
8 Proven Best Practices To Optimize IGA
Maintaining the right balance between data security and user access ease can be a challenging task for the IT team. In this article, we’ll learn how your team can strike this equilibrium by implementing IGA best practices.
To keep your SaaS app data safe from security breaches while making user access easy, IT teams need to find the right balance. Follow IGA best practices to achieve this balance.
With IT infrastructure becoming more complex, risk and security management teams seek heightened control over user access provisioning, as well as the precise delineation of rights and privileges across IT assets. However, the question arises: where do these complexities originate?
The landscape encompasses an array of on-premise and cloud-based applications alongside associated digital resources. Furthermore, a diverse range of workforce users, including managers, contractors, and employees, necessitates varying access levels. Recognizing that not all individuals should possess identical application rights is pivotal. The escalation of privileges places the organization at risk of intentional or unintentional data leaks, damage, or mishandling.
Beyond the security implications, these concerns extend to non-compliance issues, potentially failing to meet regulatory requirements, and the introduction of complications during internal or external audits.
Consequently, IT and security teams aspire to exercise meticulous control over identity governance and administration. Their objective is to facilitate user access to appropriate applications in a manner that aligns with business objectives, effectively circumventing disruptions.
While investing in a dedicated IGA tool presents an evident solution, adhering to the following 8 best practices is imperative. These practices will ensure enduring security and effective compliance management for your organization.
8 Identity Governance & Administration Best Practices
To begin, developing a comprehensive identity management strategy that aligns seamlessly with your organizational strategic objectives is crucial. This strategy serves as a guiding framework, clarifying the ultimate goals you aim to achieve. It should be tailored to harmonize with your organization's broader objectives for the same period.
Within this strategy, you need to define the internal policies that your identities will adhere to. This includes determining the guidelines for access provisioning and deprovisioning processes. Additionally, you must outline the various roles and their associated rights within your system. Lastly, don't overlook the vital aspect of compliance tracking.
Once these foundational elements are in place and you're ready to embark on the journey of mapping devices and user identities, it's crucial to follow the following measures to ensure a seamless transition:
1. Centralizing data management for effective governance
Individuals often possess various identities across numerous digital platforms. Establishing a centralized identity management system becomes essential to correlate these identities with users and effectively oversee their access. This approach allows for the creation of a unified identity encompassing user attributes, roles, access levels, privileges, and entitlements.
Centralized management simplifies monitoring processes, facilitates the addition of new access rights, enables modifications to existing permissions, and supports customization efforts. Moreover, centralized data availability empowers concerned departments such as IT, risk management, and cybersecurity, making reporting and risk assessment more efficient and effective
2. Securing high-value assets with a zero-trust approach
To safeguard sensitive data within high-value assets (HVA), robust measures are essential. Implement IGA practices as a defense against vulnerabilities and threats. Begin by identifying, listing, and maintaining a constant vigil over HVAs. For cloud applications, scrutinize integrations, shared data, storage, and user permissions.
Enforce identity management, restricting privileges, and instituting a zero-trust policy. Tailor custom policies for user access to thwart misuse, and proactively eliminate dormant accounts to bolster security.
In the context of remote work, ensuring company data security is paramount. Conventional username/password authentication harbors risks. Embrace a comprehensive zero-trust policy for both security and identity. Continuous verification is pivotal, mandating authentication for all actions, even within your network.
Enhance this with added verification layers for new networks, data requests, or unfamiliar devices. By giving precedence to these measures, your organization elevates security, fortifies data integrity, and guarantees authorized access to vital resources.
3. Streamlining user authentication with SSO & multifactor authentication (MFA)
Passwords are the entry point for authenticating a user into an IT system. Having a strong password policy is one thing that you can enforce among your users. You can even use an SSO (Single Sign-On) that allows users to access all internal applications from one dashboard with a single username and password.
Users find it the best way to access it as they don’t have to remember multiple passwords and can reset them in one go. You can also set internal rules to set strong passwords that are difficult to crack and allow them to be reset at regular intervals. If you want to strengthen this further, multifactor authentication is the answer. This means they have to use one or two more authentication methods after entering the password.
This is because anyone can log in when with the right username and password. With the help of IGA tools, IT teams can set up MFA that users must follow to authenticate themselves fully. You can either select one or two methods from the following along with passwords, phone numbers or email authentication, unique tokens, security questions, or biometric authentication like a fingerprint or facial scanner.
4.Privilege minimization for stronger security and streamlined complaince
The principle of least privilege serves as a cornerstone for a secure environment. It revolves around granting users the precise access they need for their roles, avoiding unnecessary permission escalations. This not only reduces complications but also empowers IT and security teams to maintain tight control over access levels, actively mitigating vulnerabilities.
For non-admin and super-admin accounts, adhering to the least privilege principle is vital. This translates to assigning essential privileges tailored to their functions. Custom rules can temporarily provide elevated permissions for critical tasks, with validation preceding bestowal and prompt revocation afterward.
This approach streamlines monitoring, bolsters defenses against surface-level attacks, and maintains a balance between operational efficiency and security.
Ensuring adherence to industry standards—such as HIPAA, SOC, COBIT, NIST, and others—is paramount. Establishing a resilient system for continuous compliance management takes center stage. Regularly monitoring identity and access systems, conducting audits, and meticulous documentation form the bedrock. Taking a proactive stance on data protection involves precise analysis of access privileges.
Moreover, adhering to data retention protocols and responsible data disposal is pivotal. Automation simplifies the separation between data worth retaining and data that can be let go. This approach not only safeguards data but also nurtures trust among stakeholders.
5. Implementing effective segregation of duties (SoD) practices
A combination of multiple privileges is enough for an application user to go against the system or leak data. This is why you should embrace SoD while assigning permissions to user roles. For example, you cannot assign the same user access to import the data and delete them. This way, it’s also easier to find out the source of any security incident that has happened.
Involving multiple people in every process can be heavy on users, but it can also instill great controls and security practices right from the start. One of the ways through which SoD can be implemented is identity tools where you can roles with custom permissions, assign them to the right users, and manage them consistently.
You can combine SoD with access certification to strengthen it. Here, users have to continuously verify themselves before performing an intended action, like before every login attempt or initiating any critical step. This also helps you be aware of who accesses what and know if there are any discrepancies in this.
SoD can become super complicated with increased roles and functions. You have to devise carefully, look for what users require to carry out their roles without creating a security compromise situation, and frame the SoD policies based on them.
6. Automating workflows for enhanced data governance
Streamlining processes through automated workflows is crucial for expediting the often cumbersome and time-consuming tasks of provisioning and deprovisioning. These processes can become increasingly complex as new users and applications are added to the system. By implementing automated workflows, the burden of manual intervention is significantly reduced, allowing for easy scheduling and execution with just a few clicks whenever access needs to be granted or revoked.
Through automated workflows, the potential for errors related to application access, role assignment, and permissions is greatly diminished, as there is no manual input required. Employees gain instant access to the necessary resources, while you can ensure their permissions align precisely with their roles. This not only enhances operational efficiency but also curtails operating costs.
In scenarios requiring user deprovisioning, swift action is imperative once a user departs. Manual processes might prove insufficiently agile in such cases, potentially leaving dormant accounts vulnerable. The implementation of automated workflows stands as the optimal strategy to preempt any security breaches stemming from improperly deprovisioned users.
7. Generating identity governance and administration(IGA) log reports
Identity governance and administration tools are critical in producing comprehensive identity data reports. These reports encompass various aspects, such as user access data every month, logs detailing user activities, compliance status updates, and more. Such reports serve as invaluable resources for security and IT managers, empowering them to evaluate the organization's security stance and proactively avert potential security breaches.
A distinctive feature of IGA tools lies in their capacity to tailor these reports according to your specific IGA requirements. Furthermore, these tools offer the option to automate the delivery of these reports, streamlining the process for users.
As you embark on the setup of this functionality, a key objective should be to centralize the storage of these reports. For optimal accessibility, it is recommended to opt for cloud-based storage solutions over local systems. Cloud storage offers the advantage of convenient storage and seamless accessibility, fostering a more efficient approach to managing these critical reports.
8. Conducting frequent audits for mitigating risks
Frequent audits have proven indispensable for numerous IT teams in identifying and mitigating significant vulnerabilities and risks. These proactive measures save valuable time and resources and preempt potential breaches. Your team can establish a consistent monthly or quarterly audit schedule to ensure a robust security framework.
The process entails assigning the appropriate team of skilled professionals to execute the audit. This involves meticulous planning, including scheduling, allocation of resources, and strategic execution. During these audit sessions, the IT or risk manager scrutinizes various facets, such as user identities, high-value assets (HVAs), access logs, internal controls, role assignments, special privileges, and unauthorized access attempts.
Additionally, compliance checks and related evaluations are conducted to ensure adherence to regulatory standards.
The insights gained from these audits serve as a comprehensive risk assessment. This assessment illuminates weaknesses and vulnerabilities within the IT system, paving the way for proactive rectification measures before the subsequent audit cycle. Moreover, the process offers an invaluable opportunity to gauge the organization's adherence to data security protocols and regulatory mandates.
Efficient identity governance and administration have become paramount for ensuring security and compliance. Amid this context, Zluri emerges as a standout solution that redefines the conventional approach to IGA.
Zluri: Ensuring Robust IGA for Streamlined Identity Governance & Maintaining Security
Zluri brings about a transformative paradigm shift in the realm of identity governance and administration, empowering your IT teams to effectively oversee and fortify user access protocols.
Central to Zluri's approach is the provision of a centralized dashboard that offers a holistic view of the organization's entire suite of SaaS applications. This real-time, comprehensive insight forms the bedrock for ensuring secure and authorized access to mission-critical applications. By strategically deploying Zluri's IGA capabilities, your teams are empowered to optimize their identity management practices.
Zluri distinguishes itself from other IGA tools through a constellation of exceptional features, each tailored to enhance security and streamline identity management processes. By leveraging Zluri, you can proactively address the challenges presented by the dynamic nature of modern work environments, ensuring that security and compliance concerns are not only met but exceeded.
As a result, your IT teams are equipped with the means to bolster security protocols, efficiently manage user access, and navigate the intricacies of regulatory frameworks—all while seamlessly adapting to the evolving demands of the digital landscape.
1. Streamlined insights through Zluri’s innovative discovery methods
Discover the transformative power of Zluri's data engine, redefining identity governance and security measures for the modern age. Zluri stands at the forefront with an advanced data engine that employs cutting-edge discovery methods to provide unmatched insights into SaaS applications and user-related data.
These methods encompass everything from single sign-on and identity provider integration to finance system analysis and direct app integration. Optional desktop agents and browser extensions offer a comprehensive view of an organization's application landscape, enabling IT teams to swiftly identify access, scrutinize permissions, and bolster security.

Zluri's data engine eliminates the burden of manual app categorization and user access tracking. This innovation brings automation to new heights, intelligently distinguishing between managed, unmanaged, and shadow IT applications.
This automation translates into efficient resource utilization and significant time savings for IT teams, leading to a more streamlined approach to managing the organizational app ecosystem. The data engine's precision empowers IT teams to pinpoint active users, recognize critical users, and enhance security measures through a granular perspective.
Through Zluri, your IT teams can ensure that employees have appropriate permissions for service accounts, mitigating the risks of unauthorized access. With Zluri's data engine, organizations can optimize security measures, ensure compliance, and navigate the digital landscape with confidence.
2. Elevate access & user lifecycle management with Zluri's automation engine
Striking the perfect equilibrium between efficiency and security stands as an utmost priority. Enter Zluri's cutting-edge automation engine, reshaping how organizations approach access and user lifecycle management. The era of labor-intensive manual procedures is behind us; Zluri empowers your teams to concentrate on strategic endeavors while automating intricate access management tasks.
This potent automation engine transcends the fundamentals of user access; its design deliberately optimizes the entire user lifecycle journey. Commencing from the initial bestowal of access privileges to the continuous fine-tuning of permissions based on evolving roles, Zluri guarantees your organization's operational efficiency remains at its zenith without ever compromising on the security of your data.
Through Zluri's automation engine, your IT units can seamlessly grant and revoke access privileges as required, facilitating seamless onboarding and offboarding for employees and contractors alike. This conserves precious time and significantly mitigates the hazards of unauthorized access or persistent permissions.
Simplifying User Access Provisioning for Improved IT Productivity & Security with Zluri
Maintaining robust security and optimizing productivity are paramount in today's digital landscape. By revolutionizing onboarding processes, Zluri liberates IT teams from repetitive tasks and safeguards against potential vulnerabilities.
Zluri's innovation ensures that only authorized personnel gain precise access to vital SaaS applications and data. This intelligent system mitigates the risks of human error and over-provisioning, bolstering your organization's security posture.
Central to Zluri's vision is the empowerment of IT teams. Your IT teams can seamlessly design and personalize onboarding workflows through an intuitive interface, aligning with each new employee's job requirements, roles, and department. This newfound efficiency enables secure access provisioning for multiple hires concurrently, amplifying both efficiency and security.
Zluri's user-friendly interface allows IT teams to configure access privileges effortlessly based on job responsibilities and roles. As Zluri's potent workflow capabilities come into play, a substantial surge in efficiency and employee productivity follows suit.
To streamline the onboarding process using Zluri, follow these straightforward steps:
Step 1: Access Zluri's workflow module and choose "Onboarding" from the dropdown menu. Click on "New Workflow" to begin creating your onboarding process.
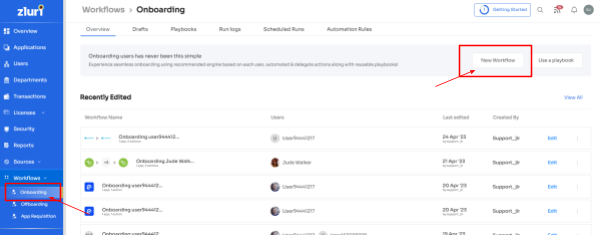
Step 2: Easily select the user(s) you want to onboard by using the search bar or manual selection. Click "Continue" to proceed.
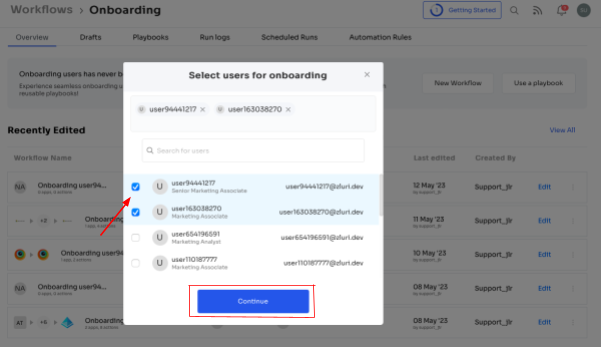
Step 3: On the left side, explore the recommended apps and select the necessary ones for the user. Tailor the onboarding process by defining desired actions for each application.
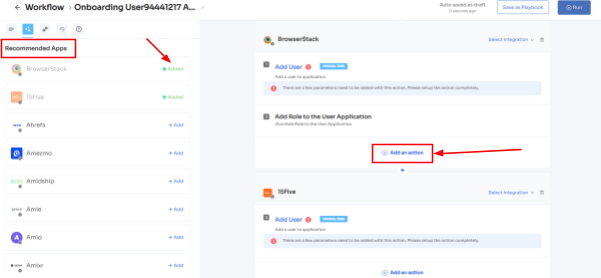
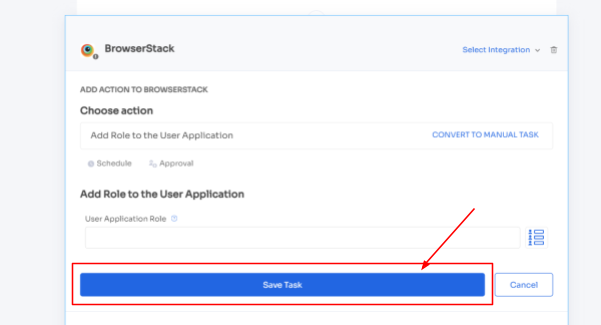
Step 4: Customize actions by selecting "Edit Action\ and providing the required details. You can even schedule these actions to be executed on the day of onboarding. Once finalized, save the actions by clicking "Save Task."
Step 5: To ensure future efficiency, preserve the workflow by selecting "Save as Playbook." Name your playbook in the prompted dialogue box and click "Save Playbook." Your onboarding workflow is now ready to be utilized.
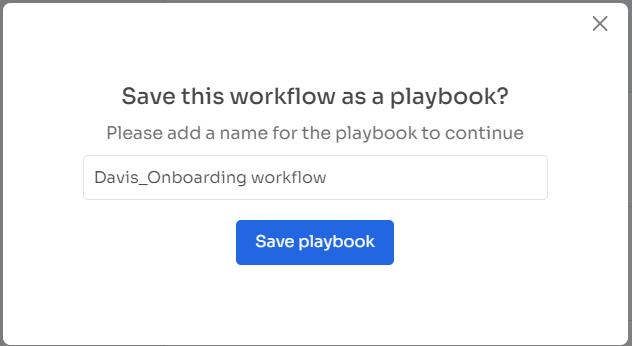
Note: Remarkably reusable and flexible, Zluri's playbooks empower you to shape an efficient onboarding journey, instilling uniformity throughout your organization. By harnessing the power of Zluri's playbooks, you lay the cornerstone for a robust onboarding experience that nurtures a profound sense of belonging and engagement among fresh hires, starting right from their first day.
This collective effort culminates in heightened productivity, diminished turnover rates, and the emergence of a work environment that is both cohesive and prosperous.
Simplifying User Access Deprovisioning for Improved IT Productivity & Security with Zluri
Zluri steps in with an ingenious solution to the intricacies of employee departures. By offering an all-encompassing offboarding playbook, Zluri simplifies the deprovisioning process, making it remarkably efficient.
Through intelligent lifecycle management, Zluri saves valuable time and resources and bolsters your organization's security by promptly deactivating access upon departure. This proactive measure eliminates the risk of data breaches and unauthorized access.
Zluri champions a user-centric approach to employee offboarding, ensuring a consistent and secure experience for all departing team members. With its smooth data transfer and backup mechanism, Zluri prevents critical information from slipping through the cracks. Additionally, Zluri's streamlined license revocation and access termination process reinforces data security.
This combination of efficiency and security empowers HR and IT teams to confidently handle employee departures, alleviating administrative burdens and instilling peace of mind during sensitive transitions. With Zluri, navigating the intricate path of user access management and offboarding becomes a breeze, guaranteeing unwavering security and uncompromised efficiency.
Now, to streamline the Offboarding process with Zluri, follow these straightforward steps:
Step 1: Access Zluri's user-friendly main interface and head to the workflow module. Simply choose the "Offboarding" option from the drop-down list, and click on "New Workflow" to begin.
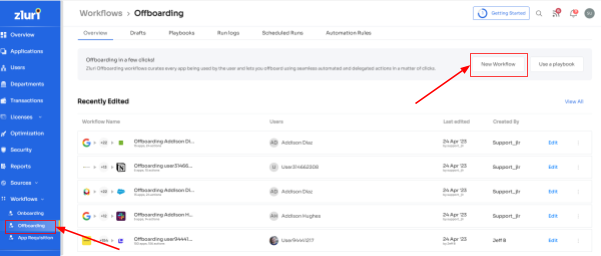
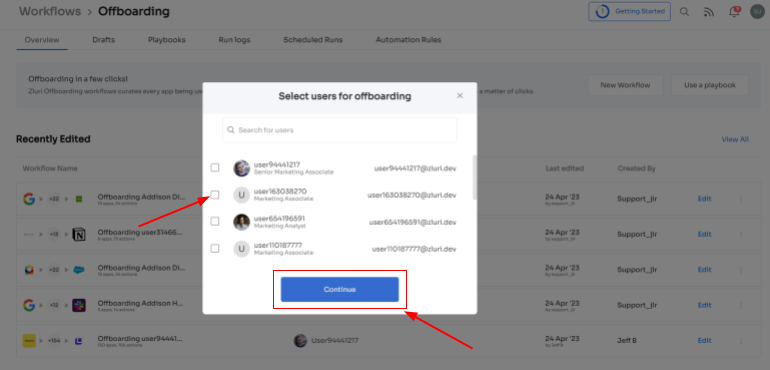
Step 2: Choose the user(s) you wish to offboard by selecting "Select the user for offboarding." Once you've made your selection, click "Continue."
Step 3: Zluri provides recommended actions tailored to specific apps. Effortlessly choose from a range of suggested actions and execute them across the selected applications.
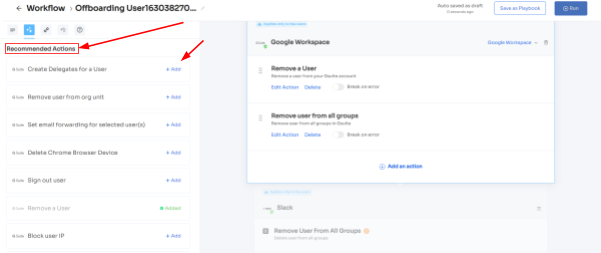
Step 4: To include additional actions, click "Add an Action." Fill in the necessary details and save the task by clicking "Save Task.".
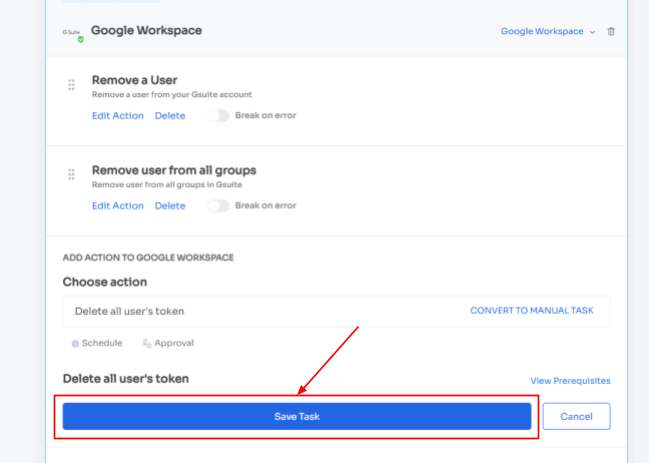
Step 5: Finalize the workflow by saving it as a playbook. Provide a name, click "Save Playbook," your offboarding workflow is now set and ready to go.
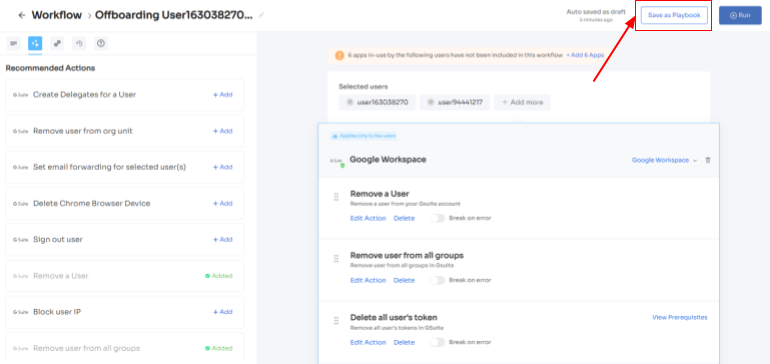
Note: Tap into the complete power of Zluri's playbooks, allowing you to create personalized workflows equipped with actions triggered by specific conditions. Craft automation that aligns perfectly with your organization's distinct needs and operations, offering a realm of unlimited possibilities.
By embracing this automation, you'll infuse newfound speed and precision into your deprovisioning processes. This translates to rapid and precise access revocation, culminating in a smooth offboarding journey.
Effortless access request management with Zluri's Employee App Store
Managing access permissions during employee transitions can be an intricate and demanding endeavor. Balancing the need to provide employees with appropriate access for their new roles while upholding the security of sensitive data against unauthorized use is paramount. Luckily, Zluri introduces the revolutionary Employee App Store (EAS), a self-serve model designed to simplify access request management, making the process efficient and secure.

Say goodbye to labor-intensive manual processes for permission management. With Zluri's EAS, both team members and approvers can seamlessly review and approve access requests tailored to specific job roles. This meticulous approach ensures employees have precisely the right level of access required for their tasks, all the while preventing unnecessary exposure to sensitive information.
Zluri empowers you with unprecedented control over access privileges, cultivating a secure environment within your organization's boundaries. Harnessing cutting-edge technology, you can effortlessly safeguard critical data, mitigating the risk of unauthorized access and retaining complete control over employee-accessible tools and resources.

The EAS functions on a robust approval system, encompassing three distinct tiers: app owners, reporting managers, and IT administrators. This multi-layered strategy empowers higher authorities to supersede decisions made by lower-level administrators or managers, enabling swift and resolute actions as needed.
Approvals and rejections of access requests are complemented by comprehensive explanations and comments, ensuring employees comprehend the rationale behind each determination. This approach fosters collaboration and clarity throughout the organization's access management process.
But that's not all! Zluri's intelligent solutions empower approvers to fine-tune specific access requests, tailoring permissions to precisely match the organization's distinct demands. Ensuring stakeholders are well-informed is critical, which is why Zluri's IGA solutions feature an exhaustive "changelog" functionality. This resource permits users to monitor updates, spanning from approvals and rejections to alterations in license duration or tier assignments.
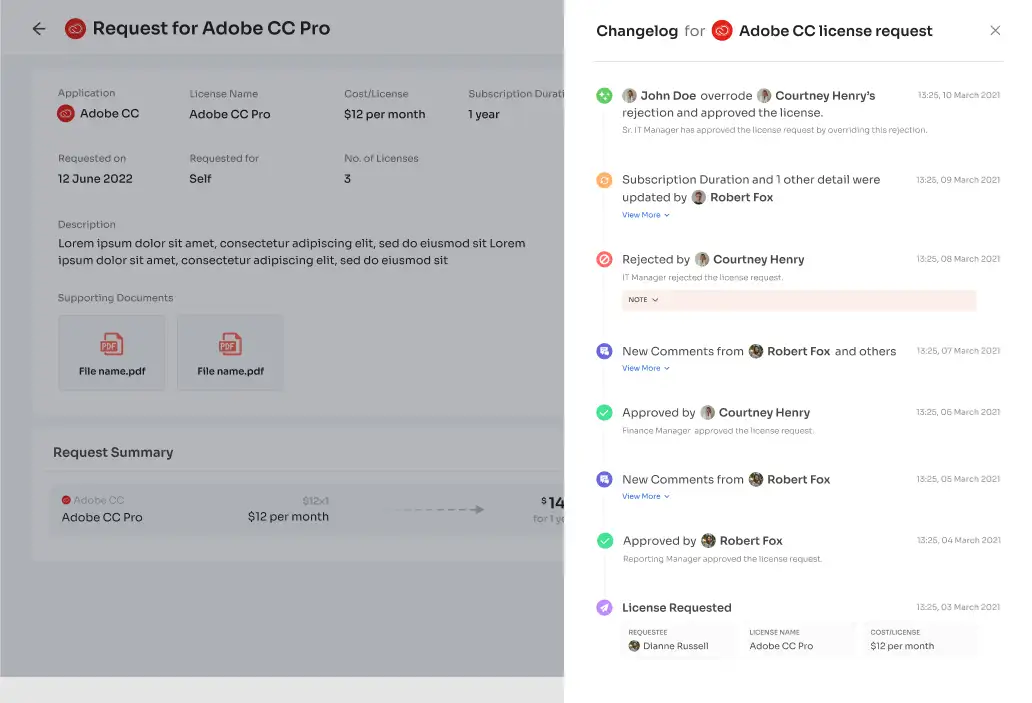
Moreover, the changelog captures valuable insights, including comments contributed by any administrator, fostering a cooperative and well-informed method to access management. Thanks to Zluri's EAS, managing access requests has never been as efficient, transparent, and secure, allowing your team to navigate employee transitions with unwavering confidence.
Transforming access certifications with Zluri's IGA solution
By seamlessly merging automation and security, Zluri redefines access certifications, liberating admins from the shackles of manual processes. This transformation saves time and amplifies the focus on mission-critical tasks. Zluri introduces a revolutionary approach to access reviews through its IGA solution. This approach, powered by automation, replaces what used to be a time-consuming and labor-intensive task with a streamlined and efficient process.
Zluri's IGA solution brings an incredible tenfold increase in review efficiency. Manual reviews become a thing of the past as Zluri empowers your team with rapid access assessments. Beyond time savings, this automation-driven approach enhances accuracy and reinforces security. Zluri's IGA solution equips your organization to navigate identity governance intricacies while upholding the highest security standards.
Comprehensive Identity Insight: A Unified Perspective on Digital Identities
Zluri's IGA solution introduces a paradigm shift with its unified access management approach. Providing a comprehensive view of an organization's access landscape eliminates the complexities of dealing with multiple identity repositories. Users and admins no longer need to navigate various directories to grasp access-related information. Instead, they can rely on a single, intuitive platform offering a seamless and cohesive experience.
- Access directory: Consider the scenario where an employee changes roles within an organization. Their access privileges need to be updated across various systems, which can be a daunting task prone to inaccuracies. With Zluri's IGA solution, the access directory captures these changes across sources, ensuring accurate and complete records. This means that when an audit is conducted, all access changes are documented, and there's no room for incomplete or outdated information.
- Access privileges: In the world of cybersecurity, examples of unauthorized access are unfortunately common. Imagine an employee who recently left the company still having access to critical systems due to oversight. Zluri's unified access management would prevent such scenarios by granting administrators real-time visibility into access privileges. If an ex-employees account attempted to access sensitive data, an instant alert would be triggered, allowing administrators to take immediate action.
- Real-time activity: Consider a scenario where a legitimate employee's account is suddenly used to access sensitive data from an unfamiliar location. This could indicate a compromised account. Zluri's IGA solution would detect this unusual activity and trigger an alert, allowing security teams to investigate and mitigate potential threats before they escalate. This proactive approach prevents data breaches and ensures that an organization's sensitive information remains secure.
Automated Reviews: Harnessing the Potential of Automation for Enhanced Efficiency
Consider a scenario where a large company with numerous employees needs to conduct regular access reviews to ensure the right people have appropriate permissions. The manual process might involve sending spreadsheets to managers, waiting for responses, and manually cross-referencing access rights. This consumes time and can lead to oversights that expose sensitive data to unauthorized individuals.
Zluri's IGA solution addresses these challenges with automated reviews. Instead of relying on slow and error-prone manual processes, Zluri's system can automatically scan access permissions, compare them against defined rules, and generate comprehensive reports. This automation saves time and significantly reduces the risk of human errors, ensuring that only authorized personnel have the right level of access.
- Access rules: Zluri's IGA equips you with unparalleled control over access rules and policies. This adaptability is tailored to align with distinct roles, responsibilities, and specific business needs. The strategic application of automation assumes a pivotal role in this process, allowing the platform to instantly review and validate user access against predefined criteria.This meticulous approach eradicates any ambiguities in the review process, ensuring access is exclusively granted to authorized personnel. Consequently, the system's security is fortified, and the risk of unauthorized access is substantially diminished.
- Scheduled certification: Zluri's IGA introduces a forward-thinking scheduling feature that automates system-generated reviews at regular intervals. By taking this proactive stance, the solution guarantees that access rights remain current and in harmony with evolving security policies and industry best practices.A consistent and compliant access environment is perpetuated through these scheduled certifications, effectively minimizing potential security gaps and vulnerabilities.
- Auto remediation: Imagine a situation where a security breach occurs, and unauthorized access is detected. Without automated remediation, the teams might rely on manual processes to revoke access, notify relevant parties, and initiate corrective actions. This delay could exacerbate the impact of the breach.Zluri's IGA solution addresses this issue by enabling auto-remediation. If a security vulnerability is identified, the system can automatically take predefined actions, such as revoking access, notifying users and managers, or triggering workflows for necessary approvals. This rapid response minimizes the window of exposure, strengthens the organization's security stance, and demonstrates a proactive defense against cyber threats.The fusion of automation with meticulous access reviews leads to an optimized process, liberating precious time and resources that can be channeled into more pivotal endeavors. This decrease in manual involvement speeds up processes and also protects against human errors, ensuring accurate and consistent access reviews.Zluri's IGA solution not only simplifies processes but also fortifies security measures. Through its automated framework, your teams are empowered to uphold a robust security posture. Scheduled certifications adopt a proactive stance, perpetually reassessing access permissions. This proactive approach acts as a shield, preemptively averting potential security vulnerabilities and ensuring alignment with compliance prerequisites.
Here’s how you can automate user access reviews. Zluri’s ‘Access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the "Access certification" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.
- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the "Application" review method if desired and add the relevant application(s) to be audited for users' access.

- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.

- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.
Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.

- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the "Save Template" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the "Review Stage" section.
Zluri's IGA solution brings about a groundbreaking change in the access review process. Through the power of automation, the burden of access review is significantly reduced. The platform automates key tasks, simplifying the workflow. As a result, your team can experience a remarkable 70% reduction in manual efforts required for access reviews.
Imagine the possibilities when Zluri's IGA takes over the review process. Your team can now divert their focus from repetitive tasks. With Zluri's IGA handling the bulk of the process, your workforce can channel their time and skills into strategic endeavors. Freed from administrative burdens, they can drive growth, innovation, and enhanced customer experiences.
Zluri stands as a catalyst for change in the world of IGA innovation. It showcases how automation can streamline operations and amplify human ingenuity. As Zluri's IGA takes center stage, brace yourself for heightened efficiency, improved security, and an empowered workforce propelling your journey forward. Book a demo now!



Go from SaaS chaos to SaaS governance with Zluri
Tackle all the problems caused by decentralized, ad hoc SaaS adoption and usage on just one platform.
.webp)
















.webp)
.webp)





.webp)