With potential security risks rising in today's IT environments, IT admins are looking for a next-gen identity & access management solution that can address the challenges of operational disruption, such as the issues caused due to security risks.
With the right access control practices, organizations can become more secure and more efficient, save costs and solve problems like data breaches, mismanagement of data, and unauthorized user access.
Access control systems and processes limit access to sensitive information, such as customer information, employee data, intellectual property, trade secrets, operational or inventory information, and industry-specific data. They also limit access to information processing systems, transaction processing, and custom software.
The consequences of flawed access control can be devastating to a company. An unauthorized person can not only view unauthorized content but can change or delete the content, perform unauthorized functions, or even take over site administration.
Hence access control is important, and when implemented effectively, they mitigate the risk of information being accessed without proper authorization.
10 SaaS Access Control Best Practices
Adequate access control is crucial for securing an organization's data. The sensitive data can be misused or lost if the company's rules are too permissive. Here are ten best access control practices that can help IT teams secure their organization's critical data.
1. Centralization of SaaS Inventory
Centralization is one of the most overlooked access management practices. By centralizing the access management, IT admins can keep an eye on users, applications, databases, data traffic flows, and more.
Legacy identity management solutions can't possibly provide the centralized view required to manage all information at once. Hence organizations require a solution that centralizes control, views all information, and monitors authority over users' identities.
When a lot of activities are happening at once, IT admins should get broader visibility across all identities. It becomes difficult to have a 360-degree view of identity security on a large scale.
A centralized system will provide visibility into resources and applications access, user behavior, and anomaly tracking across the organization. For this, the IT admin will need to select an identity security solution that can provide this centralized view of every user identity.
Zluri, a SaaS management system, does its best with 100% accuracy. It uses five discovery methods to automatically make and update SaaS inventory.

Read more about the working of the Zluri discovery engine here.
2. Zero Trust Identity Security
Zero trust identity security states that an organization's security shouldn't trust any application or user under any circumstances. The organization's systems shouldn't trust anything that tries to connect to the company's network and databases. This means constantly verifying any user legitimacy before giving access.
Zero trust is a network security framework, and it is becoming essential to every organization. The zero-trust strategy is based on identity security. A successful identity-centric zero trust model relies on the principle of least privilege, which ensures that all users get the least amount of access to do their job successfully.
The number of employees working from the outside of the corporate network had increased post-pandemic, which resulted in the usage of multi-devices across various applications. It is thus now important for organizations to fully embrace zero-trust access management in order to increase the protection of critical systems like ERP and finance systems.
3. Role-based Access Control

Role-based access control refers to restricting an organization's employees' permission to access based on the role they have within the business infrastructure. It only allows users to access what they require to perform their job.
For example, an ordinary employee of an accounting office shouldn’t have access to digital finance accounts, so his/her access to them should be restricted.
Role-based access control also guides to facilitate identity security, cybersecurity, and business processes. The employees of the organization should be assigned clear, delineated roles as a part of access management best practices; this will then help to establish who can access what within the organization.
It's important that no employee should receive permissions outside their roles; if projects demand the assignment of temporary privileges, the IT admins should make sure that those privileges are expired within a set time limit.
4. Give Least Privileged Access
The principle of least privilege is based on privilege access. It is an important access management practice for organizations but is often most neglected. It works to limit the privileges the users possess in the IT environment.
The principle of least privilege states that workers should only possess the access necessary to perform their job processes. The role-based access focuses on identity governance, whereas the principle of least privileged focuses on the initial permissions granted.
One of the major benefits of applying the principle of least privilege is the decrease in harm in case of a malicious entity getting into the organization. For instance, if a system is infected by malware and if this system is part of an organization that follows the principle of least privilege, then it will not be able to spread to other computers. This means that the chances of viruses, worms, or rootkits being executed reduce because most of the other employees don't have the admin rights that enable their installation.
5. Automated Onboarding and Offboarding
Onboarding and offboarding of employees in an organization come under identity security. When onboarding a new contractor, vendor partner, or employee, IT teams need to access the privileges and permissions that the individual should be granted based on their unique roles.
This can be extremely complex for large organizations, especially if there is only a manual provisioning process. Due to the number of employees and projects, this often leads to a high margin of error.
With identity security solutions, IT organizations can automate onboarding and offboarding processes. This saves the IT department time and money. It increases productivity by ensuring that new employees have the right access they need from day 1 of joining.
It also reduces risks by quickly deprovisioning employees' access when they leave the company or move to another department.
With Zluri, you can create playbooks for onboarding and offboarding.
It gives contextual app recommendations on what app the new joiner will need.
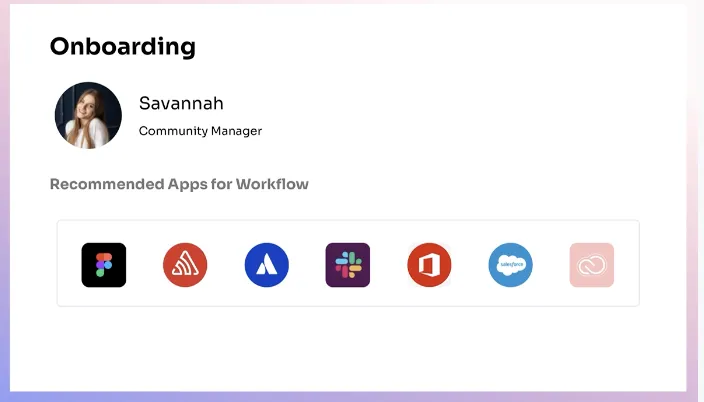
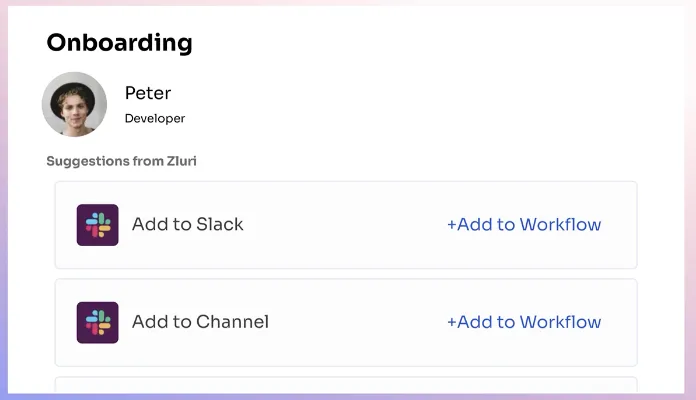
It also gives in-app suggestions like what project, workspace, and channels to add them to and sends greeting messages as soon as they join.
Zluri allows you to deprovision users in 1 click.
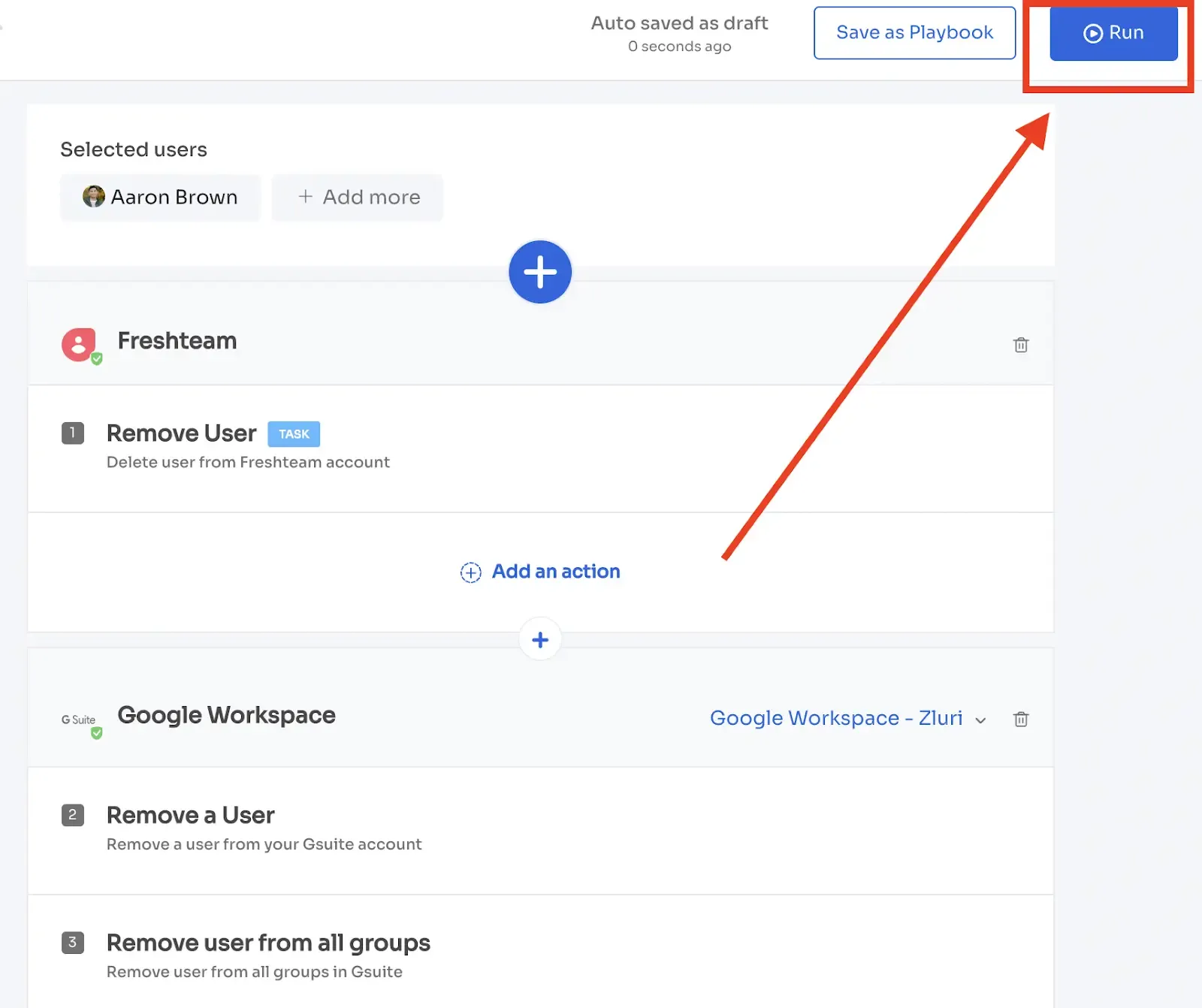
Zluri one-click deprovisioning
Zluri protects the company's data by deprovisioning employees from all the apps they were using. It helps you revoke access from all the apps the employee had access to rather than just their SSO or Google workspace and secure the organization's data from unauthorized users.

While terminating the licenses of the users, Zluri takes a backup of data in those apps so that the admin can transfer it to the new joining owner. The offboarding process is based on three steps processes: retrieval, revoke and reassign.
6. Multi-factor Authentication
The single-factor authentication schemes mostly depend on passwords, which are consistently proven unreliable for an organization's identity security. Hackers can easily crack, guess or circumvent password-based logins.
Employees often use weak passwords or repeat their passwords across multiple sites. This bolsters cyber attacks.
Employees are often uncomfortable using a password-based single-factor authentication system, as passwords can be forgotten. It also requires time and resources to recover a password.
Therefore it is necessary for organizations to deploy and maintain multi-factor authentication as a part of their access management practices. The more steps IT admins add between the access request and digital access, the more secure it remains.
Multi-factor authentication steps can include geofencing, biometrics, time for access request monitoring, hard tokens, password, and SMS messaging.
7. Orphaned Account Detection
There is constant change occurring in every organization, particularly regarding the workforce. When an employee moves to a different department or leaves the organization, the user access to that individual's account needs to be adjusted or removed from the network. Failure to deprovision or remove these accounts can lead to the accumulation of orphaned accounts.
Orphaned accounts contain the previous user's data but no longer have an assigned user. Such accounts can be hacked. The hackers can gain the credentials and take on the identities of the previous users. This leads to security breaches and attacks.
Therefore, organizations need to seek identity and access management solutions that help discover and remove orphaned accounts in their network. The solution should be able to automate and mandate the offboarding process to ensure no orphaned accounts slip past the identity security.
Zluri helps you eliminate the problem of SaaS ownership. It helps you manage SaaS ownership in collaboration with other departments and individuals.
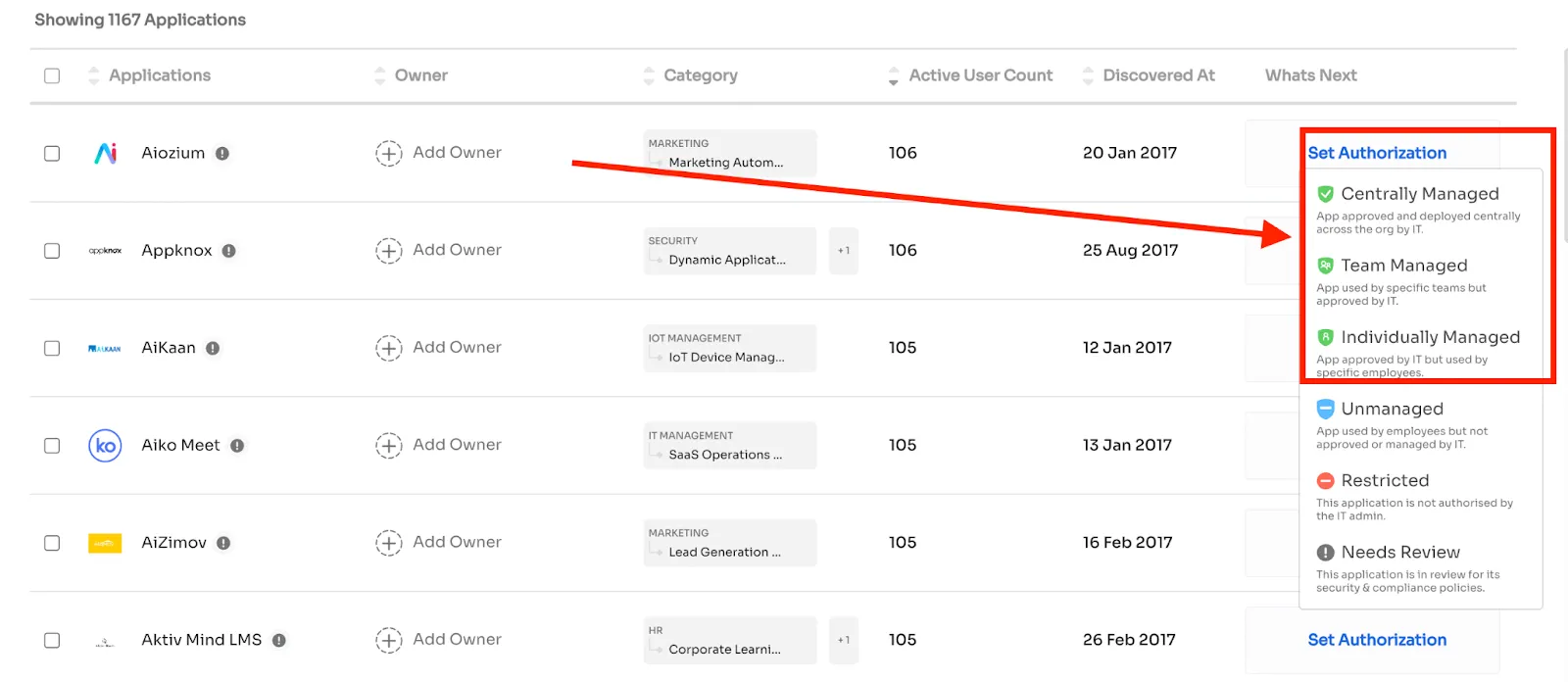
You can have centralized ownership, department-wise ownership, or even individual ownership.
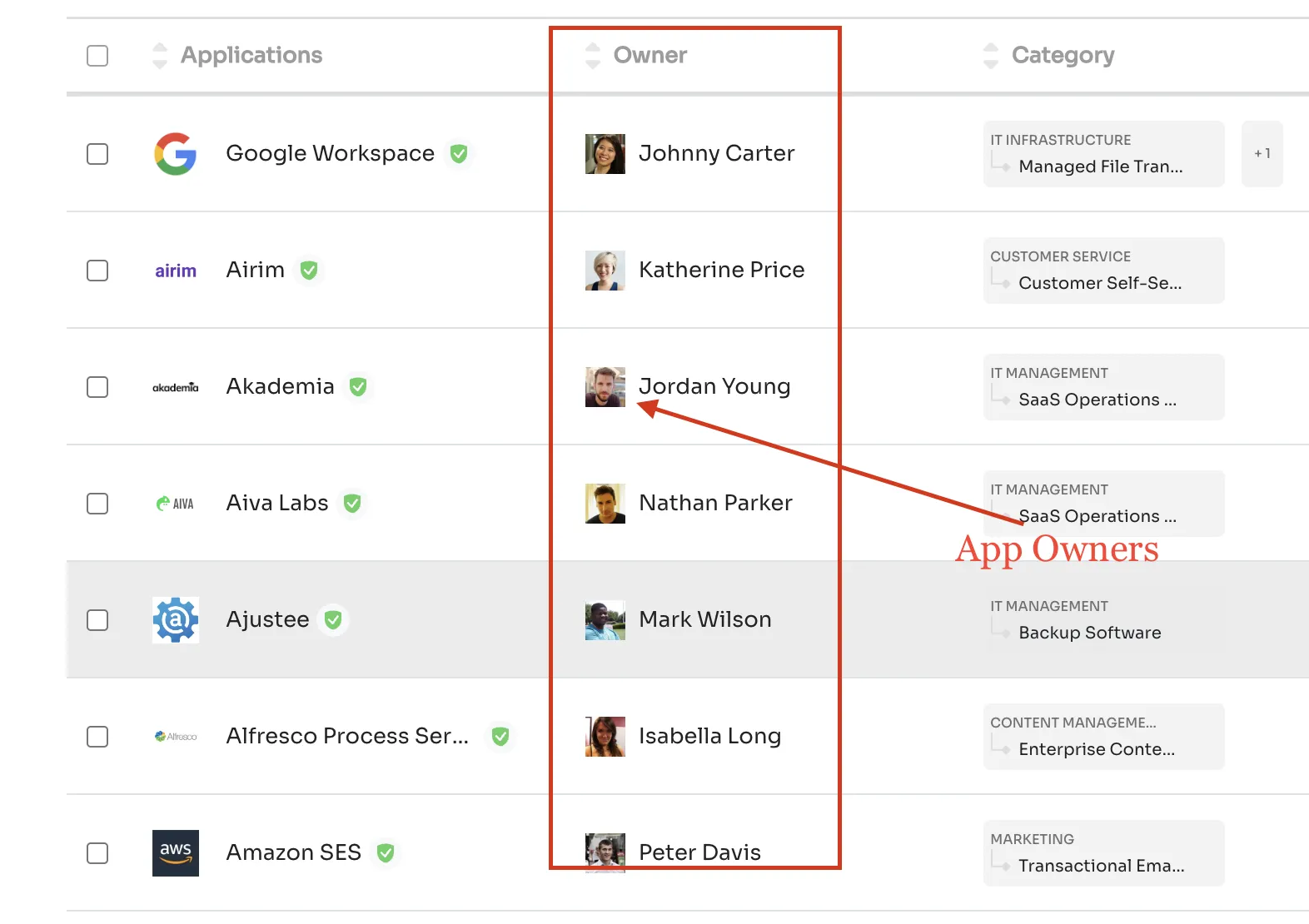
Maintain app ownership
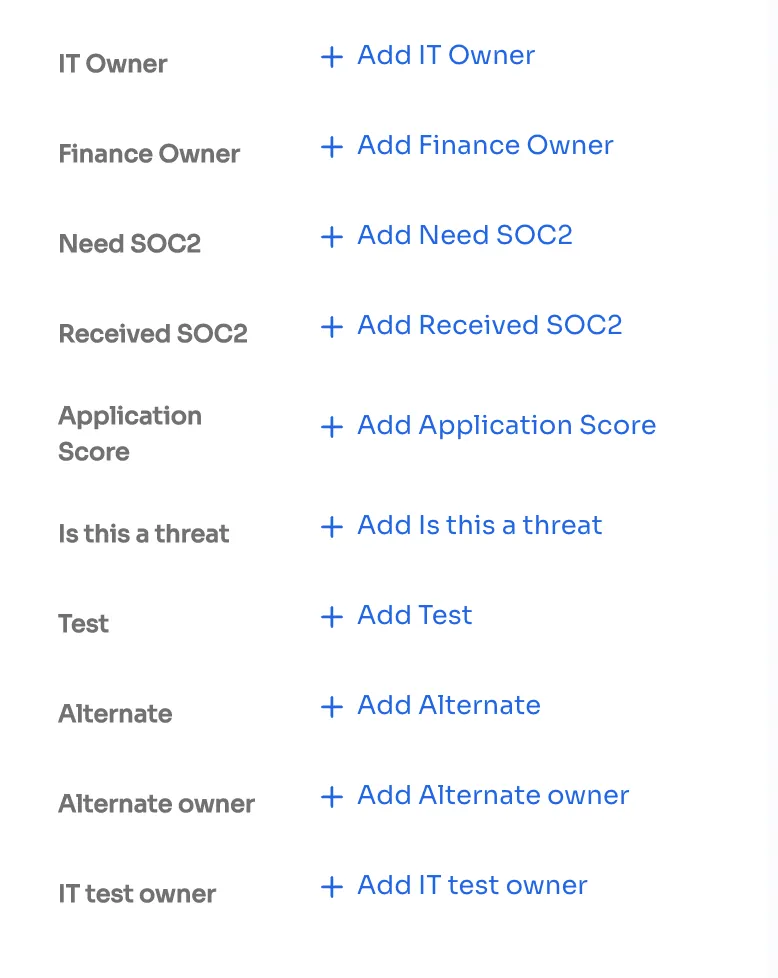
Delegate Ownership for Various Tasks with Finance Owner and Alternate Owner
8. Removal of High-risk Systems
Many organizations hesitate to move from on-premise solutions to the cloud because of potential security threats like data exposure, data loss, and external threats. On-premise data centers and applications are riskier than other cloud-based counterparts. The reason is that cloud service providers offer a wealth of security capabilities that can't be matched by on-site resources, like data loss prevention, web security, intrusion management, encryption, etc.
Moreover, on-site data systems need manpower, money, and resources to keep hackers and data breaches at bay.
By shifting to cloud service providers, IT teams can improve security through patch management, encryption, integration, segmentation, and secure access management.









.svg)














