Many employees made the most of the work from home during the pandemic. While some opted for side gigs for additional bucks, others used their free time to look for more lucrative jobs.
On the other hand, many employees were relieved of their duty when companies decided to reduce the workforce to cut the losses and survive.
Whatever the case be, the HR & IT departments have been facing the heat of offboarding a good number of the remote workforce since then.
Before the pandemic, offboarding used to be a no-so-rosy affair, with a handful of the team members delivering the customary farewell speech. But the pandemic turned the tables and put the spotlight on employee offboarding practices.
It became the responsibility of each member: HR, functional head, IT head... to ensure that the employee is leaving the organization in all smiles.
They had to make sure that the employee wouldn't access the data, fudge with the details, and do anything to upset the security, and their corporate data was secure.
Whether it is intentional or accidental, data is sensitive, and breaches should not happen.
Moreover, ex-employees can add red flags by putting up bad reviews about the organization and thus tarnishing the brand value.
To understand what issues companies faced during the offboarding and how those issues were tackled, Zluri surveyed IT leaders to find out their perspectives on offboarding.
The Critical Findings from the Survey

- 58% of executives reported that offboarding processes have changed because of COVID-19 and an enforced remote workforce and have become more challenging. While 32% said the pandemic did not change the offboarding processes, 10% were not sure.
- Overall, 76% of execs agreed that employee offboarding represents a significant security threat—with access privileges being the biggest concern.
- Two-thirds (67%) of executives believe that employees exiting the organization are more likely to cause security breaches by accident than intentionally.
- Overall, 86% believe that security threats have changed due to a remote workforce being in place during COVID-19.
- Email decommissions (78%) and reacquisition of company hardware (77%) are the most common offboarding protocols for employees.
- Two-thirds now use software to guide offboarding, with 39% implementing internal tools and 27% using third-party tools.
- Most of them believe offboarding protocols are sufficient, but access management remains a priority.
- Overall, 77% believe that their offboarding protocols provide adequate security measures.
- Executives target access management (31%) over the next quarter, followed by process automation (26%).
During an employee offboarding, the most common processes include transferring the employee's job responsibilities, returning the office equipment, deactivating the access rights, passwords and conducting exit interviews.
While there should not be any loose ends when an employee leaves the organization, the offboarding process should flow naturally from the regular pattern of employee communication.
Challenges of Offboarding in The Digital Age

While the above may look very easy outwardly, essentially, it's challenging to achieve it seamlessly if the employee is working remotely.
Often what happens is employee offboarding is done hastily and casually. The employee user account is closed, and the company hardware and access cards are collected back.
But in a digital workspace, separated by time and distance as in remote working, where employees use several SaaS and other digital tools, offboarding requires a lot more than closing the user account. You need to take action to secure data touched by the employees.
These days' companies are using offboarding software for a better and efficient offboarding process. And the software can be internal or third-party tools for effective de-provisioning.
By de-provisioning, it means that you're deleting a user and removing their access from multiple applications and network systems at once. An organization initiates a de-provisioning action when an employee leaves the company or shifts to another role within the organization.
The Task of Deprovisioning

When companies introduced the Single sign-on (SSO), everyone felt a heave of a sigh as they were saved from the hassle of remembering 'n' number of passwords for each of their accounts.
While password-based systems work based on the human's capacity to recall complex passwords, SSO requires users to remember just one complex password.
Once a user signs in to SSO, he need not create or keep remembering different passwords for signing in to different apps.
SSO worked on authentication and authorization. While this enables a user to access the applications without the rigmarole of signing in every time, it also has its downside.
Once the IT administrator gives access to an employee to use an application using SSO, whenever the user tries to access the app—it gives the permission.
Though SSO can be considered advantageous over license key and password-based models, SSOs have specific challenges. And the challenges are critical at the time of de-provisioning as part of the offboarding process.
Once authentication and authorization are executed in the SSO model, the user can establish a connection with the app and continue for a session or a particular duration.
When the session is active, the user can perform multiple tasks without going through the authentication and authorization process. Unfortunately, it is one of the significant setbacks of SSO, especially when a disgruntled employee is being offboarded.
In the case of many others, they keep using it without realizing that they are committing a data breach. In many cases, the session is active not for hours but days or months. In several scenarios, the app overrides the SSOs, making things worse.
Another critical aspect of SSO is the data loss during the de-provisioning of users. For example, when an employee leaves the organization, a lot of the company's data is left as such. But it belongs to the company and has to be preserved.
The available ways are to take the backup of the data or transfer it to another user. But when a project is completed, a company needs to store the data, and unfortunately, such provisions are rare with SSOs.
It's here Zluri comes into the picture.
Zluri is an enterprise SaaS Management Platform that helps organizations discover, manage, optimize, and secure their SaaS applications from a single dashboard. Zluri enables the IT team to take complete control of their SaaS-based landscape.
The core value of Zluri is that it connects directly with the applications with which Zluri gets data directly from the source.
The Zluri Advantage At The Time Of Deprovisioning
When de-provisioning, Zluri monitors users for which apps they have access to and what level permissions they have, sign-in logs, audit, and access logs.
Here's a glimpse of Zluri's advantage over SSOs.
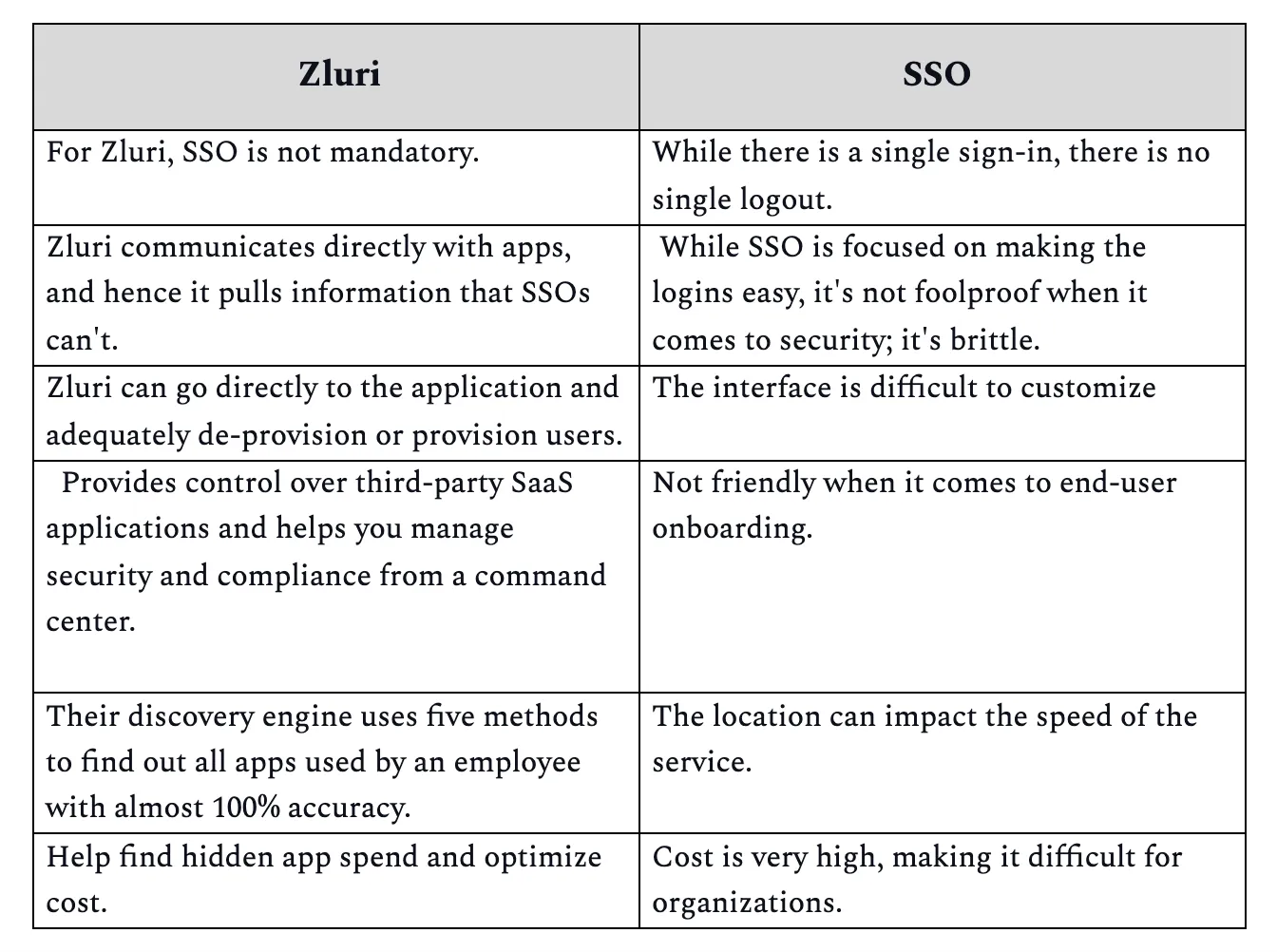
Now, let's look at the significant pros of Zluri in employee offboarding and de-provisioning.
- Zluri discovers your organization's subscriptions, along with the category and function of every application.
- Spot used and unused/underused apps and removed duplicate apps with overlapping functions.
- It removes unsecured apps and uses its direct integrations with 300+ apps for feature-level usage insights.
- It automates employee onboarding and offboarding functions. It's easy and can be done with a single click.
Zluri shows the way when it comes to de-provisioning at the time of employee offboarding. Here's how Zluri goes about the de-provisioning act.
Removal of access to devices: Zluri revokes authentication for the user from all the devices.
Data backup: Zluri transfers the data or takes a backup so that there is no data loss.
Revoke the user's license: Zluri removes the user from the application after the data backup has been taken.
SSO Removal: Zluri removes the SSO.
Zluri helps IT teams simplify, plan, secure, and get the most out of their SaaS application portfolio. With Zluri, you can take control of your cross-application stack and make employee offboarding a foolproof and pleasant experience.









.svg)














