Why rely on manual account creation methods when you can automate the process with just in time provisioning? But what is just in time provisioning? In this article, we'll discuss it in detail.
Let me ask you a question — 'Do you really believe manually gathering user details, jotting them down in spreadsheets, updating the data in identity provider systems and applications, and then creating an account is an efficient approach?'
(This is just a basic overview of the manual account creation process; more steps are involved at the backend.)
The answer will probably be – no! Just by looking at the steps, you can estimate how much time and effort your IT admins have to put into creating a single user account. Moreover, despite dedicating hours or even days to these tasks, mistakes still sneak through (entering incorrect user data or accidentally creating accounts for inactive users). Ultimately, it's like investing all that time and effort into a process just to get it wrong!
So, what can be done to avoid all the hassle? The answer is simple—automation! You can leverage SAML just in time provisioning for this purpose. Let's understand it in detail.
What Is Just In Time Provisioning?
Just in time (JIT) provisioning is a process of leveraging security assertion markup language (SAML) protocol to automate the creation of user accounts on-the-fly in web applications.
In simple words, IT admins can avoid pre-setting accounts for each user by simply using SAML JIT provisioning. This SAML protocol-based method enables the auto-creation of user accounts, which means user accounts will automatically be created when a user attempts to log into the application for the first time via a third-party identity provider (IdP).
We've broken down the process step-by-step to provide you with more clarity on how exactly just in time provisioning works.
How Does Just In Time Provisioning Work?
Note: The first and foremost thing you as an IT admin need to do is — set up a single sign-on (SSO) between the application (service provider) and identity provider (IdP). This will help JIT provisioning work smoothly. Along with that, you also have to make sure the chosen service provider supports SAML JIT provisioning — otherwise it will simply won’t work.
Here’s a simple breakdown of how SAML just in provisioning works:
Step 1: Initial Login
When a user attempts to log in to an application using single sign-on (SSO) for the first time (which means their account doesn't exist yet), just in time provisioning gets triggered (you have to do the setting beforehand).
Step 2: SAML Authentication
The application redirects the user's login requests to the identity provider. Then, the IdP authenticates (verifies) the user's entered details.
Step 3: SAML Assertion
Once successfully verified, the IdP sends a SAML assertion back to the application (service provider). This assertion contains the user's key details, such as user identity (e.g., username), user attributes (e.g., user roles and permissions), and other relevant information.
Step 4: Account Creation
After that, the service provider reviews the SAML assertion (authentication token provided by the identity provider) and checks whether the user already has an existing account or not. If in case no account is found (that has used those details), then the application uses the SAML assertion information to automatically create a new account for the user.
Step 5: Account Granted
Lastly, the user is granted access to the application and their newly created account.
In Which Scenarios Can SAML Just In Time Provisioning Be Applied?
See, there's no rulebook or strict guidelines dictating when to apply/use SAML just in time provisioning – so it's entirely up to you, when to implement it and where. Think of it as a tool in your toolkit that you can pull out whenever it's needed.
However, there are certain scenarios where SAML just in time provisioning truly works the best, such as — when organizations frequently hire new employees, organizations have a large SaaS stack (as in 100s of apps present in the stack), or organizations that deal with seasonal workers/freelancers.
Let's say your organization just hired 50 new employees and wants your IT admins to create these new hires' accounts in 100 applications (apps present in the organization's SaaS stack) as quickly as possible so that they can begin working from day one.
Now, if your IT admin starts manually setting up accounts for each one, it will take them days, if not weeks, to complete the task. So, instead of spending endless hours, your IT admins can simply implement SSO and JIT provisioning across all 100 applications. Now, whenever the new hire logs in to an application using SSO, their accounts will automatically be created for that very app — without needing any manual intervention from your admins. It's a huge time-saver!
In short, your IT admins simply need to adjust your application's settings, and the rest of the configured system handles it.
However, JIT provisioning is not restricted to saving time; it also offers a few other benefits. What are these benefits? Let's find out.
Benefits Of Implementing Just In Time Provisioning
Listed below are some of the benefits that you can avail by implementing JIT provisioning:
1: Keeps User Data Consistent Across Systems
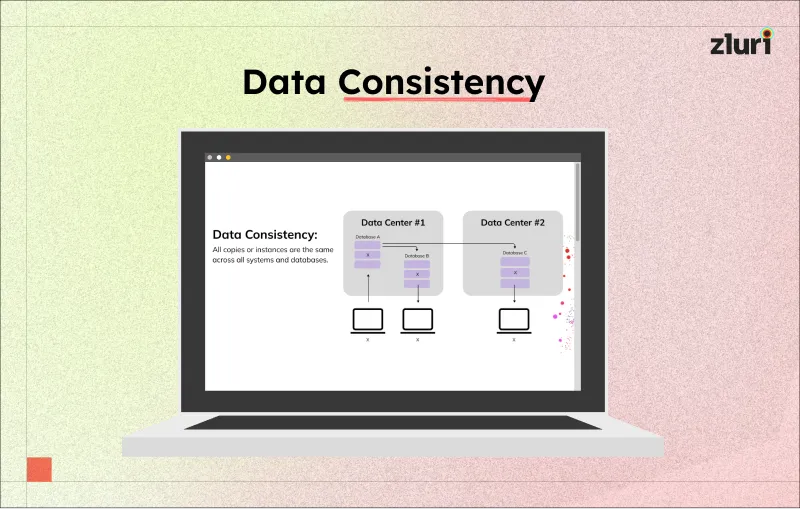
Generally, IT admins manually synchronize (i.e., ensuring that two systems are aligned and updated with the same data simultaneously) user information between the IdP and application (SP).
As a result, they often miss updating user data in one of the systems (this can happen accidentally or intentionally), causing user data inconsistencies across systems. However, just in time provisioning eliminates these data inconsistencies by automatically handling synchronization (it automatically updates the same user data in both IdP and SP simultaneously).
2: Prevents The Creation Of Duplicate And Unnecessary User Accounts

When IT admins manually create user accounts, they accidentally create duplicate accounts for users or inactive users. This usually happens because IT admins often manage multiple account creation simultaneously (at once). To top it off, they also lack visibility into (don't have a clear view) which users' accounts are already created. As a result, unnecessary user accounts accumulate over time, cluttering both the SP and IdP systems.
However, just in time provisioning effectively addresses the issue of duplicate or unnecessary user account creation by automatically checking for existing user accounts before creating new ones. If no existing account is found for the user, it creates a new one (only when needed).
Also, since JIT provisioning is triggered when a user attempts to login into an application, it helps make sure only active user accounts are created. This further helps prevent cluttering the system with accounts of inactive users.
3: Creates A Safety Barrier Between Unauthorized Users And Your Applications
JIT provisioning makes sure that each user is given a unique identity/identification (ID), which they can use to access the application they need. However, the catch is that users can only access an app if they use their assigned ID; if they try to use different or unauthorized credentials, their access will be denied instantly(they won't get the entry).
This control helps ensure that no unauthorized users can access your organization's systems and applications and comprise them. In fact, since it ensures that each user has a single, managed identity across all systems, it also prevents identity sprawl.
Also Read: What Is Identity Sprawl?
Now that you are familiar with the JIT provisioning concept, let's address one important question – 'Is Just in time provisioning the same as SAML provisioning or just in time privilege?'
See, although just in provisioning is a standout concept, many organizations still often confuse it with either SAML provisioning or just in time privilege. Honestly, it's quite understandable — because SCIM provisioning and JIT provisioning both are used for account creation. On the other hand, just in time provisioning and just in time privilege sounds alike.
However, regardless of their shared similarities, they are quite different from one another. Here's how.
Understanding The Difference: JIT Provisioning Vs SCIM Provisioning & Just In Time Privilege
Below we’ve compared just in time provisioning with each key concept one by one for better clarity:
- Just In Time Provisioning vs SCIM Provisioning
SCIM (system for cross-domain identity management) provisioning automates user account creation, updation, and deletion. Meanwhile, JIT provisioning solely focuses on automating the creation of user accounts on-the-fly; it doesn't help with updating and deleting user accounts.
Also, SCIM provisioning relies on REST APIs to automate these tasks, whereas JIT provisioning leverages SAML to automate the creation of user accounts.
Apart from that, SCIM provisioning offers the flexibility to create user accounts at any time (even before users make any login attempts – making it perfect for pre-provisioning). On the other hand, JIT provisioning only gets triggered when a user logs in for the very first time.
- Just In Time Provisioning vs Just In Time Privilege
Just in time privilege (also known as JIT privilege) is an access control that focuses on granting authorized user access to apps for a limited timeframe. Meanwhile, just in time provisioning is a SAML protocol-based method that does a totally different thing – automating the user's account creation.
JIT privilege manages 'who gets in' and for 'how long' (all about controlling access), and JIT provisioning handles 'how the user can access the app' by creating accounts when necessary.
Also Read: What is Just in Time Access? It's Types and Benefits
Leverage SAML Just In Time Provisioning for Creating Your User’s Account
SAML just-in-time provisioning is the go-to solution for organizations determined to eliminate the bottlenecks that slow down user account creation. Automating the account creation process accelerates the account setup and minimizes the risk of data inconsistencies, and significantly eases the burden on IT admins, allowing them to focus on other core tasks.
In fact, it also takes care of the security aspects by ensuring that only authorized users are assigned a unique ID that they can use to access the organization’s applications while keeping unauthorized users locked out completely.
However, as we’ve mentioned earlier, JIT provisioning will only work if the application supports it. So you need to check before implementing JIT provisioning — whether the applications you use support it or not!
In case your application doesn’t support JIT provisioning, and you are short on time to switch to an alternative application that supports it – then you can opt for Zluri. What exactly is Zluri? Zluri is an advanced access management solution that directly integrates with your HRMS to create unique IDs/accounts (with user details like their name, email address, and role) for new users. Here’s how it works: Zluri pulls their details from the HRMS (through integration) when a new user is onboarded and instantly assigns the user a unique ID/account. Later, Zluri evaluates and verifies the user’s ID/account and seamlessly grants them access to resources/relevant applications (suitable for their role). It's even simpler than just in time provisioning; all you need to do is implement Zluri and integrate it with your HRMS, and Zluri takes care of the rest of the work.









.svg)














