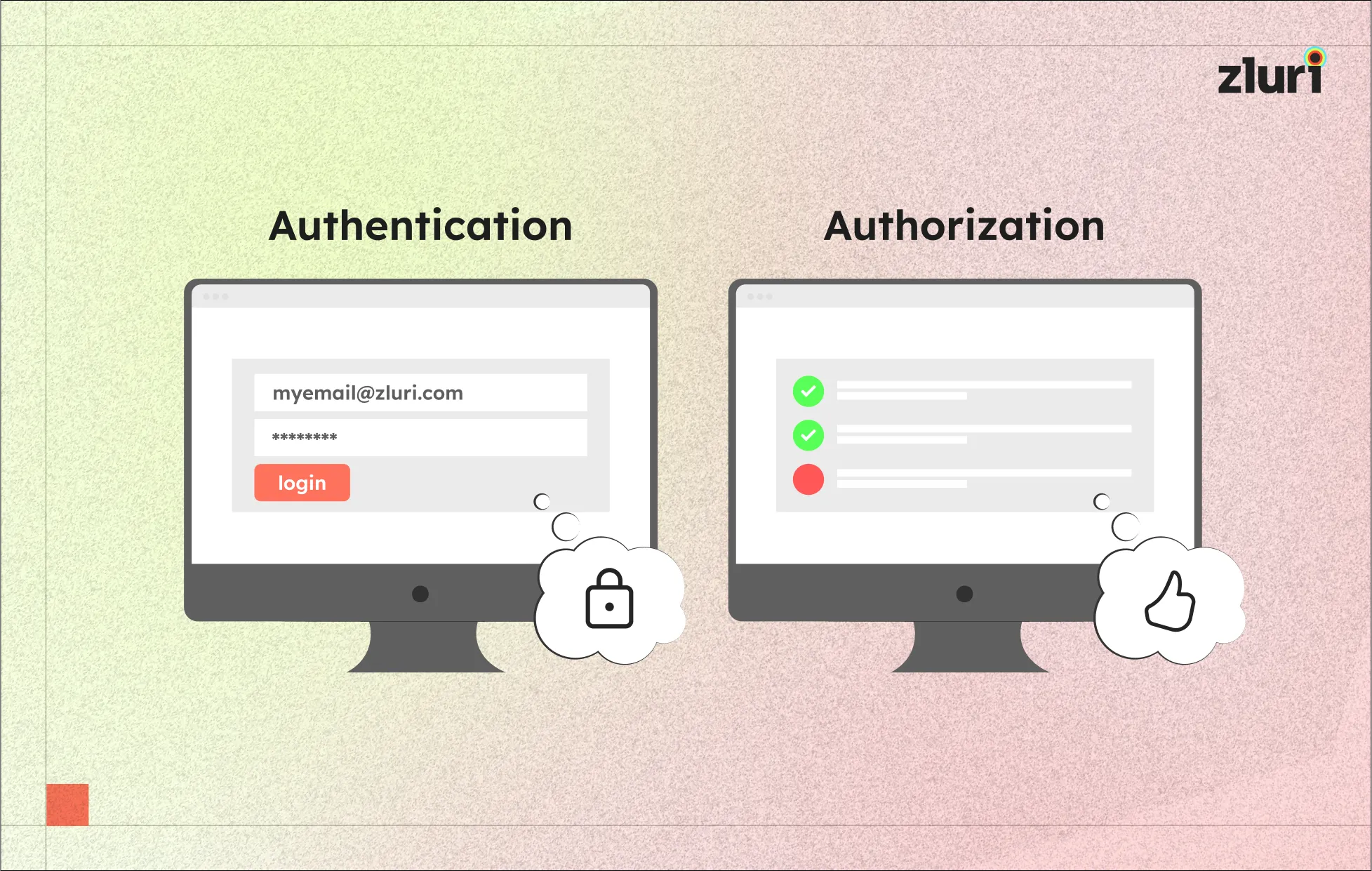
Authentication and authorization are security practices used by IT admins to safeguard organizations' systems and critical information. Although similar, they serve distinct but equally essential functions in protecting SaaS apps, data, and other resources.
In this article, we'll explore how these security practices (i.e., authentication vs authorization) differ and their role in securing an organization's resources.
Authentication and authorization are often used interchangeably. This is because both practices control and manage access to resources within an organization. Despite sharing common objectives, they use distinct methods to achieve them.
So, let's find out what methods authentication and authorization use and what sets them apart.
What Is Authentication?

Authentication, also known as \"authn,\" is a process that involves verifying a user's identity before granting access to networks, applications, critical data, accounts, systems, and other resources. In this process, a user submits a form of identification, usually a username, and then validates their identity by providing proof such as a password, biometric data, or token. This mechanism helps ensure access to specific systems and data is restricted to authorized users only.
Note: Users can use these three forms of authentication to verify their identity:
- Something you know: It can be PIN, password, or any security question and answer.
- Something you have: It can be a virtual token like a time-based one-time password (TOTP).
- Something you are: It can be biometric characteristics like fingerprints or facial recognition (retina scan).
For example, in an organization, employees must enter their login credentials to authenticate themselves and access any application, device, or system.
What Is Authorization?

Authorization, also known as \"authz,\" is a process that involves defining the level of access a user has to system resources, including applications, data, and networks. Once a user is authenticated, the IT admin determines what level of access permissions a user should hold within the organization.
For example, IT teams authorize employees to access certain files and apps necessary for their role but restrict them from accessing files designated for managers.
Authorization controls access to organizational resources, ensuring unauthorized users cannot gain access.
After going through the definition of authorization and authentication, you may have a brief understanding of their differences. However, we've compared them based on distinct parameters to provide more clarity.
Authentication vs Authorization: Comparison Based On Different Parameters
Below, we have differentiated both the security practices (i.e., authentication vs authorization) in detail to help you clearly understand what distinguishes them.
1: Purpose
The first comparison factor between authentication vs authorization lies in their primary objectives.
- Authentication ensures users are who they claim to be. It also prevents unauthorized users from accessing the system, which further helps keep an organization's sensitive information secure.
- On the other hand, authorization's ultimate aim is to ensure users' access rights or permissions are effectively and accurately managed (grant, modify, and revoke access as required). This helps ensure users hold the right level of access necessary for their roles and responsibilities and nothing beyond throughout their lifecycle.This prevents unauthorized access and potential security breaches as it helps keep users out of areas or functions they shouldn't be in.
2: Techniques Applied
In the context of authentication vs authorization, different methods are employed to achieve their respective goals.
- There are 5 methods of authentication, which are:
- Password-based authentication: This is the simplest form of authentication. It requires a password associated with a specific username. The user is successfully authenticated if the username and password match the system's database.
- Passwordless authentication: The user does not need a password in this method. Instead, they receive a One-Time Password (OTP) or link on their registered mobile number or email. This is also known as OTP-based authentication.
- 2FA/MFA: Two-factor authentication (2FA) or Multifactor Authentication (MFA) is a more secure authentication method. It requires additional verification, such as one-time PINS or answers to security questions, to authenticate the user.
- Single Sign-On (SSO): Single Sign-On allows users to access multiple apps with a single set of credentials. Once users sign in, they are automatically signed into all other web apps linked to the same centralized directory.
- Social Authentication: This method uses existing credentials from social networks to verify the user without requiring additional security measures.
- Whereas there are 4 methods of authorization, which are:
- Role-Based Access Control: RBAC provides users access to resources based on their organizational roles and privileges.
- Attribute-Based Access Control: ABAC grants users access to the organization's systems based on various attributes. It uses attributes related to the user, environment, and resources to decide if the user meets the criteria for accessing specific resources.
- Mandatory Access Control: MAC uses a set of predefined security labels to restrict individuals' ability to access data.
- Discretionary Access Control: Unlike MAC, DAC grants privileges based on the user and their access group. Here, the resource owner can grant access to other users as needed.
3: Responsibility
In the context of authentication vs authorization, the responsibilities differ between the two processes.
- The user carries out the authentication process. They need to provide a form of identification or authentication, such as a password, fingerprint, or security token, to verify their identity and gain access to apps, data, and the system.
Note: The form of authentication that users need to provide depends on the specific system in place.
- The IT team is in charge of the authorization process. They act as gatekeepers, determining who has access to specific resources within the organization. They configure permission levels, determining what users can see, change, or use. Unfortunately, users cannot modify their access level on their own after it's been set by the IT team. However, they can request an access change, and the IT team will verify the need and accordingly grant them access.
4: Entry Procedure
In the context of authentication vs authorization, the entry procedure involves distinct steps for each process.
- During the authentication process, users need to provide an ID token, such as a password or fingerprint scan, which the system checks against its records (database) to confirm their identity. And then provide them entry to the organization's network.
- Once a user's identity is verified and they are allowed in (network access granted), they need further permission to access specific areas or resources. This is where users need to provide access tokens, which might be a temporary code generated upon login. This token reflects the permissions assigned to users by the IT teams during authorization. If the access token matches the user's permission level, they are further granted access to the resources they need.
5: Identity And Access Management
In the context of authentication vs authorization, both processes play critical roles in Identity and Access Management (IAM).
- Authentication enables your team to verify the identity of users attempting to access the organization's network and other computing resources. This practice helps ensure that only authorized users can access the organization's IT assets, preventing unauthorized users from accessing and compromising data, damaging systems, or causing disruptions.
How does the authentication process work?
The authentication process involves transferring credentials from a human to a machine during network interactions to verify the user's identity. It happens in two ways:
- User authentication: To verify themselves, the user (human) provides valid credentials or details like a username and password to the device (like a computer).
- Machine authentication: This happens automatically, without users needing to take any action. For instance, a guest account on a computer that lets you in straightaway.
Note: Authentication applies to both wired and wireless networks, granting access to systems and resources connected to the Internet or network.
- Meanwhile, authorization enables your team to control, manage, and secure access to SaaS apps, data, and other corporate resources.
How does the authorization process work?
IT teams usually set up a detailed authorization system that doesn't give everyone access to all resources. Instead, access is given based on job roles, which means employees can only access the resources needed for their work. Limiting access to what's necessary for each role minimizes the risk of damage from security breaches or cyber threats.
After going through the differences between authentication vs authorization, you may be confused about which security practice to implement. Let's find out the answer to this question.
Strike A Balance: Implement Authentication & Authorization Together
Strong authentication, like complex passwords or multi-factor authentication, is necessary, but it is not enough on its own. For example, if a hacker breaches into your organization's system by stealing your users' passwords, they can immediately hamper your critical data.
But with a two-layer defense, which means implementing both authentication and authorization, you can create an extra layer of security.
Even if unauthorized users or hackers bypass the initial security system, they wouldn't have the necessary \"keys\" (permissions) to access sensitive areas or cause harm within the system. This way, you can minimize the impact of potential breaches.
In short, to strengthen your digital security, you need both authentication and authorization to work together. This layered approach will help ensure that only authorized individuals gain access, reducing the risk of data breaches and system disruptions.
However, to implement these security practices effectively, you will need an automated access management solution like Zluri in place. What is Zluri? How does it work? Here's a quick brief.
Zluri: Your Go-To Solution To Authenticate & Authorize User’s Identity & Access
Zluri's advanced access management solution helps your team seamlessly authenticate users' identities and grants them authorized access to organizational resources. But how does it do that?
- Assigns Digital Identity To New Users Upon Onboarding
When a new employee joins a company, Zluri's system creates a digital identity for them. But how? Zluri's system integrates with the organization's HRMS, which contains all the necessary information about employees, such as their name, role, department, and contact details.
During onboarding, Zluri's system automatically fetches all relevant data associated with the new employee from the HRMS. This includes details like job title, department, and other information. Using the fetched data, the new employee is assigned a digital identity.
- Authenticates The Identity Before Granting Access
Once your IT team has assigned new employees a digital identity, they create accounts for them with Zluri's access management. This allows your team to efficiently grant, modify, or revoke access by verifying employees' digital identities before providing the necessary access.
- Enforces Access Control Policies
Zluri's access management helps your team enforce different access control policies, including SoD, RBAC, PoLP, and just-in-time access.
By implementing these access control policies, they can ensure that only authorized users hold access to the right resources and nothing beyond that.
- Thoroughly Monitor Access Activities
Zluri's access management enables your team to monitor all access activities within your organization. Including which user has access to which applications, their status as active or inactive, what permission level they hold, and more.
Your team can also identify access patterns and user behavior by tracking users' access activities. This will help prevent security breaches and uphold a well-governed and secure environment.
To learn more about Zluri's access management, book a demo now.
Frequently Asked Questions (FAQs)
What Comes First: Authentication Or Authorization?
Authentication always comes before authorization. First, the system verifies the user's identity (authentication) and then checks what the user can access (authorization).
What Is An ID Token And How It Is Used In Authentication?
An ID Token is a piece of data sent from the authentication server to the organization's system that confirms the user's identity. It is used to validate that the user has successfully authenticated.
What Is An Access Token & How Is It Used In Authorization?
An access token specifies the permissions granted to a user. The system uses it to determine what resources and actions the user can access.









.svg)














