OpenID Connect (OIDC) and Security Assertion Markup Language (SAML) are the most popular authentication protocols. Although both share similar purposes, i.e., verifying digital identity (ensuring that users are who they claim to be), but the way they manage the authentication process varies greatly. In this article, we'll explore how OIDC vs SAML differ.
But you may ask, 'Why is it important to understand the difference between OIDC vs SAML?' Well, OIDC and SAML authentication protocols apply to different, specific use cases.
So if you try to use the wrong authentication protocol in the wrong situation (like using OIDC authentication protocol in the banking sector – note: OIDC lacks the specific features required to authenticate financial institutions' customers and protect sensitive data ), you will probably end up with results that don't align with your expectations. It's just like applying the wrong formula to solve a problem, which won't work or give the right result.
Therefore, it's important to understand which authentication protocols suit your needs and how they differ.
So, let's start by understanding what OIDC and SAML are.
What Is OIDC?
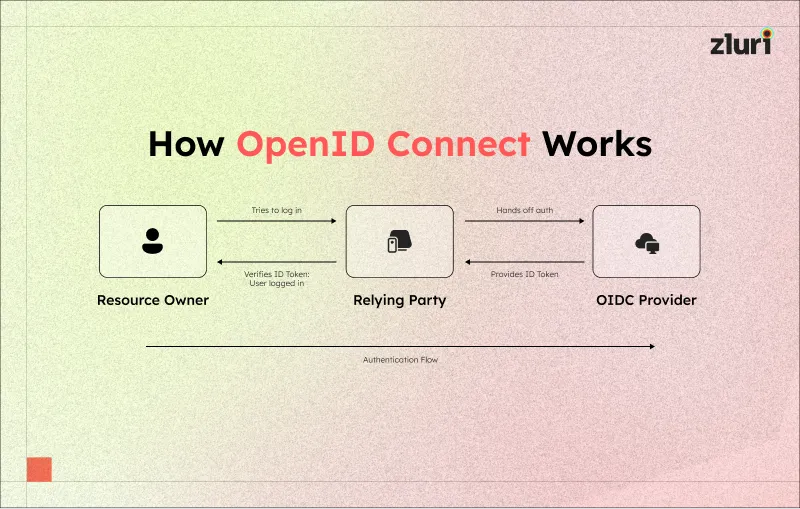
OpenID Connect (OIDC) is an identity authentication protocol built using the OAuth 2.0 authentication framework. Think of OIDC as a bouncer that grants digital identities (end users) access to SaaS apps by asking identity providers (IdPs) such as FusinAuth and Google if they know or recognize the identity (who requested app access). If they do, OIDC lets users access the application, too, without having to share passwords.
But how? Like other authentication protocols, such as Kerberos, OKI, and LDAP, OpenID Connect supports single sign-on (SSO). It allows users to log in with a single set of credentials (name, ID number, or email), eliminating the need to enter passwords whenever they want to access an application.
In addition, to further simplify the authentication and login process, OIDC uses JSON Web Tokens (JWTs). When a user first logs into a website using OIDC, the site generates a unique token (a digital pass for digital identity) containing the user's login information. Further, these tokens are sent to the user's PC's storage so that they don't need to enter their username and password again whenever they return to the site.
Instead of asking users for their login details, the website accesses the token details, verifies their identity, and lets them in. However, note that these access tokens have expiration dates, so the website may sometimes ask users to enter their login details instead of granting direct access.
What Is SAML?
Security Assertion Markup Language (updated version SAML 2.0) is another authentication protocol that supports single sign-on and authenticates users. However, it doesn't use JSON-based tokens but relies on extensible markup language (XML) to exchange authentication data between identity providers and apps (service providers).
XML is a well-known information-formatting standard that encodes data (making it easily understandable by both humans and computers). SAML uses basic SOAP (simple object access protocol) or HTTP (hypertext transfer protocol) requests to exchange XML-encoded data.
Note: In this user authentication process, the service (application or website) that requests the user's identifying information is known as 'service provider' (SP).
Now that you are familiar with OIDC and SAML, let's explore the differences between OIDC vs SAML further.
OIDC vs SAML: Comparison Based On 5 Different Parameters
Below, we have differentiated OIDC vs SAML based on 5 different parameters. By going through these comparison parameters, you will clearly understand how OIDC vs SAML differs.
1: Difference Between OIDC vs SAML Authentication Procedure
Every authentication protocol has a distinct procedure for verifying whether the users (identities) are actually who they claim to be. So, let’s take a look at how the authentication procedure of OIDC vs SAML varies.
- When a user opens an app or website and logs in, OIDC instantly initiates the authentication process. Since the authentication part is delegated to identity providers, the app (relying party) sends the user login details or ID token straight away to the identity provider (which can be Google) to verify the details. Once the details are verified and approved by IdPs, OIDC then grants the user access to the app.
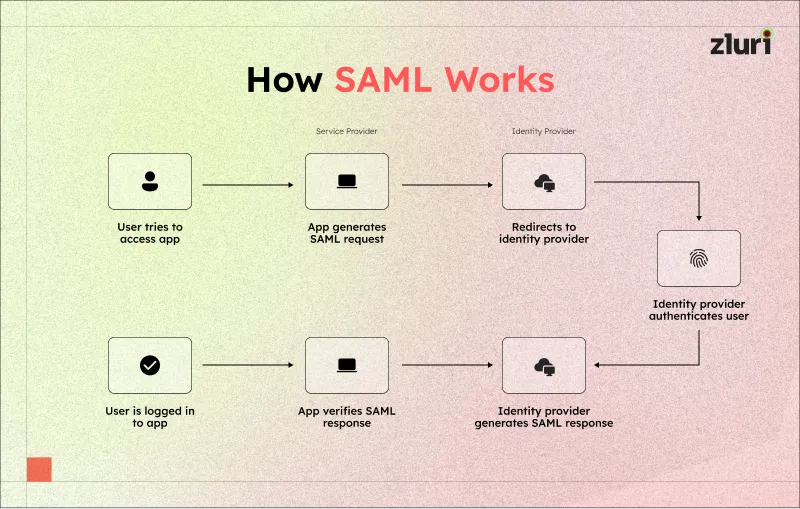
- On the other hand, when a user attempts to log in to access an application (service provider), SAML directly initiates the authentication process. First, the app (service provider) generates a SAML request, which is redirected to the identity provider. The IdP verifies the request and sends an encoded SAML assertion (request-response) back to the app. This assertion is in XML document format that contains permission details and a token that confirms that the user has been authenticated. The app then verifies the assertion and grants the user access to the app.
2: Difference Between OIDC vs SAML User Data Privacy Protection Measures
For most organizations, users' data privacy is one of the top concerns, which is why they constantly look for authentication protocols that implement necessary measures and controls to protect users' data privacy. So, let’s see which authentication protocol (OIDC vs SAML) is better at protecting data privacy.
- OIDC has a built-in data privacy and control feature that allows users to decide how much personal information they want to share with an application (relying provider). This way, they can keep their sensitive data, such as — phone numbers, driving licenses, or any government-issued documents, safe from potential misuse. But rest assured, this capability doesn’t compromise the authentication process at all. In fact, OIDC ensures the app (RP) and IdPs properly use the given details to thoroughly verify user’s identities.
- On the other hand, SAML helps protect user data privacy by allowing them to extract or delete specific data when needed. However, unlike OIDC, SAML doesn't have built-in data privacy and control features by default. But, it is technically possible to set up selective data sharing in a SAML-based system, it just would require additional development work (coding).
3: OIDC vs SAML Integration Support Difference
Not every authentication protocol is built to support smooth integration. However, organizations generally prefer authentication protocols that effortlessly connect with apps (without configuring the settings much). Since integration support is important for most organizations, it's worth examining which authentication protocol (OIDC vs SAML) offers better integration support.
- OIDC offers the flexibility to seamlessly integrate with single-page applications (SPA). In fact, it works well with any security setup without slowing down performance or impacting authentication processes.
- Meanwhile, SAML does not smoothly integrate with single-page applications. Unlike OIDC, SAML requires additional coding and configurations to work with SPAs. Even if you manage to integrate SAML with single-page apps, remember that it might reduce the apps' performance (delay the apps' overall responsiveness) and limit/impact other features. This integration can also hamper and delay the authentication process.
4: Difference Between OIDC vs SAML Security Mechanisms
Both OIDC and SAML have distinct security mechanisms, so let’s see how OIDC vs SAML security practices differ.
- OIDC uses a type of encryption known as OAuth 2.0’s bearer token encryption. This allows end users to authenticate themselves once by using a single set of credentials. Then, they can securely access apps multiple times without logging in repeatedly. However, if this bearer token gets into the wrong hands (unauthorized users), they can immediately access apps and possibly exploit sensitive data.
- On the other hand, SAML focuses on protecting data in transactions (data exchanged between IdPs and SPs). It uses signed assertions and XML signatures to verify and encrypt all the data being exchanged. This ensures that data is protected and doesn’t get tampered with during transit.
5: OIDC vs SAML Use Case Comparison
Lastly, to fully avail the benefits of authentication protocols, you have to ensure they are implemented in an environment specifically designed for them. Now, for that, you need to understand where OIDC vs. SAML can be applicable, so let's quickly find out.
- Since OIDC is a lightweight identity protocol (simple to implement and requires fewer resources to manage) and offers flexible integration support, it is perfect for modern app ecosystems. It is also suitable for organizations that prefer a basic setup for verification to grant users temporary access or short-term logins. In fact, various well-known private organizations like Nomura Research Institute, PayPal, Microsoft, Ping Identity, and Amazon use OIDC.
- Meanwhile, SAML is a heavyweight protocol (complex implementation and resource-intensive). It is well-suited for enterprise-level environments with older, traditional applications requiring a high-level security setup to protect sensitive data. For example, government agencies generally use SAML to verify citizens' IDs and financial institutes (banking sector) to verify customers' details.
Even after going through the OIDC vs SAML comparison, if you are still confused about which is an ideal fit for your organization, consider different factors. To gain more clarity, read on.
OIDC vs SAML: Which One To Choose?
While determining which authentication protocol among OIDC vs SAML is more suitable, consider evaluating factors such as – your organization size & type, budget, and the application type you handle.
For instance, SAML can be a perfect fit if you run a large, established organization with thousands of applications and users or a financial institute. This is because SAML works well with traditional enterprise environments and offers extensive security features to protect sensitive data.
On the other hand, if you are a little tight on budget or have a modern application ecosystem, then you should consider OIDC. This is because OIDC requires less investment compared to SAML, is easier to manage and maintain, and supports seamless integration (which allows it to work easily with modern SaaS apps).
However, you need to decide which of the two would be a perfect fit, so choose the authentication protocol (OIDC vs SAML) that truly meets your specific needs.
Additional Tip: While evaluating factors, you may get lost in the comparison details, so list your needs and create a checklist. Then, compare OIDC vs SAML side by side. At last, whichever authentication protocol ticks off the most boxes can be your choice. You can confidently go for that authentication protocol.
Although authentication protocols (OIDC vs SAML) are great for verifying identities and granting them secure permission (ID token or SAML assertion) to log into an app, these protocols aren't enough to protect your organization's SaaS app data against cyberattacks. What can be done? You can try implementing Zluri's access management solution. It enforces access control policies and regularly monitors users' access permissions to ensure only authorized users can access required SaaS applications and data. In case unauthorized access attempts occur, Zluri immediately notifies IT teams about the same, allowing them to take immediate action to prevent the unauthorized user from compromising crucial data.
Also Read: SASE vs. CASB: Which is the Suitable Security Solution?
Frequently Asked Questions (FAQs)
1. What Is A Relying Provider?
A relying provider, also known as a relying party, is an application or website that relies on identity providers (IdPs) to verify/authenticate user identity (who wants to gain access to that app).
2. What Is SAML Assertion?
A SAML assertion is an XML document that contains details about an identity’s authentication permissions and other relevant data. The identity provider sends it in response to a service provider's SAML authentication request.
3. Can OIDC Replace SAML?
Currently, OIDC cannot replace SAML. SAML has been in the market for over 20 years and has earned the trust of countless organizations. This simply means SAML isn’t going anywhere anytime soon. Meanwhile, OIDC is a relatively newer player. However, it is rapidly gaining popularity due to its modern and flexible design. So, maybe in the near future, it may replace SAML.








.svg)














