boost productivity and efficiency, eliminating the need for manual work.
This is just a brief overview of Zluri's capabilities. There's much more to explore! Let's find out how Zluri stands out from its competitors, providing an unparalleled solution for effective access governance.
1. Gain Full Visibility Into User Access Data With Zluri’s Data Discovery Engine
Zluri is better than competitors at discovering data since it is primarily a SaaS management platform. This advantage has made Zluri exceptionally effective in identifying SaaS app and user access data, providing your IT team complete visibility into users' access data.
With Zluri's nine discovery methods - MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional), your IT team can unveil crucial insights. They can seamlessly determine which users have access to which specific SaaS apps, their access rights, their user status (active or inactive), and more. These invaluable insights help your team effectively manage user access and enhance overall SaaS app data security.
Furthermore, equipped with such detailed knowledge, your IT team can easily conduct access reviews. Also, the review process becomes more streamlined, efficient, and minimizes the chances of oversight, ensuring that access privileges precisely match user roles and comply with regulatory requirements.
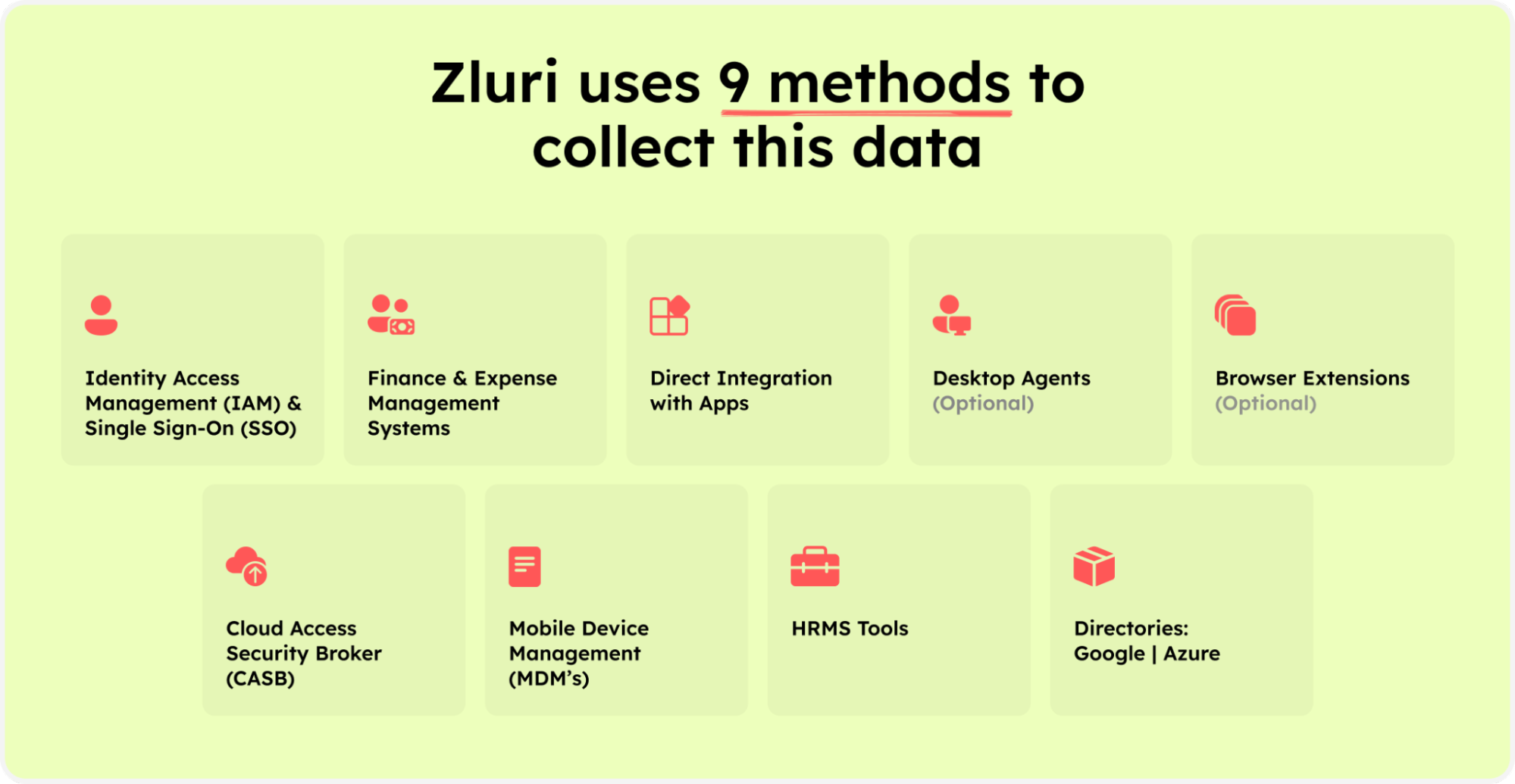
Zluri’s nine discovery methods
2. Automate Access Management With Zluri’s Automation Engine: Ensuring User Access Aligns With Their Role & Responsibilities
Effective access management begins right from the moment an employee joins a company. The IT team is responsible for ensuring that from day one, the right access is granted to the right applications. However, when IT teams manage the provisioning process manually, it becomes prone to errors, affecting productivity and efficiency.
- Ensuring the Right Access Is Granted To the Right Employees
So what Zluri does is it ties user profiles with their digital identity during onboarding. Further, when your IT team verifies user identity to grant them access during the provisioning process, they can simply cross-check the details from a centralized dashboard. Thus, this integration allows your IT teams to accurately assign user access that aligns with their job role.
But it doesn't stop there; Zluri automates the entire provisioning process, granting new employees access with just a few clicks. By automating the process, your team can ensure the right access is granted to the right employees with the right level of permissions to necessary apps. That further boosts employees' productivity by enabling them to start working from day one.
You must be wondering how Zluri automates the provisioning process. Well, your IT team can create onboarding workflows. All they need to do is select users they want to grant access to or onboard and apps (you can even choose from recommended apps option), which all apps they want the users to access.
Then, your team can take necessary actions easily by clicking "add an action." Here, they can schedule the workflow and more.
Zluri even provides in-app suggestions, allowing your team to add employees to different channels, groups, or projects or send automated welcome messages.
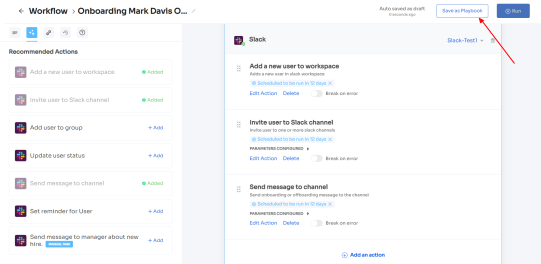
The actions can vary for different applications and are mentioned under recommended actions. Once all the actions are set, you can directly run the workflow or save it as a playbook for future use.
For added efficiency, Zluri offers automated playbooks (i.e. collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.
Note: Apart from that, your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the finance department employees.
- Ticketless Access Management
Now comes a critical phase where the risk of access mismanagement arises. As employees transition to new roles, departments, or require access to certain apps for specific tasks, their access requirements keep changing. Generally, they have to wait for days to approve their app access request since the manual method involves multiple steps. So what Zluri does is it eliminates the time-consuming manual access request process through automation. Let’s see what it does.
To stay updated with the changes, Zluri integrates with HRSM. With the help of this integration, Zluri automatically retrieves and displays updated employee data on a centralized dashboard. By leveraging this integration, your IT team can easily access and verify employee details without manual effort.
This streamlined process ensures access permissions align with current employee roles and responsibilities. Whether granting or revoking access, your team can efficiently manage user privileges based on the most up-to-date information available.

It doesn't stop there, Zluri takes a step further to streamline the access request process by making it ticketless. It offers an Employee App Store (EAS), a self-serve model, which is a collection of applications pre-approved by your IT team. With this self-serve model, employees enjoy the flexibility of choosing any application from the app store and gaining quick access in no time.

All they need to do is raise a request, and the IT team will verify and review their identity before providing access to the requested application. If approved, employees gain access right away. If access is declined, they receive prompt notifications along with reasons for the decision, any modifications made, or suggested alternatives for the application, all viewable in the "Changelogs."

- Revoke Access When Not Required By The Employees
Revoking access from departing employees or those who no longer require certain application access is a critical task for IT teams. Even a single oversight in this process can potentially lead to security breaches, jeopardizing data security.
Zluri recognizes this concern and provides a solution by automating the deprovisioning process. With just a few clicks, your IT team can effortlessly revoke required or all access from employees without missing any crucial steps. This automation ensures timely and thorough revocation, safeguarding SaaS app data from potential security breaches such as unauthorized attempts.
Furthermore, to automate the process, your team can simply create an offboarding workflow. All they need to do is select the users from whom they want to revoke app access and then they will come across a list of recommended actions (such as signing out users, removing them from org units, and more).
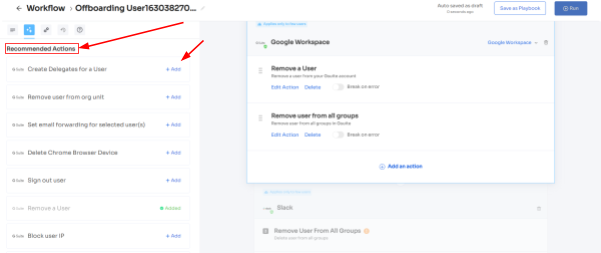
Your team can choose one or multiple actions at once from the list; a point to note is that these actions will be executed post the deprovisioning process. Once all desired actions are added, your team can run the workflow instantly or save it as a playbook for future use.
3. Be Audit-Ready with Zluri's Access Certification Capabilities
The next crucial step in access management is access reviewing, which ensures that every user has the appropriate level of access to apps and data, maintaining data security. However, manual access reviewing can be time-consuming and inefficient, requiring IT teams to gather user lists, user statuses, access patterns, and all the apps to which users have access.
For instance, a user had admin-level access to a specific application, but your IT team revoked those permissions two months ago because they no longer needed such high privileges. However, it's essential to periodically review this user's access to ensure it remains appropriate and that they haven't been granted admin-level permissions again without a valid reason. Manually managing this process would be time-consuming and inefficient.
To address this challenge, Zluri steps in with automated solutions. Zluri automates the entire access review process by collecting all user access-related data in one centralized location. This simplifies the reviewing process for your team or reviewers, removing any complexities and enhancing efficiency.
The capabilities we've discussed so far are just the beginning. Zluri has more exclusive features that set it apart from its competitors, so let’s explore them in detail.
- Unified Access Review
Zluri's unified access review feature empowers your IT team to easily determine which users have access to specific SaaS apps and data. How does Zluri accomplish this? It utilizes an access directory that centralizes all user access-related data in one place.
With the valuable insights provided by the access directory, such as user access permissions (admins, users, or others), and the department the user belongs to, your IT team can thoroughly assess users' access privileges and ensure they align with their designated roles.
Furthermore, Zluri's activity & alerts capabilities are crucial in keeping everything running smoothly. This feature offers real-time information on users' recent activities and notifies IT teams about new logins.
Armed with these insights, reviewers can quickly make decisions during access reviews, ensuring that the right individuals have the appropriate access privileges at all times.
- Automated Access Review
No more manual headaches with spreadsheets and JSONs! Zluri takes the hassle out of access reviews by automating the entire process. Just head to Zluri, create a certification, select the apps and users you want to review, and rest, the reviewers will review and update you about the compilation via email.
So, by automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%. Now let’s move ahead and see how it works.
- Once you have gained access to contextual data through Zluri’s unified access feature, you can step further by creating access rules around these insights. For example, if someone is an admin on Salesforce, you can easily set up a review policy specifically tailored to that scenario.
- Next comes the schedule certification feature, where you can create certifications based on the gathered information. This allows you to take actions based on the insights you've gained. For instance, you can use data like last login, departments, user status (active or inactive), and more to make informed decisions during the review process, such as whether the user can carry on with the existing access or need any modification.
With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. It's a smarter, more efficient way to ensure the right access for the right users, all while keeping your data secure. Zluri's automated access reviews and access rules are the key to simplifying your access governance process.
- Secure access orchestration/auto-remediation
Once the access review is completed, changes will take place as per the set actions during certification creation, so all the actions, such as access modification or removal, are a part of secure access orchestration. This seamless process ensures that access is managed securely and efficiently, safeguarding your organization's valuable data and resources.
For example, while creating a new certification in Zluri, your team will encounter the configuration action where they can create deprovisioning playbooks and modify playbooks. If the reviewers decline certain access permissions, the deprovisioning playbook will automatically execute, and the same goes for the modified playbook. Reviewers must also provide relevant reasons for declining or modifying access permissions.
Point to note: These actions will take place automatically after the review; that's why this process is also known as the auto-remediation process.

Apart from that, Zluri also offers integration features that are quite beneficial at the time of gathering access data. Though Zluri already has data within its platform, but integration allows it to gather even more valuable insights. Leveraging these integrations further enhances your access review process and strengthens the organization's overall security posture.
For example, the top priority for the company is to review the Identity System and core applications, as they pose the highest risk. The Identity System stores crucial employee data and requires timely and thorough reviews to ensure security. So what Zluri does is it integrates with Salesforce, Okta, Azure, and other applications. Further, these integrations play a crucial role in gathering identity system and SaaS app data, providing valuable insights and streamlining the review process.
Additionally, Zluri generates reports that are commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And audit trails act as roadmaps, showcasing the changes made during previous reviews.
For instance, if an employee's admin-level permissions were changed to user-level, it becomes essential to review and ensure that the access remains appropriate or if there were further changes back to admin. Understanding the reasons behind any upgrades is crucial for maintaining proper access control.
So Zluri automatically generates reports on such changes, which further helps in the reviewing process.
So why wait? Book a demo now and witness how Zluri enables your GRC team to streamline identity governance.



Go from SaaS chaos to SaaS governance with Zluri
Tackle all the problems caused by decentralized, ad hoc SaaS adoption and usage on just one platform.
.webp)
















.webp)
.webp)





.webp)