Policy-based access control offers a refined approach to managing access rights based on defined policies rather than roles alone. This guide explores how implementing PBAC can strengthen your organization's security posture and streamline access management processes effectively.
As an IT manager, you might face the ongoing challenge of ensuring that the right people have the right access without compromising security.
Traditional methods often rely on role-based access control (RBAC), which can be rigid and limited in adapting to dynamic organizational needs. This can lead to gaps in security, where unauthorized access might slip through unnoticed, posing significant risks to data integrity and compliance efforts.
Enter Policy Based Access Control (PBAC), a sophisticated solution tailored for the complexities of modern IT environments. Unlike RBAC, PBAC allows your organization to define access policies based on specific criteria such as user attributes, time of access, and location. This approach enhances security by enforcing granular permissions and improves operational efficiency by automating access management tasks.
In this article, we delve into the core principles of PBAC, its benefits, and its best practices.
What is Policy Based Access Control (PBAC)?
Policy Based Access Control is a dynamic and adaptable method to manage system user access. Its flexibility in aligning user roles with defined policies allows for precise control over resource accessibility. PBAC grants the ability to swiftly adjust access privileges in response to evolving regulations or internal policies without needing to extensively modify predefined roles across the organization.
PBAC ensures that these policies govern resource access by assigning specific policies to user types. When users attempt to access a resource, the system evaluates their assigned policies to determine if access should be granted or denied. This method allows for a granular control system, ensuring that users only access what their policies permit.
PBAC's versatility extends across various resources, covering files, databases, applications, and network devices, making it a comprehensive solution for access control. Moreover, its synergy with other security models, such as RBAC, enables organizations to implement a layered security approach, strengthening overall protection.
Benefits of Policy Based Access Control
Policy Based Access Control offers a range of benefits that cater to the evolving needs of modern organizations:
1. Consistent policy enforcement
PBAC stands as a robust mechanism that guarantees the consistent implementation of security protocols across an organization's spectrum of systems and resources. By employing PBAC, you can establish a standardized framework for security, significantly reducing the likelihood of oversight or irregularity in access permissions.
This uniformity in policy enforcement plays a pivotal role in mitigating risks associated with potential vulnerabilities. It is a fundamental pillar in fortifying the security architecture by minimizing the chances of unauthorized access or gaps in access control measures.
Through PBAC's consistent application, organizations foster an environment where every access point adheres strictly to predefined security policies, ensuring a cohesive and reliable defense against potential threats or breaches.
2. Reduced administrative burden
PBAC significantly diminishes the administrative workload by consolidating the management of access controls. PBAC simplifies the tasks associated with assigning, modifying, and retracting access privileges across various systems and resources through centralization.
This is achieved through automation and the implementation of policy-driven methodologies. Automation reduces the need for manual intervention in routine access management tasks. By establishing predefined policies, PBAC automates decision-making processes, allowing for consistent and efficient handling of access rights without requiring continuous human oversight.
Consequently, admins are freed from access control management's repetitive and time-consuming aspects. This liberation of resources enables them to focus on more strategic and mission-critical responsibilities within the organization, contributing to improved productivity and operational efficiency.
3. Enhanced security
PBAC offers an agile and responsive security approach by swiftly adapting access privileges to dynamic scenarios or emerging threats. This proactive adaptability is pivotal in fortifying an organization's security stance.
PBAC's agility in adjusting access rights promptly minimizes the window of vulnerability, effectively narrowing the exposure time to potential security risks. This swift response mechanism bolsters the organization's defense mechanisms, mitigating the likelihood of unauthorized access or breaches.
By dynamically altering access permissions in real-time, PBAC strengthens the overall security posture, ensuring that resources remain protected and sensitive data stays inaccessible to unauthorized users. This adaptability serves as a proactive defense strategy, reducing exploitation opportunities and enhancing resilience against potential security incidents.
4. Adaptability for hybrid and remote work
Policy Based Access Control stands out for its capability to facilitate secure access to resources regardless of where users are or their devices. This adaptability is instrumental in upholding stringent security measures while catering to the diverse requirements of a geographically dispersed workforce.
PBAC's flexibility in defining access policies enables seamless yet controlled entry to critical systems and data, ensuring that employees, whether in the office, at home, or on the go, can securely access what they need. This capability to enforce policies based on various factors, such as user roles, location, time, and device type, enables organizations to maintain a robust security posture while accommodating today's dynamic work setups.
By allowing authorized access based on specific conditions and contexts, PBAC empowers companies to embrace the agility demanded by remote work environments without compromising on security. This adaptability fosters productivity and collaboration across dispersed teams and mitigates risks associated with unauthorized access attempts or potential breaches from disparate locations and devices.
5. Risk mitigation
PBAC finely tunes user access privileges by considering multiple factors such as roles, contextual information, and specific situational conditions.
This meticulous approach is a robust barrier against various risks, notably thwarting unauthorized access attempts, potential data breaches, and insider threats. By pinpointing and precisely defining who can access what resources, under what circumstances, and at what times, PBAC significantly narrows down the vulnerability window.
The granularity of these policies means that access is not just based on user roles but also considers contextual aspects, like the user's location, device, time of access, or even the specific task being performed. This contextual understanding adds layers of security, reducing the chances of exploitation by unauthorized entities attempting to breach the system.
5 Best Practices of Policy Based Access Control
These practices are foundational pillars in establishing and maintaining effective Policy Based Access Control within organizations.
1. Clear Policy Definitions
Clear policy definitions in Policy Based Access Control are foundational in establishing precise guidelines tailored to an organization's specific needs. These policies ensure access control measures align with broader organizational goals while reducing stakeholder ambiguity and confusion.
Policy clarity fosters implementation, simplifies compliance adherence, and facilitates effective communication regarding access requirements and potential risks.
By providing a clear and standardized framework, well-defined policies streamline the deployment of access controls and support a more robust and comprehensible access management system within an organization.
2. Implement Least Privilege
Implementing the principle of least privilege is a crucial best practice in Policy Based Access Control due to its profound impact on security and data integrity. Limiting user permissions to the bare minimum essential for their designated roles significantly reduces vulnerabilities and potential security breaches.
This practice minimizes the attack surface, preventing unauthorized access and potential exploitation by malicious entities. Moreover, adherence to this principle ensures heightened data integrity by limiting the risk of unauthorized modifications or exposure of sensitive information.
By implementing least privilege, you and your teams can establish a proactive security approach, mitigating insider threats, enhancing compliance adherence, and maintaining an adaptable security posture within policy based access control.
3. Enforce Separation of Duties (SoD)
Enforcing Separation of Duties (SoD) is a pivotal best practice in access control, ensuring that no single user possesses excessive authority. By dividing access rights across different users or roles, SoD significantly diminishes the risk of internal conflicts, intentional misuse, or inadvertent errors.
This approach reduces the likelihood of conflicts of interest and acts as a safeguard against potential security breaches. SoD enhances accountability and oversight, making it easier to track and audit activities, identify anomalies, and maintain compliance with regulatory standards.
Ultimately, by limiting the capabilities of any single individual, SoD policy serves as a robust defense mechanism against insider threats, bolstering the overall security posture of an organization.
4. Utilize Role-Based Access Control (RBAC)
Implementing role-based access control (RBAC) stands as a crucial best practice due to its ability to streamline access management. RBAC simplifies administration by associating permissions with specific organizational job roles or functions. This approach minimizes complexity by allowing admins to manage access based on predefined roles rather than handling permissions for individual users.
It enhances operational efficiency by providing a structured framework for assigning and revoking permissions, enabling quicker adaptation to organizational changes in roles or responsibilities. RBAC promotes efficiency and strengthens security by adhering to the principle of least privilege, ensuring that users only access resources necessary for their roles.
Additionally, RBAC aids in regulatory compliance by offering a systematic approach to access control, facilitating clearer audit trails, and promoting accountability within the organization.
5. Regular Policy Review and Updates
Regular policy review and agile updates are pivotal in Policy Based Access Control for dynamic organizations. This practice ensures that access control policies remain adaptive and aligned with the evolving security landscape and industry standards.
By consistently reviewing these policies, organizations can swiftly identify and address emerging threats, optimize operational efficiency, and stay compliant with changing regulations.
This proactive approach strengthens security measures and fosters organizational resilience by enabling swift adjustments to access controls in response to evolving business needs and potential security risks.
Policy Based Access Control Use Cases
Let's explore the use cases that exemplify PBAC's indispensable role in safeguarding information integrity and restricting access to authorized entities across various domains.
- Financial Institutions: Banking and financial organizations handle vast amounts of sensitive data. PBAC can be utilized to regulate access to financial records, customer information, and transaction histories.
For instance, a policy might dictate that only specific employees in the compliance department can access transaction data above a certain threshold for regulatory reviews. - Educational Institutions: Schools, colleges, and universities handle student records, grading systems, and research data. PBAC can be employed to control access to these records.
A policy might specify that only faculty members within a particular department can access the research database containing ongoing projects and scholarly articles. - Corporate Environments: In corporate environments, PBAC serves as a crucial mechanism for governing access to sensitive resources, including proprietary information, employee records, and intellectual property.
For instance, PBAC policies can be implemented within a company to define precisely who can access specific repositories or databases. In a scenario involving research and development, PBAC could be utilized to create a policy ensuring that solely authorized members of the R&D team have access to the experimental data repository.
This restriction guarantees that valuable intellectual assets remain safeguarded and accessible only to those individuals directly involved in the designated research initiatives, enhancing data security and preventing unauthorized access or potential breaches.
A robust platform with comprehensive access control capabilities becomes indispensable for implementing and managing Policy Based Access Control across various domains and use cases. This is precisely where Zluri emerges as a game-changer, offering features designed to streamline and fortify identity and access management across organizations.
Empowering Access Control with Zluri: Fortifying Policy Based Access Control
Zluri's Identity Governance and Administration (IGA) platform redefines how organizations enforce and manage access policies, fortifying security measures and bolstering compliance protocols.
Zluri's Advanced Data Engine for Unrivaled Insights and Security
Zluri's advanced data engine revolutionizes IT management by providing comprehensive insights into an organization's application landscape and user data. This innovation addresses IT managers' perennial challenge in fortifying security measures and ensuring organizational compliance.
This data engine integrates nine robust discovery methods designed to cater specifically to the needs of IT teams. These methods includes: MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
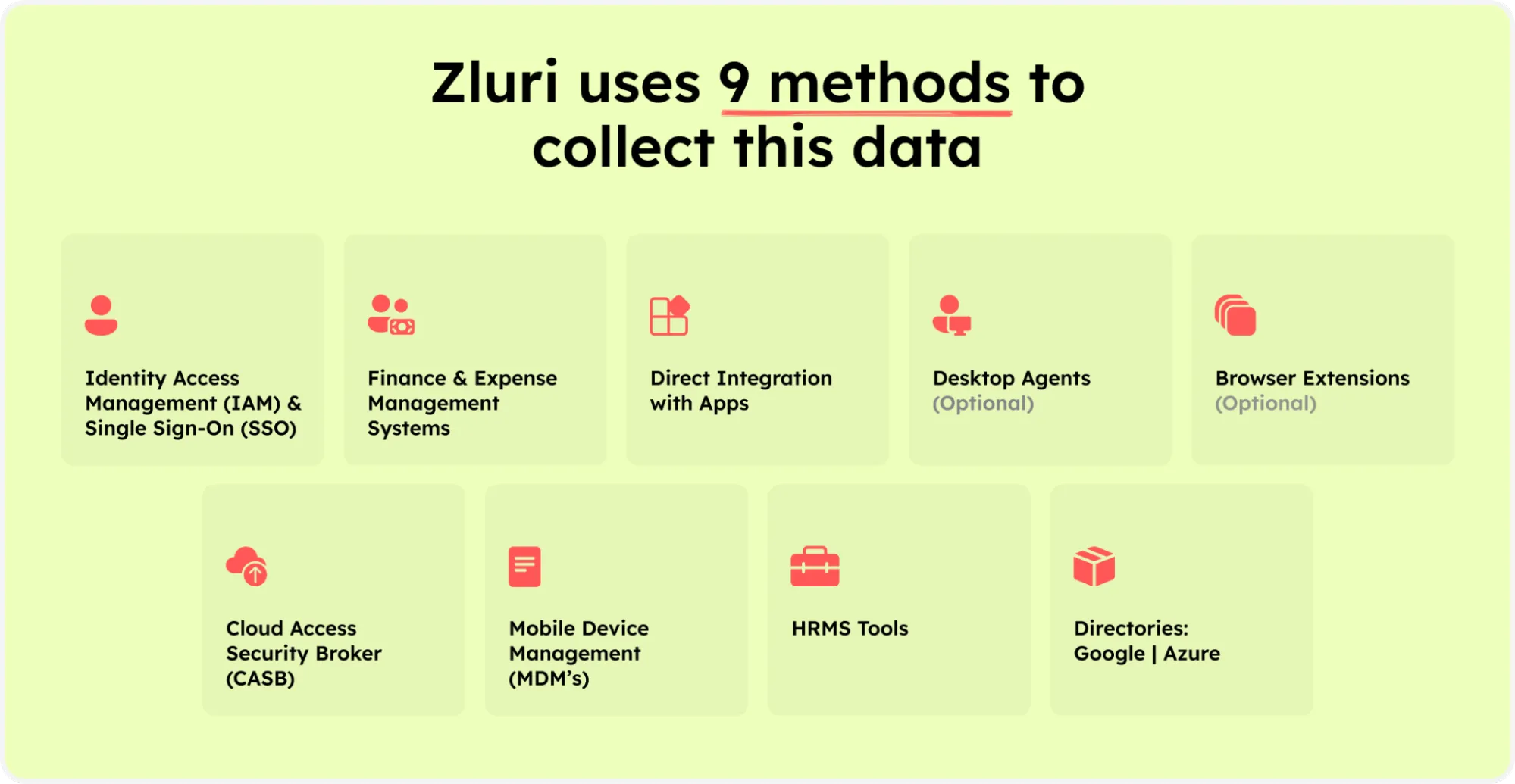
Zluri’s nine discovery methods
These methods provide a comprehensive view of the app ecosystem, allowing teams to swiftly identify users, scrutinize permissions, and pinpoint critical user interactions. This granularity significantly enhances security and compliance efforts.
Zluri's data engine automates app categorization and access tracking, freeing up time and resources. It identifies managed, unmanaged, and shadow IT apps, enabling precise oversight without manual intervention.
Simplify User Lifecycle Management with Zluri's Advanced Automation Engine
Maintaining a secure and compliant environment while efficiently managing user access is an ongoing challenge for IT managers. Handling user lifecycles—initial setup, role adjustments, and permission revocations—requires precision and speed.
Automating access provisioning and deprovisioning eliminates time-consuming and error-prone manual tasks.
Optimize Access Control with Zluri's User Lifecycle Management Platform
Revolutionize access control with a comprehensive solution that simplifies onboarding and offboarding processes while boosting operational efficiency.
- Enhanced Onboarding Experience
Zluri's user lifecycle management (ULM) capabilities revolutionize the onboarding process for new employees by securely granting access to critical resources. Seamlessly integrated with HR systems, Zluri enables your IT team to centrally create user accounts across multiple applications centrally, minimizing errors and administrative burdens. This integration ensures new hires have correct access privileges on their first day.
- Efficient Offboarding Procedures
Covering the entire employee lifecycle, Zluri automates deprovisioning workflows during employee offboarding, swiftly revoking user access across all applications. This proactive approach minimizes risks related to abandoned accounts and potential security breaches, ensuring a seamless transition while safeguarding digital assets during employee departures.
Distinctive Access Control Features:
Zluri offers unique features tailored to enhance access control significantly.
- Customizable Workflows:
Zluri offers the flexibility to create tailored access control workflows. These workflows can be adapted to suit specific user roles, departments, and seniority levels within the organization, ensuring precise and efficient access management.
Onboarding
Offboarding
- Powerful App Recommendations & In-App Suggestions:
Zluri analyzes user profiles and organizational data to provide context-based app recommendations for optimal provisioning.

It also offers in-app suggestions to boost user productivity by recommending actions for efficient task execution. This capability empowers your IT team to make informed decisions, enhancing overall operational efficiency.
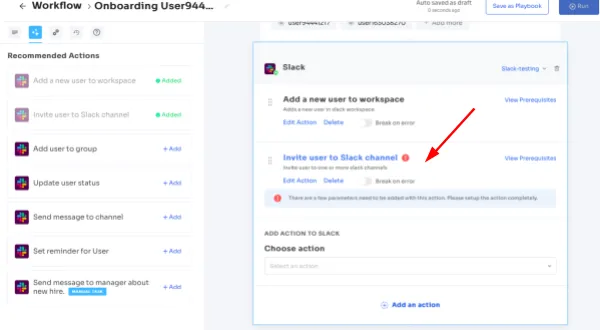
- Reusable Playbooks:
Save customized workflows as predefined "playbooks" with Zluri, eliminating the need to recreate processes for each user. This feature saves time and ensures consistency, allowing quick application of playbooks to maintain efficiency and uniformity in access control procedures.
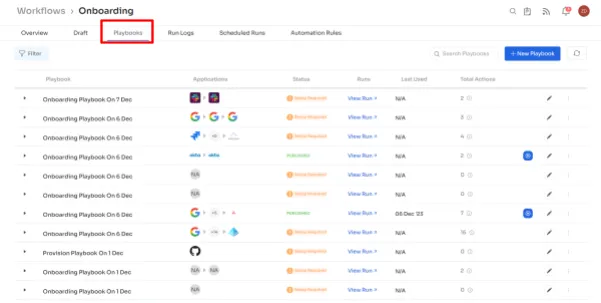
Redefining Access Request Management for Organizational Efficiency with Zluri’s EAS
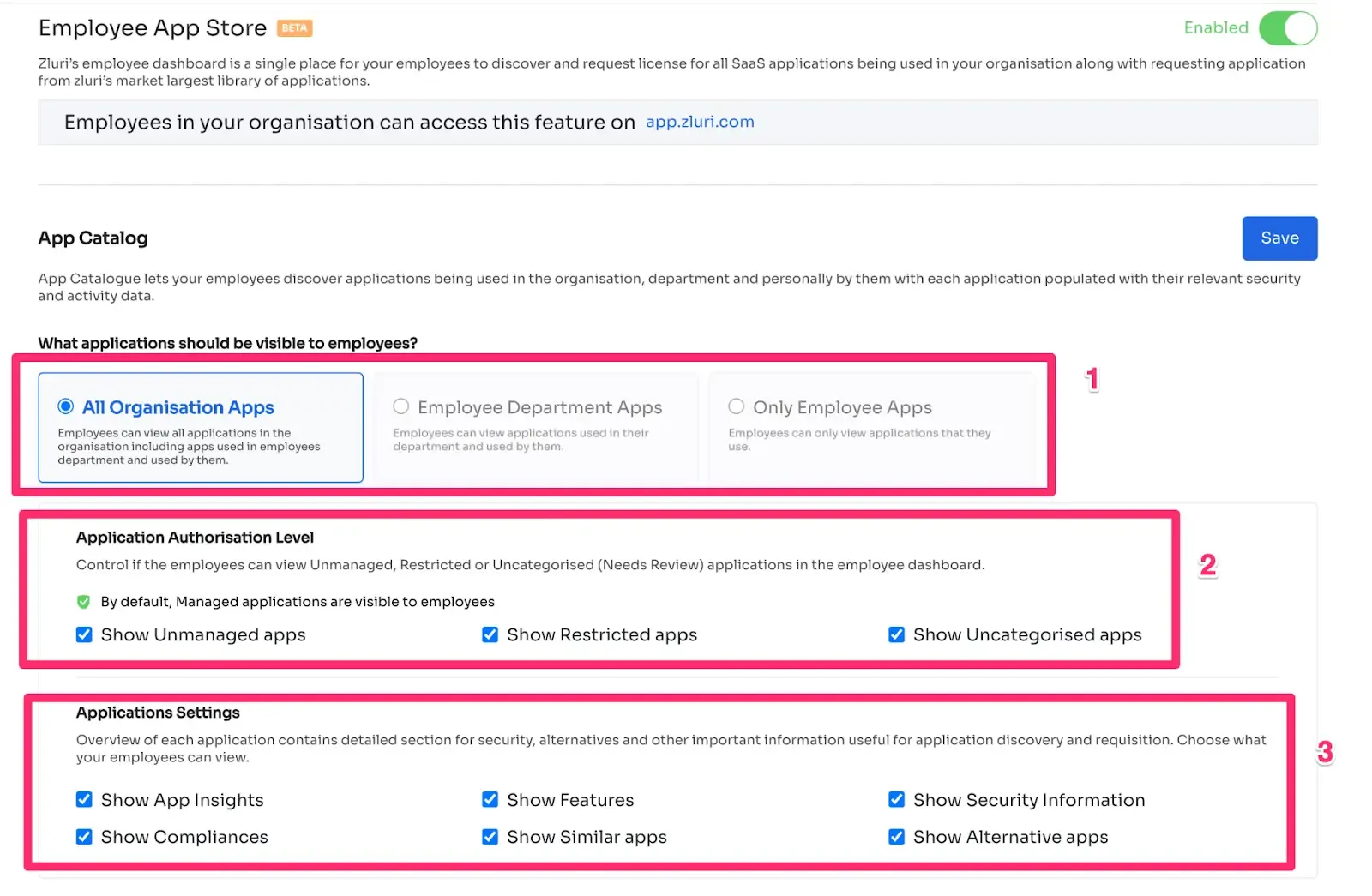
Zluri's Enterprise App Store (EAS) is a game-changer in handling access requests during organizational transitions. This innovative self-serve solution simplifies the complex task of managing user access with a suite of advanced features to optimize resource allocation efficiently.

- Precise Role-Based Access Control:
EAS is engineered to adapt role-based access control permissions during role shifts swiftly. By tailoring permissions to match individual job roles, it ensures that employees have precisely the right access required for their tasks. This precision enhances security by limiting access to sensitive enterprise data.
- Meticulous Access Approval Process:
EAS empowers designated approvers to thoroughly review access requests according to specific job roles and responsibilities. This meticulous approach ensures that permissions granted are finely tuned to meet each individual's unique organizational needs.
- Transparent and Hierarchical Approval System:
EAS maintains centralized control while involving app owners, managers, and IT admins for efficient approvals, with higher-level oversight for streamlined workflows.
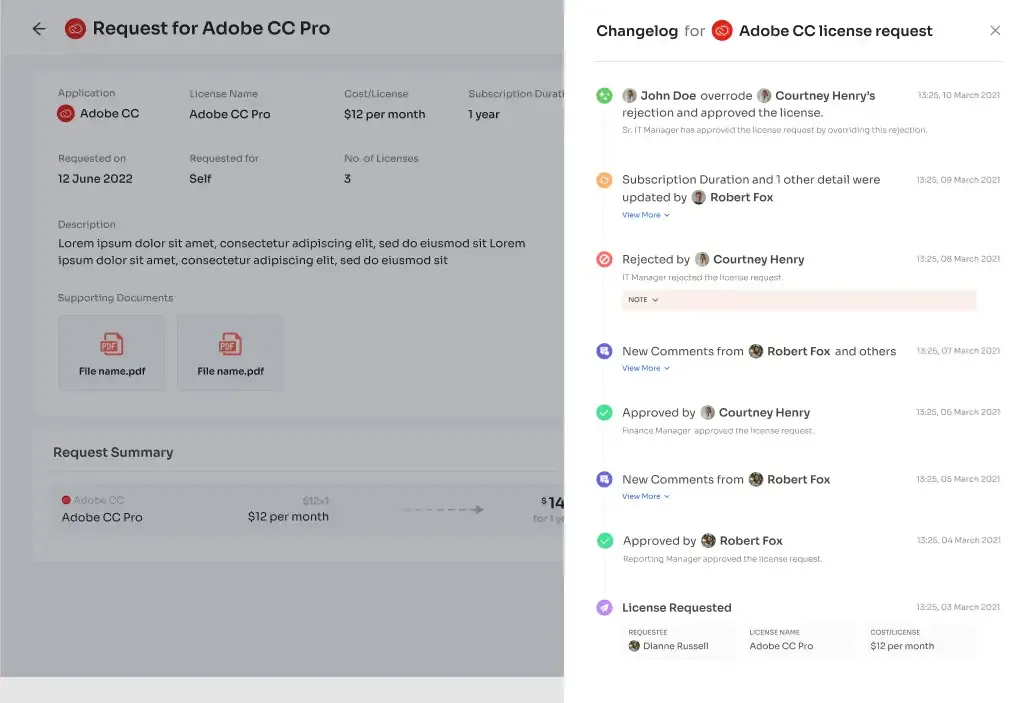
- Transparent Rejection Management:
In cases of denied access requests, EAS provides detailed explanations for the rejection. This transparent approach fosters a culture of understanding by elucidating the reasoning behind decisions, promoting collaboration within the organization.
Customized Request Modifications:
EAS offers flexibility by allowing approvers to modify access requests to suit evolving organizational requirements. This agility ensures that access permissions can be adjusted promptly to meet changing needs, enhancing operational efficiency.
- User Empowerment through Change Tracking:
The "changelog" feature in EAS keeps users informed about updates related to their access requests. This transparency gives users visibility into their requests' status, encouraging engagement and fostering a collaborative organizational culture.
Zluri's EAS optimizes access request management with precise control, transparent processes, and adaptability, making it an invaluable asset during role transitions.
Strengthen Compliance with Zluri's Access Certification Solution
Zluri’s access certification solution is a powerful ally for IT managers and their teams, meticulously crafted to strengthen security measures and ensure strict compliance adherence within organizational frameworks.
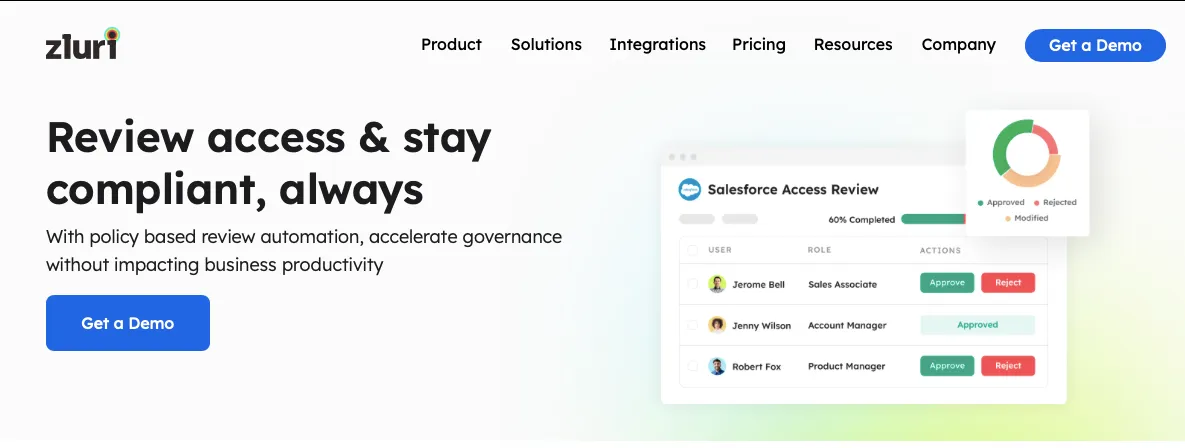
- Empowering Access Management: Zluri's platform enables IT teams to proficiently handle user access rights and permissions, effectively reducing risks associated with unauthorized access and compliance gaps across critical organizational applications and systems.
- Unified Collaboration: Zluri brings together key stakeholders—security, IT, and auditors—into a cohesive platform. This consolidation streamlines the entire process, from reviews to comprehensive reporting, fortifying the organization's security and compliance foundations.
- Sophisticated Automation: A notable feature is its advanced automation, leveraging precise algorithms for assessing user access rights. Customizable review parameters and scheduled evaluations ensure efficiency during pivotal moments like employee transitions.
- Proactive Security Measures: Zluri's proactive auto-remediation swiftly addresses access violations, minimizing the risk of unauthorized breaches. It efficiently adapts access rights during role changes or employee departures, reinforcing a robust security framework.
- Insightful Reporting: The solution's reporting capabilities provide comprehensive insights into access patterns, vulnerabilities, and compliance statuses. These detailed analyses empower IT teams to make informed decisions, strategically manage access controls, and identify potential risks or inefficiencies for rectification.
Why wait any longer? Schedule a demo now and witness the incredible capabilities of Zluri's access control and governance features firsthand. Experience the power for yourself!
FAQs
1. How does PBAC differ from other access control models like RBAC and ABAC?
PBAC defines policies that dictate access based on various attributes, such as user roles, attributes, time, location, and more. RBAC (Role-Based Access Control) primarily uses roles to manage access, while ABAC (Attribute-Based Access Control) uses attributes dynamically.
2. How are policies defined in PBAC?
Policies in PBAC are defined based on a combination of factors such as user attributes (roles, department, clearance level), resource attributes (file type, sensitivity), environmental conditions (time of access, location), and relationships between entities.
3. Is PBAC suitable for compliance and regulatory requirements?
Yes, PBAC can aid organizations in meeting compliance standards by providing a structured approach to access control. It allows for implementing specific access controls mandated by regulations like HIPAA, GDPR, or PCI DSS.









.svg)














