
How Zluri Helps with SOX Readiness
Compliance with SOX can be a complex and demanding process. Organizations must adhere to stringent internal controls, policies, and procedures. However, with the assistance of Zluri, navigating the intricacies of SOX becomes more efficient and effective.
The Sarbanes-Oxley Act (SOX) is a critical regulatory framework. It imposes strict requirements on organizations to ensure financial accountability, transparency, and the detection and prevention of fraudulent activities. Complying with SOX regulations is vital for businesses to maintain the trust of investors, stakeholders, and the public.
However, achieving SOX compliance can be challenging due to the complex requirements and the ever-evolving business landscape.
In this context, technology is crucial in facilitating and streamlining the process of achieving and maintaining SOX compliance. The right solutions can automate and streamline SOX readiness processes, enhance visibility, and provide organizations with the tools to mitigate risks effectively.
That is where Zluri comes into play.
How Zluri Helps with SOX Readiness: Top Ways
Let’s delve into how Zluri facilitates SOX readiness for organizations operating in today’s dynamic regulatory landscape.
1: Complete Visibility into App Usage with Data Discovery Engine
Zluri's data discovery engine empowers organizations with complete visibility into their IT environment, ensuring full transparency across systems, applications, and data repositories housing financial information. Here's how Zluri achieves this:
- Multiple Data Discovery Methods: Zluri employs various data discovery methods to ensure coverage of the IT landscape. These methods include:
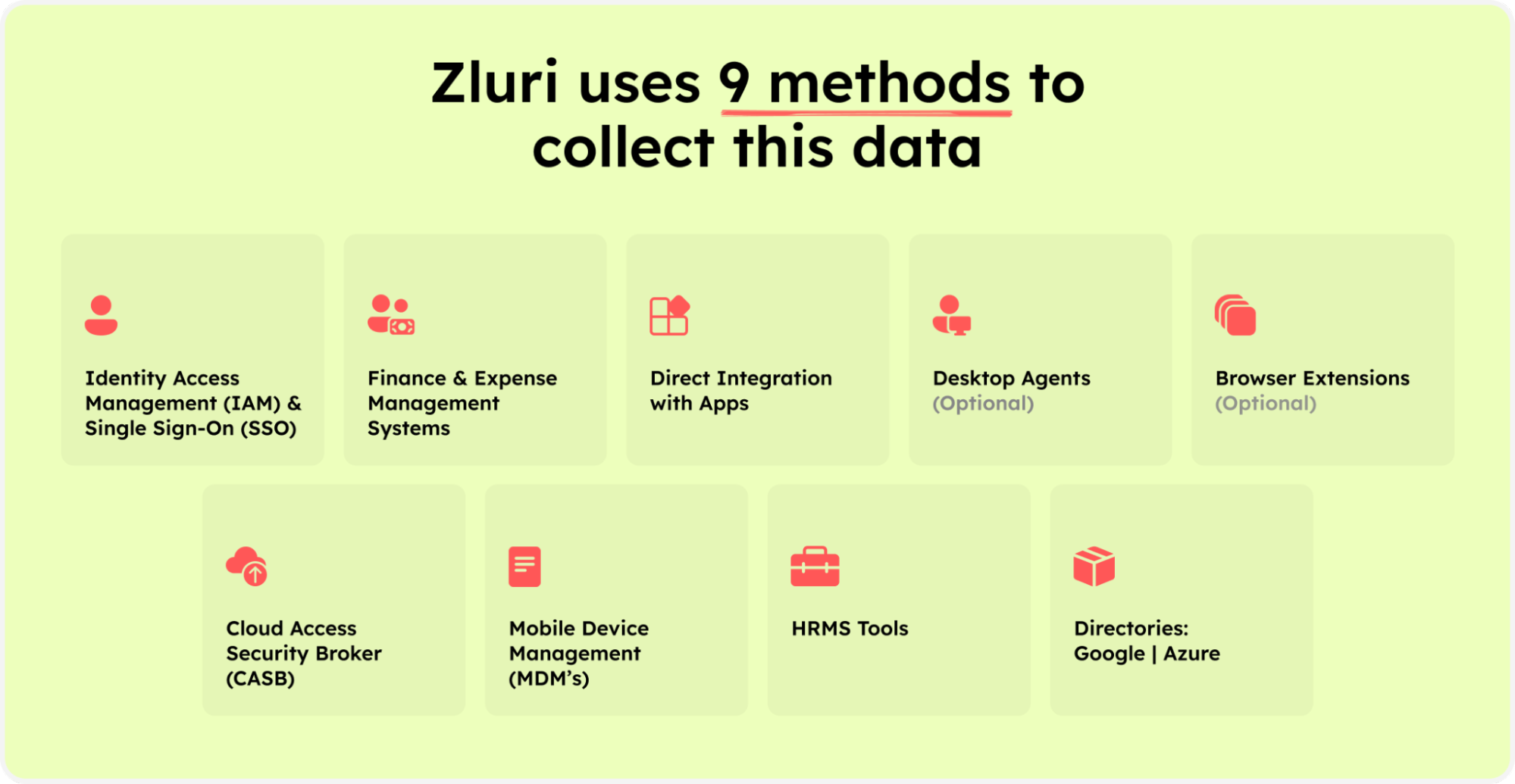
Zluri’s nine discovery methods
- Single Sign-On (SSO) & Identity Providers (IDPs): Integrating with SSO and IDP solutions allows Zluri to access and analyze user authentication and access data across different applications and systems.
- Finance Systems Integration: Zluri integrates with finance systems to access and analyze financial data, ensuring visibility into critical financial systems and transactions.
- Direct Integration: Zluri establishes direct integrations with systems and applications to gather data and insights directly from the source, eliminating dependencies on intermediaries.
- Optional Desktop and Optional Browser Agents: Zluri deploys agents on desktops and browsers to monitor user activities and access permissions, providing visibility into user interactions with applications and data.
- Mobile Device Management (MDM) Platforms: Integration with MDM platforms allows Zluri to monitor and manage access to corporate data on mobile devices, ensuring complete visibility into all endpoints.
- Cloud Access Security Broker (CASB) Platforms: Zluri integrates with CASB platforms to monitor and control access to cloud-based applications and data, ensuring visibility and compliance in cloud environments.
- Human Resource Management System (HRMS) Platforms: Integration with HRMS platforms enables Zluri to access employee data, roles, and responsibilities, facilitating alignment between user access and organizational roles.
- Active Directories: Zluri leverages Active Directory integration to gather information about user accounts, groups, and access permissions, ensuring visibility into user access across the network.
- Accurate Cataloging and Classification: Zluri accurately catalogs and classifies data assets, including systems, applications, and data repositories containing financial information. By systematically categorizing data assets based on their sensitivity and criticality, Zluri helps organizations prioritize their compliance efforts and focus remediation activities on high-risk areas.
- Identification of Compliance Risks: Zluri's data discovery engine identifies potential compliance risks by analyzing access permissions, user activities, and data interactions across the IT environment. By detecting anomalies, policy violations, and unauthorized access attempts, Zluri helps organizations proactively address compliance gaps and mitigate risks before they escalate.
Prioritization of Remediation Efforts: Zluri assists organizations in prioritizing remediation efforts by highlighting critical compliance risks and vulnerabilities. By providing actionable insights and recommendations, Zluri enables organizations to allocate resources effectively and address compliance issues in a timely manner, minimizing exposure to regulatory penalties and reputational damage.
2: Unified Access Review & Automated Access Review Process
Zluri aids access review processes by offering unified access review capabilities and automated workflows, enabling organizations to streamline and enhance their compliance efforts, particularly in adherence to SOX regulations. Here's how Zluri achieves this:
- Unified Access Review: Zluri provides a centralized platform for conducting access reviews across multiple systems and applications. This unified approach eliminates the need for manual review processes scattered across disparate systems, ensuring consistency and completeness in access review activities. By consolidating access review activities into a single interface, Zluri simplifies the review process and reduces administrative overhead, leading to improved efficiency and accuracy.
- Automated Access Review Process: Zluri automates the access review process, from scheduling reviews to generating reports and notifications. Automated workflows streamline repetitive tasks, such as identifying users with excessive access privileges or detecting policy violations, allowing organizations to focus their efforts on addressing critical issues. By leveraging automation, Zluri helps organizations conduct access reviews more efficiently and effectively, ensuring compliance with SOX regulations and other compliance requirements.
- Centralized Monitoring and Reporting: Zluri enables organizations to centrally monitor access review activities and track compliance metrics in real-time. Through customizable dashboards and reporting tools, organizations gain insights into access review status, compliance trends, and areas of improvement. This centralized visibility allows stakeholders to make informed decisions and take proactive measures to address compliance gaps and mitigate risks effectively.
- Integration with Identity Management Systems: Zluri seamlessly integrates with identity management systems and directory services, ensuring accurate and up-to-date user data for access reviews. By leveraging existing identity and access management infrastructure, Zluri simplifies the process of identifying users and their access rights, facilitating more accurate access reviews.
- Compliance with SOX Regulations: Zluri's unified access review and automated workflows align with SOX regulations, which mandate periodic reviews of user access rights to financial systems and applications. By providing organizations with the tools and capabilities to streamline access review processes, Zluri helps ensure compliance with SOX requirements and demonstrate effective internal controls over access management.
3: Automated Access Certification for Access Rights Reviews
Many regulatory frameworks, such as SOX, require organizations to demonstrate effective access controls and periodic reviews of user access rights. Automating access certifications helps ensure compliance with these regulations by providing auditable records of access reviews and approvals.
Here's a SOX compliance checklist that might help you make better decisions.
Zluri's automated access certification capabilities empower organizations to efficiently review and certify user access rights to critical financial systems and applications.
Now, let’s take Okta as an example to see how you can automate access review in Zluri.
Zluri significantly reduces the risk of unauthorized transactions, data loss, and data breaches by automating this process.
- Efficiency Advantages: By leveraging Zluri, organizations can accelerate the access certification process, minimizing overall effort by an impressive 70%. This newfound efficiency not only optimizes access management protocols but also frees up valuable resources to drive growth and innovation within the organization.
- Unified Access Management: Zluri provides a centralized hub for managing user identities, access privileges, and the entire certification process. By consolidating user access-related information from various sources, Zluri eliminates the need to navigate multiple directories, providing instant access to all necessary information for conducting thorough access certifications.
- Insights for heightened visibility into user access privileges: Zluri's access review capabilities offer a unified approach to access management by consolidating user access-related information from various sources into a single, intuitive platform. This insight ensures heightened visibility into user access privileges across the organization, facilitating swift identification of discrepancies or suspicious permissions during access certifications.
- Real-time Monitoring and Alerts: Stay ahead of potential security breaches with Zluri's real-time activity tracking and instant alerts for anomalous behavior or unauthorized access attempts. These features are crucial elements in maintaining compliance during access certifications, ensuring organizations remain proactive in addressing security risks.
- Streamlined Access Certifications: Zluri's automated review capabilities streamline access control policies, ensuring robust security and regulatory compliance during access certifications. Administrators can define access rules and policies based on roles and business requirements, with instant reviews conducted against established criteria to maintain compliance and minimize security risks.
- Proactive Maintenance: Zluri allows organizations to proactively schedule certifications based on insights, ensuring access permissions remain up-to-date and compliant. Moreover, its auto-remediation capabilities respond to access violations by triggering corrective actions for immediate resolution, further enhancing SaaS security posture and compliance adherence during access certifications.
- Demonstrating Compliance: Regular reviews and audits of user access rights enable organizations to demonstrate compliance to auditors, stakeholders, and regulatory bodies. By leveraging Zluri's features, organizations can avoid penalties and fines, enhance their reputation, and instill confidence in customers and partners.
4: Segregation of Duty (SoD) Policy Implementation
SOX aims to protect companies by establishing internal controls to prevent fraud and errors in financial reporting. SoD helps achieve this goal by ensuring that no single individual can initiate, approve, and record transactions related to financial reporting without proper checks and balances.
By segregating duties among different individuals, SoD reduces the risk of fraudulent activities, such as unauthorized transactions or falsification of financial records.
Zluri takes SoD monitoring and enforcement to the next level by providing a modern access management platform designed to prevent potential security breaches and ensure compliance with regulatory requirements, particularly SOX. Here's how Zluri achieves this:
- Complete Visibility with Data Discovery Engine: Zluri's data discovery engine scans user access data, giving your IT team complete visibility into who has access to what. By gaining deep insights into user access contexts, your team can ensure that no individual possesses excessive power or sole responsibility for critical IT tasks, thus mitigating the risk of fraud or errors.
- Seamless Policy Enforcement with Automation Engine: Zluri's automation engine allows your IT team to seamlessly enforce SoD policies throughout the employee lifecycle, from onboarding to offboarding:
- Streamlined Onboarding: Zluri automatically links employee profiles with digital identities from the organization's HRMS, facilitating identity verification and role assignment without manual intervention. Customized onboarding workflows and role-based access control (RBAC) ensure that employees receive appropriate access permissions from day one, minimizing the risk of role conflicts or over-permission.
- Mid-Lifecycle Transition Management: Zluri notifies your team about changes in employee roles or departments, enabling timely modification of access permissions to prevent excessive privileges. The App Catalog and App requisition enhance access request management by dynamically adjusting app visibility based on user roles and responsibilities.
- Efficient Offboarding Workflows: Zluri automates the offboarding process, ensuring that access permissions are promptly revoked for departing employees. By implementing role-based access controls and providing centralized visibility, Zluri supports you and your team in enforcing SoD policies and procedures, reducing the risk of data breaches during employee transitions.
5: Robust Reporting and Monitoring to Maintain Compliance with Regulations
Zluri offers robust reporting and monitoring features, empowering organizations to maintain compliance with SOX regulations and effectively manage access-related risks. Here's how Zluri achieves this:
- Aggregation of Data from Disparate Sources: Zluri aggregates data from various sources, including identity management systems, directory services, and access logs from applications and systems. By centralizing this data, Zluri provides a complete view of user access rights, activities, and compliance status across the organization's IT environment.
- Audit-Ready Reports: Zluri enables organizations to generate audit-ready reports demonstrating compliance with SOX regulations and other regulatory requirements. These reports provide detailed insights into access review activities, policy violations, and user access trends, facilitating transparency and accountability during compliance audits.
- Customizable Reporting: Zluri offers customizable reporting capabilities, allowing organizations to tailor reports to their specific compliance needs and requirements. Organizations can define parameters such as access review frequency, policy violation thresholds, and compliance metrics to generate relevant and actionable reports.
- Real-Time Monitoring: Zluri provides real-time monitoring of access-related activities and events, enabling organizations to detect and respond promptly to potential compliance issues. By monitoring user access patterns, policy violations, and suspicious activities in real-time, Zluri helps organizations mitigate risks and maintain compliance with SOX regulations.
- Actionable Insights: Zluri presents actionable insights derived from data analysis, helping organizations identify areas for improvement and take proactive measures to enhance compliance efforts. Whether it's addressing policy violations, optimizing access review processes, or implementing corrective actions, Zluri provides actionable recommendations to support continuous compliance improvement.
- Ad Hoc Reporting: In addition to pre-defined reports, Zluri allows organizations to create ad hoc reports to address specific compliance inquiries or audit requests. This flexibility enables organizations to respond promptly to auditor inquiries and provide the necessary documentation to demonstrate compliance with SOX regulations.
- Audit Trail: Zluri maintains an audit trail of access-related activities, ensuring traceability and accountability in access management processes. Organizations can track changes to user access rights, access review outcomes, and policy enforcement actions, facilitating compliance monitoring and audit preparation.
6: Real-time Alerts and Notifications to Address Risks Promptly
Real-time alerts and notifications offered by Zluri serve as a proactive mechanism for organizations to maintain compliance and address potential risks promptly. Here's how Zluri's real-time alerts and notifications contribute to enhancing compliance and mitigating financial misconduct:
- Timely Detection of Suspicious Activities: Zluri continuously monitors user activities and real-time access patterns across critical systems and applications. By analyzing this data, Zluri can identify deviations from established norms or patterns that may indicate suspicious or unauthorized activities. Prompt detection of such anomalies enables organizations to take immediate action to investigate further and mitigate potential risks before they escalate.
- Proactive Identification of Policy Violations: Zluri's real-time monitoring capabilities extend to enforcing compliance with organizational policies, including Segregation of Duty (SoD) policies and other regulatory requirements. By comparing user actions against predefined policies and access controls, Zluri can flag instances of policy violations as they occur. This proactive approach allows organizations to address compliance issues in real time, reducing the likelihood of regulatory penalties or sanctions.
- Alerts for Unusual Access Patterns: Zluri can generate alerts for unusual access patterns or behaviors that may indicate potential security threats or policy violations.
For example, Zluri can detect excessive access privileges granted to a user, unauthorized attempts to access sensitive data, or unusual login locations or times. By receiving alerts for such activities in real-time, organizations can investigate and respond promptly to prevent security breaches or compliance lapses.
- Customizable Alerting Rules: Zluri allows organizations to customize alerting rules based on their specific compliance requirements and risk tolerance levels. This flexibility enables organizations to tailor alerts to their unique needs and focus on the most critical compliance issues. Whether it's setting thresholds for access privileges, defining criteria for policy violations, or specifying escalation procedures, Zluri's customizable alerting rules empower organizations to proactively manage compliance risks effectively.
- Integration with Incident Response Processes: Zluri's real-time alerts and notifications can seamlessly integrate with incident response processes, enabling organizations to initiate timely investigations and remediation actions. By providing relevant context and actionable insights, Zluri empowers incident response teams to make informed decisions and take appropriate measures to address compliance issues swiftly.
The Ongoing Importance of Leveraging Technology for SOX Compliance
Achieving and maintaining SOX compliance stands as a paramount concern for organizations striving to uphold trust and credibility with stakeholders. As complexities persist, technology solutions emerge as indispensable assets in navigating these challenges effectively.
Zluri, with its suite of advanced features tailored specifically for SOX compliance, emerges as a frontrunner in simplifying and streamlining compliance efforts. Through automated access certification, robust enforcement of segregation of duty policies, and real-time alerts and notifications, Zluri empowers organizations to bolster their SOX readiness and demonstrate unwavering commitment to regulatory adherence.
As organizations prioritize risk management and compliance, investing in technology solutions like Zluri emerges not only as prudent but as imperative for navigating the intricate terrain of SOX compliance with confidence and efficiency.



Go from SaaS chaos to SaaS governance with Zluri
Tackle all the problems caused by decentralized, ad hoc SaaS adoption and usage on just one platform.
.webp)
















.webp)
.webp)





.webp)