
What Is Identity Sprawl: The Ultimate Guide
The increasing adoption of SaaS has led to a surge in the number of user accounts, resulting in a phenomenon known as "identity sprawl." This occurs when users create multiple separate and incompatible accounts to access different apps or online platforms. Due to this, users' identities become spread out and scattered. Further causing potential security risks and management challenges for organizations.
In this article we’ll discuss the what is identity sprawl and what can be done to mitigate them
Before we further understand how identity sprawl has become a concerning challenge for organizations, let's first learn in detail what actual identity sprawl means.
What Is Identity Sprawl?
Identity sprawl is a situation where a user's identity is managed by multiple siloed systems or directories that lack synchronization with each other, resulting in multiple identities for the same user. This issue often arises when an application or system cannot integrate with the organization's central directory service, resulting in the need to manage an additional set of user identities to support access to that specific application or system.
Furthermore, identity sprawl has been an issue for organizations adopting cloud services, as cloud services typically operate with distinct identity silos, requiring users to maintain separate identities for each cloud service they use.
For instance, users frequently use different online services such as social media platforms, shopping websites, and productivity tools. Over time, these users may create separate accounts with different usernames and passwords for each service, resulting in identity sprawl. Such as, the user might have one account for their social media platform and another for their e-commerce website.
As the user's online activity expands, managing this increasing number of accounts becomes tedious. The user is likely to use similar or identical passwords across multiple accounts for ease of memory, unknowingly putting their security at risk. If one of these accounts gets compromised, due to a data breach or other security breach, it could lead to a domino effect, jeopardizing the security of other accounts that share the same credentials.
Why Is Identity Sprawl A Challenge?
As more employees work remotely and use different online services like Skype, Dropbox, Zoom, Slack, and Salesforce, IT teams have noticed that employees have created multiple usernames and passwords. This caused a problem for IT teams because they had many different user identities and separate systems to manage. Further, connecting all these systems together became a challenge, and there was no central place to keep accurate user profiles and permissions.
The situation becomes more complicated with cloud-based apps and services used for remote work. These applications often required separate user identities and had their own systems for managing identities. This mishmash of management systems led to slow user provisioning, ghost accounts, inconsistencies in user privileges, and difficulties in enforcing security and compliance policies.
Users managing multiple accounts also experienced password fatigue, leading them to reuse the same passwords for different applications and services, compromising security.
A unified identity management approach can be adopted to mitigate such risks and improve user experience. By consolidating identity across different services, the user can access various platforms with a single set of credentials, streamlining the login process and reducing the number of accounts to manage.
This enhances the user's experience and security by minimizing the chances of password fatigue and credential-stuffing attacks, which can lead to unauthorized access and potential data breaches.
Now, let's explore the practices that can help your IT team effectively mitigate identity sprawl and its associated challenges.
4 Best Practises To Mitigate Identity Sprawl
Given below are the effective strategies that can help your IT team to overcome the challenges posed by identity sprawl.
1. Replace the Outdated Identity Management System With A Modern IGA Solution
Depending on manual methods to manage user identities and access hampers efficiency and increases the likelihood of human errors creeping in. Not only that, it even becomes difficult for the IT teams to gain complete visibility into users' accounts, as there are multiple user accounts within the organization. Also, manually tracing how many accounts each user has, which applications they have access to, and more can be a tedious and time-consuming task for IT teams.
However, this concern can be addressed by replacing manual methods and inefficient identity management systems with modern IGA solutions.
With the help of advanced IGA solutions, your IT teams can gain complete visibility into users and access data. Further, they can easily monitor the number of users, their associated accounts, the applications they have access to, the specific permissions granted to each user, and more, all from a single platform. By gaining granular visibility, your teams can eliminate identity sprawl and can thoroughly govern user access rights.
Thus, transitioning to modern IGA solutions streamlines identity management processes, reduces errors, and strengthens the organization's overall security posture.
2. Implement Privilege Access Management
Your IT team needs to ensure that users can access only the apps and data necessary for their roles while restricting unnecessary access. But how are the IT teams supposed to do that?
Well, with the help of a modern and automated IGA solution, your IT teams can enforce least privilege access policies. By enforcing these policies, employees will have access limited to what is essential for their responsibilities. As a result, your IT team can reduce over-provisioning of privileges and mitigate potential security breaches, such as unauthorized access. This further helps in ensuring a more secure environment for your organization.
3. Embracing Identity Orchestration For Seamless Enterprise Identity Systems Integration
Another option is to implement identity orchestration, which adds an abstraction layer enabling applications to seamlessly integrate with different identity systems in the enterprise without requiring changes to the application code.
Through identity orchestration, identities, and policies are replicated across various identity systems by fetching identity data from multiple stores and directing login requests to the appropriate identity provider.
Identity orchestration aims to unify incompatible identity systems' APIs, data models, and access policies into a consistent identity fabric. Although implementing orchestration demands time and resources, it significantly reduces IT team burdens and streamlines the enforcement of consistent access and privilege policies throughout an organization's IT ecosystem.
4. Create A Single Source Of Truth By Centralizing The Identities Of All Users, Devices & Apps
The most effective and lasting solution to address identity sprawl is to create a single source of truth by centralizing the identities of all users, apps, and devices. Your IT teams need to create profiles for each identity, cross-referencing and verifying attributes and privileges across every identity data source while ensuring they align with their designated roles. However, this presents a significant challenge due to the varied formats and schemas of the data.
An even more daunting obstacle lies in replicating or synchronizing this centralized image with each identity silo, as each system may operate independently and have its own unique characteristics.
But with an effective IGA solution, your team can address these challenges and create a secure IT environment by providing a single source of truth to effectively manage user identity and access.
Now that you know what benefits you can avail by implementing an IGA solution let's see which modern IGA solution is worth considering for your organization. Although various options are available in the market; one solution that stands out is Zluri. Zluri is a modern autonomous and automated IGA platform that allows your IT team to streamline the identity and access management process and eliminate identity sprawl. How does it do that? Here's a quick read-through.
Zluri: A Modern, Autonomous & Automated IGA Solution To Control, Manage, & Govern User’s Access
Are your IT teams struggling with effectively managing user identity and access, and battling identity sprawl? If so, your search comes to an end here with Zluri. Zluri is your ultimate modern IGA solution that enables your IT team to seamlessly control, manage, and govern users’ identity and access. With Zluri, they can easily trace how many accounts the users have (active and inactive), what all access permissions they have, which apps they can access, and more.
How does Zluri make it all possible? It offers advanced functionalities, including a data discovery engine, automation engine, access certification, and other features. These features are designed to help your IT team ensure the right users have access to the right app, systems, and data with the right permission level when needed.
This further helps in reducing/eliminating identity sprawl, other potential security breaches and maintaining a secure access environment.
To help you understand better, we’ll discuss each feature in detail. By doing so, you will know how Zluri works and why it serves as the ultimate solution for identity and access management related challenges.
Unveil All The User’s Identity And Access Data Existing Within Your Organization With Zluri’s Data Discovery Engine
When IT teams rely on outdated manual methods or inefficient solutions, it often hinders their ability to gain complete visibility into the user access context. Due to a lack of visibility, the IT team gathers inaccurate insights/data for access reviews, further impacting the entire access review process.
However, Zluri comes to the rescue with its data discovery engine feature, enabling your IT teams to gain complete visibility into user accounts, access, and SaaS app data across the organization.
Wondering how it works? Zluri's data engine employs five discovery methods: SSO or IDP, finance systems, direct integrations, browser extensions (optional), and desktop agents (optional).

Zluri’s nine discovery methods
These methods enable IT teams to obtain in-depth insights into user access contexts. They can easily track which users have how many accounts, which specific apps and data they can access, their department and position, the level of access permissions (e.g., read, edit, or delete) they are holding, and more.
Armed with such detailed insights, your IT team can efficiently keep track of the entire identity and access management process, ensuring a well-controlled and secure environment.
Effectively Manage User’s Account And Their Access From The Time Of Onboarding To Offboarding With Zluri’s Automation Engine
Manually managing user accounts and their access throughout their lifecycle is susceptible to errors, resulting in a higher likelihood of mismanagement of access and account. Moreover, this approach burdens the IT team as they have to manually manage each and every process from gathering data to verifying user accounts and granting access to suspending accounts upon departure.
Also, it negatively impacts employee experience and productivity. Apart from that, relying on manual methods for user access management can further pose data security risks.
So, let’s explore how with Zluri’s automation engine, your IT team can automate and manage the repetitive access management process throughout different phases of the user's lifecycle.
Granting New Verified Employees Account Access To SaaS App Data Upon Onboarding
By managing the account creation process of the new employees manually during onboarding, there is a potential risk of creating duplicate user accounts and further granting employees access to unnecessary applications. Moreover, relying on the manual method means onboarding one employee at a time by verifying their identity and creating their account. This can be time-consuming and negatively impact the overall experience of new joiners.
So what Zluri does is; it automates the entire provisioning process, from creating individual accounts for each employee and granting multiple new employees access with just a few clicks. By automating the process, your team can ensure the right access is granted to the right employees with the right level of permissions to necessary apps. That further boosts employees' productivity by enabling them to start working from day one.
Also, it makes it more convenient for the IT team by tying user profiles with their digital identity during onboarding. So that when your IT team verifies user identity to grant them access during the provisioning process, they can simply cross-check the details from a centralized dashboard. Thus, this integration allows your IT teams to assign user access that aligns with their job role accurately.
Now let's move on and see how Zluri automates the provisioning process. Well, your IT team can create onboarding workflows. All they need to do is select users they want to grant access to or onboard and apps (you can even choose from recommended apps option), which all apps they want the users to access.
Then, your team can take necessary actions easily by clicking "add an action." Here, they can schedule the workflow and more.
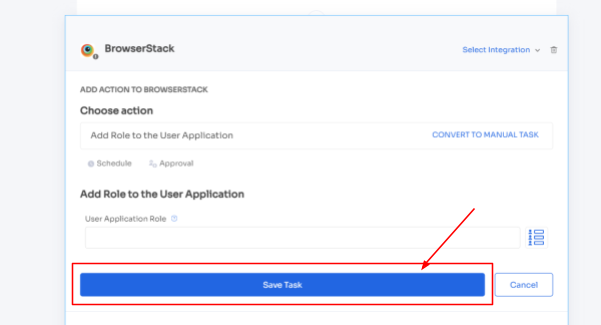
Zluri even provides in-app suggestions, allowing your team to add employees to different channels, groups, or projects or send automated welcome messages.
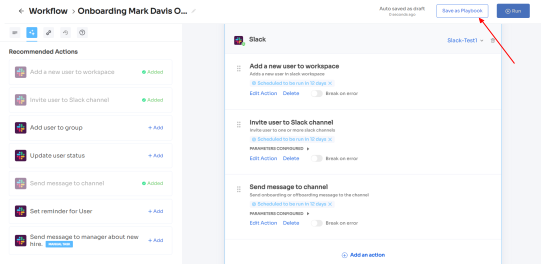
The actions can vary for different applications and are mentioned under recommended actions. Once all the actions are set, you can directly run the workflow or save it as a playbook for future use.
For added efficiency, Zluri offers automated playbooks (i.e., collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.

Note- Apart from that, your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the finance department employees.
Speed Up The Access Request Management Process With Zluri’s EAS
As employees' roles, departments, or positions change, their access requirements evolve accordingly. Additionally, they may need access to new applications for specific projects in certain situations. However, managing these access changes manually poses challenges for the IT team, as they often encounter difficulties identifying all the necessary modifications.
The drawbacks of manual access request management don't end there; the entire process involves multiple steps, resulting in extended waiting periods for employees to receive final approval, disrupting their workflow significantly.
So what Zluri does is it eliminates the time-consuming manual access request process through automation. Let's see what it does.
To stay updated with the changes, Zluri integrates with HRMS. With the help of this integration, Zluri automatically retrieves and displays updated employee data on a centralized dashboard. By leveraging this integration, your IT team can easily access and verify employee details without manual effort.
This streamlined process ensures access permissions align with current employee roles and responsibilities. Whether granting or revoking access, your team can efficiently manage user privileges based on the most up-to-date information available.

It doesn't stop there; Zluri takes a step further to streamline the access request process by making it ticketless. It offers an Employee App Store (EAS), a self-serve model, a collection of applications pre-approved by your IT team. With this self-serve model, employees enjoy the flexibility of choosing any application from the app store and gaining quick access in no time.

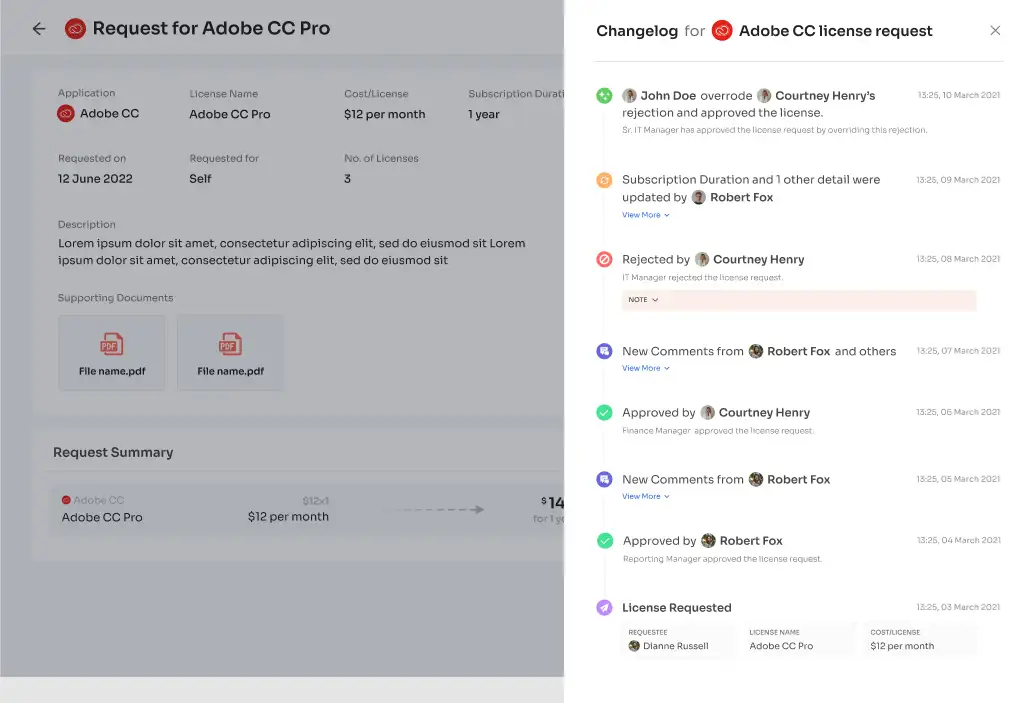
All they need to do is raise a request, and the IT team will verify and review their identity before providing access to the requested application. If approved, employees gain access right away. If access is declined, they receive prompt notifications along with reasons for the decision, any modifications made, or suggested alternatives for the application, all viewable in the "Changelogs."
Apart from that, to make it more convenient for employees to access apps and add more security layers, Zluri utilizes authentication methods, including multi-factor authentication (MFA), in which users have to verify their identity in multiple ways.
Like along with passwords, users might be asked to enter a code sent to their email, scan a fingerprint, or answer a secret question. Adding an extra layer of security helps ensure a higher level of protection.
Also, Zluri offers single sign-on (SSO), enabling users to access different applications with a single set of credentials. By reducing password fatigue, this feature enhances user experience and reduces the risk of security breaches and chances of unauthorized access.
Securely Suspend Accounts & Revoke Access From Departing Employees
Suspending accounts and revoking access from departing employees or those who no longer require certain application access is a critical task for IT teams. Even a single oversight in this process can lead to security breaches, and compromise data security.
Zluri recognizes this concern and provides a solution by automating the deprovisioning process. With just a few clicks, your IT team can effortlessly suspend accounts and revoke the required or all access from employees without missing any crucial steps. This automation ensures timely and thorough revocation and suspension, safeguarding SaaS app data from potential security breaches such as unauthorized attempts.
Furthermore, to automate the process, your team can simply create an offboarding workflow. All they need to do is select the users from whom they want to revoke app access, and then they will come across a list of recommended actions (such as signing out users, removing them from org units, and more).
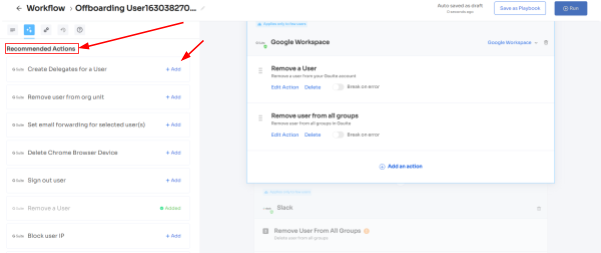
Your team can choose one or multiple actions at once from the list; a point to note is that these actions will be executed post the deprovisioning process. Once all desired actions are added, your team can run the workflow instantly or save it as a playbook for future use.
Seamless Govern User Accounts & Access With Zluri’s Access Certification
Conducting access reviews for user accounts manually using spreadsheets and JSONs can be inefficient and consume valuable time and effort, leading to inaccuracies in reports.
Zluri streamlines the access review process to address these challenges through its access reviewing capabilities. With Zluri's unified access review feature, your IT team can easily identify which users have how many active/inactive accounts, access to which all SaaS apps and data, and more. This valuable insight is gathered from Zluri's access directory, where all user access-related data is stored in one centralized location.
Furthermore, with the help of these insights, including user roles, department, and more, your IT team can thoroughly examine user access privileges, ensuring employees' access permissions aligns with their respective roles.
Also, Zluri's activity and alerts feature ensures smooth operations by providing real-time updates on users account’s recent access activities and notifying IT teams about new logins. This valuable information enables reviewers to make informed decisions promptly during access reviews, ensuring that the right individuals maintain appropriate access levels at all times.
Furthermore, Zluri offers the convenience of automating the entire access review process. Simply go to Zluri's IGA interface, create a certification, select the apps and users for review, and rest the reviewers will review and update you about the compilation via email. This automation yields 10 times better outcomes, saving the IT team's efforts by 70% compared to manual methods.
Once you have acquired contextual data through Zluri's unified access feature, you can then create access rules based on these valuable insights. For instance, you can establish a review policy tailored specifically to scenarios where a user account holds admin privileges on BambooHR.
Next comes the schedule certification feature, enabling you to create certifications based on the gathered information. This empowers you to take appropriate actions based on the insights obtained. For example, you can use data like last login, departments, user status (active or inactive), and more to make informed decisions during the review process, determining whether users can retain existing access or require modifications.
Additionally, after successfully creating access certification, if any user activity deviates from the set access policies, Zluri initiates auto-remediation actions, such as it runs a deprovisioning playbook to revoke access if users' access does not meet the access criteria or modifying access with the reviewer's intervention.
Note: For critical data, Zluri enables manual review and remediation of access to ensure extra scrutiny and control.
With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. It's a smarter, more efficient way to ensure the right access for the right users, all while keeping your data secure. Zluri's automated access reviews and access rules are the key to simplifying your access governance process.
Here’s how to create access certification in Zluri:
Step 1: From Zluri’s main interface, click on the ‘Access Certification’ module.
Step 2: Now select the option ‘create new certification.’ You have to assign a certification name and designate a responsive owner to oversee the review.
Step 3: Under Set Up Certification, choose the ‘Application’ option. Proceed further by selecting the desired application for which you want to conduct the review and choose a reviewer (generally the primary reviewers are the app owners) accountable for reviewing access to that particular application.
After that, you need to select the fallback owner/reviewer, if the primary reviewer is unavailable, the fallback owner can review the user access (you can select anyone for the fallback reviewer, whom you think is responsible enough). Also, the reviewers will get notified through the mail that they will conduct a review.
Once you are done selecting the reviewers, you can click on Next.
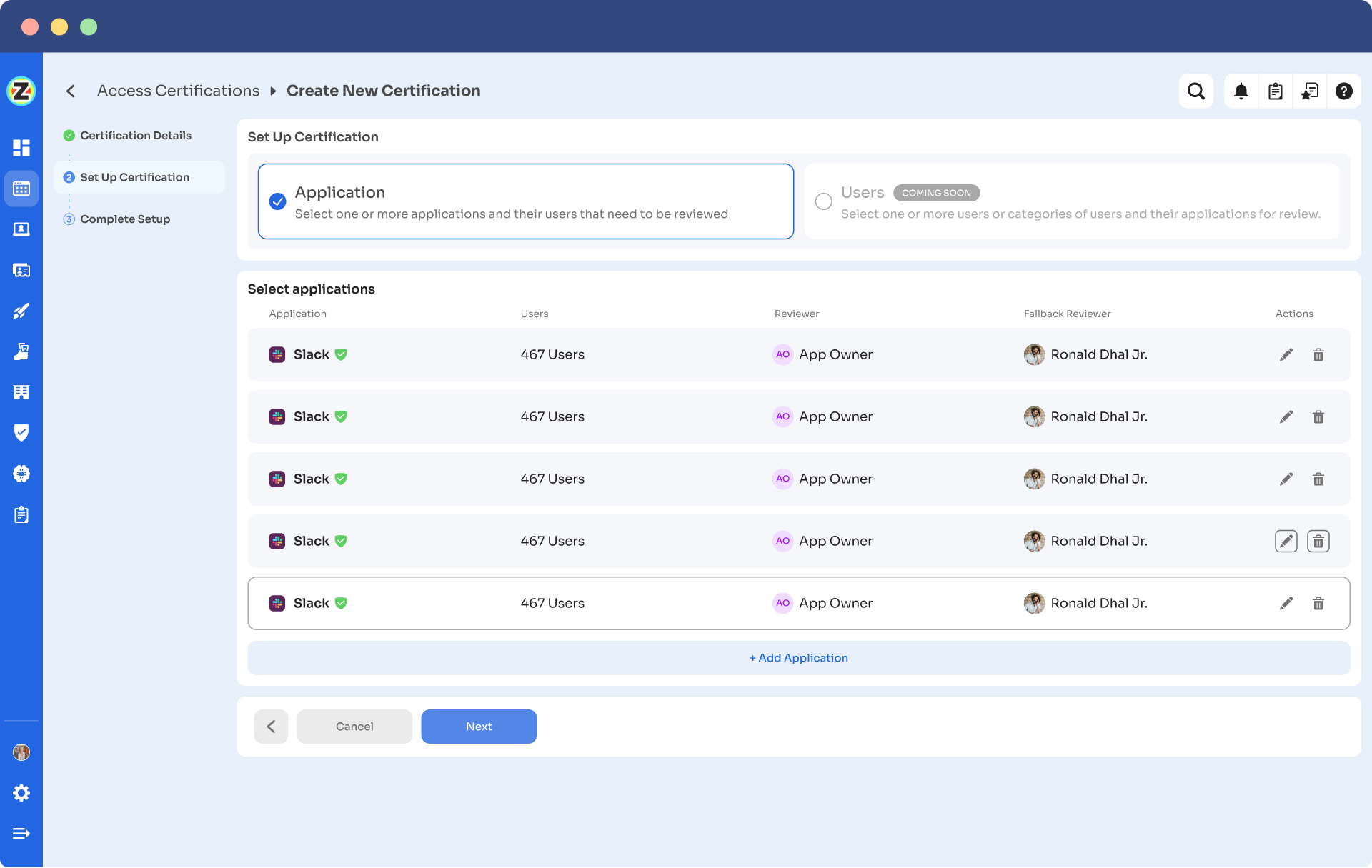
Step 4: Select Users for Review, choose the users whom you want to review for the selected application. Once you are done selecting the users click on next. You will be able to view all the information related to the users. Then you need to specify the criteria or parameters such as user department, job title, usage, and more. Now click on update and then click on next.
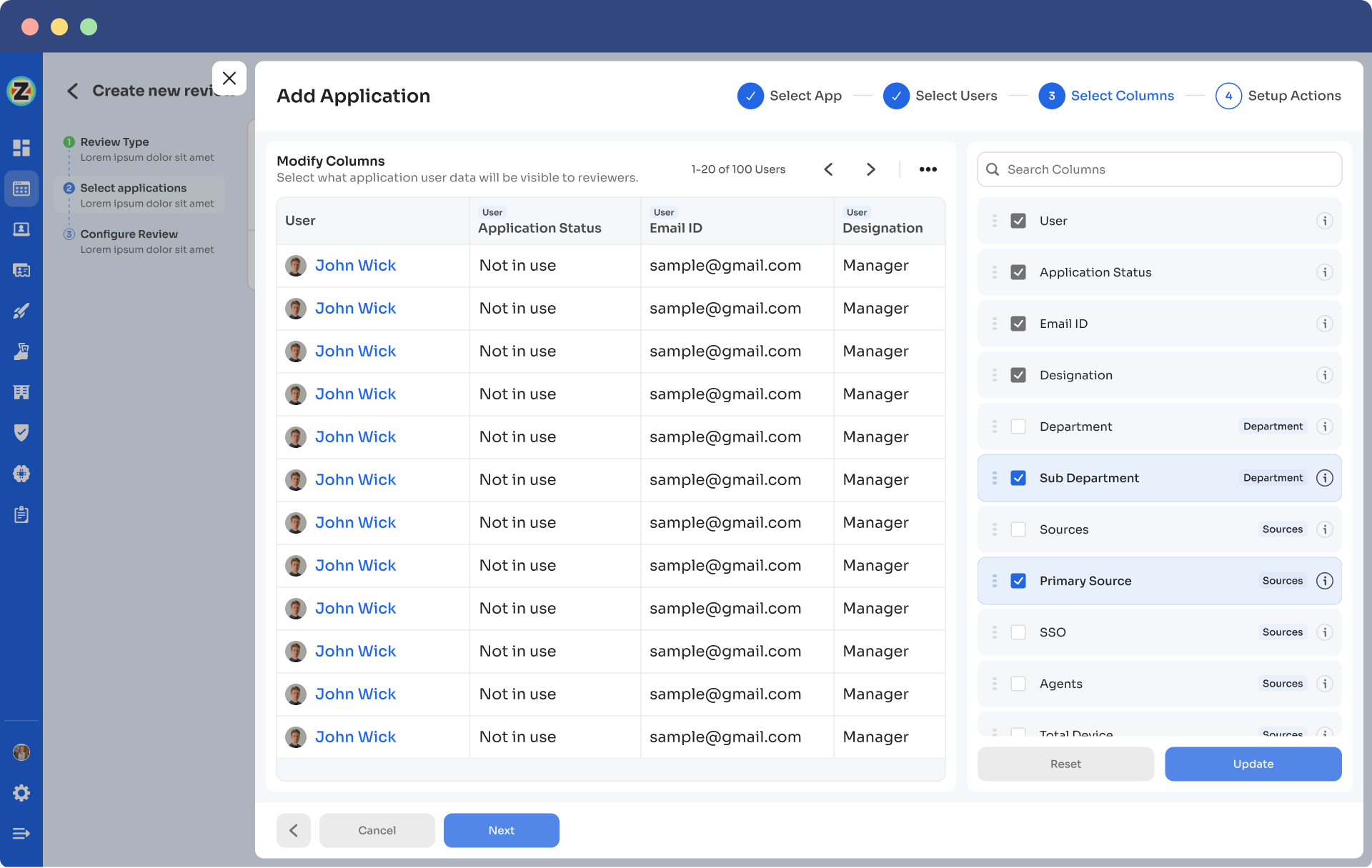
Note: Select those relevant data points only that you wish your reviewers to see while reviewing the access. By filtering the criteria appropriately, you enable your reviewers to make swift and well-informed decisions, streamlining the review process and ensuring efficiency.
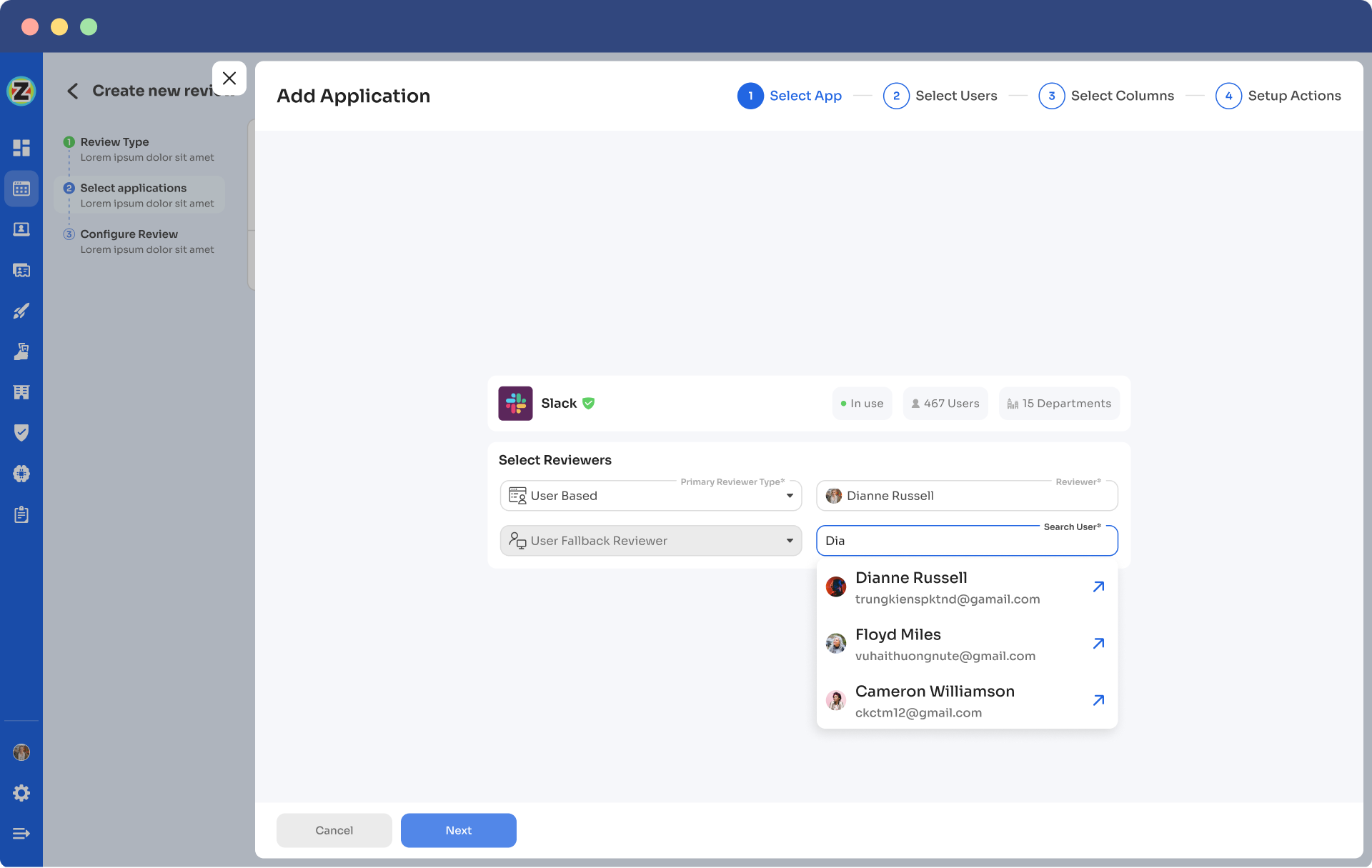
Step 5: Now the Configure Action page will appear, basically, here you have to choose actions. These actions will run post the review.
There are three actions:
Approved- once reviewers approve the user access, Zluri won't run any action, the users can continue with their same access without any interruption.
Rejected- when the reviewer declines or doesn’t approve the user access, you have to run a deprovisioning playbook to revoke the access of that application from the user. If the user has access to critical apps then you can request the assigned reviewer to manually deprovision the user access or else Zluri will auto-remediate if it’s not critical access.
Modify- In this last case; you again need to create a playbook to modify the user access. However, you need to state whether the access permission needs to be upgraded or degraded.
Step 6: Additionally, you can even schedule the actions by setting up the start date and within what time span you want the review to be completed.
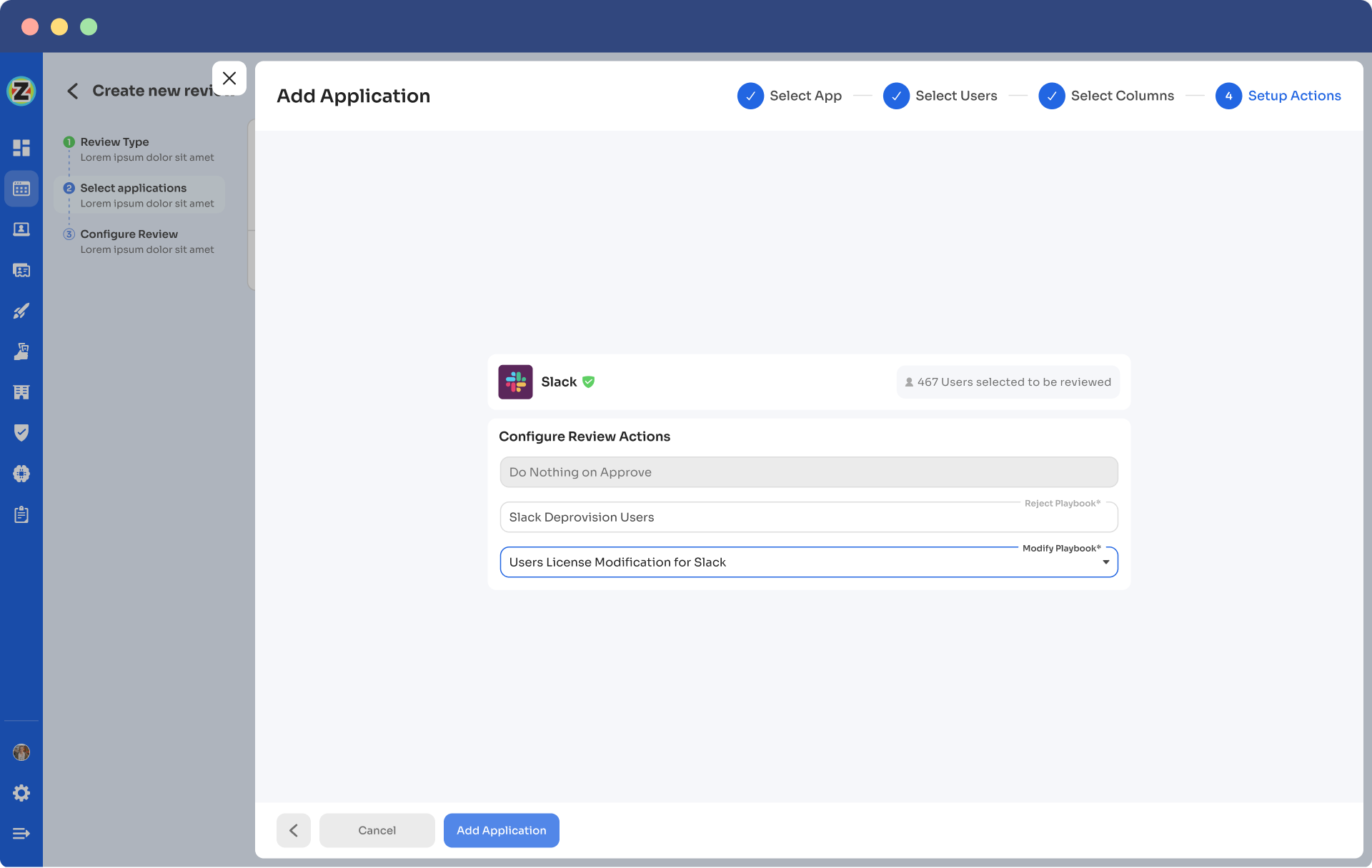
Step 7: Lastly you can keep track of the automated access review process by clicking on the ‘Review Status’ and view whether the review is still pending, modified, declined, or approved.
Also, you can add multiple applications and follow the same process for each selected application.
Zluri also provides the owner access to a snapshot view of the entire certification process status. Also, they can get an overview of the pending reviews and monitor the status of each app’s review, including their assigned reviewers and their completion status.
You can even send reviewers reminders who are yet to complete their reviews.
Further, to streamline the process for reviewers, Zluri provides reviewers with all the user access data in a single screen, i.e., the reviewer screen. For the same screen, reviewers can approve, modify, and decline access by verifying the data, and also they have to add relevant comments on the same.
Now, you will be able to view the entire status of the review process on the chart and once the process is completed and the owner (assigned reviewer of the certification process) is fine with the review. You can click on conclude and it will straight away send the reports to the reviewers' email.
Zluri is not restricted to these only, It offers additional capabilities like integration and reporting features. Zluri’s integration features are quite beneficial when gathering access data. Though Zluri already has data within its platform, but integration allows it to gather even more valuable insights. Leveraging these integrations further enhances your access review process and strengthens the organization's overall security posture.
Additionally, Zluri generates reports commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And, audit trails act as roadmaps, showcasing the changes made during previous reviews.
Now that you know how Zluri can be the perfect IGA solution to mitigate the cornering identity and access management challenges. So why wait any longer? Book a demo now and witness how with Zluri, your IT team can govern, manage, and control user access by ensuring that users have the right access aligned with their roles and responsibilities, mitigating potential security risk



Go from SaaS chaos to SaaS governance with Zluri
Tackle all the problems caused by decentralized, ad hoc SaaS adoption and usage on just one platform.
.webp)
















.webp)
.webp)





.webp)