ForgeRock Identity enables your IT team to manage and monitor identity (users) access thoroughly. It ensures users are granted secure access to resources and continuously monitors all user access activities. This further helps restrict unauthorized users, preventing cyberattacks and security breaches.
With so many features, it still lacks in certain areas, and thus, many IT teams look for ForgeRock alternatives. This blog lists various alternatives to ForgeRock for Identity and Access Management.
ForgeRock Identity provides IAM (Identity and Access Management) solutions for IT teams to manage digital identities securely and control access to the apps and systems. It provides a set of tools and capabilities for managing user identities, authentication, authorization, and access control in a centralized manner.
Some of the most used key features are listed below:
ForgeRock Identity Features
With ForgeRock Identity Platform, IT teams can manage access to applications and data across the entire enterprise, including on-premises, cloud, and mobile environments.
Also, it offers a range of authentication mechanisms, including single sign-on, multi-factor authentication, and adaptive authentication, which uses risk-based analysis to determine the appropriate level of authentication for each user.
Even though it offers such benefits, it still lags behind because of its limitations, for example:
ForgeRock Identity Drawbacks
- ForgeRock Identity doesn't provide robust reporting functionalities, which could restrict your ability to thoroughly assess access levels and identify potential gaps during audits, thereby hindering your compliance efforts
- Its OpenAM certification is quite costly, so it's unsuitable for businesses with budget constraints.
- The tool's integration capabilities with certain systems, such as Unix-based systems, pose challenges for your team in effectively managing access to those systems. This limitation can potentially expose your organization to security risks
However, sticking to one tool is not mandatory. As a manager, you have the flexibility to explore ForgeRock alternatives to avail full functionalities that will help your IT teams streamline the identity access management process more effectively.
So, to assist you in finding a suitable alternative, we've compiled a list of ForgeRock competitors that can better fit your organization's access environment. Now, let's move ahead and explore the tools.
Here’s A List Of 9 Best ForgeRock Alternatives
Below are some well-recognized ForgeRock alternatives that you can consider opting for your identity and access management needs.
1. Zluri

Zluri offers advanced access management solutions that ensure only the right user can access the right applications at the right time. It securely manages, controls, and governs user access to organizational SaaS applications. This system is designed to enhance and streamline identity and access management tasks, including granting, modifying, and revoking access, implementing policies, ensuring compliance with strict regulations, and more.
Now, let's explore all the benefits Zluri's access management offers:
- Accurately Discover User Access Data
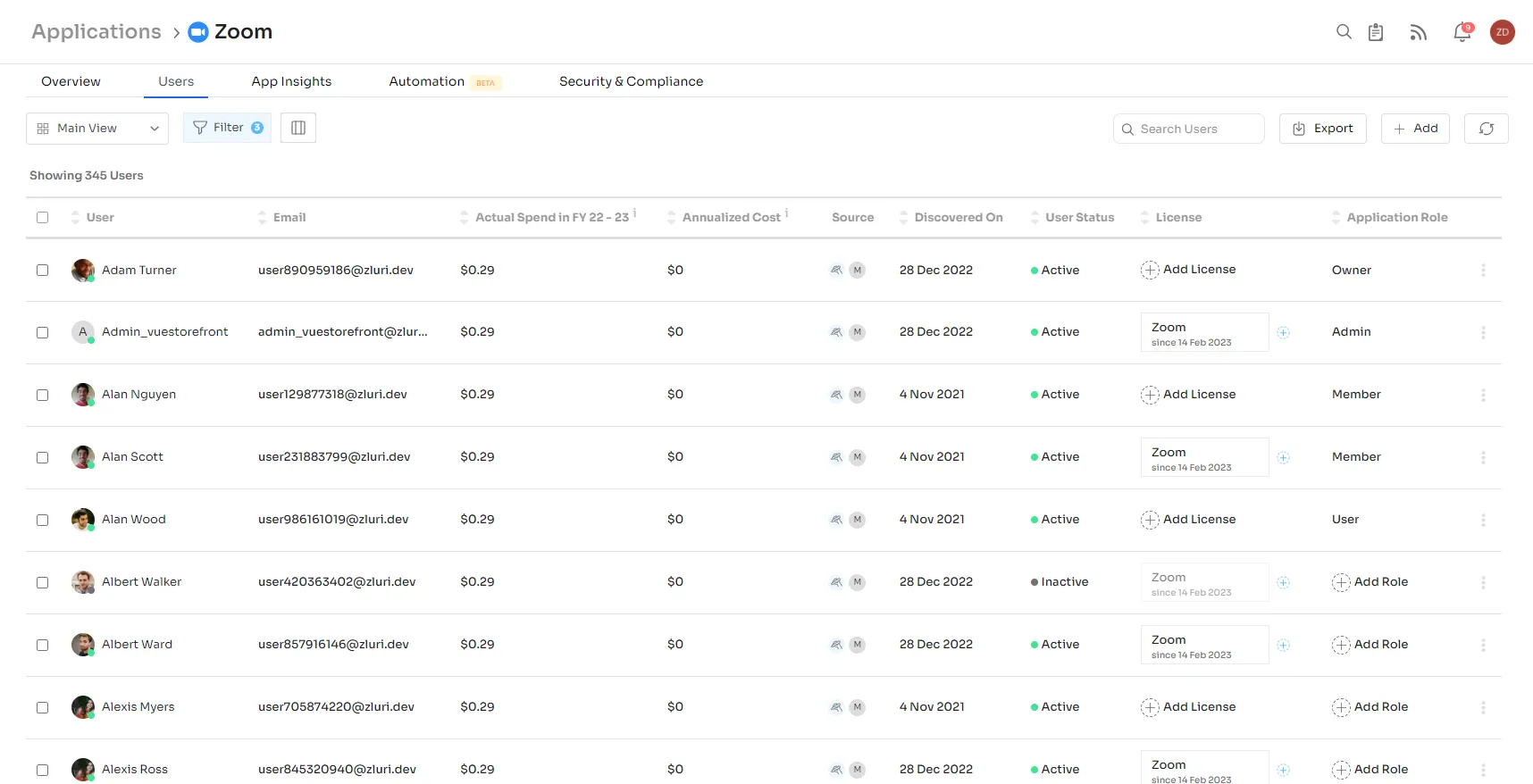
Zluri's access management is better than competitors at discovering user access data. With Zluri's nine discovery methods, i.e., MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional), your IT team can seamlessly identify who has access to what.
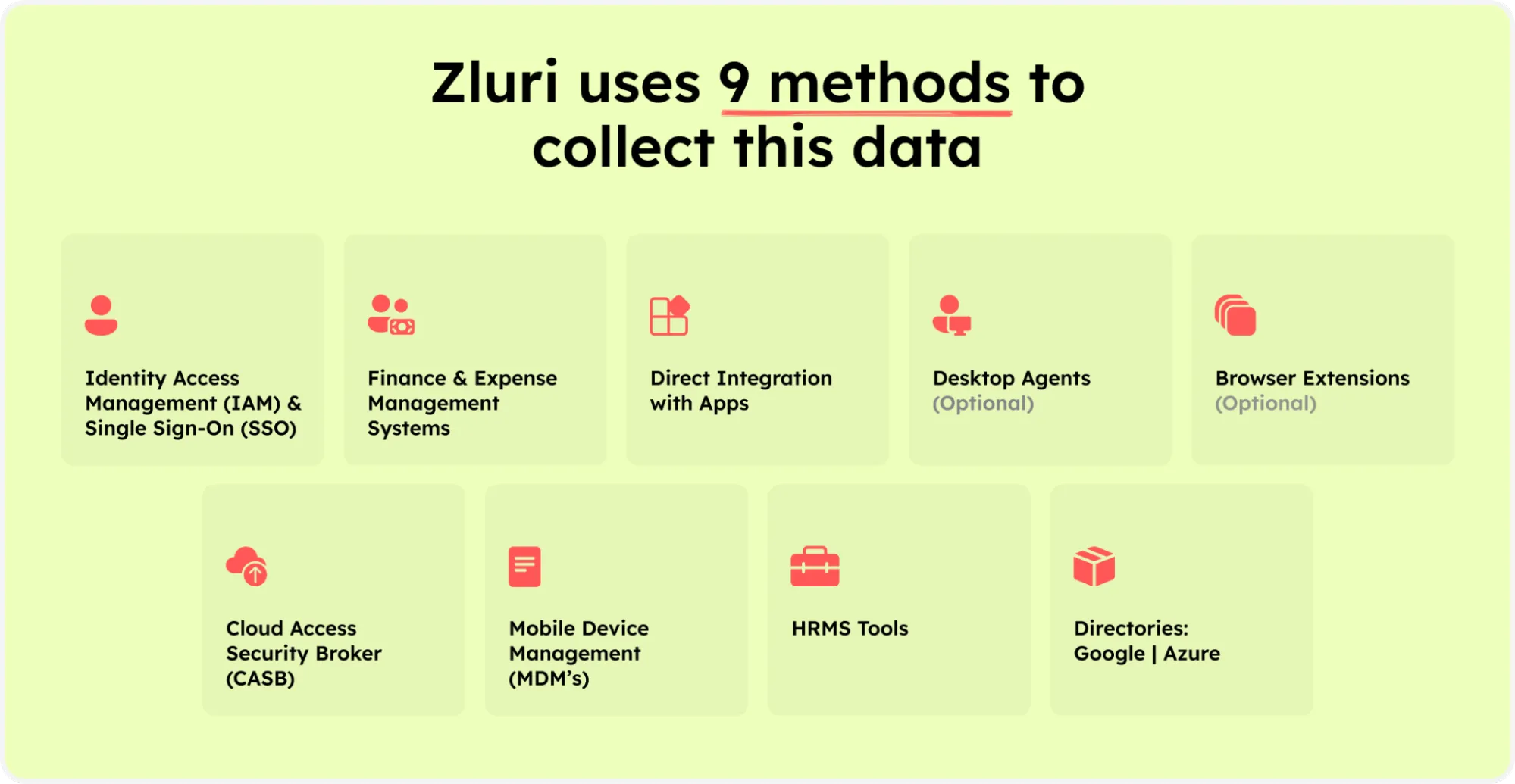
Zluri’s nine discovery methods
For instance, Zluri's access management helps your IT team identify which users have access to particular SaaS apps, what access rights are granted to them, identify the user status (active or inactive), and more.
These insights are a game-changer for user access management and SaaS app data security. Armed with such granular knowledge, your IT team finds it easier to conduct access reviews. Also, the process becomes streamlined, efficient, and less prone to oversight, ensuring access privileges align with user role and compliance requirements.
- Seamlessly Manages Employee Access to SaaS Applications
Zluri's access management seamlessly integrates with your organization's HR system, ensuring your IT team can access up-to-date employee data.
This integration automatically retrieves and displays comprehensive employee information on a centralized dashboard. This enables your IT team to efficiently grant, modify, or revoke access, ensuring that only the appropriate employees have timely access to specific applications.
Furthermore, by streamlining this process, your IT team can improve user experience and productivity by reducing the waiting time for gaining application access.
- Helps Your IT Team To Thoroughly Monitor Access Activities
Zluri's access management enables your IT team to keep track of all access-related activities throughout your organization. This includes monitoring user access to specific applications, keeping a tab on their status as active or inactive, identifying their permission levels, and more.
By consistently monitoring user access activities, your IT team gains insights into access patterns and user behavior. This proactive approach enables your team to ensure that only authorized users can access sensitive SaaS application data, establishing a well-governed and secure environment.
- Helps Your IT Team To Conduct Regular Access Audits
Zluri's access management supports your IT team in performing regular access audits, which involves assessing users' current access permissions to evaluate their continued relevance. Through this review process, your IT team can readily identify any instances of unauthorized or excessive access rights held by users. Accordingly, your team can adjust permissions accordingly, ensuring users have the appropriate level of access to critical applications.
For example, if any user access deviates from the set access policies, Zluri initiates auto-remediation actions.
Such as, it runs a deprovisioning playbook to revoke access if users' access does not meet the access criteria or modify access with the reviewer's intervention.
(Note: For critical data, Zluri enables manual review and remediation of access to ensure extra scrutiny and control)
Additionally, Zluri's access management allows your team to document these access audits, providing a record that serves as evidence of compliance. This documentation demonstrates that access permissions align with updated compliance regulations, helping your organization avoid substantial fines and maintain compliance
- Generates Curated Reports
Zluri's access management generates curated reports that play a pivotal role in identity and access management (IAM). It provides IT teams valuable insights to effectively control and secure user access to digital resources within an organization.
Also, Zluri's reports provide visibility into who has access to what systems and data. This visibility is essential for maintaining a clear understanding of user privileges and potential security risks.
Moreover, as per KuppingerCole’s report, Zluri provides ready-to-use compliance reports are generated right after a review is done.
Additionally, it allows your IT teams to promptly identify any unauthorized access, suspicious activities, or violations of access policies. So that, accordingly, they can take preventive measures to protect sensitive SaaS app data against potential security breaches.
Now that you're aware of the benefits offered by Zluri's access management to streamlining identity access management, why not book demo and experience it firsthand? It could be the perfect fit for your organization.
Pros
- Zluri's access management gives your IT team a centralized dashboard to monitor which users can access specific applications. This centralized visibility streamlines the access management process. It eliminates the need to navigate through multiple screens to gather user and app data, saving your team's time and enhancing their efficiency

- With Zluri's access management, your IT team can create and customize workflows for onboarding and offboarding. These workflows allow them to securely grant access and revoke access to SaaS apps. With just a few clicks, they can onboard and offboard multiple employees. This helps save IT teams productive time and ensures no crucial steps are overlooked

Cons
- Employee actions, like accessing specific SaaS applications, do not appear in the security tab, necessitating your IT team to review each user's profile to determine their app access. Due to this, it takes time to verify if the requested application aligns with the employee's role
- In certain instances, configuring and integrating with other tools can be somewhat intricate, demanding attention to detail to ensure they work properly
Customer Rating
- G2: 4.8/5
- Capterra: 4.9/5
2. Azure Active Directory

Azure Active Directory is now Known as Microsoft Entra ID. It is amongst one of the prominent ForgeRock alternatives that guards employees' identity and crucial data against cyberattacks with multi-cloud identity and access management capabilities. This includes single sign-on, multi-factor authentication, conditional access control, and passwordless authentication.
Also, Azure Active Directory provides an easy and quick sign-in experience for employees to keep them productive, and they no longer have to waste time managing passwords.
Furthermore, Azure Active Directory centrally manages all the users' identities and access permissions, which helps improve visibility and control. With its efficient automated identity governance, IT teams can ensure that only authorized users can access premises applications and data.
Pros
- Azure Active Directory provides a centralized dashboard that enables IT teams to monitor employee access activities seamlessly. This way, they no longer have to waste time going through different screens to navigate user-access data
- It offers IT teams transparent data encryption features to secure crucial data by encrypting it. This helps the IT team ensure unauthorized users cannot access the data stored on the organization's servers
Cons
- Azure Active Directory is not suitable for non-technical users, as it involves high-level coding. So you need to make additional investments in hiring experts to ensure proper utilization of the application
- It only supports a few integration tools, which has an impact on workflow because developers can't rely on particular integration tools to develop applications for guarding sensitive data and employee identities
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5
3. Jumpcloud
JumpCloud offers a centralized identity & access management solution that allows IT teams to manage one set of credentials per user and one identity. It is amongst one of the prominent ForgeRock alternatives that streamlines and automates the creation and deactivation of identities.
Additionally, it uses group-based access control, including automated group suggestions, which enables IT teams to quickly grant new employees access to apps and data based on their role, designation, or department. This further helps in maintaining identity security.
Furthermore, when an employee departs, it deactivates their account and revokes access to any apps or data with it, enabling IT teams to secure crucial data.
Pros
- With Jumpcloud app integration and SSO features, you can significantly reduce the number of passwords employees require to manage. This helps enhance the employee experience while simultaneously strengthening security by minimizing password fatigue
- Its ability to remove employees from multiple groups when they exit from the organization with a single click is a time-saver for IT teams. This also enables IT teams to revoke access to particular applications and ensure security policies are enforced efficiently and consistently
Cons
- Jumpcloud cannot run a command or a batch of commands on a one-time basis for automating certain IT processes. Due to this, IT teams have to manage it manually, costing them their productive time and effort
- Sometimes, it locks users out from their own devices, and they have to verify/authenticate their credentials/identity multiple times to gain access to application
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
4. Rippling
Rippling is an identity management software that serves as one of the notable ForgeRock alternatives. It seamlessly configures, protects, and controls users' devices and apps. When new employees are onboarded, it grants secure access to applications and data based on their position and division within the organization. Similarly, upon an official termination or resignation, Rippling also terminates an employee's access to all Internal systems.
Rippling SSO improves productivity and security across the board by enabling easy, one-click access to all of an organization's apps from a centralized dashboard. Because of its capability, IT managers can keep an eye on and assess real-time app usage by users.
Pros
- Rippling’s IAM offers you a centralized dashboard where you can view all the employee access activities from one location, enabling you to keep track of the entire access management process properly
- It allows you to customize alerts as per your requirement, for instance, it will notify you when an employee raise request for app access
Cons
- Data cannot be updated in bulk, which slows down the process and reduces productivity and efficiency
- This tool doesn't allow you to restrict/ limit what the employees can view, which increases the risk of security breaches as employees can view crucial data and critical apps that they might try to access and misuse them
Customer Rating
- G2: 4.8/5
- Capterra: 4.9/5
5. Ping Identity

Ping Identity is an identity & access management platform with centralized adaptive authentication that provides a seamless user experience. It allows IT teams to connect any application to any device/system. Also, this tool provides seamless access to employees, which improves employee experience.
Also, this ForgeRock alternative follows a zero-trust security strategy that helps maximize connectivity and minimize friction. It verifies/authenticates each employee's role, position, or department during onboarding and grants authorized access to the organization's apps and data. This helps in maintaining identity security.
When employees depart from the organization, it suspends/deactivates the employee's account and revokes all access to apps and data to guard the crucial data against security breaches.
Pros
- Ping Identity uses open standards, which improves its compatibility with other SaaS apps. Due to this, it becomes a suitable platform to utilize for user authentication
- Integrating single-sign-on and multi-factor authentication ensures that employees access company data and apps safely and securely without having to remember multiple passwords or usernames
Cons
- The login process times out very quickly, leaving you with the minimum time to verify your credentials/identity. This can get highly frustrating and causes work to pause.
- Sometimes, the application would automatically unpair from your device, and you have to perform the setup process over again, wasting your productive time and energy
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
6. Okta Workforce Identity
Okta Workforce Identity is a cloud-based identity & access management platform. This notable ForgeRock alternative enables IT teams to grant employees secure and instant access to the organization’s applications, devices, and data. Also, IT teams can manage authorization, user authentication, and SSO across different apps and systems.
Furthermore, Okta Workforce Identity IT teams manage employees' identities and access permissions from a central location, simplifying identity management and strengthening security posture. Also, Okta Workforce Identity integrates employee identity seamlessly across your security stack with features like Directory integrations and FastPass.
Pros
- The verification process with Okta Workforce Identity is very secure. Before providing access to employees, it double- or triple-verifies their identification, adding an extra layer of security to minimize the likelihood of cyberattacks and unauthorized access attempts
- Okta Workforce Identity allows your IT team to set permissions for employees, and with customization capabilities, they can even modify the access permissions with changes in employees' roles, like at times of mid-lifecycle change
Cons
- At times, the notifications are multiplied, such as when you receive multiple login notifications for a single login, which disrupts and delays the login or approval process
- Integrating Okta Workforce Identity with other applications is a difficult process that needs the involvement of technical expertise. Besides that, each app needs to be individually integrated with it, which takes time.
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
7. ARCON IDAM

ARCON IDAM is a cloud-based identity & access management solution that ensures the employee's overall employment tenure details are managed and maintained from a single platform. This assists IT admins in performing access certification and monitoring employees' access activity faster and more efficiently.
Furthermore, this ForgeRock alternative helps employees gain authorized access to business systems, applications, and data quickly, and they no longer have to wait to gain legitimate access, which enhances the employee experience.
Pros
- ARCON IDAM offers role-based access control, enabling IT teams to assign access rights to users based on their dedicated roles. It helps restrict access to authorized users, preventing unauthorized access attempts
- It allows IT teams to monitor employees' access activities, which helps identify suspicious activity and immediately freeze the user's screen or terminate the session, securing the crucial data
Cons
- The session terminates unexpectedly, disrupting the flow of work, and thus, you have to re-do the entire process from the beginning
- Sometimes, OTP validation fails, and you have to log in again, consuming more time and delaying the process of accessing apps
Customer Rating
- G2: 4.6 /5
- Capterra: 4/5
8. SailPoint Identity IQ

SailPoint Identity IQ is one of the prominent ForgeRock alternatives that custom-builts for complex businesses, as it seamlessly automates access requests, provisioning processes, and access certification. Also, IT teams can use SailPoint IdentityIQ, with its own library of connectors and integrations, to govern access to business systems and applications.
This ForgeRock alternative conducts regular audits, generates reports on which applications employees have access to, login attempts, and more, and keeps track of their access activities to prevent security breaches.
Pros
- Sailpoint Identity IQ allows you to create custom integrations using REST (Representational State Transfer) connectors and SCIM (System for Cross-Domain Identity Management)
- In one location, it manages all application access for employees, allowing them to search for apps to which they have access when they require without wasting time
- It provides you with a view to all access an employee has within the organization, making it easier to monitor access activities of employees like logins attempt and level of access permissions they have
Cons
- There isn't much insight on the request status, as it does not give alerts on updates or notify employees of application access request status
- To debug or troubleshoot problems, you need to have code-level knowledge, so businesses needs to outsource experts to deal with it which consumes additional cost
Customer Rating
- G2: 4.4/5
- Capterra: 4.2/5
9. Oracle Identity Management

Oracle Identity Management enables your IT team to manage the complete lifecycle of user identities. This ForegRock alternative provides scalable solutions encompassing identity governance, access management, and directory services.
This scalable solution helps your IT team enhance security measures and simplify compliance requirements. Furthermore, Oracle Identity Management is a constituent of the Oracle Fusion Middleware product family. It enhances agility, facilitates informed decision-making, and reduces costs and risks across various IT environments.
Additionally, Oracle Identity Management serves as a fully integrated service, delivering essential identity and access management functionalities through a multi-tenant Cloud platform called Oracle Identity Cloud Service.
Pros
- Oracle Identity Management enables your IT team to edit and move data from one location to another effortlessly with a few clicks. This eliminates the need for manual intervention and significantly enhances productivity
Cons
- The data transfer process is slow, presenting a notable challenge for your IT team, especially while transferring large volumes of data, such as transferring new employee data from HR to the IT system
Customer Rating
- G2: 4.1/5
- Capterra: 4.4/5
Opt For An Ideal IAM Platform To Effective Manage Your Access Environment
So, here you have it: an overview of 9 noteworthy ForgeRock alternatives. However, the ultimate decision rests in your hands as to which one to explore further. Nevertheless, the decision-making process should be guided by a thorough evaluation of factors such as cost, complexity, scalability, integration capabilities, automation features, and reporting capabilities.
Compiling a comprehensive list of feature requirements is recommended to ensure the selected tool effectively aligns with your organization's unique needs. This approach streamlines the selection process, enabling you to pinpoint vendors that align best with your requirements. By incorporating all these requirements into the list, you can ensure that the tool seamlessly integrates with your business requirements and priorities.
FAQs
How Does ForgeRock Work?
The ForgeRock Identity Gateway employs a Microgateway and DevOps approach to seamlessly enhance the security of your contemporary cloud and microservices applications. It does this without causing any disruption, and it's like having a smart control system that remembers and makes quick decisions about who can access what.
What Is ForgeRock Authentication?
The ForgeRock Authenticator (OATH) and OATH authentication modules receive one-time passwords created by the user's device. Meanwhile, the HOTP authentication module generates and delivers passwords to users through email or SMS.








.webp)
.svg)














