
Top 3 Challenges of Mid-Lifecycle Change Management
As an IT manager, it's imperative to prioritize mid-lifecycle changes and navigate through the challenges they bring. Let’s explore the challenges of managing mid-lifecycle changes and the necessary steps to address them effectively.
In the realm of IT automation, onboarding, and offboarding processes often steal the spotlight. However, there is an overlooked aspect that can revolutionize your IT operations: mid-lifecycle management workflows.
While they may not receive the same recognition, these workflows can streamline manual work when employees transition to different departments or relocate to new cities within your organization. By implementing efficient mid-lifecycle management workflows, you can unlock new levels of productivity and efficiency for your IT teams.
Let’s explore the key challenges you face when it comes to mid-lifecycle changes and provide insights on how to address these challenges. By understanding these obstacles and implementing the right strategies, you can ensure a smooth and successful transition while maximizing the value derived from your SaaS apps.
Top Challenges Faced in Managing Mid-Lifecycle Changes
Let's delve into the challenges and discover actionable solutions to optimize your mid-lifecycle change management processes.
1. Insufficient automation capabilities
Insufficient automation capabilities can create challenges for you and your IT team, impacting their efficiency and productivity. Manual processes are time-consuming and prone to errors, wasting time and resources. This not only hampers operational efficiency but also places a burden on you to address the resulting issues and delays.
However, by embracing automation, you and your IT team can experience numerous benefits. Automation eliminates the need for repetitive manual tasks, allowing you to reclaim valuable time that was previously spent on mundane activities. This time savings can be utilized for more strategic initiatives and addressing higher-value tasks that drive business growth.
Automation streamlines critical processes such as application deployment, configuration management, and system updates. These tasks can be executed swiftly and flawlessly, reducing errors and improving overall reliability. Automation establishes a solid foundation for stable operations by ensuring consistency, enhancing system security and customer satisfaction.
By leveraging automation, you can optimize resource allocation, improve operational efficiency, and deliver better results. It empowers you to focus on strategic initiatives, adapt to evolving business needs with agility, and drive innovation within the organization.
2. Fragile data security & lack of privacy
Without proper attention to data security and privacy, organizations become vulnerable to data breaches, unauthorized access, and the potential consequences of non-compliance with regulatory mandates.
Data security and privacy pose a challenge during employee mid-lifecycle changes primarily because of the potential for unintended exposure of sensitive information. System upgrades or migrations often involve transferring data to new platforms or environments, creating opportunities for data leakage or unauthorized access if adequate precautions are not taken.
Without robust security measures in place, you expose yourself to the perils of data breaches, unauthorized access, and the specter of non-compliance with regulatory mandates. But fret not; you can rise above these challenges by proactively addressing data security and privacy concerns during mid-lifecycle changes. You can:
- Conduct a thorough risk assessment to identify vulnerabilities and prioritize security measures.
- Utilize encryption and secure protocols (SFTP, FTPS) for data in transit and at rest. Leverage VPNs for secure remote connections.
- Implement strong authentication, password policies, and role-based access controls to prevent unauthorized data access.
- Safeguard privacy by using data masking and anonymization techniques when sharing with third parties.
- Stay updated on regulatory requirements (GDPR, HIPAA, PCI DSS) and implement appropriate controls.
These measures can transform mid-lifecycle changes into opportunities for growth, fortified data security, and unwavering stakeholder trust.
3. Not having appropriate knowledge transfer & training
The lack of appropriate knowledge transfer and training poses a significant challenge during mid-lifecycle changes. When key personnel leave or applications undergo updates, the continuity of knowledge becomes uncertain. Without effective knowledge transfer and training programs in place, new team members and stakeholders struggle to adapt swiftly to their roles.
This challenge can lead to disruptions, decreased productivity, and jeopardize critical projects. It becomes crucial to address this issue proactively in order to minimize the negative impacts. Failing to prioritize knowledge transfer and training initiatives during mid-lifecycle changes can result in turbulent transitions, interrupted operations, and a missed opportunity to embrace innovation.
Overcoming this challenge requires identifying and capturing critical knowledge, establishing a centralized hub of wisdom, developing tailor-made training programs, fostering mentorship and cross-training opportunities, and cultivating a culture of perpetual learning within the organization. Investing in knowledge transfer and training becomes imperative to successfully navigate mid-lifecycle changes and ensure the organization's sustained growth and success.
To tackle these hurdles head-on, you must invest in cutting-edge automation tools, implement intelligent recommendation systems, and establish a centralized platform for seamless software management. By embracing these transformative solutions, you can unlock the power to conquer mid-lifecycle challenges like never before. One such platform is Zluri.
How Zluri Helps Manage Mid-lifecycle Changes Efficiently
Imagine this: one of your valuable IT team members needs to transition from the IT department to the procurement department to support the organization's evolving needs. While this change is necessary, granting and revoking access to applications and business resources can be complex based on shifting job profiles. Manual efforts become arduous and prone to errors, consuming valuable time and resources.

Enter Zluri, the game-changing platform that simplifies and automates midlife cycle changes. With its advanced access management capabilities, Zluri empowers your IT admins to seamlessly manage access permissions, ensuring employees have the right resources for their new roles while safeguarding data security.
But wait, there's more! Zluri goes above and beyond by offering an Employee App Store. Gone are the days of waiting for approval and wasting precious time. Zluri's Employee App Store ensures that employees quickly gain access to the applications they need to hit the ground running.

The Employee App Store grants your employees the freedom to choose from a wide range of applications available in the store, enabling them to quickly gain access to the tools that enhance their productivity and effectiveness. No more tedious back-and-forths or waiting for IT to grant access. With just a few simple steps, your employees can request access to the applications they need, putting them in control of their technology stack.
To request access to an application through the EAS, the process is straightforward:
- Switch to Employee View: On the Zluri main interface, locate the icon in the upper right corner and click on it. A drop-down menu will appear, and from there, select 'Switch to Employee View' to access the Employee View interface.
- Request Access: The Overview dashboard will be presented by default in the Employee View. To initiate the access request, click on 'Request Access to an Application.'

- Enter Application Details: A dialogue box will appear, allowing your employees to enter the application name they require access to. Clicking 'Continue' will move them to the next step.

- Exploring Similar Applications: In some cases, certain applications may not be used in your organization. However, employees can still request them. Clicking 'Continue' will display a dialogue box showing similar applications commonly used within the organization.

- Choosing a Similar Application: If employees find a similar application suitable for their needs, they can simply click on it to proceed with the request.
- Ignoring and Continuing: Alternatively, if they wish to continue with their initial request, they can click on 'Ignore and Continue.'
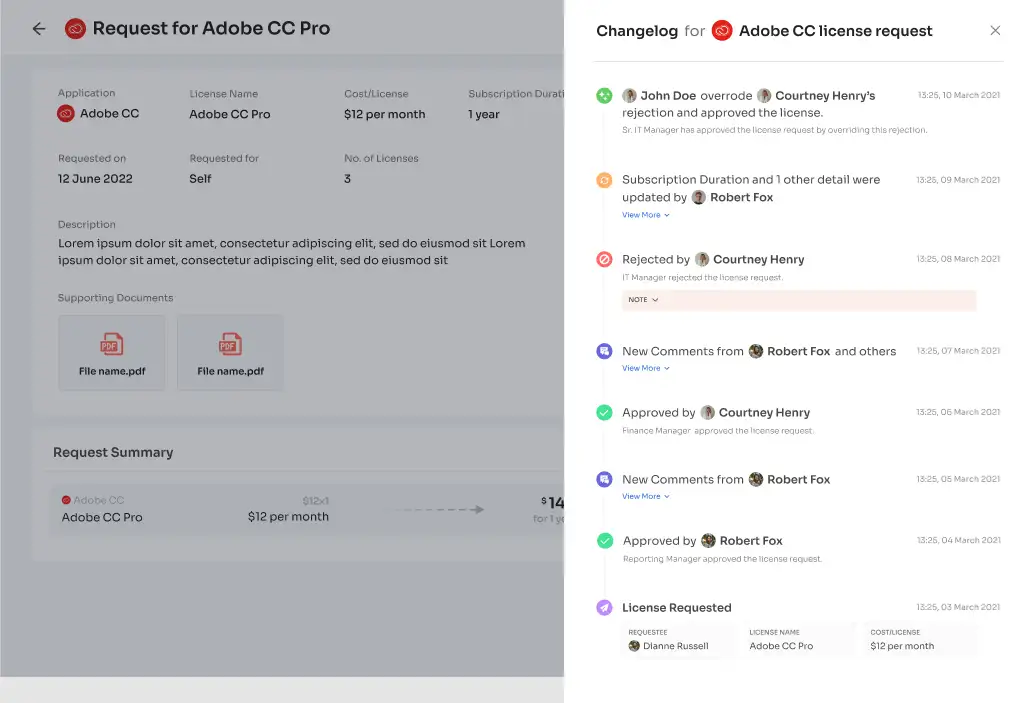
- Providing Required Details: The next step involves providing essential details, such as selecting the license plan, subscription duration, and describing the reasons behind the application request. Additionally, employees can attach any necessary supporting documents. Once all the information is filled out, they can click on 'Confirm Request.'

- Staying Updated: If there are any modifications to the request or if one of the approvers suggests alternative applications, employees can conveniently check the 'Changelogs' section to stay updated with the progress of their request.
In addition to providing your employees with a wide range of approved applications, Zluri's Employee App Store offers powerful integration with the SaaS Buying services. This unique synergy allows you to leverage the expertise of Zluri's SaaS buying team to secure the best possible pricing for your SaaS contracts.
Apart from that, Zluri goes beyond access management and app selection and combats the shadow IT phenomenon. By comprehensively discovering and monitoring existing SaaS applications, Zluri enables you to maintain control over the software landscape. This ensures compliance, minimizes security risks, and eliminates the potential chaos caused by unauthorized applications operating outside IT's purview.
Furthermore, Zluri empowers your IT admins to monitor access permissions for all employees, offering valuable insights into user activities. Regular audits and detailed reports enable proactive security measures, mitigating risks and ensuring adherence to organizational policies and industry regulations.
So, IT managers, embrace the power of Zluri! Let it be your guide in managing midlife cycle changes easily and efficiently. Book a demo now!



Go from SaaS chaos to SaaS governance with Zluri
Tackle all the problems caused by decentralized, ad hoc SaaS adoption and usage on just one platform.
.webp)
















.webp)
.webp)





.webp)