SaaS discovery is key for IT teams to optimize their SaaS stack, but hidden apps or shadow IT pose a challenge. This blog highlights top 8 SaaS discovery methods to tackle this and enhance digital systems.
Are you struggling to manage and optimize your SaaS portfolio?
Well, managing an organization’s SaaS landscape can be overwhelming, often leading to overlooked resources and inefficiencies. Without a complete view of your SaaS landscape, you risk missing out on key efficiencies and opportunities, leading to wasted resources and misalignment with your business goals.
That’s where SaaS discovery comes in. SaaS discovery is more than just keeping track of software— it's about gaining actionable insights that help identify hidden redundancies and align your resources with your company’s goals. Let's explore what SaaS discovery is, its methods and how to make the most of them.
What is SaaS Discovery?
SaaS discovery is the process of systematically identifying and managing the SaaS applications used within an organization. This involves exploring and documenting all software tools across different departments and teams.
The main goals of SaaS discovery are to gain a comprehensive view of your software environment, understand how applications are used, optimize costs, enhance security and compliance, and improve operational efficiency.
Typically, this process uses specialized tools and SaaS Discovery methods to scan networks, analyze data usage, and track user activities. The result is a detailed inventory or map of SaaS applications that helps organizations make informed decisions about software use, licensing, security, and resource allocation.
What are the Key Challenges in SaaS Discovery?
SaaS discovery, while immensely beneficial, comes with its own set of challenges that organizations might encounter:
- Security and Privacy Concerns: Performing SaaS discovery involves accessing and analyzing data related to software usage, raising legitimate concerns about data security and privacy. Safeguarding sensitive information during the discovery process is paramount but poses a challenge.
- Lack of Centralized Visibility: In large organizations or those with decentralized structures, obtaining a centralized view of all SaaS applications used by various departments or teams becomes challenging. This lack of visibility can hinder efforts to comprehensively manage and optimize software usage.
- Shadow IT and Unsanctioned Applications: Identifying all SaaS applications used across an organization can be challenging due to the prevalence of shadow IT. Employees often use unauthorized applications or platforms without IT approval, complicating the comprehensive discovery of all software in use.
- Integration Complexity: Ensuring seamless integration and interoperability between various SaaS applications can be intricate. Discovering how these applications interact and ensuring their cohesive functionality without causing disruptions or data silos requires meticulous attention.
To overcome these challenges, we need to use effective discovery methods to identify the SaaS apps used in your organization. Let’s discuss the top SaaS discovery methods in detail.
8 Best SaaS Discovery Methods For IT Teams
The most effective SaaS discovery methods typically involve combining several approaches to gather diverse perspectives and comprehensive information before making a decision.
1. Cloud Access Security Broker (CASB)
Cloud access security brokers (CASBs) are intermediary software tools that operate between an organization's on-premises infrastructure and cloud services. They regulate access, enforce security policies, and monitor data transmission, safeguarding sensitive information within cloud applications. Here's how CASB platforms help in SaaS discovery and management:
- Network Traffic Analysis: CASBs analyze network traffic to detect and manage SaaS applications. This helps identify unauthorized or unmonitored SaaS usage, commonly known as shadow SaaS, and mitigates associated security and compliance risks.
For instance, a company uses a CASB to monitor and manage the usage of cloud applications across its network. It provides visibility into which SaaS applications are being accessed and helps enforce security policies by blocking unauthorized applications and protecting sensitive data.
- Enforcement of Security Policies: By enforcing security policies across cloud applications, CASBs ensure that data handling complies with organizational standards and regulatory requirements. This minimizes the risk of data breaches and unauthorized access.
- Comprehensive Monitoring: CASBs provide continuous monitoring of data transmission within cloud applications, helping organizations maintain visibility and control over their SaaS environment.
Despite their strengths, CASBs have limitations in detecting SaaS usage outside the corporate network. This poses a challenge for monitoring remote work scenarios, creating a potential blind spot. To address this, organizations may need to implement supplementary strategies such as endpoint monitoring tools and regular audits to achieve comprehensive SaaS oversight and security management.
2. API Connectors
API connectors play a crucial role in software management platforms (SMPs) by accessing and consolidating data from various SaaS vendor portals. Here’s how they help in SaaS discovery and management:
- Data Aggregation: API connectors gather essential information such as user assignments, contact details, and application rosters within a SaaS subscription. This aggregation provides a centralized view of all SaaS applications in use.
- Quick Integration: These connectors swiftly integrate into SMPs, delivering immediate insights. For example, they can identify discrepancies between purchased and allocated subscriptions, revealing optimization opportunities and helping to manage costs effectively.
However, API connectors have their limitations. They only work with known applications and may miss shadow SaaS—unauthorized applications used without IT’s knowledge. Additionally, the effectiveness of API connectors depends on the quality and depth of data provided by each vendor, which can vary. Moreover, SMPs can only support a limited number of connectors, restricting access to the vast array of SaaS applications available.
To overcome these challenges, organizations should combine API connectors with other discovery methods, such as network traffic analysis and regular audits, to ensure comprehensive SaaS management and uncover any hidden applications.
3. Browser Plugin
Deploying a browser plugin is an effective method for monitoring software usage on company-endorsed hardware. Here’s how it helps in SaaS discovery and management:
- Tracking Software Activities: Browser plugins monitor both sanctioned and unsanctioned software activities, providing insights into shadow IT within the organization. This helps in identifying unauthorized software usage and potential security risks.
- Real-Time Monitoring: These plugins offer real-time monitoring of software usage, enabling organizations to respond quickly to any suspicious or unauthorized activities.
However, browser plugins have limitations that cannot monitor activities on personal devices or across different browsers, providing only a partial view of software usage. This means that while they are useful for tracking activities on company hardware, they do not offer comprehensive oversight of all software usage within an organization.
To address these limitations, organizations should use browser plugins alongside other discovery methods, such as network traffic analysis and regular audits, to ensure a more complete understanding of their SaaS landscape.
4. Agents
Agents are essential for analyzing usage patterns across hybrid platforms, providing valuable insights into cost optimization and usage efficiency. Here’s how they help in SaaS discovery and management:
- Cost Optimization: By monitoring user activity across both on-premises and cloud environments, agents help identify opportunities to migrate users from higher-cost tiers to more cost-efficient ones. This ensures that subscription costs align with actual usage, optimizing the overall spend on SaaS applications.
For example: A company deploys endpoint agents to its employees' devices. These agents collect data on the software installed, including SaaS applications used locally or accessed through desktop applications, providing a comprehensive view of SaaS usage across the organization.
- Comprehensive Monitoring: Agents offer detailed insights into how applications are being used, enabling teams to make informed decisions about resource allocation and application management.
Despite their advantages, agents have limitations. They are not as effective as single sign-on (SSO) and API connectors in uncovering shadow SaaS applications—unauthorized software that operates outside of IT’s awareness. Additionally, the implementation process for agents requires more time and resources, leading to a longer time-to-value compared to other discovery methods. This delay can slow down the realization of their benefits.
To mitigate these challenges, organizations should use agents in conjunction with other discovery tools, such as automated discovery and network traffic analysis, to ensure a more comprehensive approach to SaaS management and cost optimization.
5. Single Sign-On (SSO)
Single sign-on (SSO) is a centralized authentication solution that streamlines user access to multiple authorized applications within a company's ecosystem using a single set of credentials. Here’s how it helps in SaaS discovery and management:
- Streamlined User Authentication: SSO simplifies the authentication process, allowing users to access multiple applications with one set of credentials. This enhances user experience and reduces the administrative burden of managing multiple login credentials.
For example, when employees log in to their company portal via SSO, they automatically gain access to various SaaS apps without needing to log in separately to each one. This centralized login helps the organization track and manage SaaS application usage.
- Centralized Control: SSO provides centralized control over access to sanctioned SaaS applications, ensuring that only authorized users can access critical software. This enhances security by enforcing consistent access protocols across integrated applications.
While SSO is one of the effective SaaS discovery methods, it has some limitations. SSO licenses, particularly for enterprise-level tools, can be significantly more expensive, sometimes tripling the cost compared to non-SSO licenses. Additionally, SSO is limited to applications integrated with the SSO system, making it ineffective for detecting or managing access to shadow SaaS applications outside its scope.
Despite these limitations, SSO remains a powerful tool for managing sanctioned SaaS usage within an organization. To achieve comprehensive SaaS governance and monitoring, organizations should complement SSO with other discovery methods, such as network traffic analysis and regular audits, to ensure they capture all applications in use, including unauthorized ones.
6. Pay Records
Analyzing a company's financial records is a reliable method for uncovering existing software contracts. Here’s how it helps in SaaS discovery and management:
- Identifying Active Subscriptions: By tracing expenditures, organizations can identify active SaaS subscriptions that might have been overlooked. This involves examining invoices, direct debits, and staff expenses to find instances where employees have procured SaaS solutions funded by the company.
- Uncovering Hidden Costs: Financial records can reveal hidden costs associated with shadow SaaS, providing insights into all software expenses and ensuring a more accurate budget.
While financial records are crucial for identifying contractual obligations, they offer limited visibility into actual usage patterns. They show what the company is paying for but not how or if the software is being used. To gain a comprehensive understanding of the SaaS landscape, it is essential to complement this approach with other discovery methods.
Integrating financial insights with data from usage analytics or employee surveys can provide a more holistic view. This combination helps organizations understand not only what they are paying for but also how effectively the software is being utilized, enabling better management and optimization of SaaS resources.
7. Web Proxy
Web proxies play a significant role in securing employee internet traffic by evaluating the risk associated with each visited site. Here’s how they help in SaaS discovery and management:
- Risk Assessment and Restriction: Web proxies assess the risk of websites visited by employees, proactively restricting access to potentially harmful sites such as those known for phishing or malware. This enhances overall network security.
For instance, an organization can use a web proxy service to monitor internet traffic. The proxy captures and analyzes data about web applications accessed by employees, including SaaS apps, providing insights into application usage and helping enforce access policies.
- Partial SaaS Discovery: While not primarily designed for SaaS discovery, web proxies can provide some insights by monitoring and logging web traffic. They can identify patterns and usage of SaaS applications, particularly those accessed via the corporate network.
However, web proxies primary function is not focused on identifying SaaS applications, often requiring exhaustive manual analysis to extract relevant insights. Moreover, they rely on network traffic, which means they cannot monitor SaaS applications accessed via personal devices or outside the corporate network.
Additionally, web proxies often require endpoint agents, which can lead to compatibility issues with specific SaaS applications from various vendors. These challenges highlight the difficulties of relying solely on web proxies for comprehensive SaaS discovery and management.
To achieve a more complete SaaS discovery process, organizations should use web proxies in conjunction with other methods, such as automated discovery tools and financial record analysis, to ensure a thorough and effective SaaS management strategy.
8. Rule-based Matching
Rule-based matching in network management involves creating predefined rules that automatically guide the network management system to discover and include specific areas in its topology. Here’s how it helps in SaaS discovery and management:
- Efficient Discovery: Rule-based matching enables the efficient discovery of numerous devices with minimal manual input. It involves creating a set of rules that define specific patterns, characteristics, or metadata associated with various SaaS applications. When these rules are applied to network traffic, user activity, or software inventories, they help in identifying and categorizing applications that meet the defined criteria.
For example, rule-based matching can detect SaaS applications by analyzing URLs, file names, or specific usage patterns. If a rule is set to recognize applications from certain domains or with particular data attributes, the system can automatically flag and categorize these applications in real-time. This is particularly useful for large and dynamic networks where manual discovery would be impractical.
- Automated Compliance: By defining specific rules, organizations can ensure that all discovered devices and applications comply with predetermined standards and policies. It ensures that all software in use is accounted for, managed, and compliant with organizational policies. Altogether, it helps maintain a consistent and secure network environment.
Despite its efficiency, rule-based matching has limitations. It can lead to license constraints due to the sheer volume of discovered devices and applications, and fine-tuning the rules for complex networks can be challenging. Additionally, managing the post-discovery process, including tenant assignments and filtering out excessive discoveries, can be time-consuming.
To mitigate these challenges, organizations should complement rule-based matching with other SaaS discovery methods, such as network traffic analysis tools. This combination ensures comprehensive and accurate SaaS management, reducing the risk of missing critical applications or overloading the system with irrelevant data.
How Discovery Methods Benefit Different Areas of an Organization?
Each department of an organization benefits uniquely from SaaS discovery methods. These methods offer valuable insights and opportunities for optimization, compliance, and strategic decision-making within the organization.
- SaaS Discovery methods for IT and Security
Discovery methods wield significant influence within IT and security domains, offering multifaceted benefits crucial for organizational safety and efficiency.
- Firstly, they serve as invaluable tools for risk identification by meticulously pinpointing every SaaS application in use. This comprehensive visibility significantly curtails the risks associated with shadow IT, minimizing potential security vulnerabilities that might arise from unmonitored software.
- Moreover, these methods play a pivotal role in access control and compliance. By employing discovery methods, organizations can enforce stringent access control measures. This ensures that security protocols are uniformly applied across all software employees utilize, fortifying the overall security posture.
- Additionally, discovery methods contribute immensely to security patch management. IT teams leverage these methods to monitor and manage security patches for diverse applications vigilantly. This proactive approach bolsters cybersecurity, promptly addressing and mitigating software vulnerabilities.
- SaaS Discovery methods for finance
Together, the following aspects showcase how discovery methods in finance streamline spending and budgeting practices and fortify the organization's financial compliance, bolstering its financial health and regulatory adherence.
- Cost Optimization: These methods provide a clear lens into SaaS spending, enabling finance departments to pinpoint underutilized or redundant applications. This insight paves the way for cost-saving opportunities by strategically reallocating resources and optimizing software subscriptions.
- Budget Allocation: With a comprehensive overview of SaaS applications, these methods facilitate precise budget allocation. This understanding ensures funds are directed toward essential tools and licenses, aligning financial resources with operational needs for enhanced efficiency.
- Financial Compliance: Discovery methods play a pivotal role in maintaining financial integrity. These tools ensure compliance with financial regulations and internal controls by monitoring software expenses, reinforcing the organization's adherence to regulatory standards.
- SaaS Discovery methods for procurement
Discovery methods play a crucial role in optimizing SaaS procurement strategies within organizations, particularly in three key aspects:
- Vendor Management: These methods provide an expansive view of the diverse range of software vendors utilized across the organization. By cataloging and analyzing this comprehensive vendor landscape, procurement teams gain valuable insights into vendor relationships, facilitating better vendor management and oversight.
- Contract Negotiation: Leveraging discovery methods to understand the actual usage patterns of various software applications empowers procurement teams during contract negotiations. Armed with precise utilization data, contract negotiations become more informed, allowing contracts to be structured based on real needs, potentially leading to considerable cost savings.
- Optimized Procurement Strategy: The insights gleaned from discovery methods enable a data-driven approach, guiding decisions regarding vendor selection, contract terms, and resource allocation, and optimizing the procurement process.
- SaaS Discovery methods for CIOs & operations
Discovery methods empower CIOs and operational leaders to enhance workflow efficiency, allocate resources effectively, and make informed strategic decisions.
- These methods provide crucial visibility into departments' most utilized and efficient applications. This understanding empowers CIOs and operational heads to streamline workflows by leveraging and encouraging these highly effective tools.
By optimizing workflows, productivity surges, enabling teams to accomplish tasks more efficiently and effectively.
- Understanding the landscape of applications used within operations aids in precise resource allocation. CIOs can strategically direct resources by prioritizing support and optimization efforts toward pivotal tools for daily operations.
This targeted approach maximizes the efficiency of resources, ensuring that time and investments align with the most critical tools necessary for smooth operations.
- Insights derived from discovery methods are critical for strategic decision-making. These revelations inform CIOs and operational leaders about the adoption or optimization of technology.
By aligning these decisions with overarching business objectives, organizations can ensure that technological investments and enhancements are purposeful, contributing meaningfully to the company's growth and competitive edge.
Understanding the impact of discovery methods on organizational areas is crucial. It sets the stage for exploring how various SaaS management platforms like Zluri optimize SaaS discovery and management in the context of enhancing various facets within an organization.
Optimize SaaS Discovery & Management With Zluri
Zluri is a top-tier SaaS management tool designed to streamline the discovery, management, security, and optimization of your SaaS applications from a single platform. As a leading SaaS management platform (SMP), Zluri features the world's largest app library, with over 225,000 applications. This extensive library, combined with advanced discovery methods, ensures comprehensive SaaS discoverability.

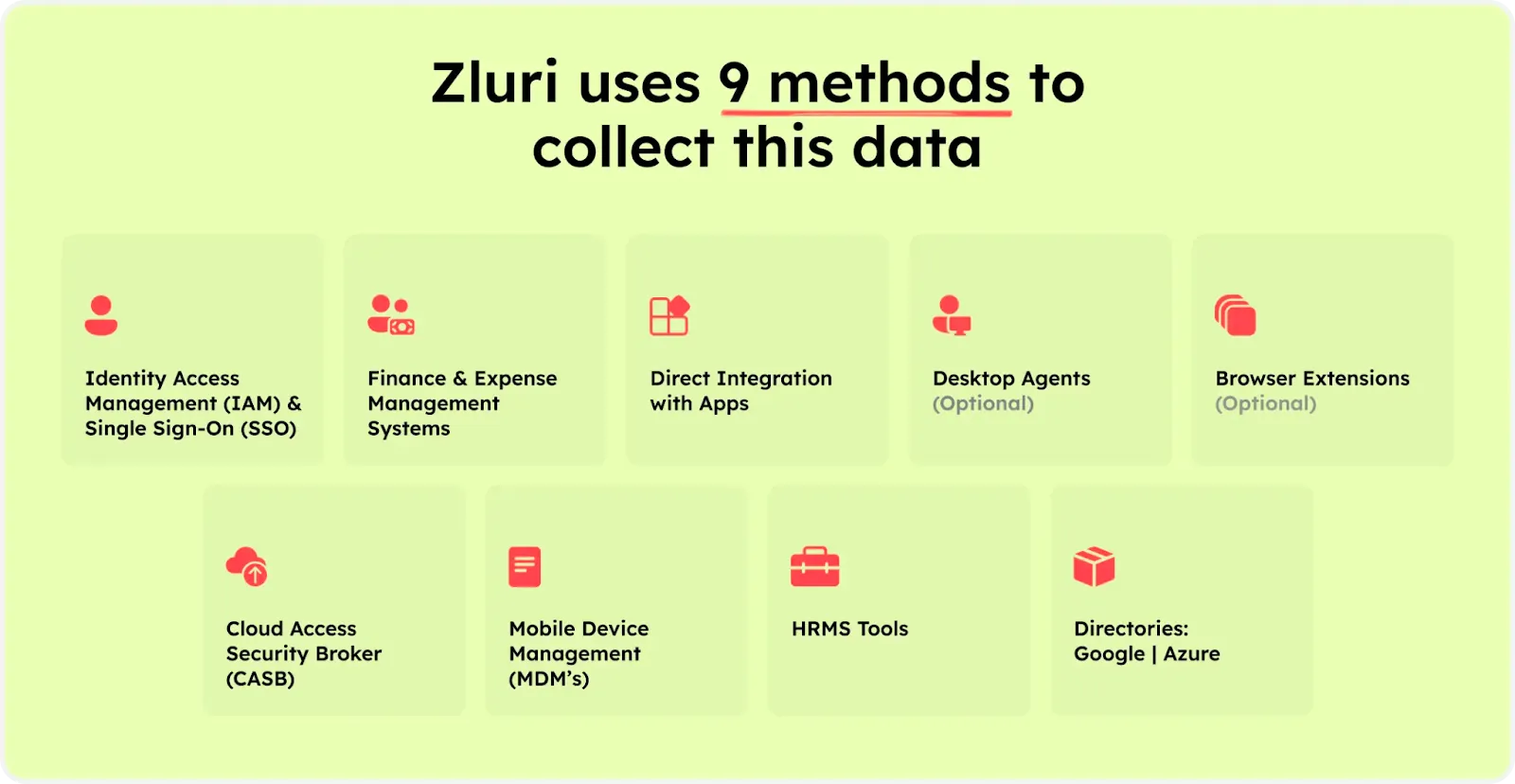
Zluri utilizes 9 robust SaaS discovery methods—IDPs & SSO, Finance & Expense Systems, Direct Integrations, Desktop Agents, Browser Extensions, CASBs, MDMs, HRMS, and Directories—to trace SaaS applications within your organization. This multifaceted approach provides IT admins with a complete view of application usage, enabling effective management of both active and inactive applications.
With real-time insights and detailed reports, Zluri helps you identify and eliminate inefficiencies such as duplicate apps, auto-renewals, unused licenses, and abandoned applications. The platform simplifies usage monitoring, assesses application efficiency, and optimizes licensing costs.
The below-mentioned image shows the unused and underprovisioned licenses of each app in your organization.
Zluri’s automated features streamline IT tasks, including access management, onboarding and offboarding, while also combating shadow IT by revealing unauthorized apps and ensuring compliance with organizational policies. The unified dashboard enables IT teams to manage application renewals, access details, and security from a single command center, enhancing your ability to secure, manage, and optimize your SaaS ecosystem effectively.
Book a demo now to experience the benefits of a leading SaaS management platform!
Embracing the Continual Evolution of the Ongoing SaaS Discovery
To conclude our discussion, it's better to say that SaaS discovery is an ongoing journey rather than a one-time task. As businesses evolve, their software needs change, new applications emerge, and existing ones undergo updates. Staying current requires businesses to be agile and proactive in exploring, evaluating, and integrating new SaaS solutions.
This ongoing process helps them stay aligned with technological advancements, respond to industry changes, and address evolving organizational requirements.
Additionally, embracing continuous SaaS discovery methods enables businesses to optimize their software investments, reduce costs, and ensure that their technology infrastructure supports their shifting objectives and strategic goals.
Frequently Asked Questions (FAQs)
1. How do businesses usually start the SaaS discovery process?
Businesses often begin by identifying their needs, setting clear objectives, and conducting basic research to understand available software options.
2. What mistakes should be avoided during SaaS discovery?
Avoid rushing the process, neglecting scalability needs, overlooking hidden costs, disregarding user feedback, and not considering the long-term implications of the software choice.
3. Are saas discovery methods efficient and accurate?
SaaS discovery methods can be efficient and accurate, but their effectiveness largely depends on the tools and processes used. Automated discovery tools, for example, can quickly scan networks and identify applications, providing a broad overview of software in use.
To enhance accuracy and efficiency, it’s beneficial to combine automated tools with manual methods like conducting regular audits and engaging with different departments.
4. What are the benefits of SaaS Discovery for Your Organization?
SaaS discovery offers several advantages for organizations by providing greater visibility and control over software applications in use. It helps identify all applications being used across the organization, including those that may not be officially approved. This visibility ensures that all software is accounted for and managed effectively. further, it ensures that all software applications adhere to regulatory requirements and internal policies.









.svg)














