The need for modern IGA
We have officially entered the era of the Intelligence economy, where data and security have become the most critical drivers for secure and scalable growth.
Identity is the genesis of providing a great customer experience. In a world that’s accelerating towards SaaS and Cloud, it has become the ‘New security perimeter.’ There are two key shifts that are contributing to an increasingly complex identity and access ecosystem:
1. SaaS Acceleration
With the accelerated transition from on-prem to SaaS, companies face new security challenges they never encountered while establishing access control. This is a result of the lack of modern systems that can govern security policies that make sense for SaaS.
'You can only validate who is accessing these applications and not validate what they are using.'
2. Work Decentralization
Employees can access applications from anywhere, creating a decentralized work environment. For instance, a team with multiple collaborators can share access to a set of online documents provided by a cloud-based productivity suite. Employees can access these documents from public Wi-Fi networks, unsecured devices, etc., because the network perimeter is no longer there.
Key challenge: While using Identity as the modern perimeter is a fair enough solution, a long list of access permissions, access methods, and endpoints means no access control beyond the perimeter.
Organizations must have a firm understanding of every interaction users have with their SaaS applications. Siloed IAM tools & outdated software cannot provide IT teams with the visibility to track access information across critical information systems.
The high wire balancing act of Security & Compliance
The consequences of these key shifts is an increased risk of data and security breaches and a lack of industry compliance. Getting perpetually secure and compliant is a near-impossible task, given the importance of building trust in today's competitive vendor landscape & the rising pressure of security on industries like healthcare and finance
Zluri's Modern Access Governance platform for the Identity Cloud
At Zluri, we've launched a robust modern identity governance and administration platform tailored for the SaaS and AI era. Our unique approach helps govern access to your SaaS landscape for the entire user lifecycle through user provisioning, automated access reviews, and self-service access requests.
Why our solution is unique
- Discovery engine:
Zluri's platform enables visibility into 300+ SaaS apps, providing real-time access data, insights, and AI-powered alerts. With an API-first approach Zluri can provide IT and security teams a stronger control over every critical SaaS applications, and enabling 100% visibility.
- Automation Engine:
Zluri's automation engine powers self-operating access workflows, streamlined review automation, and a defined rule and policy engine. Zluri can set up workflows in a way where insights it auto-connected to the required actions.
Our discovery, and automation engines give us better granularity and context to simplify how governance is done for the cloud today.
Current modern IGA capabilities
Cloud-first Access Reviews:
Every organization has employees working in different departments that access critical & sensitive data.
The major question is whether they should be accessing in the first place.
With the decentralization of SaaS, it's a lot easier to gain privileged access but a lot more complex to control.
At Zluri, we've realized the need for a modern approach to reviewing user access, and so we built a solution that provides three key capabilities:
- Contextual real-time data & alerts on access roles, activity, misconfigurations
- Automation that accelerates access reviews without spreadsheets & JSON
- One place for Security, GRC, and auditors to review and report everything
Companies can reduce unauthorized access, protect data integrity, and keep auditors happy by staying compliant with real-time, streamlined reviews.
Learn more about Access Reviews
Lifecycle Management:
Manage user identity and access rights from onboarding and offboarding. Using an automated power engine, we can access requests, approvals, access reviews, and user transitions and centralize these activities into playbooks.
You can read more about Zluri's Lifecycle Management here.
On-boarding Playbook:
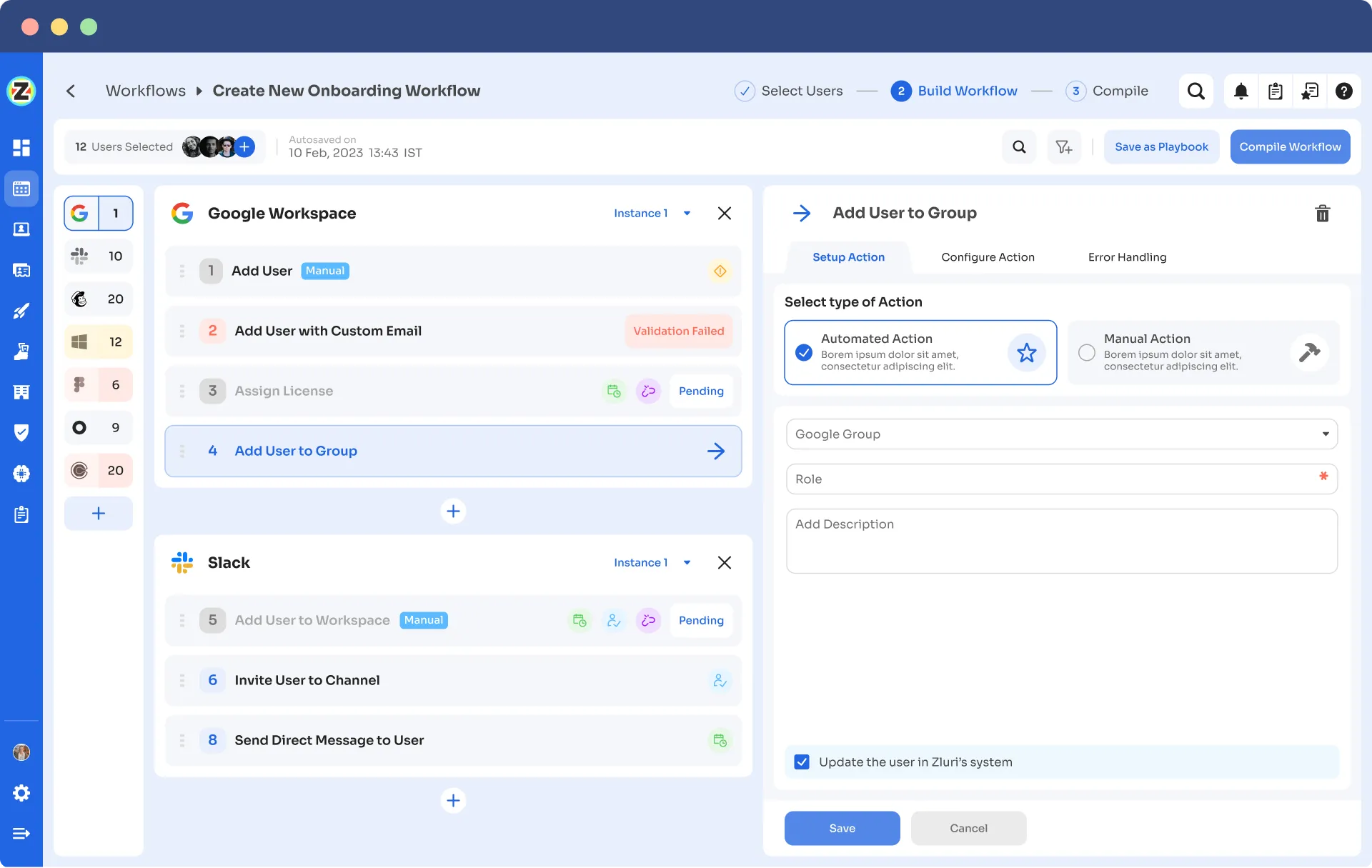
Off-boarding Playbook:
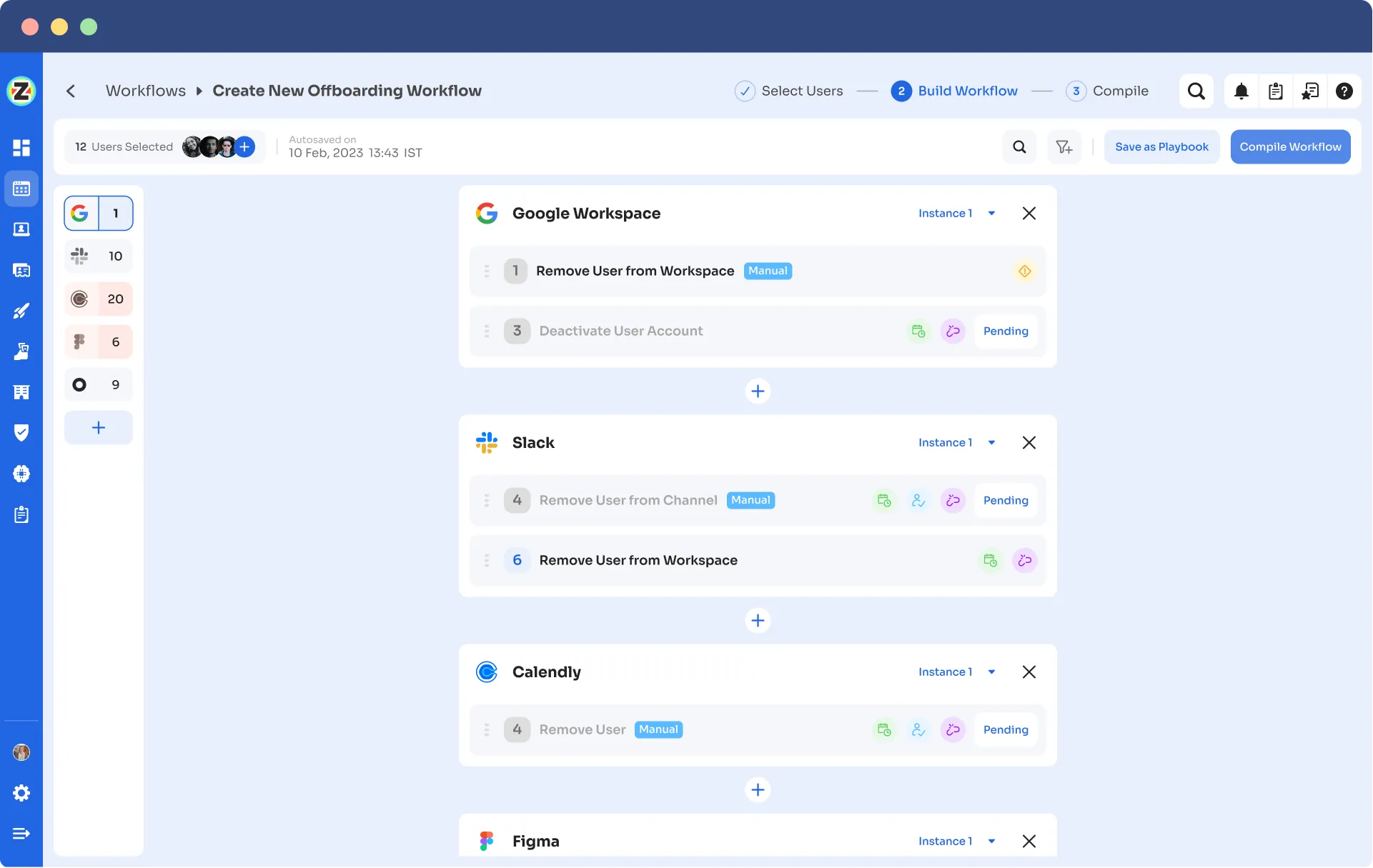
App Store:
Users can submit access requests for necessary permissions, which are then reviewed and approved or denied by stakeholders based on predefined policies, rules, and compliance requirements.
Here is an interesting article on How To Optimize User Access Requests With Zluri
How Access Certifications work in Zluri
Step 1: Select the Application and Reviewer
Choose the application for which you want to run the certification campaign for. Select the reviewer responsible for reviewing access to that application.
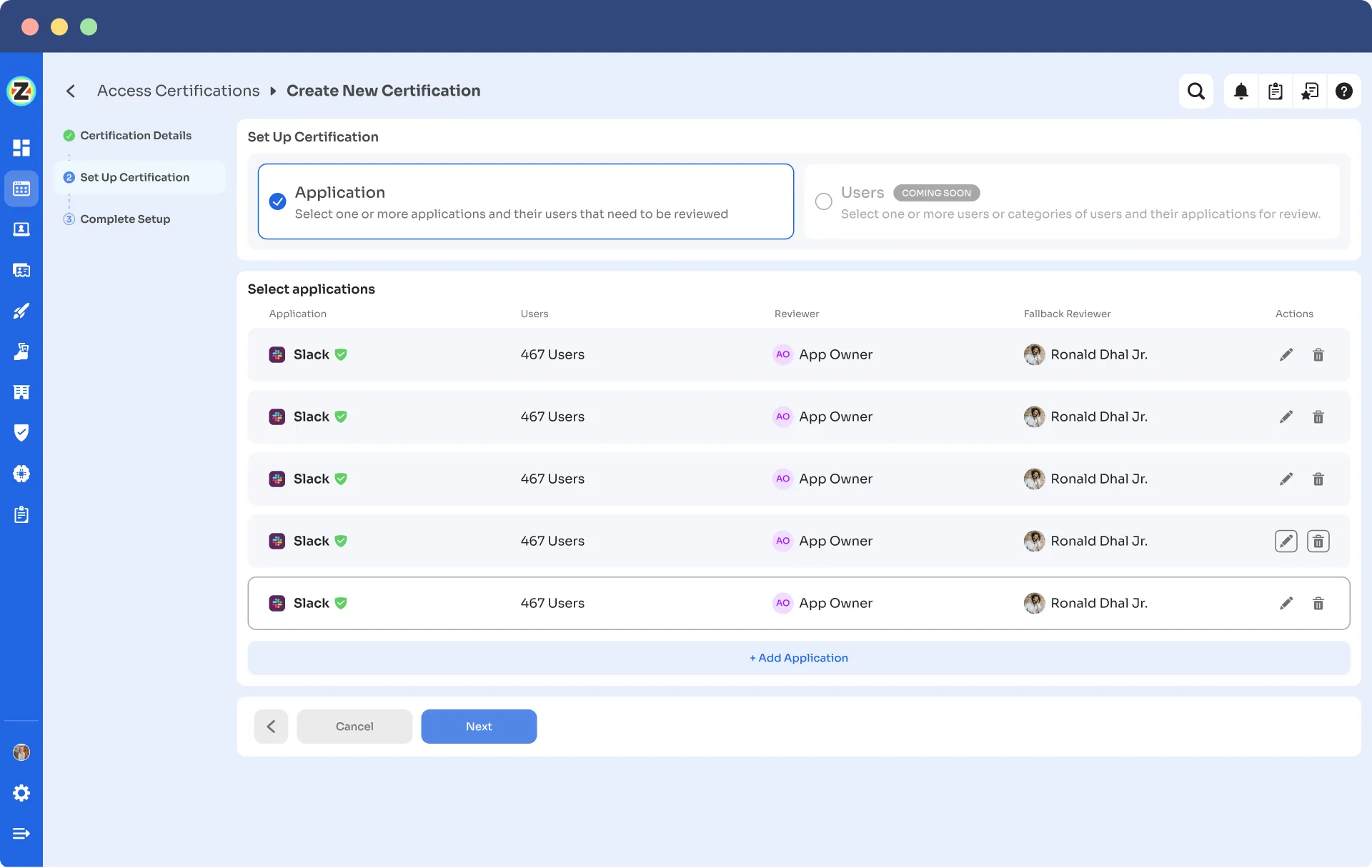
Step 2: Select Users for Review:
Determine which users need to be reviewed for the selected application. Specify the criteria or parameters for user selection, such as user roles or permissions.
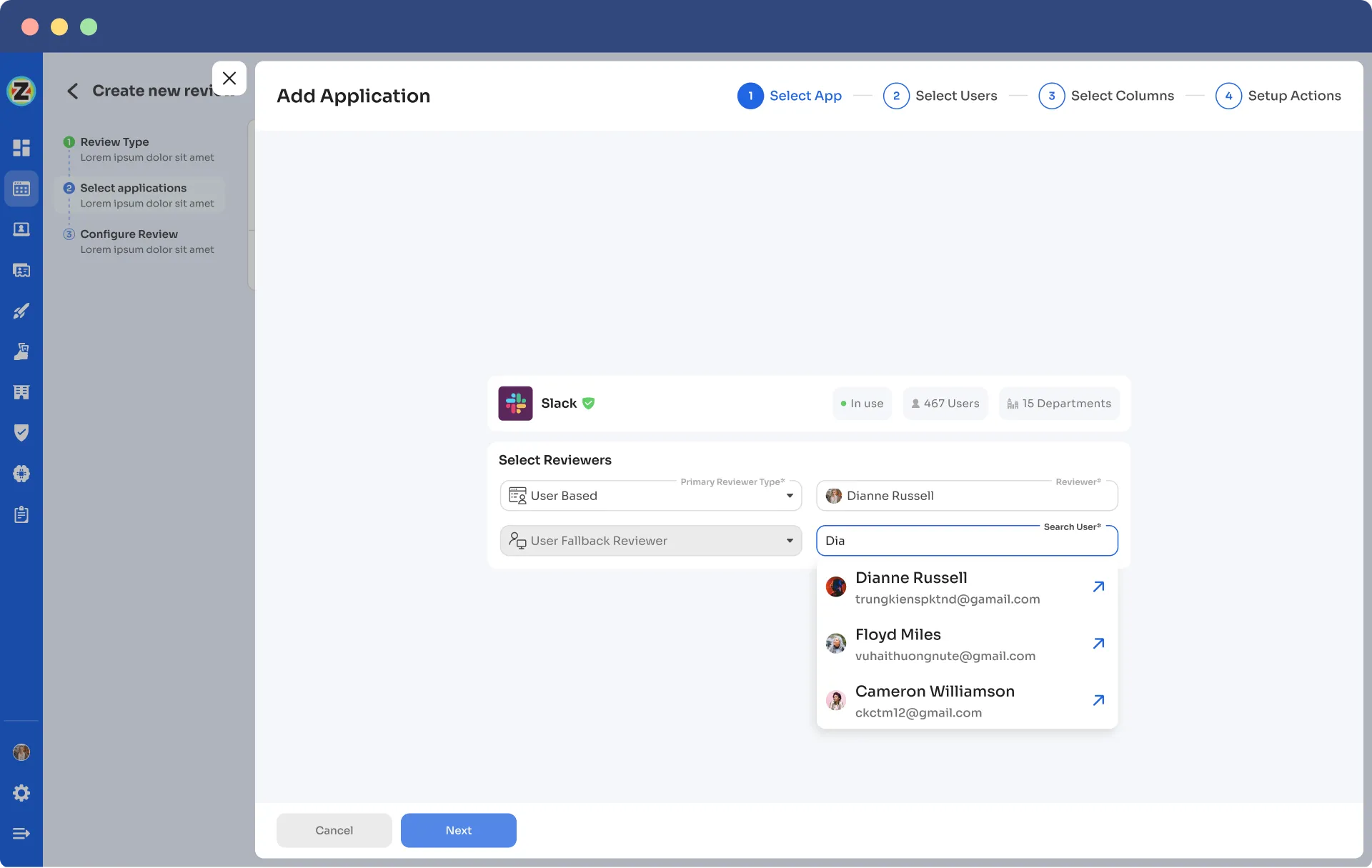
Step 3: Define Reviewer's Visibility:
Identify the user information that should be visible to the reviewer during the review process. Select the relevant data points necessary for the reviewer to assess user access appropriately.
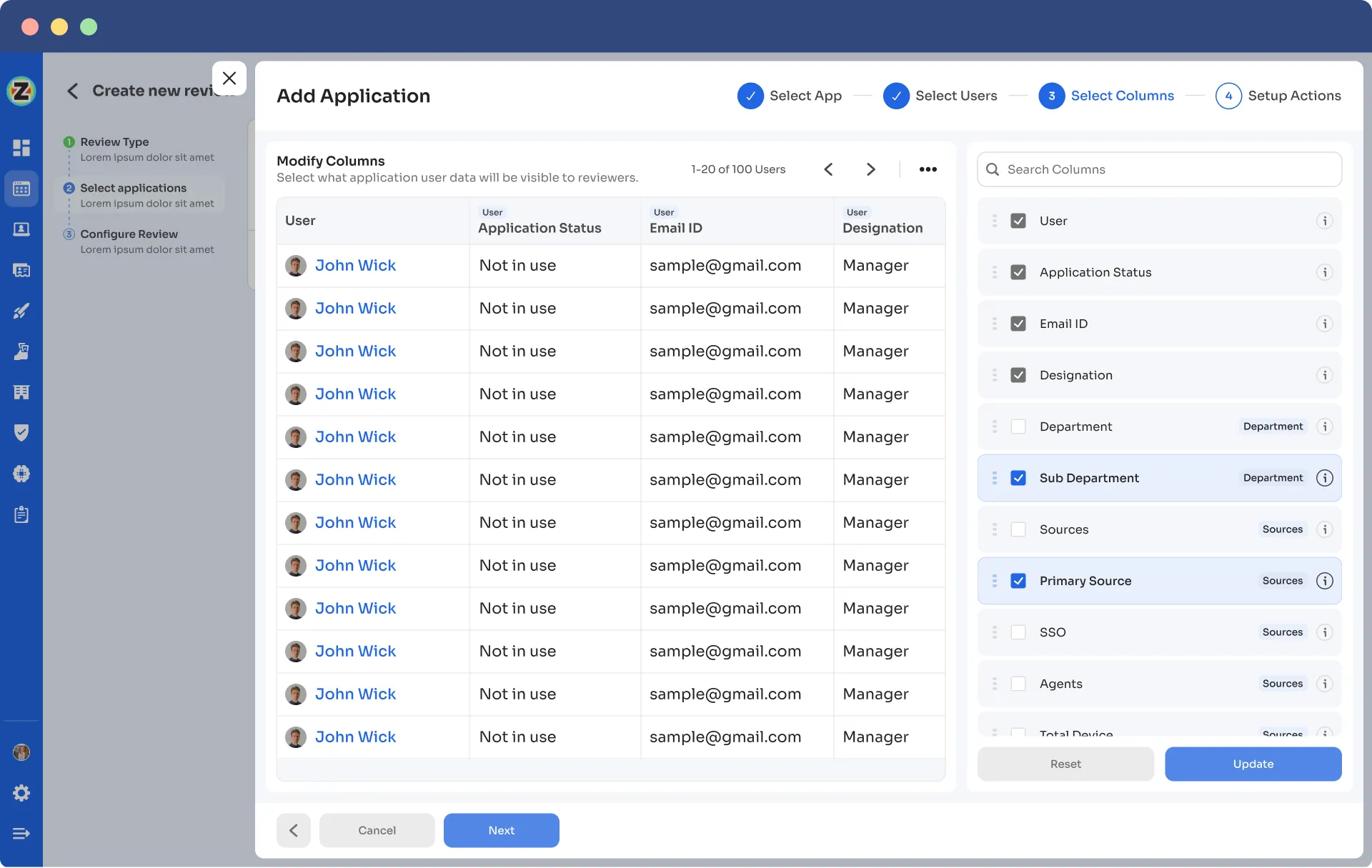
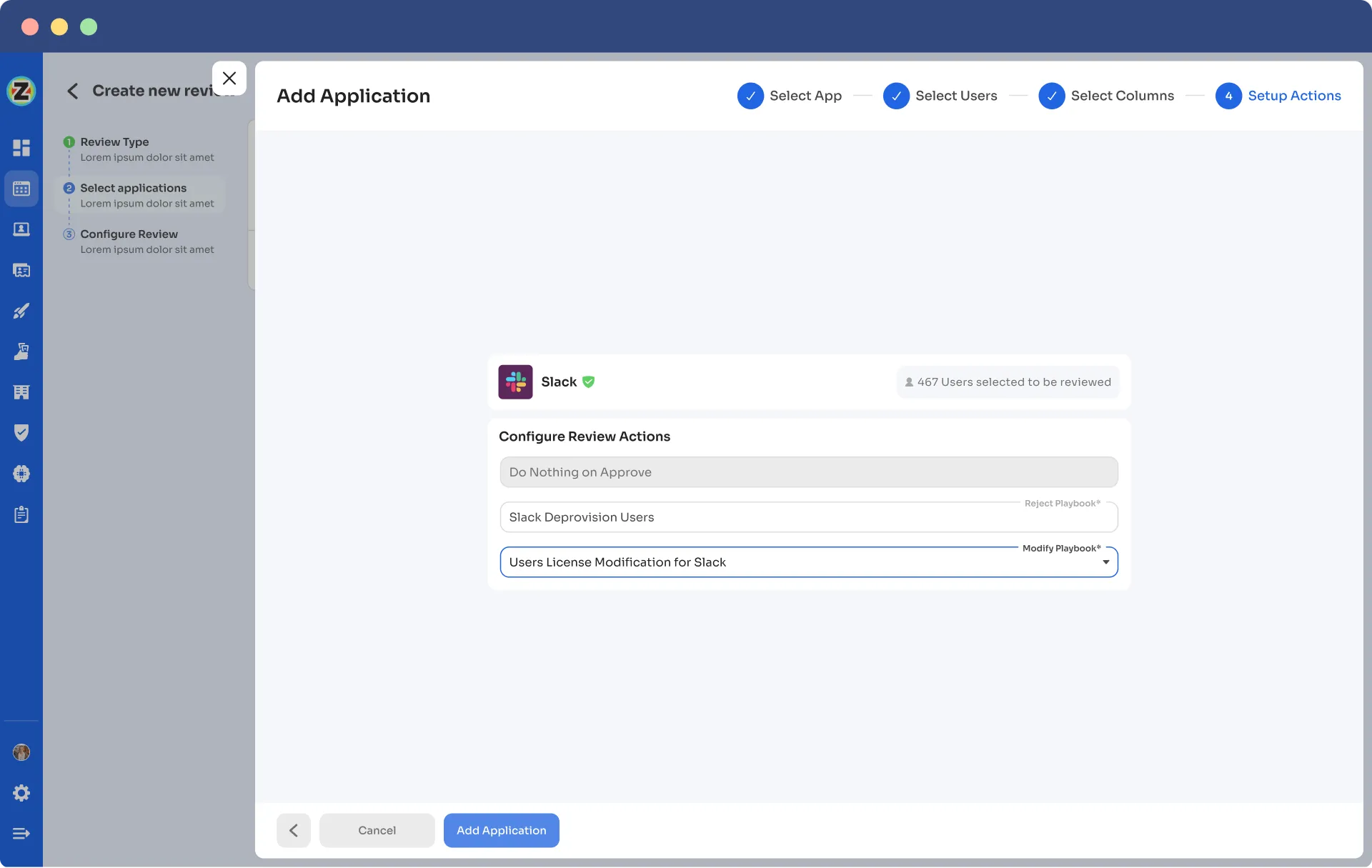
Step 4: Auto remediation:
Once you have taken action on an Access review or an Access certification, you must de-provision the user if it's revoked, which must be done automatically. Only some computers can do that for many applications.
The following monitoring and status updates are provided:
- As the owner, you can access a snapshot of the overall certification process status.
- Get an overview of the pending reviews and work remaining to follow up with respective reviewers.
- Track the status of each application's reviews, including the assigned reviewers and their completion status.
- Send reminders to reviewers who still need to complete their reviews.
By following this process, you can streamline the certification, review, and de-provisioning workflows while providing necessary visibility to reviewers and ensuring efficient management of user access to applications.
The Future of IGA is Autonomous and Automated
Remember when i-Robot and Blade Runner were released, and all we could think about was what the future would bring? Our world has evolved to one where Artificial Intelligence has appeared, and we are adapting to it.
With businesses undergoing digital transformation, they are likely to have various resources across various departments in the cloud infrastructure. To manage this complexity an autonomous and automated IGA is vital.
IGA is the brain for proper visibility and control over access privileges and ensures conformity with business policies.
Zluri's modern IGA platform is an automated way to mitigate risks and identify chaos within the modern enterprise.
Find out how Zluri's Modern IGA governs access to the SaaS






.png)


.svg)














