As an IT manager, it's crucial to grasp the fundamentals of IT governance. It helps to make informed decisions and drive your IT strategies to success. IT governance ensures your organization's projects, programs, and operations are completed on time, within budget, and meet strategic objectives.
Achieving success depends on the implementation of a well-defined and strategic IT governance plan. It determines your ability to change and add value to your business constantly. If you want to discover how to create more profitable IT strategies, do not miss out on these 8 IT governance best practices.
What is IT Governance?
IT governance is a part of corporate governance—a structured approach to managing the various aspects of IT services. It is the set of processes, policies, and standards that your IT team uses to govern the overall IT operations in an organization.
The main goal of IT governance is to increase efficiency in IT operations, reduce risks, minimize costs, and maintain better regulatory compliance with the changing business requirements.
IT governance is paramount because it helps you strike the right balance between innovation and risk management. Defining roles, responsibilities, and procedures ensures that technology investments deliver value, maintain data security, and align IT projects with business needs.
Why is IT Governance Important?
IT governance is important because it is the backbone of a company's success:
- Better Business Insights: IT governance ensures your company foresees its performance and potential risks.
- Alignment with Organizational Goals: IT governance ensures that technology aligns with and supports the objectives of the business operations.
- Achieve Company Goals: It makes sure that we're getting the most out of our tech resources to achieve our company's objectives.
- Measuring IT Investments: It's a way to assess how effectively we're investing in our IT department and whether these investments are paying off.
- Connecting Tech Management and Development: Think of IT governance as the bridge that connects the folks who manage technology and those who build it.
Role of IT Governance
The role of IT governance is to:
- First, determine the objectives, goals, vision, and mission.
- Ensure that all projects and changes are planned, budgeted for, authorized, scheduled, and monitored.
- Design and implement the IT governance framework.
- Finally, manage risks and liabilities in all IT projects.
In addition, an efficient IT governance structure with their respective roles and responsibilities is important. The below mentioned descriptions provide a clear overview of the organizational structures and the roles and responsibilities within an organization for an effective enterprise governance.
What are IT Governance Frameworks?

Organizations that leverage the IT ecosystem to gain competitive advantage need to develop a model of IT governance for managing their systems and applications. To realize the benefits of IT Governance, it is best to establish an IT governance framework or an IT governance model. A framework can help you implement policies and procedures to maintain the governance program year after year.
Several frameworks have been developed in recent years. Below are some examples of IT Governance Frameworks:
- COBIT (Control Objectives for Information and Related Technology)
- ITIL (Information Technology Infrastructure Library)
- COSO (The Committee of Sponsoring Organizations of the Trade Way Commission)
- CMMI (The capability Maturity Model Integration)
- FAIR (Factor Analysis of Information Risk)
Domains of IT Governance
Below mentioned are the five domains of IT governance that effectively oversee and align your IT activities with the organization's strategic goals while minimizing risks, optimizing resources, monitoring performance, and ensuring compliance and security.
- Strategic Alignment: This domain focuses on ensuring that your IT activities and investments are in sync with your organization's overall goals and objectives. To achieve this, you need to have a clear understanding of the strategy with business strategy and align your IT plans, projects, and resources accordingly.
- Risk Management: This domain involves identifying and evaluating these risks and then putting measures in place to mitigate or manage them. It's crucial for safeguarding your company's information and ensuring that your IT systems are resilient against potential threats.
- Resource Management: This domain involves allocating resources like hardware, software, and personnel effectively. It ensures that you have the right tools and skills in place to support your IT initiatives without overspending.
- Performance Measurement: This domain focuses on tracking and evaluating the performance of your IT systems and processes. You need to define key performance indicators (KPIs) to measure how well your IT system is delivering value to the organization. It helps you identify areas that need improvement and make data-driven decisions.
- Compliance and Security: This domain is all about ensuring that your IT practices and systems meet the necessary compliance standards. It also encompasses protecting sensitive data and ensuring the security of your IT infrastructure to prevent data breaches.
8 IT Governance Best Practices
To oversee the delivery of specific projects, manage change, and ensure that the processes are executed correctly, you need to adopt certain IT governance best practices.
- Make IT infrastructure essential to business strategy
SEMrush, a MarTech SaaS platform, found that 84% of small enterprises use at least one digital platform to share their products. In addition, nearly 79% of them use digital tools in their business, and 55% of small businesses report technology as a means of customer interaction.
The data shows how businesses have become more technology-driven. With everything shifting online, making IT infrastructure essential to business strategy is unavoidable.
IT infrastructure should be prioritized; it will help you maximize your existing resources, strengthen your digital transformation strategy, and reach the organization's objective.
- Put the right team in place
Introducing IT infrastructure to your business strategy is only the first step. Selecting people with the desired skill set and talent is a game-changer.
Putting the right team in place, one of the IT governance best practices, requires proper planning and implementation. You can start by setting up a panel of experts who will be in charge of recruitment.
Additionally, a business can run for decades only when it recreates and innovates with time. Thus, while recruiting IT talent, you must try to choose people who have the ability to innovate. The past projects completed by them should demonstrate their ability.
- Monitor IT performance
Monitoring is one of the IT governance best practices. Selecting a team for IT governance isn't enough. You must have someone to monitor to determine whether things are working well. Someone who can right the wrong and constantly improve the existing strategy.
Naomi Oreskes once said, "Scientific monitoring is going to be terrifically important because whatever steps we take, we will have to monitor those steps to know if they are working."
- Define roles and responsibilities
Because of the importance of the IT ecosystem in an enterprise, there is a growing trend for companies to create governance committees for their IT departments. IT governance committees come in all shapes and sizes.
Still, they have the same purpose at their core: to oversee the IT function and make sure it's operating as efficiently and effectively as possible. So, the challenge with IT governance committees is making them effective.
Without the allotment of roles and responsibilities, it becomes difficult to make decisions, provide oversight, and determine accountability. To accomplish that, IT governance needs to define its role, scope, and processes clearly.
Check the Role of an IT Asset Manager in this post.
By clearly setting expectations for each member of the IT governance committee, you can maintain a productive group that keeps your business moving forward.
- Highlight integrity
Nothing is more frustrating than a lack of clarity on priorities. It is one of the IT governance best practices and vital to make each member responsible for oversight and management of the policies and procedures.
The best way is with a compelling vision statement, which defines your program's highest priority concepts and values. Also, include a mission statement that clearly states how you will achieve those goals.
And have a set of objectives, so people know how they fit into the larger picture. Finally, make members responsible for oversight and management of policies.
- Don't forget about compliance
Data is a company's most precious resource. As companies collect and handle more data, it is more important than ever to monitor security measures carefully and ensure that their data remains safe. Most of the security breaches occur due to poor security policies. Thus, it is crucial to review your security policies and follow compliance standards.

Effective IT governance helps your organization implement security policies and ensure every member follows all the security compliances. These compliances include developing security policies and security audits. Future business decisions might impact organizations' liabilities.
- Prioritize effective risk management
It is not just about knowing and tackling the threats; and it is also about identifying and managing the risks. To do so, you need to know what those risks are in the first place. Then, you can start your risk assessment and mitigation process.
The IT governance team must regularly identify and assess reputational, operational, financial, regulatory, and legal risks. It has to consider the company's size, processes, and technologies.
The IT governance team can mitigate risks by designing compliance, evolving processes to make compliance an integral part, and co-experiment which works best for your company.
- Make employees' education a priority
The ultimate risk to any organization is not losing data due to a hardware failure or accidentally erasing something important. The top threat is security breaches due to human error.
Employees can be taught how to prevent phishing attacks and stop them from happening. Without proper education, employees might feel like an easy target for hackers. And that feeling can lead to a decrease in employees' morale and productivity.
The best way to do this is by providing comprehensive training on recognizing phishing scams. This IT Governance best practice emphasizes accentuating education, providing training to handle sensitive data, and using devices carefully while working.
By following these IT governance best practices, you can ensure that your IT operations are efficient, secure, and aligned with your business goals. However, manually doing these can be cumbersome for your IT team. This is where identity governance and administration tools, like Zluri, come into play. Let's see how.
Leverage Zluri to Get Started With IT Governance
Zluri offers a robust identity governance and administration (IGA) platform designed to empower you in securing and managing access to your complete SaaS ecosystem across every phase of a user's journey.
Zluri's IGA platform offers the means to effortlessly maintain authority and bolster security using various features, including automated user provisioning, access assessments, and self-service access requests.
With Zluri's IGA platform, you can guarantee that each user's access privileges are diligently administered, fully aligning with your organization's established policies. This not only fortifies your security measures but also ensures compliance with the necessary regulatory standards.
Let's explore how Zluri stands out from other IGA tools by offering unique capabilities.
- Powerful Discovery Engine
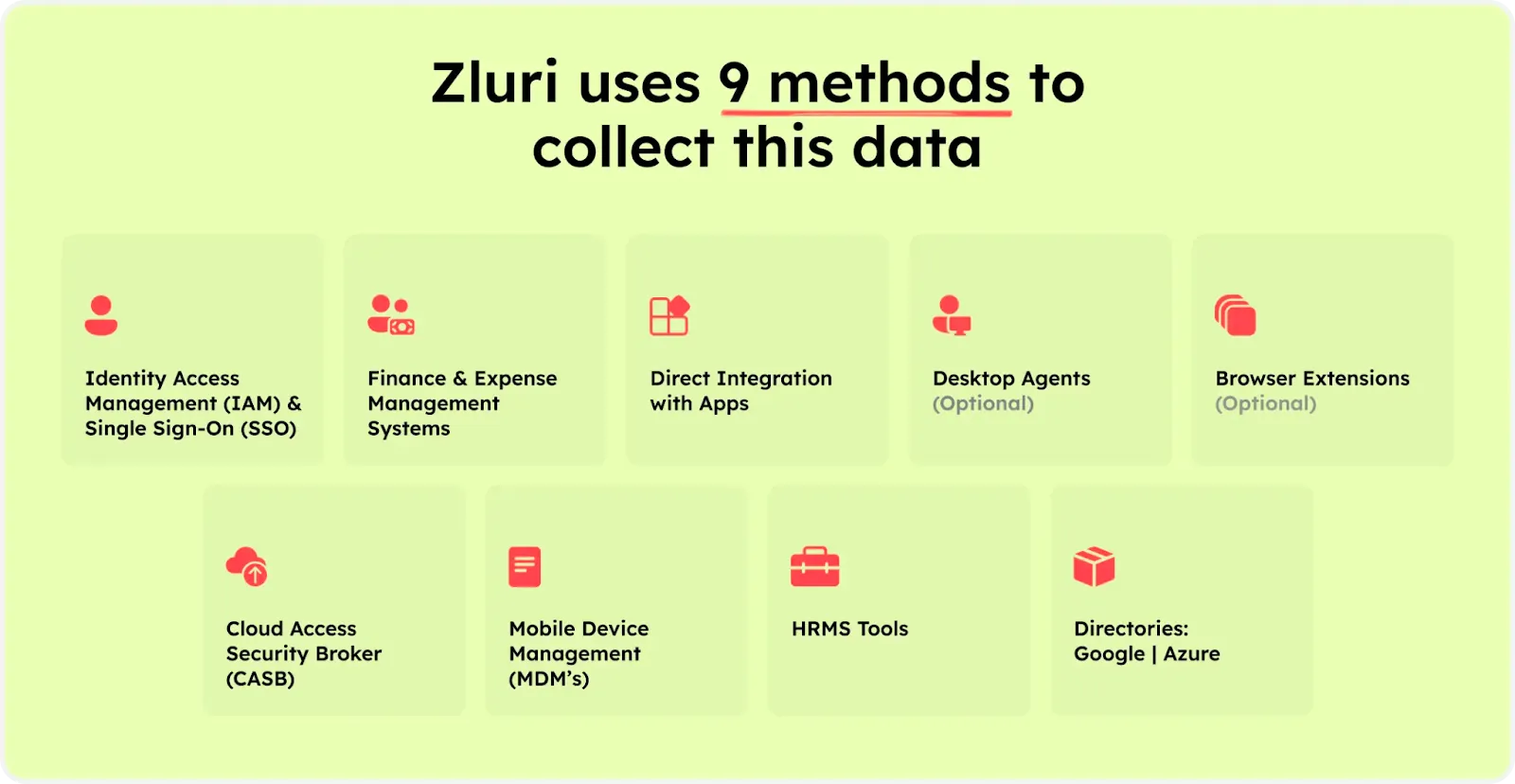
Zluri simplifies the task of extracting valuable insights from your SaaS applications and user data for your IT team We offer 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
However, Zluri's capabilities extend far beyond mere discovery. The IGA platform takes it further by seamlessly integrating with over 300 SaaS applications, ensuring you can access real-time data, actionable insights, and AI-driven alerts to keep you well-informed.
Thanks to API-based integrations, Zluri guarantees an exhaustive data discovery process across all your SaaS applications, leaving no information concealed. You can rely on Zluri to provide 100% visibility into your SaaS environment.
What's even more impressive is Zluri's extensive library, boasting an impressive collection of over 225,000 apps. Our platform excels in offering comprehensive access data, delving into granular details. This equips you with a thorough understanding of user permissions and access levels within your SaaS ecosystem.
- Robust Automation Engine
Zluri's automation engine is like a self-driving system for your organization. It takes care of access workflows effortlessly, ensures smooth and efficient automation with thorough reviews, and follows a clear set of rules and policies.
Now, let’s explore Zluri’s IGA capabilities
Lifecycle Management
Zluri's user lifecycle management (ULM) solution is your gateway to efficient user access management without compromising on security. Zluri's ULM platform simplifies the onboarding of new employees, granting them swift access to essential applications and resources with ease.
With streamlined processes and seamless integration with HR systems, Zluri empowers your IT teams to efficiently establish user accounts across multiple applications, all from a centralized hub. This not only eliminates errors but also alleviates administrative burdens, ensuring that new employees enjoy the right access from their very first day.
Moreover, when employees depart from your organization, our platform seamlessly executes automated deprovisioning workflows, enabling your IT teams to revoke user access across all applications. This proactive approach minimizes the risk of abandoned accounts and potential security breaches.
Furthermore, Zluri offers distinctive features that set it apart from the competition, ensuring an effective access management strategy:
- Customizable Workflows: Zluri allows you to create predefined workflows tailored to your organization's unique requirements, eliminating the need for manual access permissions. The intuitive interface enables you to customize workflows based on user roles, departments, and seniority levels.
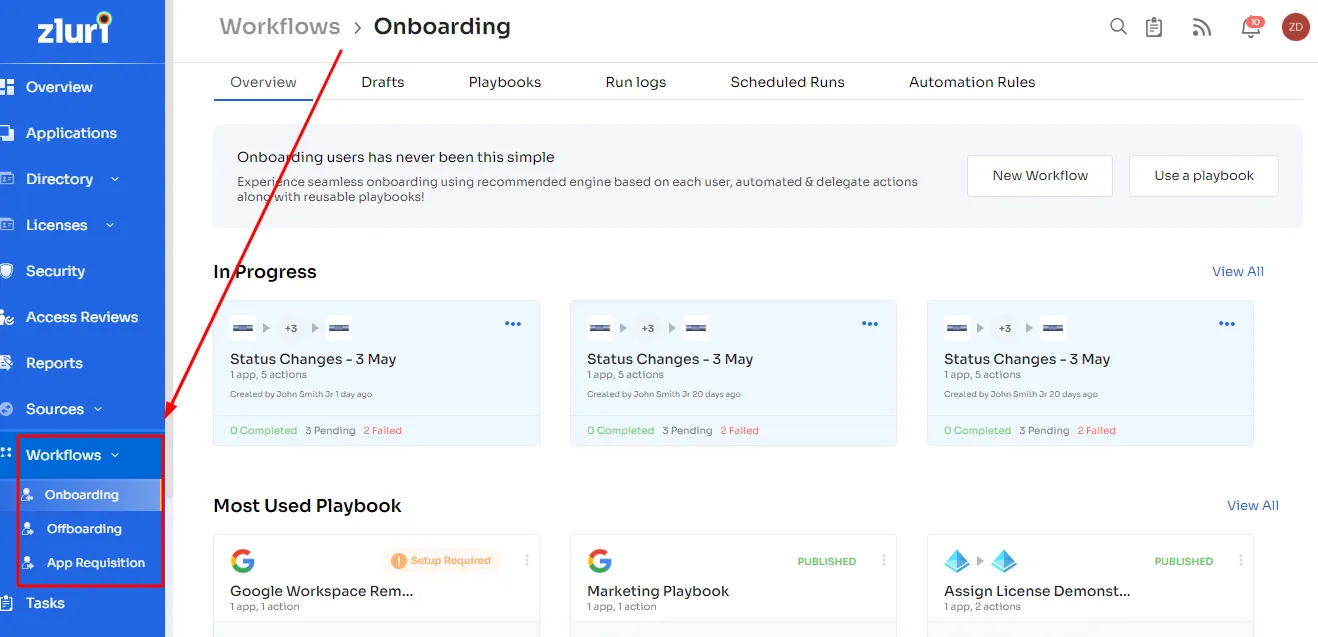
- Onboarding
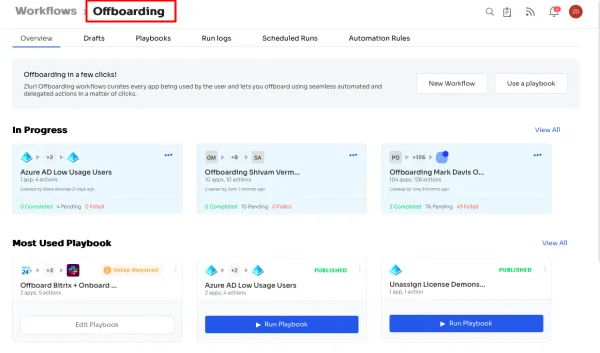
- Offboarding
- Powerful App Recommendations & In-App Suggestions: Zluri provides context-based app recommendations based on user profiles, department, and seniority levels, simplifying the process of app provisioning for your team.

- Additionally, it offers in-app suggestions to enhance user productivity by guiding them on efficient task performance.
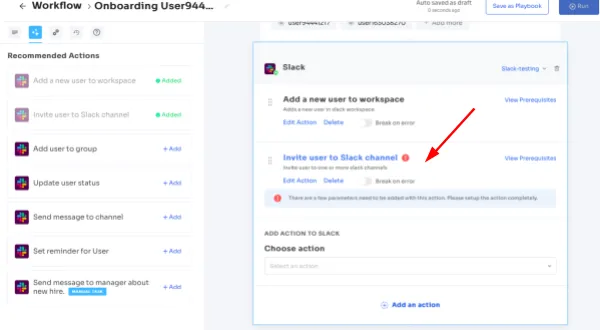
- Automation Playbooks: By saving predefined "playbooks" for both onboarding and offboarding workflows, Zluri streamlines the process and increases operational efficiency, eliminating the need to recreate workflows for each user.
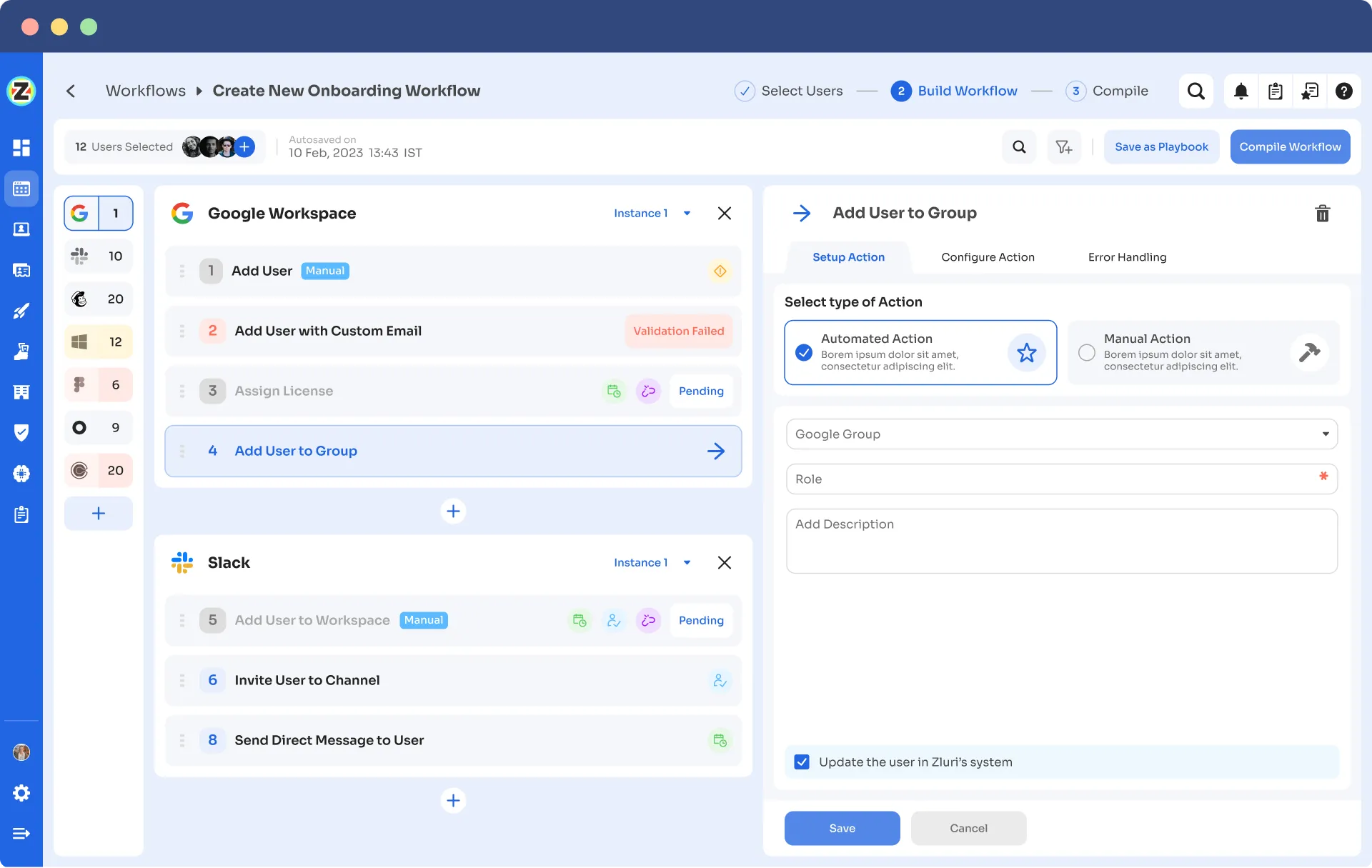
Onboarding Playbooks
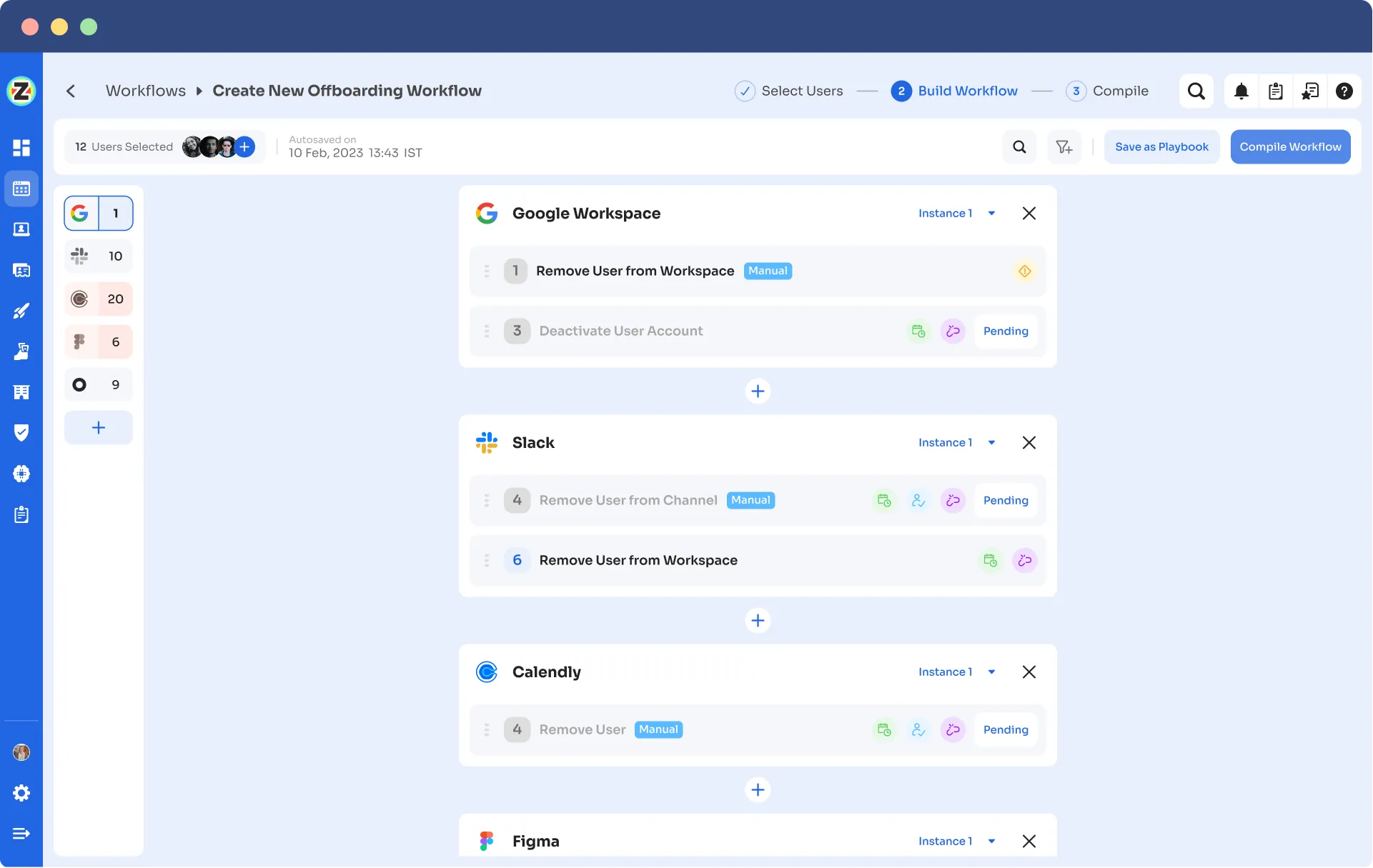
Offboarding Playbooks
Note: These playbooks help your team to ensure security and compliance while provisioning and deprovisioning users’ access even in the future.
But what happens when a user’s role changes during the mid-lifecycle transitions?
Ad-hoc access request management
Zluri streamlines the intricate task of managing user access during role transitions through its intuitive Enterprise App Store (EAS), a self-service platform. This robust feature empowers your IT team, ensuring a seamless approach to overseeing employee access to critical tools and applications.

With the EAS, your team or designated approver can efficiently review and authorize access requests, taking into account the unique job roles and responsibilities of your employees. This meticulous process guarantees that permissions granted align perfectly with their specific needs, thereby giving you the ability to govern access and safeguard sensitive information within your organization.
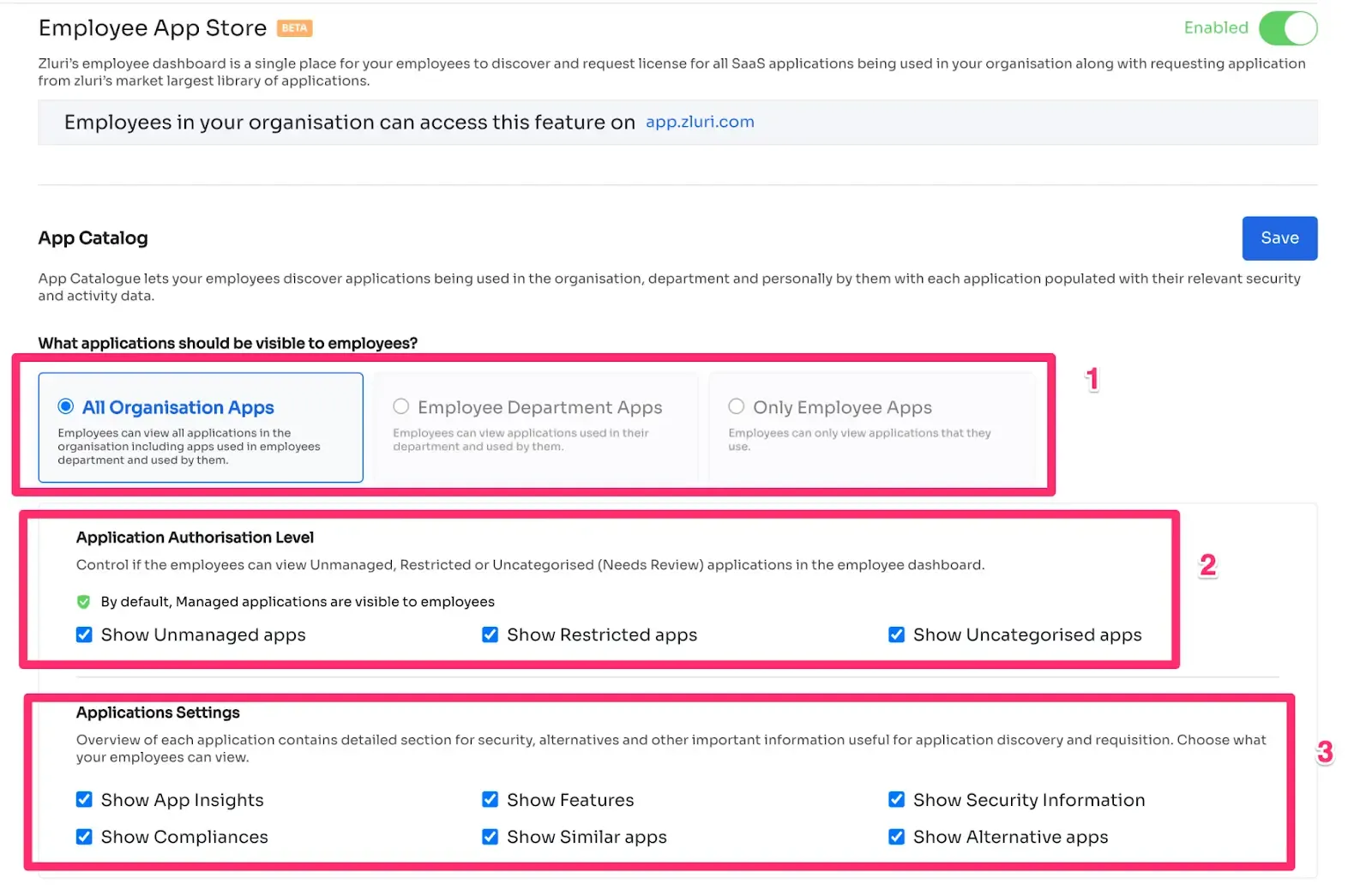
Zluri's transparent approval system is structured into three distinct levels: app owners, reporting managers, and IT admin. This hierarchical approach empowers higher-level authorities with decision-making authority, enabling them to override any decisions made by lower-level administrators or managers.
In situations where an access request faces rejection, decision-makers have the ability to provide insightful comments explaining the rationale behind the decision. This commitment to transparency and clarity ensures a harmonious access request process. Approvers also possess the flexibility to make adjustments to specific requests as needed.
To keep users well-informed and in the loop, Zluri offers a "changelog" feature. This feature allows users to effortlessly monitor updates related to their access requests, offering critical insights into the approval or rejection of requests, any changes in license duration or tier, and comments added by administrators. This functionality ensures users remain up-to-date and informed about any developments or decisions concerning their access to applications.
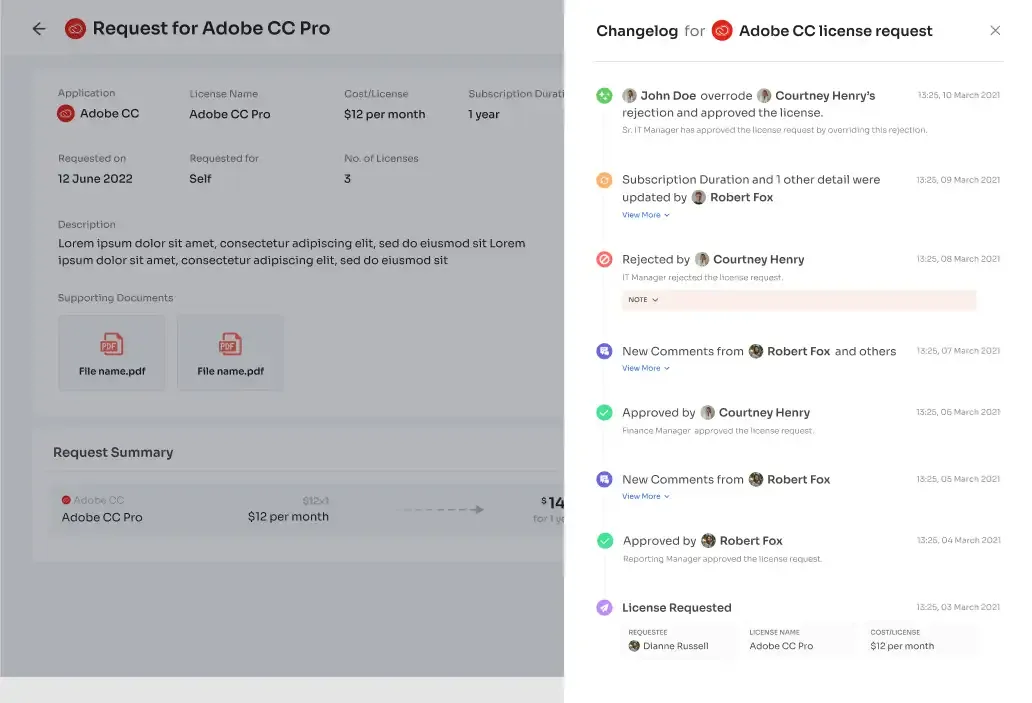
Now, let's say an employee in the marketing department requests access to a marketing analytics tool. The employee’s manager reviews the request and approves it, as it aligns with the employee’s job responsibilities. However, when the request reaches the IT admin, they notice that the access requested included certain advanced features that were unnecessary for his role, potentially posing a security risk.
In this case, the IT admin can modify the request to limit the employee's access to only the essential features, maintaining both security and cost-efficiency. They can leave comments explaining the change and the reasons behind it. This not only ensures that the employee gets the access required but also that the organization's IT governance policies are adhered to, ultimately safeguarding sensitive data.
- Access certification
Zluri makes managing who has access to your company's data and systems a breeze. It offers a user access review solution for your IT team and auditors to check and control user access.
With Zluri, you can easily set rules for who gets access to what, choose who reviews it, and even plan when to review it.
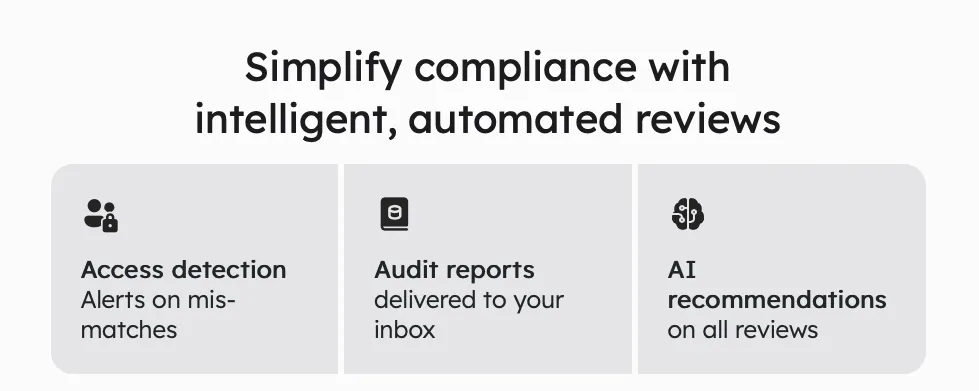
Zluri is super smart and can automatically check if people have the right access, saving time and preventing mistakes that can happen when doing this manually with spreadsheets.
But wait, there's more! Zluri can also auto-remediate access issues if it finds any problems. This keeps your company safe and following the rules. It can revoke access for people who shouldn't have it, which means less chance of security problems or data leaks.
Zluri also creates reports that help you see what's happening with access. It can show you patterns, issues, and if you're following the rules. This is very useful for audits and making sure people only have the access they need.
What makes Zluri special in IT governance?
- Continuous Access Reviews: Zluri can regularly check access rights to make sure they're correct. This helps you find and fix problems quickly.
- Real-Time Access Reviews: Zluri uses super smart technology to watch access in real-time. It can spot unusual or risky actions and stop them to keep your data safe.
- Compliance Made Easy: Zluri makes sure you're following the rules by using smart technology to keep everything in line with industry standards and regulatory requirements.
FAQs
What are IT governance practices?
IT Governance, often abbreviated as ITG, plays a pivotal role in the strategic management of your organization's technology resources. It involves the careful orchestration of critical IT decisions to enhance overall IT management, guarantee regulatory adherence, and optimize the return on investment from your technology assets.
What are the 3 pillars of IT governance?
Effective IT governance is anchored on three core pillars: reporting, compliance, and security. Reporting empowers IT governance to quantifiably assess and convey the value of IT to the organization and its key stakeholders. Compliance, on the other hand, equips IT governance with the capabilities to seamlessly fulfill the legal and regulatory obligations that pertain to IT operations.
What are the elements of Enterprise Governance?
The foundation of enterprise governance comprises four vital elements: individuals, procedures, outcomes, and objectives.









.svg)














