Access request management is an essential subset of the identity management lifecycle. It includes evaluating, approving, or denying user requests to interact with organizational resources.
This process requires more than just identifying the requester and their access needs. It's a balancing act between ensuring the organization is safe and ensuring things run smoothly.
That’s what the access request management tool does. It is a modern, reliable, and almost foolproof way for an organization to manage user access.
Access request management is a part of IT security operations that prevent unauthorized users from accessing and stealing potential organizational data. It stores user information, their roles, the teams they belong to, and the policies that must be implemented.
This can be tedious and time-consuming as admins are responsible for several processes, including provisioning, deprovisioning, enforcing data rights, access governance rules, and the least privilege principle. They are also responsible for ensuring that audits are ready and security and privacy rules, both domestic and international, are followed.
It is easy to understand how labor-intensive, time-consuming, and expensive access request management can be when considering hybrid ecosystems and manual processes. IT teams have to evaluate these risk factors across a wide range of legacy and new technologies and changing regulatory pressures from the various compliance standards. CCPA (California Consumer Privacy Act), SOX (Sarbanes-Oxley Act ), and the GDPR (General Data Protection Regulation) are some examples.
After evaluating a request, IT or application administrators must manually add the requester to a role, create an application account, or add the user to a group. To eliminate any human error, Identity and Access Management tools are the current solution that are dependable for controlling access to every user in the organization.
These tools allow administrators to swiftly view, certify, grant, and revoke user access and actively enforce organizational regulations. The provision of tools makes these capabilities possible. The tool handles user access requests by evaluating the user's profiles and roles.
The tools help to speed up admin operations by ensuring that newly hired and third-party workers can quickly take up their responsibilities by having access to required tools and resources.
Additionally, the tools regulate the conditions under which users are given or refused access to those resources. This helps to protect important organizational data even more.
This article discusses the 10 best Access Request Management Tools that manage users’ access requests to software applications, third-party resources, or any external services the organization utilizes.
10 Best Access Request Management Tools
An access request management tool that allows self-service access requests makes security and compliance easier by enforcing digital identities. It also keeps track of the entire IT ecosystem.
A contemporary solution that includes an online request form and a fulfillment engine might improve service. This shortens approval timelines and expedites the process of approving or disapproving based on recommendations. The amount of labor required of requesters and approvers is decreased through an automated, standardized process, which increases worker productivity.
Let’s explore our first tool Zluri.
1. Zluri
Zluri is a SaaS management platform that automates the access management process with Employee app store. Employees can seek a license or tool access through the employee app store and track the progress of those requests. Employees can also request new ones if the apps they desire aren't included in the SaaS stack.
To obtain a more lucrative offer than most IT and procurement teams can obtain on their own, this purchase request can also be directed to Zluri's SaaS buying department.
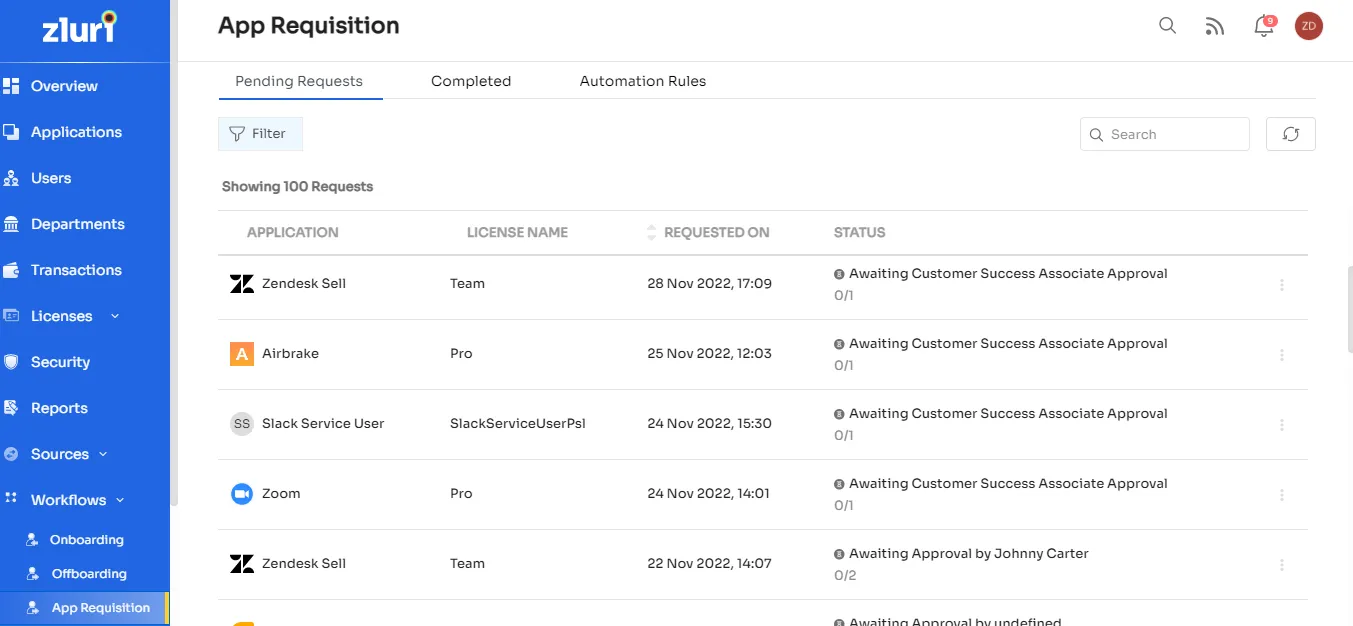
It provides an easy-to-use web portal that allows users to request access to applications they need and keep track of what's happening. Requests are automatically sent to the right people for review, approval, and access management.
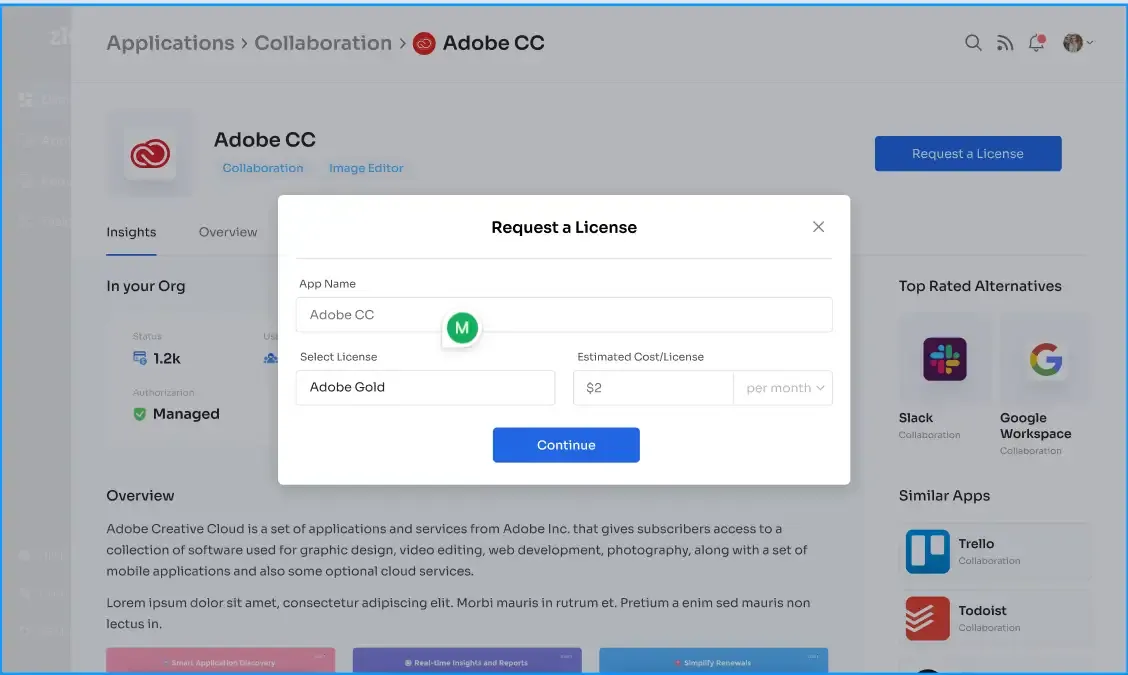
Approvers can easily get detailed information about user requests, which gives them a clear and simple view of access requests and their context. It streamlines onboarding, offboarding, and role management for more efficiency, security, and compliance. It makes sure that users only get access to what they need.
The dashboard for the employee app store is filled with all of your company's apps. The use of specific applications and which apps are used in a department can be found by employees. This makes it easier for workers to select the best apps for their needs.
The IT staff can now automate the SaaS approval process, set the number of approvers, and choose which apps and app data will be made visible or hidden to specific departments and employees. For IT teams, this saves a tonne of time, and since every SaaS purchase is public, shadow apps cannot enter.
Employees receive information that aids in the complicated decision-making process over whether or not to purchase SaaS, such as details about security and compliance as well as other app options. This saves the time that would have been required to research the app's details and make a judgment call. It supports staff mid-lifecycle management in this way.
Due to Zluri's seamless integration with more than 300 different SaaS apps, employees can begin utilizing the apps as soon as the license is approved.
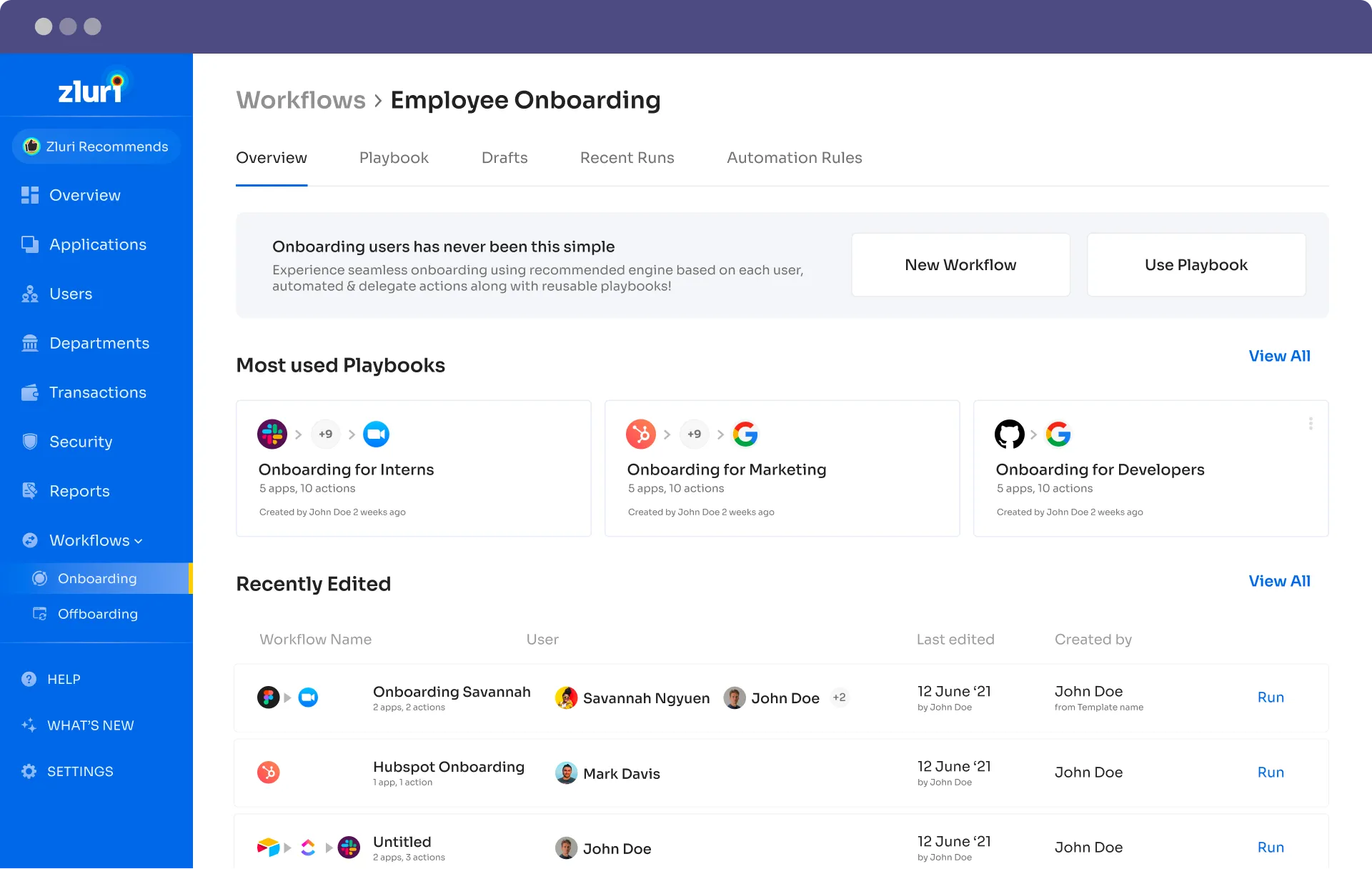
Apart from this, Zluri provides seamless automation for employee onboarding and offboarding. IT/HR teams no longer have to manually onboard new SaaS users, which is time-consuming and demanding. They can provide access to all the work tools on the 1st day of onboarding or even before and also provide access to new apps and tools for a new position.
Zluri eliminates SSO and monitors its usage system during deprovisioning. It checks user sign-in, audit, and access logs to see which apps they may use and how much access they have to each.
Zluri ensures that an employee's access to all the applications they were using, not just their SSO or Google workspace account, is terminated when they leave the organization. Zluri creates a backup of all the data from such apps before the licenses expire, which you can subsequently pass to a new owner.
2. Oracle
Oracle Identity Cloud Service works well with hybrid cloud architectures and is especially useful for managing identity and access in multi-tenant scenarios.
The platform's user portal can be modified to meet the requirements of companies that want to assign straightforward tasks to end users via an intuitive website. It offers a sizable API that may be used to link customized programs that lack built-in integrations.
The Oracle Identity Manager makes adding and removing data users from an organization simple. Because of capabilities like password management, policy administration, report, and auditing tools, Oracle IAM regularly provides data on access and user activity and analytics that may be used to enhance security features.
Key features
- A self-service interface allows users to seek access to certain data or apps, which team leaders or supervisors must approve.
- Due to the self-service interface, customers have complete control over their own identity profiles.
- Policy management solutions allow access providers to set access levels using role-based and attribute-based policies.
- Access providers have more flexibility in giving password rules, such as granting lighter limits to users with less access while recommending privileged users retain strong passwords.
- Administrators can apply the attestation tool to verify user access regularly.
3. CyberArk
CyberArk technologies offer security features without slowing down your workforce. Its AI-powered technology and other intelligent technologies enable fast, safe, and reliable access.
It works well with many small to large enterprises like Microsoft Active Directory (AD), LDAP, and Google Workspace. The platform leverages AI-backed Adaptive Multi-Factor Authentication. Using behavior-based strategies, you can monitor and restrict access to mission-critical applications using various secondary authentication techniques and AI.
This alternative also has a clear dashboard where IT admins can immediately spot failing integrations, potential risks, and other issues.
Key features
- Cyberark's SSO lets users log in once to any device or app.
- This SSO improves password security.
- AI-powered facial and fingerprint recognition provides access without passwords.
- It provides a lifecycle management solution that helps security managers control access creation and termination.
4. Sailpoint
SailPoint is another IAM provider that uses straightforward integration wizards and pre-established workflows to enable enterprises to connect, on average, up to 99% of all their current applications and data. The AI portion of the product is known as Predictive Identity. Customers can purchase Predictive Identity and integrate it with the rest of IdentityIQ immediately, adding this capability later or not at all.
It lets access providers and users manage their profiles and access rights on an easy-to-use platform. The IdentityIQ compliance manager improves compliance and audit performance by providing tools like audit reporting, analytics, and automated policy administration.
Key features
- The lifecycle manager handles self-service access requests and automates provisioning.
- The password manager makes it easy and quick for users to keep track of their passwords.
- It improves risk management by centralizing identity data, roles, policies, risks, and business processes.
- Customers can use any device to access and manage their accounts.
- IdentityIQ's identification intelligence makes it easier for security managers to identify problems and gives them tips on improving their work.
5. IBM Security Verify
The IBM Security Verify is a cloud-based identity and access management solution that lets you manage your employees' and customers' identities and access in one place. It helps protect your organization by modernizing IT and integrating identity into zero-trust projects.
IBM Verify gives your online services an extra layer of security. Even if the malicious hackers steal your password, the IBM’s two-step verification keeps your account safe.
Key features
- The unified user management feature makes it easy to add and remove users and grant or revoke access.
- Multi-Factor Authentication (MFA) can be made available to all account users, including those without federated IDs..
- Users with an IBMid are granted a one-time passcode that is time-based (TOTP).
6. Auth0
Auth0 is one of the world’s leading cloud authentication services that enable enterprises to deliver safe access to any application for any user. It is a highly customizable platform, i.e., it can be as basic or flexible as the development teams want. It provides an out-of-the-box experience in setting up authentication for your web application. Also, Auth0 offers a feature-rich dashboard for managing users, multi-factor Authentication, SSO integration, and additional security measures.
By safeguarding multiple login transactions monthly, Auth0 delivers convenience, security, and privacy so customers can focus on innovation.
Key Features:
- Auth0 supports third-party authentication technologies.
- It helps you manage control access via any device.
- The Auth0 platform allows employees to provide access even when they aren't connected to the local area network.
- Auth0 comes with a self-service password function that allows users to change their passwords without authorization from their employer.
7. PingIdentity
You can try your hands on the Ping Identity tool to manage access features in hybrid, multi-generational, and multi-cloud systems. It has a user-friendly platform that allows users to securely access the cloud, mobile, SaaS, and on-premises apps and APIs via any device.
No-code automated workflows help orchestrate the authentication setup process and unify remote access based on identity intelligence, password-less sign-on, and centralized authentication. Ping is a good option for financial institutions due to the large number of accounts supported.
Key Features
- Ping provides a centralized access security solution for web applications, mobile applications, and APIs.
- It provides users with the most scalable and high-performing identity and profile data store.
- You can manage hybrid IT or multi-cloud systems without installing, updating, and managing separate on-premises proxies and agents.
8. OneLogin
With secure one-click access to all enterprise cloud and on-premises apps for employees, clients, and partners via all device types, OneLogin streamlines identity management. By removing users from Active Directory, OneLogin can enforce IT identity policies and promptly deactivate app access for workers who leave or change roles.
Control application access, swiftly on- and off-board team members, and give end users convenient access to all of their applications across all devices. You can quickly expand your on-premises security model to the cloud. Get rid of significant identity policy management inconveniences and costs.
OneLogin effectively extends identity policies to the cloud while cutting down on expensive identity infrastructure investments and difficult integration tasks for each new app. Long-term provisioning and integration efforts are not necessary with OneLogin.
Key Features
- Enables the synchronization of users across several directories, such as Workday, Active Directory, LDAP, G Suite, etc.
- Smart factor authentication stops illegal access to secure data.
- Identity lifecycle management allows administrators to automate the onboarding and offboarding of users and applications.
- Supports multiple directory integrations for on-premises and cloud directories and SAML-based identity provider sign-in.
9. Okta
Okta, a pioneer in the SaaS-based IAM market, is a vendor-neutral platform that functions well despite the infrastructure technologies in use. Okta is mainly known for customer IAM and is building a solid workforce IAM market base for both enterprise cloud and hybrid cloud environments.
Okta has made it easier for users to access applications on any device whenever required while still enforcing strong security policies. It integrates with an organization’s existing directories and 4,000+ applications. As a result, organizations can implement the service quickly at a large scale and at a low total cost.
Key Features
- Okta offers a modern SSO.
- You can avoid data breaches and credential theft with adaptive multi-factor authentication.
- It uses high-security directories to ensure that user data is safe.
- The identity engine from Okta allows you to customize your authentication, authorization, and registration.
10. RSA SecurID
The platform's diverse deployment choices make RSA SecurID Suite a suitable solution regardless of the environment—on-premises, hybrid cloud, or totally SaaS. This is especially relevant if an enterprise needs MFA flexibility. Additionally, this solution has every capability required by bigger businesses, including the following:
- SSO
- Identity and lifecycle management
- Identity governance
Key Features
- Utilize technologies like identity insights, threat intelligence, and business context to provide your users with safe and secure access across your applications and devices.
- Any SaaS, cloud and web-based application can use it.
- All user actions are monitored and recorded by the user activity tracking tool.
- The administrator may use the password management tool to manage, authenticate, and reset passwords.
- Enables password-free authentication using SSH keys and other types of verification.









.svg)














