As an IT manager, you know how vital it is to keep your cloud systems secure, and having a strong CASB solution is key. Citrix's CASB is a powerful tool that helps secure your organization's cloud activities and keep sensitive data safe.
However, your security requirements can evolve, prompting consideration of alternative options with enhanced functionality. So, let's explore some of the best Citrix alternatives that align more closely with your security needs and offer greater adaptability.
Citrix's CASB is a crucial platform for minimizing the risks linked to cloud-based applications and data. It provides the visibility and control necessary to protect sensitive information effectively. However, some drawbacks impede the efficient security of your cloud environment. For instance, the initial setup and configuration of the solution can be time-consuming, leading to delays in detecting security issues for your team. Considering this, it might be worth exploring Citrix alternatives.
This blog post lists the top 9 Citrix competitors to simplify your search. But Before delving into that, let's briefly assess its platform, features, and drawbacks, equipping you with the insights needed to make an informed decision later on.
Citrix CASB Platform: A Quick Look
Citrix's Secure Access is a CASB platform crafted to ensure the security of cloud-based applications and data, shielding them from potential security threats. Serving as a secure bridge between users and the SaaS apps employed within an organization, it establishes a protected connection to prevent unauthorized access to sensitive data.
One notable attribute of Citrix's Secure Access is its real-time visibility and control over the usage of cloud applications. Utilizing Citrix, you gain the ability to oversee all activities in the cloud and implement security policies, preventing unauthorized users from accessing sensitive data. This high level of visibility and control guarantees the continual protection of company data.
Beyond its strong security features, the service solution offers advanced threat detection capabilities. This enables prompt identification and mitigation of potential security threats. In short, Citrix's Secure Access ensures your organization's cloud-based resources are safeguarded with state-of-the-art security measures, providing peace of mind.
Key Features Of Citrix CASB Tool
Citrix CASB boasts a range of key features contributing to its effectiveness in securing cloud-based applications and data. Some of its notable features include:
- Visibility and Control: Citrix CASB provides comprehensive visibility into cloud application usage, allowing organizations to monitor and control data access effectively. This visibility empowers administrators to make informed decisions about security policies.
- Data Protection: The solution is designed to safeguard sensitive data by implementing robust security measures. Citrix CASB helps prevent unauthorized access to sensitive information, maintaining data integrity and confidentiality.
- Real-time Monitoring: Citrix CASB offers real-time monitoring capabilities, enabling organizations to identify and respond to potential security threats promptly. These advanced features are crucial for maintaining a secure cloud environment.
- Advanced Threat Detection: The CASB solution incorporates advanced threat detection mechanisms, allowing for the quick identification and mitigation of potential security risks. This proactive approach helps prevent security incidents before they escalate.
- User Activity Tracking: Citrix CASB facilitates tracking and monitoring user activities within cloud applications. This feature enhances accountability and aids in investigating security incidents by providing detailed insights into user interactions with sensitive data.
While offering a comprehensive set of features, Citrix also has some drawbacks.
Key Drawbacks Of Citrix CASB Platform
Below are some potential limitations associated with the tool, encouraging you to explore Citrix alternatives and competitors.
- Complex Setup and Configuration: Setting up and configuring the tool can be intricate, requiring a significant investment of time and expertise to ensure a proper and effective implementation. This complexity may pose challenges for users not well-versed in the tool's intricacies, potentially leading to delays in deployment and adoption.
- System Slowness: Users may experience delays when accessing critical applications or files due to occasional system slowness. This can result in decreased operational efficiency and, in more severe cases, may lead to periods of downtime. The impact on productivity makes addressing and resolving these slowdown issues crucial for maintaining a smooth workflow.
- Manual Refresh Requirement: The tool lacks an automatic refresh feature, meaning that updates must be manually initiated. This manual refresh requirement can be time-consuming and introduces the risk of overlooking important updates. Thus, users may not work with the most current information, potentially impacting decision-making and overall system effectiveness.
- Software Update Challenges: The tool faces challenges in updating seamlessly. This difficulty can result in connectivity issues, diverting attention from strategic tasks. Instead, time and effort may be directed toward troubleshooting and resolving problems arising from outdated software. This hampers operational efficiency and shifts the focus away from more value-driven and forward-looking activities.
Having explored the limitations, let's explore essential factors when choosing the best alternative to the Cirrix CASB tool.
Essential Factors To Consider When Choosing Citrix Alternatives
When exploring Citrix alternatives, it's crucial to consider several key factors to ensure that the chosen solution aligns seamlessly with your organization's needs. Here are some essential factors to consider:
- Functionality and Features: Assess the range of features offered by potential alternatives. Consider whether they align with your organization's specific needs, including virtualization capabilities, application delivery, and remote access features.
- Ease of Integration: Evaluate how well the alternative integrates with your IT infrastructure. A smooth integration process minimizes disruptions and ensures a more efficient workflow.
- Performance and Scalability: Examine the alternatives' performance capabilities and scalability, especially in accommodating your current and future business growth. A solution that can scale with your organization is crucial for long-term success.
- User Experience: Prioritize the user experience to enhance productivity. Look for alternatives that provide an intuitive interface, seamless access to applications, and reliable performance for end-users, whether in the office or working remotely.
- Security Measures: Security is paramount. Evaluate the robust security features of potential alternatives, including encryption protocols, access controls, and threat detection capabilities. Ensure the solution aligns with your organization's security standards and compliance requirements.
- Cost Considerations: Analyze the total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance expenses. Compare these costs across different alternatives to make an informed decision that aligns with your budgetary constraints.
- Vendor Reputation and Support: Research the reputation of the vendors offering Citrix alternatives. Choose a vendor with a track record of reliability, strong customer support, and a commitment to ongoing product development and improvement.
- Flexibility and Customization: Consider each alternative's flexibility and customization options. The ability to tailor the solution to your specific business requirements can significantly impact its effectiveness in meeting your organization's unique needs.
- Compatibility with Devices: Ensure that the chosen alternative supports a variety of devices and operating systems. This compatibility is crucial for accommodating diverse work environments and ensuring user accessibility.
- Scalability: Anticipate future growth and evaluate how well the alternative can scale to accommodate increased demand for resources and services. Scalability is vital for adapting to the evolving needs of your organization.
By carefully evaluating these factors, you can make an informed decision when choosing Citrix alternatives that best align with your organization's goals, IT infrastructure, and user requirements.
Before we dive into the tools, let us introduce ourselves and demonstrate how Zluri can protect your SaaS infrastructure.
0. Zluri
Zluri, as a SaaS management platform, plays a vital role in identifying, tracking, and managing your organization's complete SaaS landscape. Utilizing five advanced discovery methods ensures a thorough 100% discovery of all SaaS apps within your organization. Once identified, Zluri offers comprehensive security and compliance information, ensuring adherence to all compliance requirements.

The platform provides detailed insights into events, shared data, and compliance and security probes related to SaaS applications. This empowers you to work towards achieving compliance while concurrently meeting your security objectives.
As per Kuppingercole's report, Zluri also keeps you informed about events concerning your apps during their usage. We actively source this information from various online channels and present it in a centralized location called \"Events.\" This includes critical updates, security vulnerabilities, data breaches, and other relevant news that may impact your SaaS applications.

Establishing connections between apps can result in different access levels to the connected app's data, ranging from read-only to write, modify, and delete access. The degree of threat escalates with the sensitivity of the data accessed by an app. For example, an app that can access Google Drive with the capability to modify or delete files is considered a high-level threat.
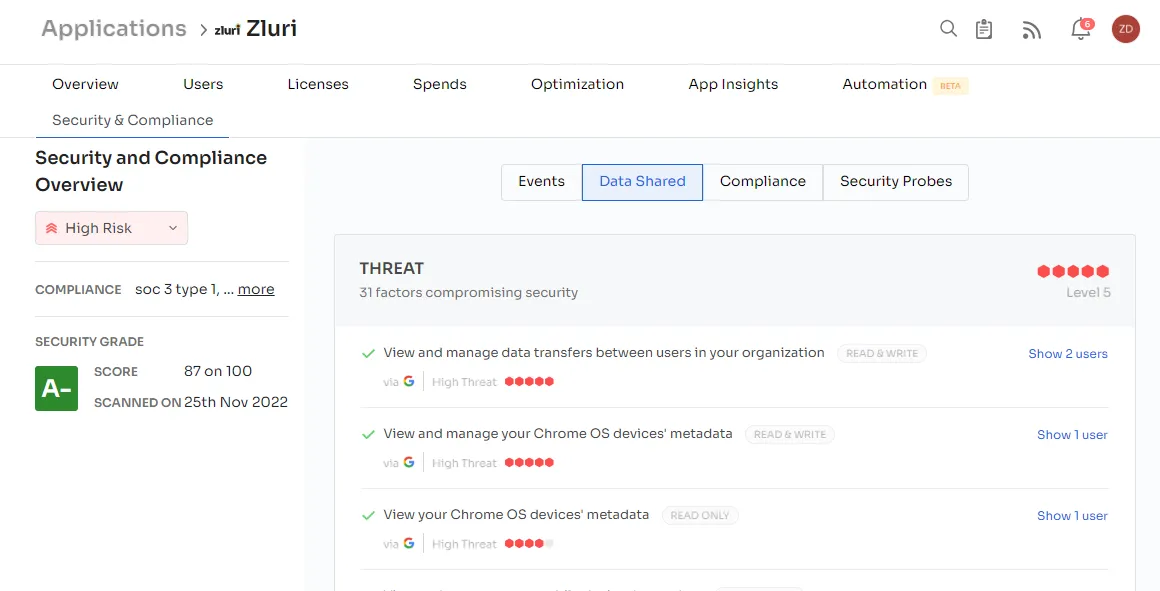
Zuri offers in-depth compliance information for each app, outlining its adherence to specific compliance frameworks. This feature simplifies the assessment of your SaaS applications' compliance status, ensuring alignment with your organization's regulatory requirements. Additionally, Zluri employs a risk-scoring system that considers the number of compliance frameworks an app follows. The higher the count, the greater the app's risk score, indicating lower non-compliance risk and an improved overall compliance posture.
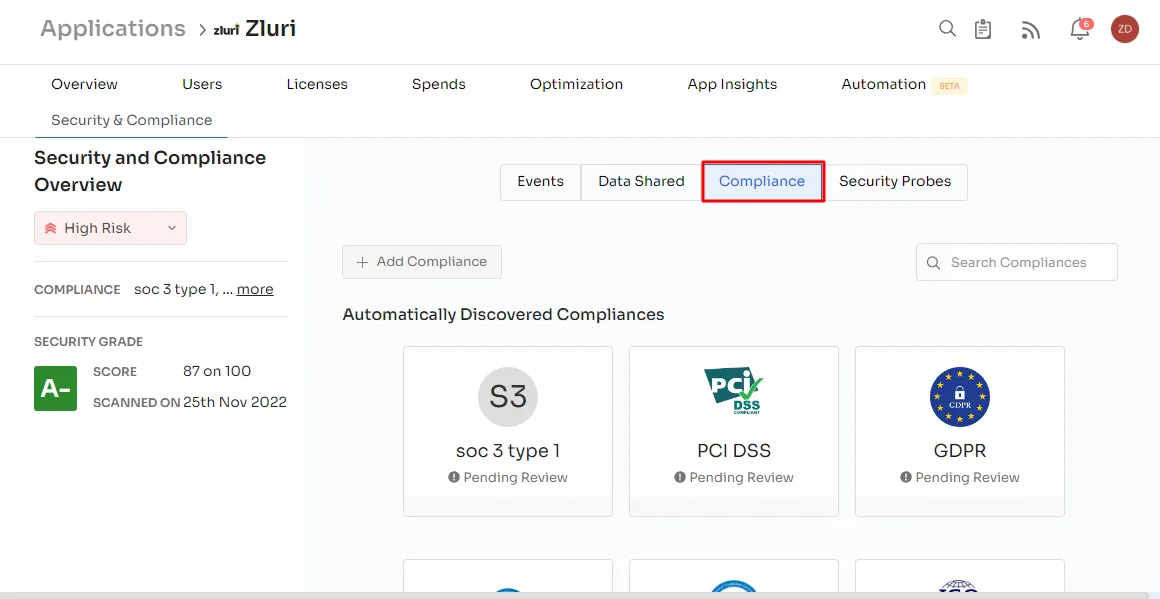
Furthermore, the platform conducts monthly technical scanning through security probes tailored to your organization's needs. Zluri prioritizes the security of your sensitive data, employing robust encryption algorithms. This ensures the safety of your data with a comprehensive, auditable log of key security-related activities.
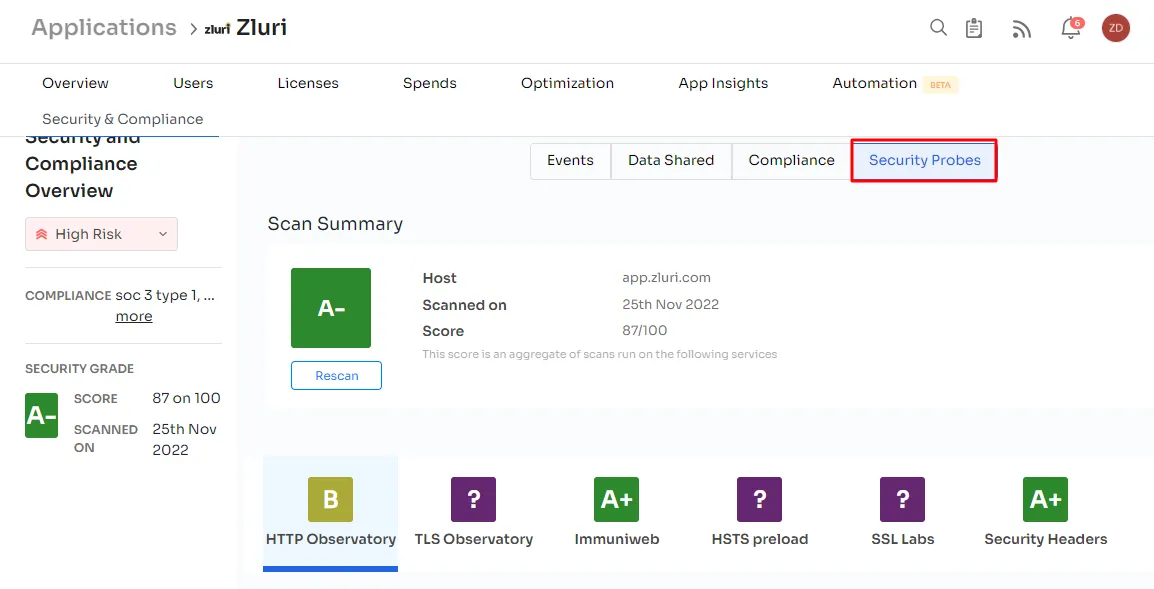
All collected data, including SaaS-app usage metrics, is retained indefinitely, encrypted, and backed up for 60 days to ensure constant accessibility.
Zluri goes the extra mile by offering a view of critical apps with high threat levels and risk scores. It also provides alerts against using critical apps that may jeopardize data confidentiality, helping you take necessary precautions for enhanced organizational security.

In addition to its strong security features, Zluri offers key benefits that empower you to efficiently oversee your SaaS applications.
Key Highlights of Zluri:
- SaaS License Optimization: Zluri simplifies the tracking, identification, and reporting of SaaS licenses, offering a consolidated view for a comprehensive insight into your SaaS stack. This automation helps monitor employee SaaS usage, identify redundant apps, and ensure compliance, ultimately saving costs and enhancing security.
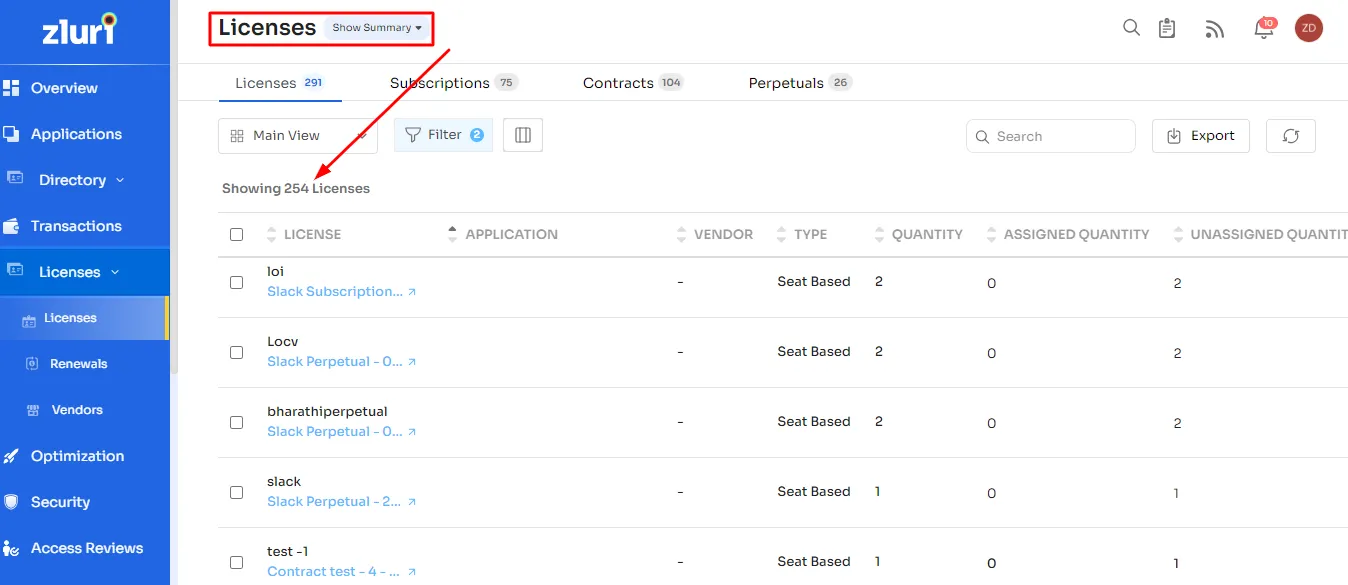
- Furthermore, Zluri facilitates the right-sizing of SaaS licenses based on usage and business requirements, optimizing costs and aiding informed decision-making.
- Elimination of Shadow IT: Zluri boasts a vast app library and employs nine discovery methods. This robust approach eradicates shadow IT by identifying 100% of your SaaS apps, providing a comprehensive understanding of your organization's digital landscape.
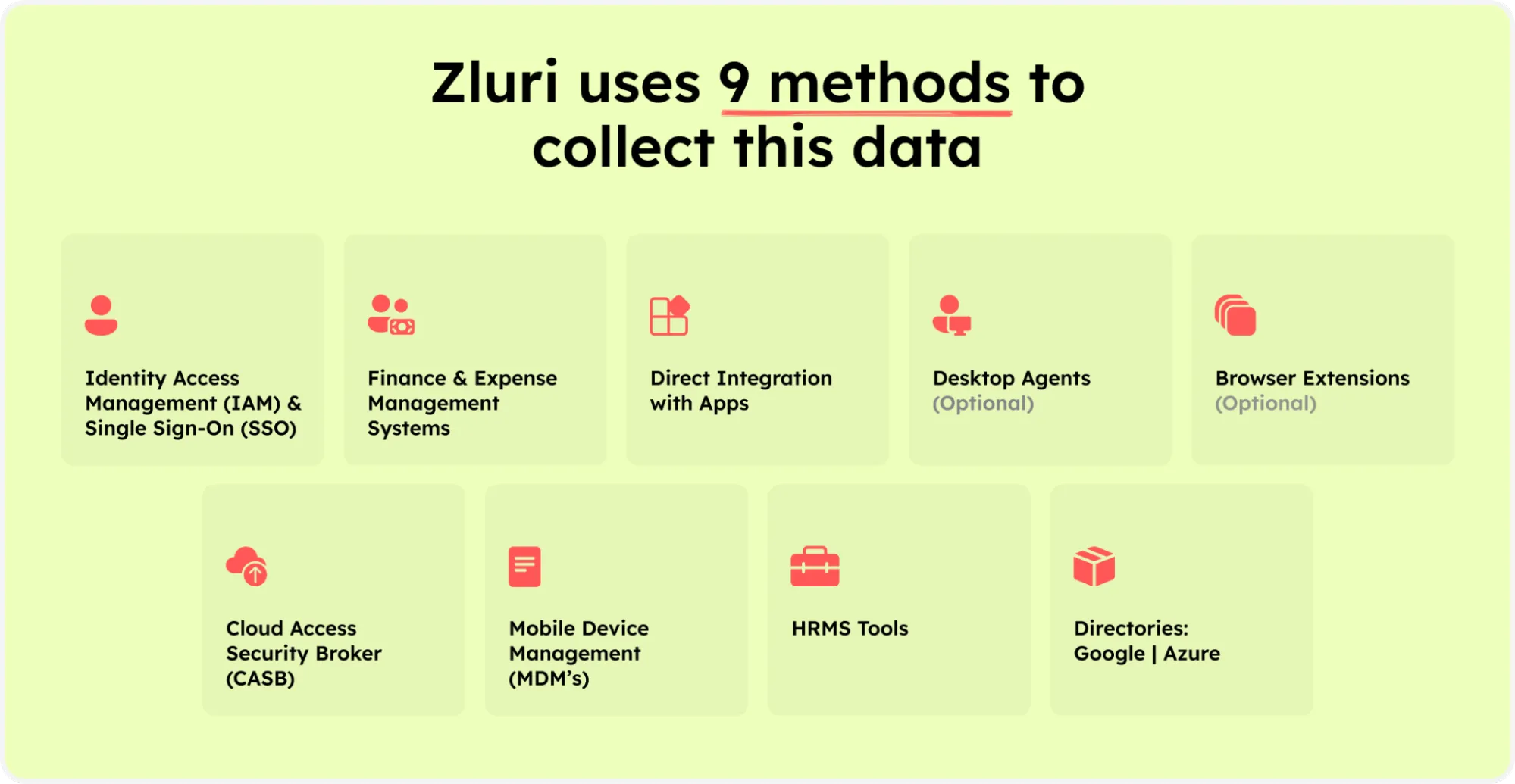
Zluri’s nine discovery methods
- Vendor Management: Zluri acts as a centralized hub for vendor contracts, offering streamlined access to metadata. This centralized approach optimizes spending, facilitating contextual storage for convenient renewals, audits, and negotiations. It enhances control over vendor relationships and ensures comprehensive management.
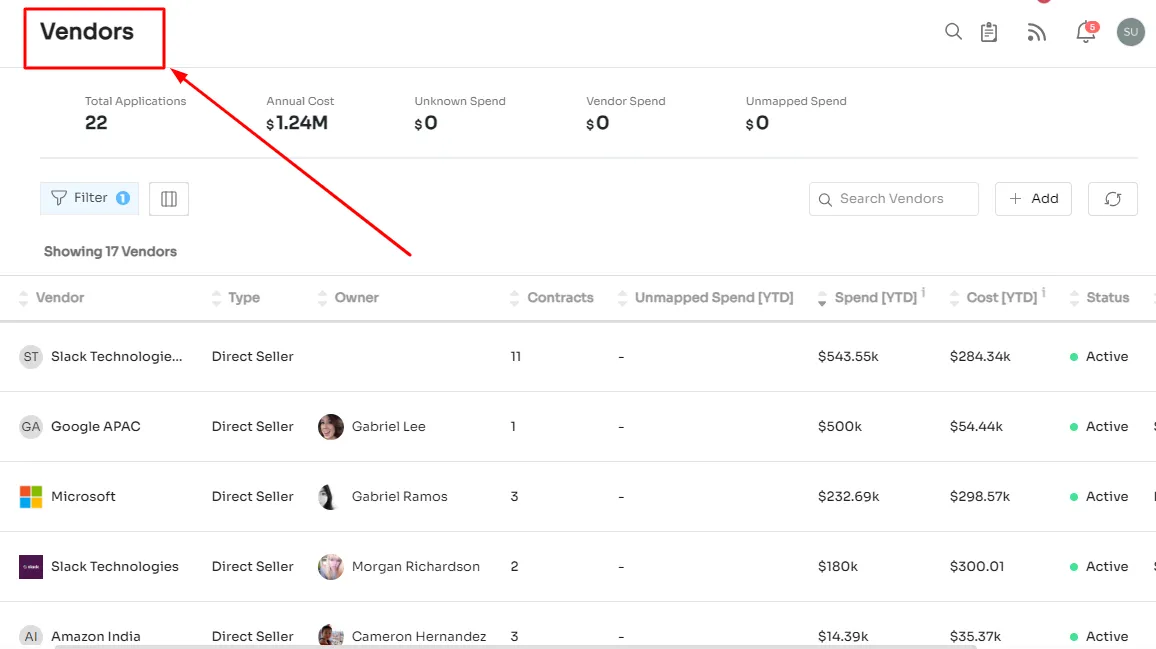
- SaaS Renewal Management: Zluri simplifies renewal through timely notifications and alerts. IT teams gain enhanced control over renewals, facilitating prompt actions, negotiations, and cost avoidance. This feature ensures a proactive approach to renewal management.

- Application Cost Optimization: Zluri enables users to monitor and control SaaS expenditures with efficient filters. Users can identify high-cost, low-usage apps, allowing for strategic decision-making to optimize costs and resource allocation effectively.
- Spend Optimization Report: Zluri's detailed report provides insights and recommendations for optimizing SaaS spending. With 22 real-time reports covering usage, expenditure, and security risks, organizations can make informed decisions, leading to better spending practices and improved financial efficiency.
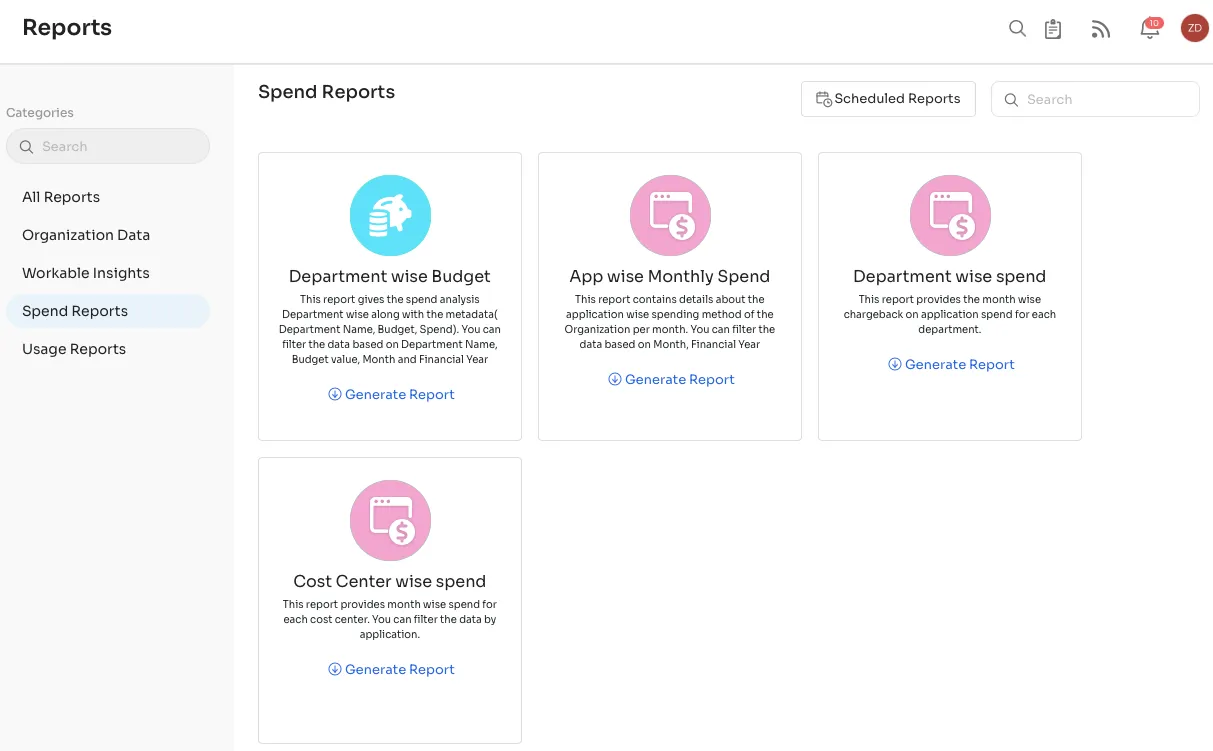
- Intelligent Insights and Analytics: Zluri delivers intelligent app insights, analytics, and trends. This feature empowers data-driven decisions, allowing organizations to optimize resources for enhanced efficiency. It provides a comprehensive view of app performance and usage trends for strategic planning.
Customer ratings
- G2: 4.8/5
- Capterra: 4.9/5

Discover a revolutionary standard in SaaS management with Zluri. Schedule a Demo Today!
List Of 9 Best Citrix Alternatives To Secure Cloud Access
As organizations increasingly pivot towards dynamic digital workspaces, the demand for the best Citrix alternatives that ensure secure and seamless cloud access has never been more critical. The below list unveils each alternative to Citrix for those seeking robust and reliable options in 2024. Let us explore them:
1. Netspoke’s CASB
Netskope's Cloud Access Security Broker (CASB) is a cybersecurity solution offering a holistic perspective on cloud services, applications, and user activities. This comprehensive view is instrumental in maintaining the safety and security of your cloud operations. Accessible from any location and device, this cloud-based solution operates on a data-centric approach, carefully balancing robust protection with optimal speed for a secure cloud transformation journey.
In the realm of threat protection, Netskope adopts a multi-faceted strategy. Utilizing the capabilities of Cloud Access Security Broker (CASB), a secure web gateway, and a sophisticated multi-layer threat detection and remediation system, Netskope comprehensively establishes a shield encompassing cloud and web services. This robust defense mechanism safeguards against a spectrum of threats and vulnerabilities, enhancing the overall safety of the digital landscape for organizations leveraging this platform.
Netskope facilitates the easy management of various cloud platforms, including popular ones like Office 365, Box, and Dropbox. It equips users with risk assessment and threat discovery tools, improving visibility and ensuring compliance with security rules.
Pros
- This solution offers improved insight into applications and data hosted in the cloud. This heightened visibility enables you to promptly pinpoint potential security threats, empowering you to proactively address and minimize these risks
- The platform's user-friendly deployment process facilitates a swift initiation of its functionalities. This ease of deployment eliminates the need for prolonged and intricate implementation procedures, allowing you to swiftly experience the advantages of the system
Cons
- If you're a small-sized organization, this software won't fit your IT budget, as it has a high implementation cost
- Additionally, the software's steep learning curve not only restricts its full utilization but also extends the time required for users to master its complete functionality
Customer ratings
- G2: 4.4/5
- Capterra: 4.8/5
2. Proofpoint’s Cloud Security
Proofpoint is a leading provider of cybersecurity and compliance solutions for enterprises. One of their key offerings is their Cloud App Security Broker (CASB), which would provide you with complete visibility and control over their organization's cloud environment.
With so many employees working from home and accessing cloud applications from various devices, you need to know who is accessing what data and when. Proofpoint's CASB platform offers real-time visibility into cloud activity, providing detailed insights into user behavior and data usage.
This can help them detect and prevent security breaches and identify areas where employees may need additional training or support.
Pros
- The tool allows you to create security rules as per your needs and set up custom alerts, allowing you to stay flexible to meet your organization's security requirements.
- The platform helps you ensure that your organization is compliant with data protection regulations, such as GDPR and CCPA, by providing visibility and control over cloud activity
Cons
- The tool gives false positives, where legitimate user activity is flagged as suspicious or malicious, resulting in an additional workload for your IT admin to investigate and remediate false alarms
- The tool is complex to implement and manage, requiring you to have a high level of technical expertise and additional training
Customer ratings
- G2: 4.4/5
- Capterra: 4.1/5
3. Lookout’s Cloud Security
Lookout Cloud Access Security Broker (CASB) stands as a robust solution dedicated to elevating cloud application security and mitigating data breach risks. This advanced CASB delivers extensive visibility into cloud applications, actively defending against both external and internal threats. With Lookout CASB, organizations comprehensively understand user interactions, endpoints, cloud applications, and data, facilitating real-time threat detection and response capabilities.
As a trusted mobile and cloud security solution provider for businesses across various scales, Lookout safeguards your cloud environments and data from cyber threats. The solution maintains continuous vigilance over your cloud environments, employing machine learning and advanced analytics to identify and respond to potential security threats in real-time.
Beyond threat detection, Lookout assists in fortifying your cloud configurations by scrutinizing your cloud infrastructure for misconfigurations, vulnerabilities, and compliance issues. This holistic approach ensures a proactive and adaptive stance towards securing your organization's cloud assets.
Pros
- Lookout's interface is user-friendly, making it easy for you to navigate and manage your organization's security settings
- It offers mobile device management features, which allow you to monitor and manage the security of your employees' mobile devices
Cons
- The software can be expensive as only a premium price can give you full security features. As a result, you will need to weigh the benefits of Lookout's features against the cost of the software
Customer ratings
- G2: 4.2/5
- Capterra: 4.7/5
4. Cisco Cloudlock

Cisco Cloudlock, one of the prominent Citrix alternatives represents an advanced cloud security platform offering real-time visibility and control across a spectrum of cloud applications, spanning SaaS, PaaS, and IaaS. It empowers users with valuable insights into data access and sharing dynamics, facilitating rapid detection and response to security threats.
Cloudlock streamlines security management across all cloud applications and data as a centralized platform, enabling IT administrators to reduce risk and proactively prevent data breaches. By leveraging Cloudlock, security teams can efficiently oversee access permissions, monitor data usage, and prevent unauthorized data exposure, all from a unified interface.
Moreover, Cloudlock provides granular controls for data sharing, allowing users to establish policies governing which data can be shared and with whom. This capability empowers organizations to maintain control over sensitive data, effectively mitigating risks associated with data sharing.
Pros
- With Cloudlock, it is easy to investigate any security issues when an alert occurs, making it easy for you to resolve the issue and secure the organization's IT environment
- The email sent to the users is straightforward and contains only the required information, allowing you to identify the problem and resolve it quickly
Cons
- As a premium cloud security solution, Cisco Cloudlock comes with a higher price tag compared to other similar solutions, impacting your organization's IT budget
- The advanced capabilities of Cisco Cloudlock lead to a steeper learning curve for your team, requiring you to dedicate additional time and resources to training and implementation
Customer ratings
- G2: 4.5/5
- Capterra: 4.5/5
5. Forcepoint’s CASB
Forcepoint CASB solution is amongst one of the notable Citrix alternatives that is crafted to offer instantaneous visibility and control over cloud applications, facilitating swift detection and prevention of security threats and data breaches.
Highlighting advanced DLP capabilities, the solution identifies and prevents data breaches by detecting sensitive data and implementing policies to hinder unauthorized access. The granular control provided by Forcepoint's CASB extends to governing access permissions and thwarting unauthorized data sharing within cloud application usage.
Augmenting its capabilities, the solution incorporates potent threat detection features, utilizing advanced analytics and machine learning to pinpoint anomalous activity and promptly mitigate threats in real time. Also, the solution provides DLP capabilities to enable you to identify and prevent data breaches. This remote access tool can detect sensitive data and apply policies to prevent unauthorized access.
Pros
- The solution is easy to deploy and manage, allowing you to quickly start securing your organization's IT infrastructure and manage it from a single console
- It provides insights into cloud usage and security risks, helping you to make informed decisions and improve your security posture
Cons
- The solution does not offer sufficient security capabilities when it comes to CASB integration and Google Cloud integration, limiting your ability to detect issues entirely
- Initially, the solution's licensing is a challenge, leading you to waste time that could be used to focus on other important tasks
Customer ratings
- G2: 4.5/5
- Capterra: 4.6/5
6. Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is a security solution and one of the notable Citrix alternatives that assist in protecting an organization's IT infrastructure from advanced threats that target cloud-based applications. As more and more organizations move their operations to the cloud, the need for advanced cloud security solutions like Microsoft Defender for Cloud Apps has become more critical than ever.
The solution detects and prevents threats in real-time. This powerful security solution uses advanced machine learning algorithms to analyze user behavior and detect potential threats before they can do any harm.
Pros
- Microsoft Defender for Cloud Apps is included in Microsoft 365 E5 and Microsoft 365 Defender, making it a cost-effective solution for organizations that already have a Microsoft 365 subscription
- It provides complete visibility for managing security policies across multiple applications, making it easier for you to enforce security policies and stay on top of potential threats
Cons
- The alerts sent are delayed compared to the actual activity that occurred, resulting in a delay for your team in detecting and resolving the problem
Customer ratings
- G2: 4.4/5
- Capterra: 4/5
7. iBoss Cloud Platform
iBoss cloud platform is a cloud security solution and one of the prominent Citric alternatives that helps you secure cloud-based applications and data in your digital workspace. It provides cloud access security broker (CASB) capabilities that enable you to monitor and control access to their virtual applications and data, ensuring that only authorized users can access sensitive information.
With iBoss, you can set policies and controls to ensure that data is protected, even if accessed from outside the organization's network.
Also, iBoss can identify and block potential threats in real-time, helping you stay one step ahead of attackers. This enables you to keep the cloud-based applications and data safe and secure, even in a major cyber attack.
Pros
- It offers a central management console, which makes it easy for you to monitor and manage their network security
- The reporting capabilities of the software are advanced, making it easy for you to get a complete picture of the security posture of the organization
Cons
- It is difficult to implement the granular security rules initially, which requires your team to have the technical expertise and leads to a rise in the overall IT budget due to additional resource
- It is expensive, especially if your organization has a limited IT budget. However, the cost can be justified if you avail of the advanced security features
Customer ratings
- G2: 3.6/5
- Capterra: 4.2/5
8. Palo Alto Networks Next-gen CASB

Palo Alto Networks is a provider of cybersecurity solutions, and their Next-gen CASB is a powerful tool for securing cloud applications and data. It provides complete visibility into cloud usage, allowing you to track user activity, detect threats, and enforce policies across multiple cloud services.
Moreover, the software offers advanced data protection features such as encryption, data loss prevention (DLP), and access control to secure sensitive information.
Also, Palo Alto Networks' Next-generation CASB uses advanced machine learning and behavioral analytics to detect and prevent cyber threats such as malware, phishing, and data exfiltration.
Pros
- With Next-gen CASB, you can apply granular policies to cloud services, including activity-level policies, data-level policies, and user-level policies, enabling you to protect sensitive data, enforce security protocols, and prevent data leakage
Cons
- The solution is complex to implement and configure, requiring significant time and resources, and may require specialized skills and expertise
Customer ratings
- G2: 3.5/5
- Capterra: 4.4/5
9. Zscaler’s Data Protection
Zscaler is a leading provider of cloud security solutions, and their CASB (Cloud Access Security Broker) solution offers powerful data protection capabilities. It combines traditional CASB functionality with advanced security features such as machine learning and behavior analysis.
Zscaler CASB provides complete visibility into cloud usage, allowing you to track user activity, detect threats, and enforce policies across multiple cloud services. It automatically classifies sensitive data and applies policies based on sensitivity, ensuring only authorized users can access it.
Further, it uses advanced encryption technologies to protect sensitive data at rest and in transit. It also uses machine learning and behavior analysis to detect and prevent cyber threats such as malware, phishing, and data exfiltration.
Pros
- It is easy to use and requires no special skills or training, allowing you to quickly set up policies and rules to protect your cloud applications
- It gives protection for cloud applications, whether they are sanctioned or unsanctioned, empowering you to be confident that your organization's data is secure, no matter where it is being accessed
Cons
- If your organization is small or medium-sized, then this solution is not a suitable fit as it is expensive compared to other tools
- The solution's reporting capabilities are not efficient, which makes it difficult for you to get insights into threat detection
Customer ratings
- G2: 4.7/5
- Capterra: 4.2/5
Choosing The Ideal Citrix Alternatives For Your Organization
As we conclude our overview of the top 9 Citrix alternatives, it's important to know that picking the right tool needs careful evaluation. To make a good decision, you should understand your organization's needs and look closely at available options. The best alternative should not just work for you now but also be able to change as your organization grows and faces new challenges.
Consider how well the Citrix alternatives and options work, whether it can grow with your needs, how easy it is for people to use, how safe it keeps your information, and if it fits your budget. Make sure it fits smoothly with what you're already using, and think about what might happen in the future. Also, check out what people say about each option to make sure you're making a smart choice. By doing this, you'll be all set to pick a Citrix alternative that doesn't just meet but goes beyond what your organization needs in the ever-changing world of IT solutions.
FAQs
1. What criteria were considered when selecting the top Citrix alternatives for 2024?
The Citrix alternatives were carefully chosen based on various factors such as functionality, ease of integration, scalability, user experience, security features, cost considerations, vendor reputation, flexibility, and compatibility with virtual desktops, various devices, and operating systems.
2. How do I know which alternative to Citrix best fits my organization's specific needs?
Consider your organization's unique requirements, such as virtualization needs, application delivery preferences, scalability demands, and user experience expectations. Evaluate how well each Citrix alternative aligns with these criteria to make an informed decision.
3. Are these alternatives suitable for businesses of all sizes, or are they more tailored to specific industries?
The listed Citrix alternatives cater to a range of business sizes and industries. Each alternative has its strengths, so assessing your organization's size, industry-specific needs, and growth plans is essential to find the most suitable option.
4. How does the cost of these alternatives compare to Citrix, and are there any hidden fees to be aware of?
The total cost of ownership varies among Citrix alternatives, including licensing fees, implementation costs, and ongoing maintenance expenses. Review the pricing structures of each alternative to understand their costs comprehensively, and be sure to inquire about any potential hidden fees.
5. Can these alternatives seamlessly integrate with existing IT infrastructure, or will compatibility issues occur during the transition?
Most of the top Citrix alternatives are designed to integrate seamlessly with existing IT infrastructures. However, it's crucial to assess the compatibility of each solution with your specific environment, ensuring a smooth transition and minimal disruptions to your workflow.









.svg)














