The PCI report gives valuable insights into compliance gaps, security risks, and areas for improvement. But what should it include, or how should the report be prepared? This article explores the key details that you need to know about the PCI report.
Achieving PCI DSS compliance is important for protecting your payment data. But following the rules is not enough—you must prove it during the audit. Auditors require clear evidence to confirm that your organization meets the necessary security requirements. This is where a PCI report comes in, serving as evidence during the audit process.
However, generating a PCI report that meets all the specific requirements can be challenging. For instance, imagine your team generates a report based on outdated software or inaccurate data. The auditors would quickly identify that the report does not fully reflect the organization's current security posture, making it irrelevant for the compliance check.
To overcome this challenge, your team must generate proper reports showing your commitment to PCI DSS compliance. Therefore, this post will cover the details of the PCI report, including its advantages, who needs the report, what to include, how to create it, etc.
Who Needs the PCI Report?

A PCI report is required by various stakeholders involved in handling payment card information.
Here’s who needs it and why:
- As an IT manager, you are required to implement and maintain systems that comply with PCI DSS standards. The PCI report will provide you with a clear view of security measures and ensure that you are audit-ready.
- Auditors require the PCI report to evaluate your organization’s adherence to PCI DSS requirements. It will give them the evidence they need to verify that all your security controls are in the proper place.
- Business owners and senior leaders will use the report to understand their organization's compliance status. It will assist them in tracking risks and making decisions to avoid penalties and data breaches.
- Merchants and service providers that accept and process credit card payments from various sources need the report to demonstrate their commitment to protecting customer data.
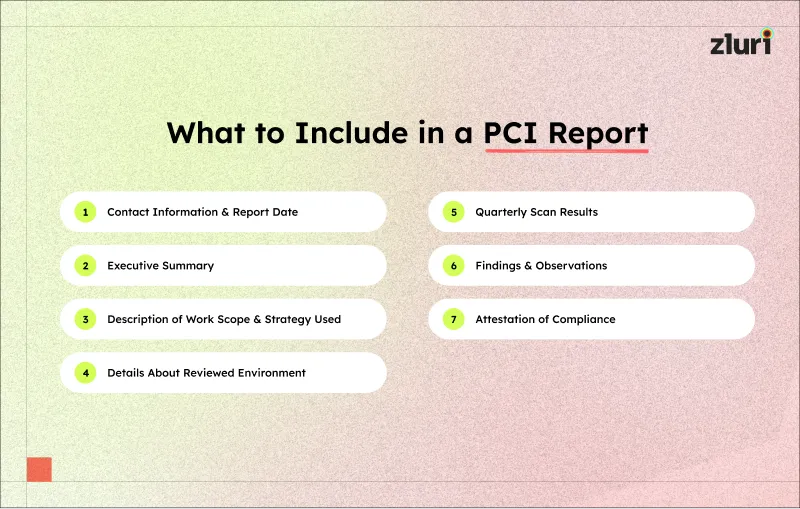
7 Key Information to Include in a PCI Report
Let’s understand the details or information to include in a PCI report.
1. Contact information and date of the report
A PCI report should begin with your organization’s basic details, including name, contact information, address, primary contact person, etc. It should also include the date when the report was completed. This will ensure that the report is updated and can be referred to by anybody who needs it in the future.
2. Executive summary
The executive summary provides a brief overview of the report. It summarizes the compliance process, the purpose of the assessment, and the overall findings. This section is generally for stakeholders who want quick insights without going through the technical details.
3. Description of scope of work and strategy used
The report should clearly define the scope of the assessment, mention the systems, networks, and processes included in the review, and outline the strategy used, whether it involved vulnerability scans, penetration tests, or other auditing methods.
4. Details about the reviewed environment
The PCI report should include a description of the environment assessed during the review. This description should involve systems like servers, databases, cloud applications, and payment terminals. It should also explain their role in handling your organization’s sensitive cardholder data and why they were part of the scope.
5. Quarterly scan results
This section in the report includes the results of quarterly vulnerability scans. It will highlight the issues identified during these scans and document how they are resolved. This will reflect your organization’s commitment to continuous monitoring and improvement.
6. Findings and observations
This section will discuss any vulnerabilities, gaps, or non-compliance issues discovered during the assessment. It will also offer recommendations for addressing these problems. Further, the section will mention positive observations, such as successful implementations or areas that exceeded compliance requirements.
7. Attestation of Compliance
The attestation of compliance (AOC) is the end of the report with an official declaration of compliance. It is a formal statement that a qualified assessor or responsible team member signs. It will confirm that your organization has met the PCI DSS requirements.
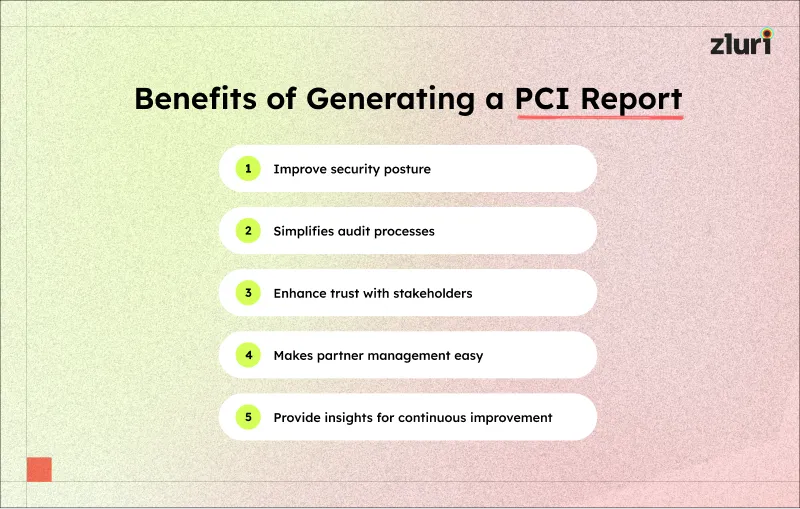
Practical Advantages of Creating a PCI Report
Now, let’s discuss the practical advantages of having a PCI report in place.
- Improves your organization’s security posture: A PCI report helps you identify vulnerabilities in your systems and processes, permitting you to cope with gaps and protect against cyber threats. For instance, you might discover an outdated firewall configuration during a PCI review. Fixing this immediately will reduce the risk of unauthorized access to your organization’s sensitive data.
- Simplifies your audit processes: Maintaining a PCI report will prepare you for audits. It provides all the necessary documentation in one place, reducing last-minute stress. For instance, if a financial institution undergoes an external security audit, a well-prepared report streamlines the process and saves time.
- Enhance trust with your stakeholders: Sharing your PCI compliance status builds trust with your stakeholders, such as customers, partners, and regulators. It assures them that your organization prioritizes safety. For instance, an online retailer can display its PCI compliance badge on its website. This reassures customers that their payment information is safe.
- Makes management of partners easy: The report will help you assess the compliance of your partners, like third-party vendors and service providers, who handle your payment data. Reviewing their practices will help you ensure they align with your security standards. For example, a SaaS provider can use the report to verify that their payment gateway vendor meets PCI DSS requirements.
- Provide operational insights for continuous improvement: A PCI report may provide precious insights into your IT environment, helping you optimize your processes and improve efficiency. For example, you might identify redundant systems during the compliance review and have removed them. Referring to this in the report will help you in the future, improving your process continuously.
5 Steps To Prepare an Effective PCI Report

Here's a step-by-step process to understand how to prepare the report.
Step1: Understand your PCI DSS requirements
The first step in creating a PCI report is to understand your organization's PCI DSS requirements. Knowing them will help you protect your organization's cardholder data and prevent security breaches. Also, identify which requirements will apply to your organization. These will depend on factors like your organization's size and how you handle payment data.
Step 2: Identify your scope of assessment
The next step is to determine the scope of your PCI DSS assessment. This will involve all your organization's systems, processes, and networks that store, process, or transmit cardholder data. Narrowing down your scope will help you save time and focus on the important areas.
Step 3: Conduct a review to identify compliance gaps
You must perform a gap analysis to identify areas where you lack in meeting PCI DSS compliance requirements. For this, review your security controls, processes, and systems. This will highlight the weaknesses or vulnerabilities that need to be fixed. Also, these gaps should be addressed appropriately to meet the required standards.
Step 4: Document everything for the audit
Documentation is a crucial part of the PCI DSS audit. You must record all your organization's policies, procedures, and security controls related to compliance. This includes evidence of the steps you've taken to meet PCI requirements. Moreover, a well-documented process will show auditors that your organization is committed to compliance.
Step 5: Engage with the Qualified Security Assessor (QSA) to conduct a formal audit
The final step is to find a suitable Qualified Security Assessor (QSA) to conduct a formal audit. QSAs are certified experts who validate your compliance. They will review your systems, documentation, and practices. Therefore, collaborating with them will help ensure your PCI report is complete and accurate.
Examples of Aspects Covered in the PCI Report
A PCI report identifies various instances where your organization might be unable to meet the PCI DSS requirements. Here are some examples.
- Inadequate Encryption Practices
The report will identify a violation if payment card data is stored or transmitted without proper encryption. For example, if sensitive cardholder information is sent over an unencrypted channel, attackers can intercept it, leaving the organization exposed.
- Weak Access Control Measures
The PCI report will identify instances where access to cardholder data is not properly restricted. If employees or third-party vendors have unnecessary access to sensitive information, auditors will point this out.
For instance, if an employee has access to payment data but does not need it for their job, the report will flag this.
- Failure to Apply Security Patches
Outdated software and unpatched vulnerabilities are a major concern. If the IT team fails to regularly apply security patches to critical systems, the PCI report will highlight this as a risk.
For example, a system running outdated payment processing software could leave the organization vulnerable to known exploits.
- Lack of Proper Logging and Monitoring:
The report will identify insufficient logging and monitoring of systems that handle payment data. Auditors will identify this gap if critical systems are not being monitored for unusual activity or potential breaches.
For instance, if login attempts or data access events are not being logged, the report will highlight this as a concern.
Keep Your Organization Audit Ready with Zluri
One key requirement of PCI DSS is to limit access to cardholder data based on the “need to know” principle. This means that only authorized users should have access to your organization’s critical data. But how can you ensure that access remains restricted over time? To do this, you need to conduct a user access review.
Regularly reviewing who has access to what systems will help prevent unauthorized access and reduce your security risks. However, manually doing this can consume time and increase the risk of human errors. Thus, you can use tools like Zluri to automate the review process.
Zluri offers an access review solution that simplifies ensuring that the right user has the right access at the right time. It provides detailed reports on user access across your apps, including information about users, their app role, review status, remediation status, and more.

Now, what happens when auditors ask for evidence? Zluri’s access review reports are ready to be presented as evidence during PCI DSS audits. The auditors can assess the users’ access and permissions based on this report.
Moreover, these reports can be downloaded or exported easily and shared with the relevant stakeholders, saving time and allowing you to focus on more important tasks.
Let’s take Monday as an example to see how you can automate access review in Zluri.
Also Read: If you want to adhere to PCI DSS compliance, go through the PCI DSS compliance checklist.
Frequently Asked Questions (FAQs)
1. Who is authorized to check PCI compliance?
Qualified Security Assessors (QSAs) are experts authorized by the Payment Card Industry Security Standards Council (PCI SSC) to evaluate and audit an organization’s compliance with PCI DSS. These certified professionals assess whether your business meets the required security standards to protect payment card data.
2. What is a credit card transaction?
A credit card transaction occurs when a cardholder uses their credit card to make a payment to a business or merchant.
3. What are the PCI compliance requirements?
Here are a few PCI compliance requirements.
- Use and Maintain Firewalls
- Proper Password Protections
- Protect Cardholder Data
- Encryption of Transmitted Cardholder Data
- Utilize Antivirus and Anti-malware Software
- Properly Updated Software
- Restrict Data Access
4. What is security log management?
Log management infrastructure includes the hardware, software, networks, and storage systems used to create, transmit, store, analyze, and manage log data. These infrastructures typically handle various tasks that help ensure the effective analysis and security of log information.


.webp)



.svg)














